
SOLUTIONS
Swimlane Automates All Security Operations
AI-enabled low-code security automation empowers teams to solve their toughest problems with ease.


SOC Automation and Beyond
Achieve 240% return on investment by using automation within every security function, from the security operations center (SOC), to governance risk and compliance (GRC), fraud, and beyond.
Solve Your Time, Team and Data Problem
One day is all that it takes to get started with Swimlane. Our security automation platform can help you mitigate alert fatigue, overcome the security talent shortage, reduce overall SecOps complexity, and more..
SecOps Automation for All Industries
No two industries or companies are the same, so flexible security automation is critical. From OT environments to financial services, the federal government, MSSPs, and beyond, Swimlane delivers automation built for your business.
Our Customers
Trusted by the World’s Leading Organizations

Experience the Power of Hero AI
Automate faster and easier than ever before with Hero AI, Swimlane’s collection of AI innovations.
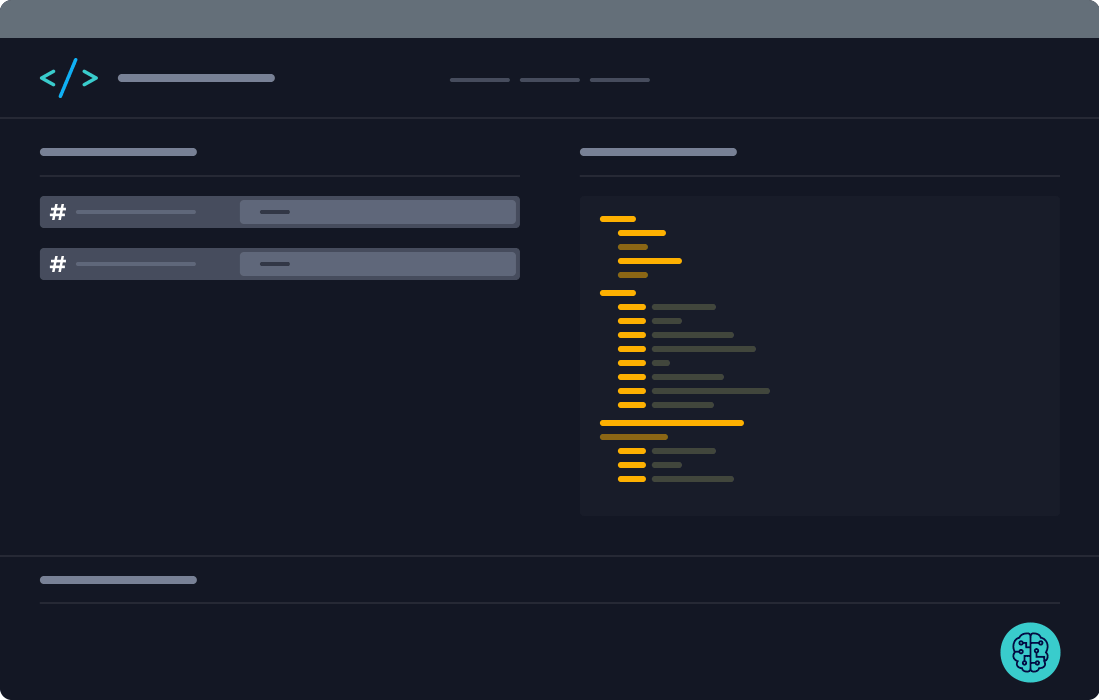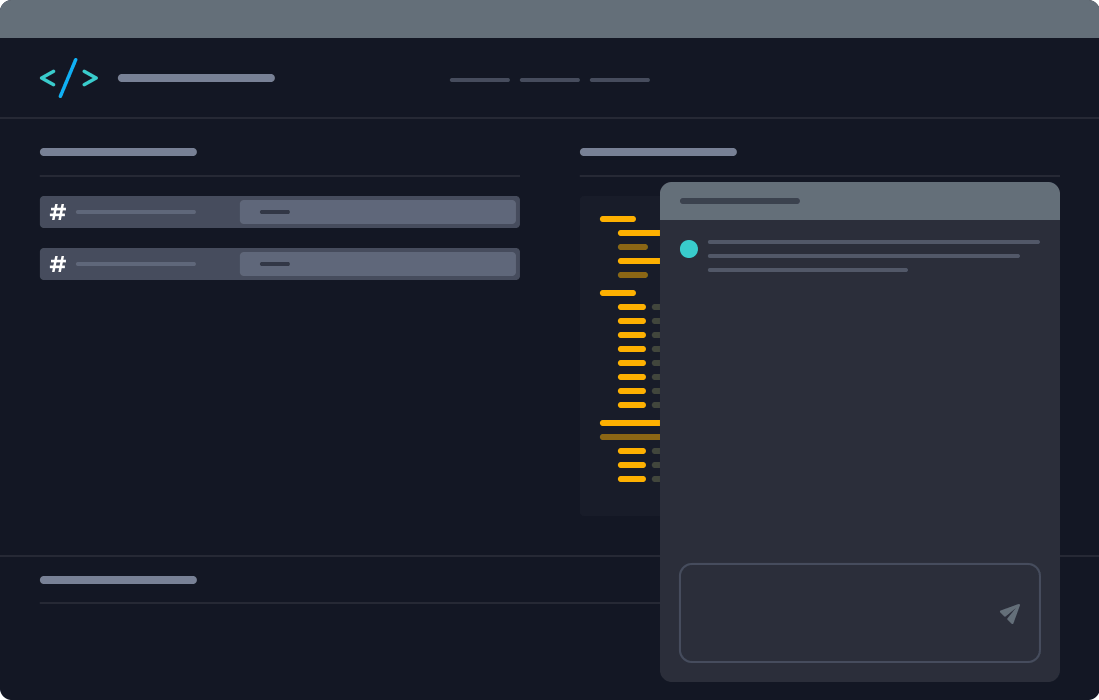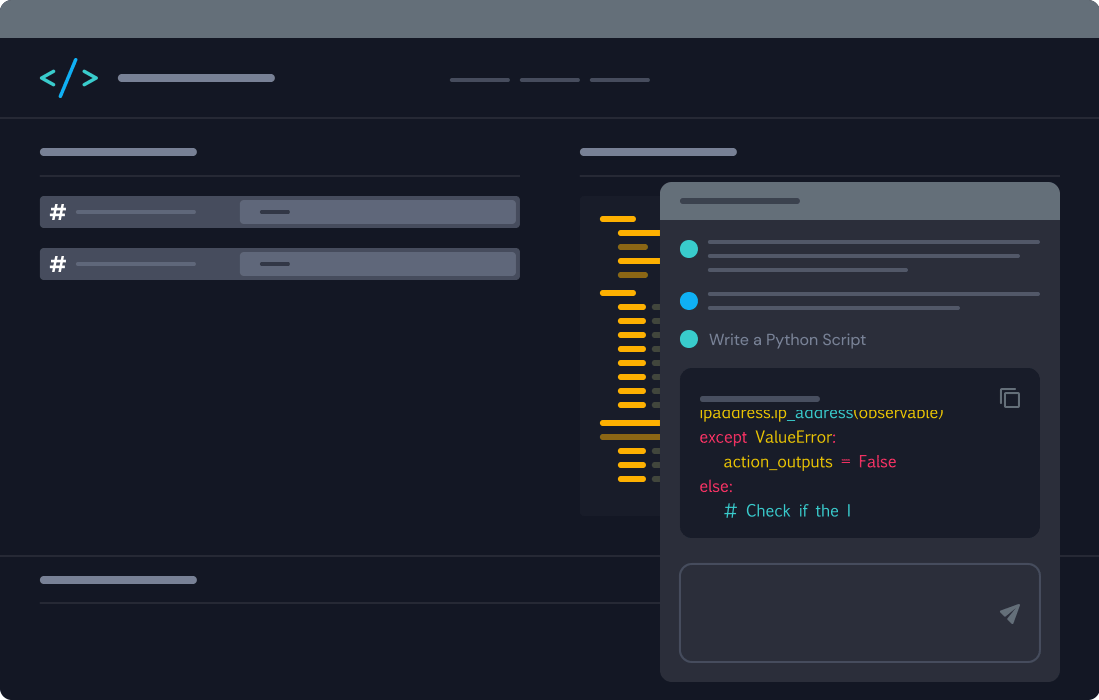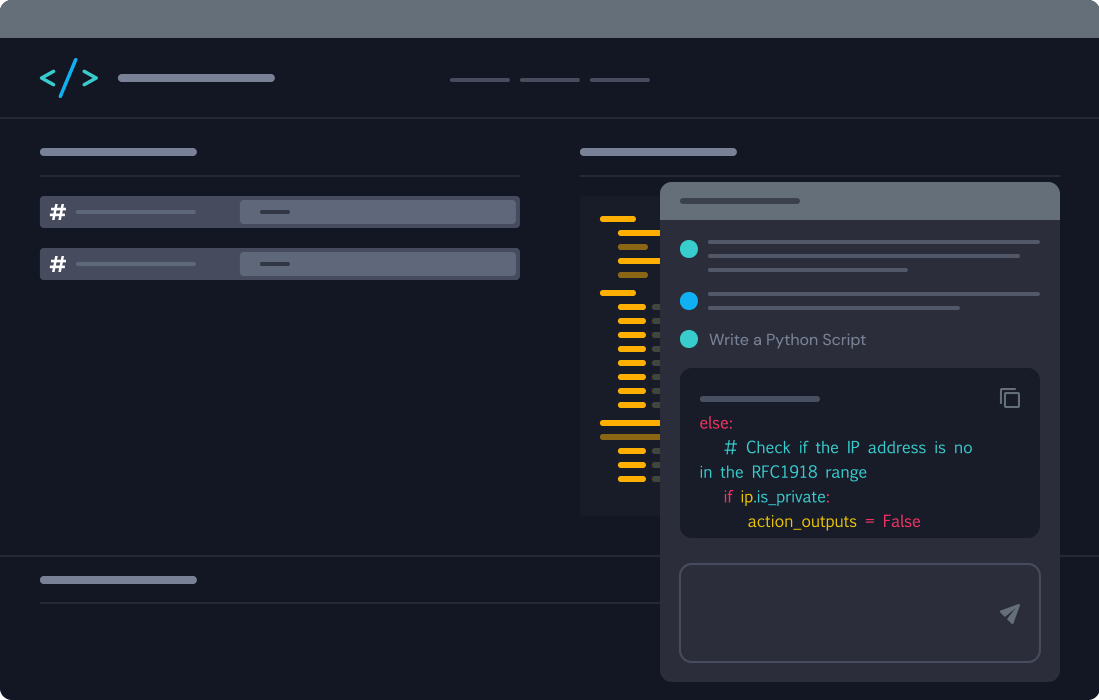
Automate Effortlessly with Turbine Canvas
Build automated workflows as easily as drawing a flowchart with your own low-code Canvas.
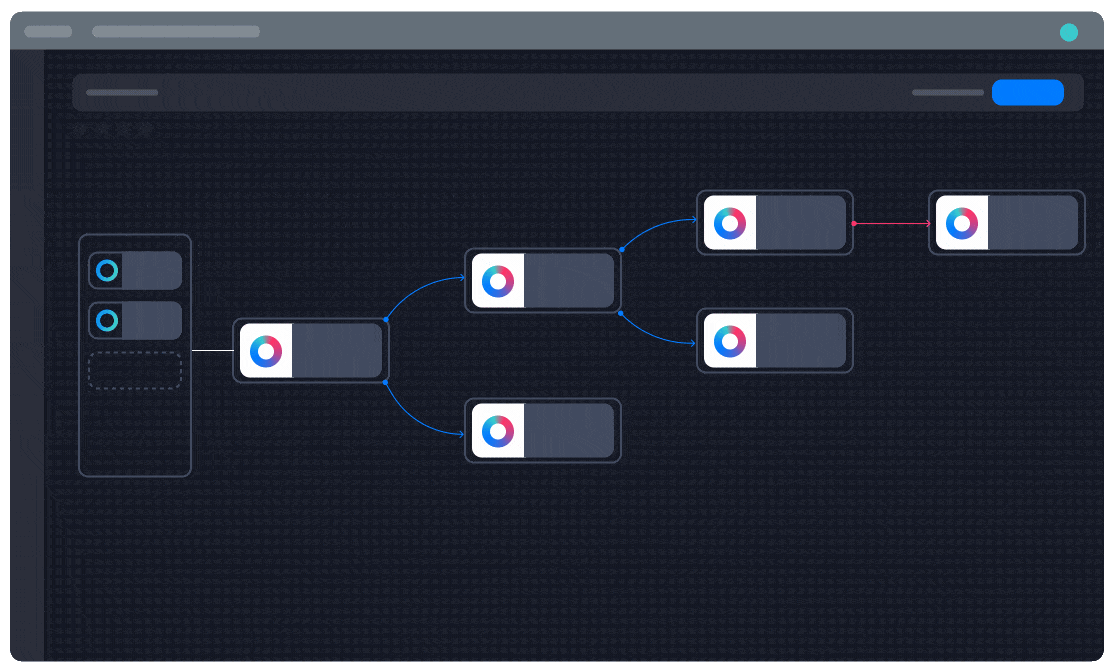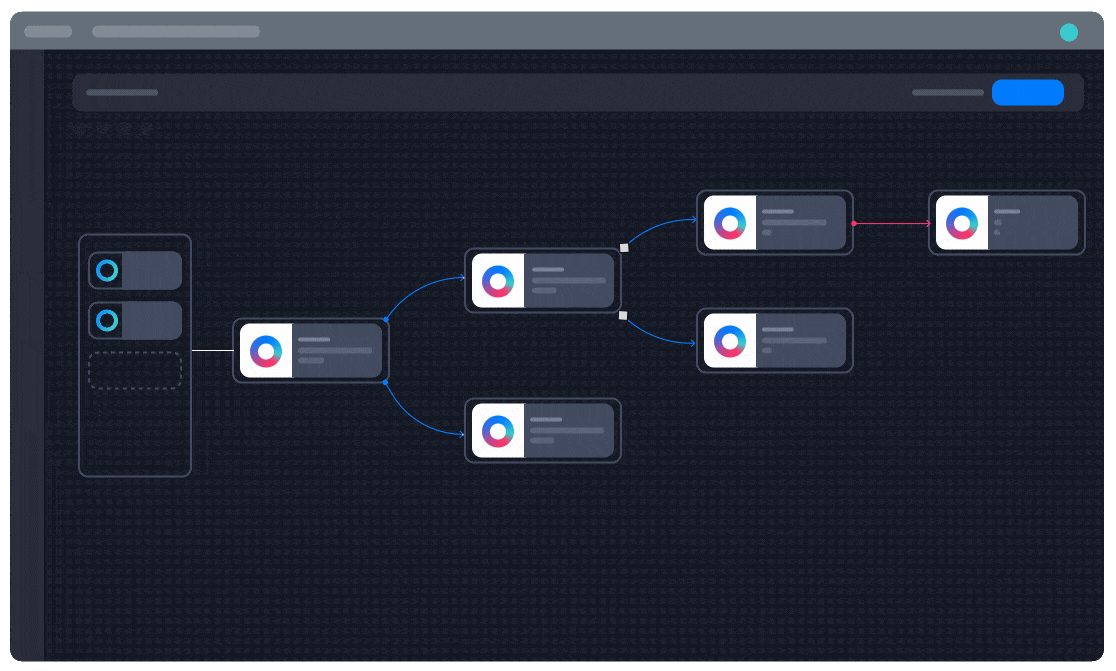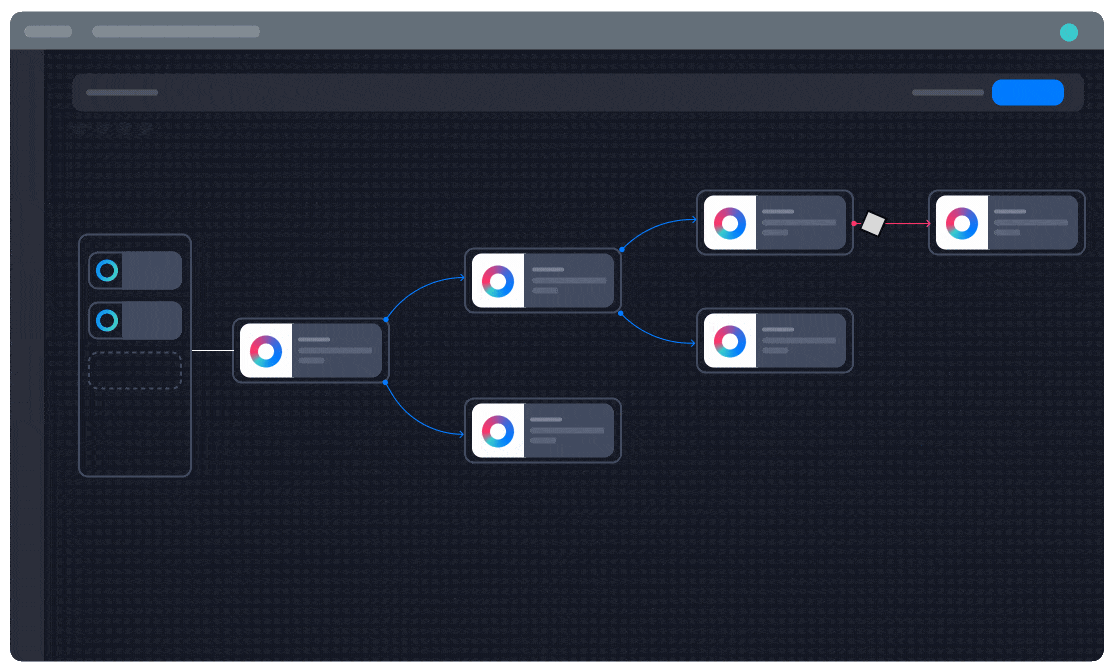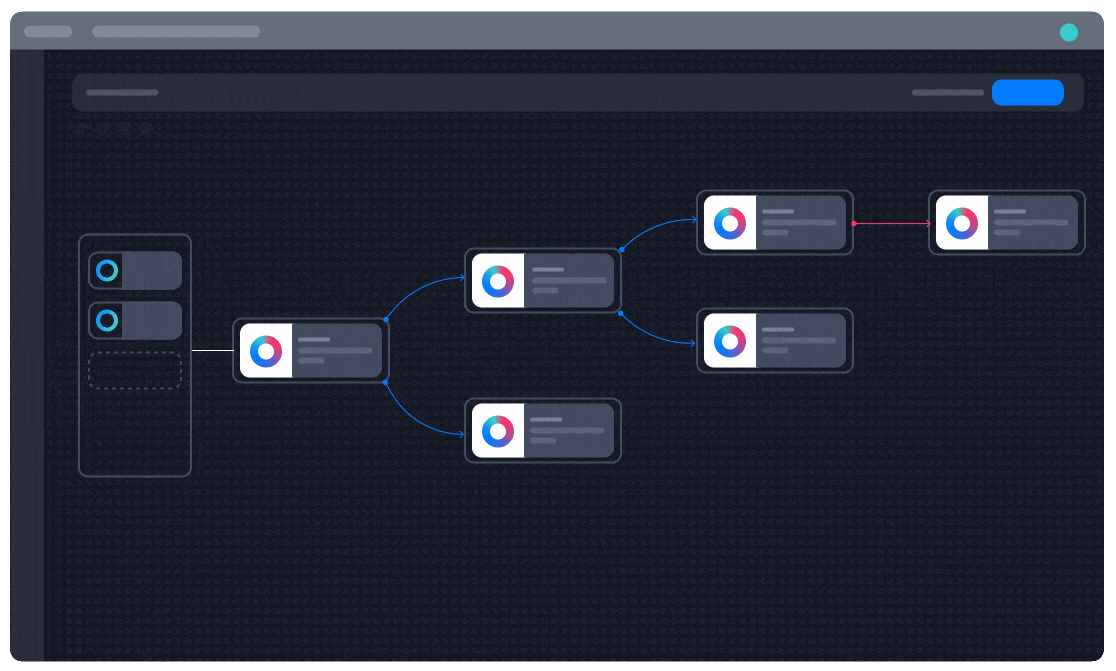
Reduce Complexity and Silos
Integrate with any API without the need for heavy development.

Extend Visibility and Actionability
Ingest telemetry from heard-to-reach sources to speed MTTR and reduce dwell time.
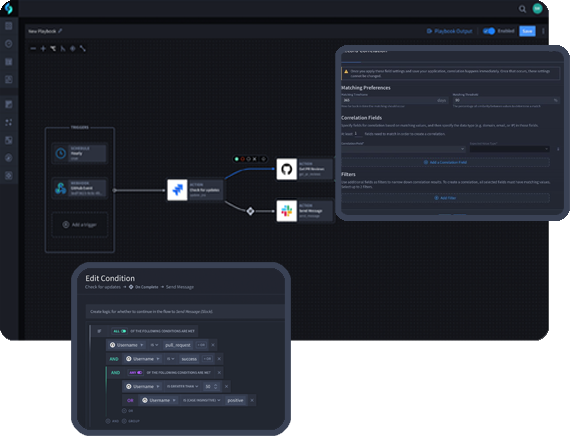
Unify Workflows, Telemetry, and Teams
Robust case management, dashboards, and reporting provide actionable insights and alignment.
Platform
The Swimlane Turbine Security Automation Platform
AI-enabled low-code security automation. Now faster and more scalable than ever.

Cyber Threat Readiness Report
Organizations are facing a growing number of security alerts, a quickly evolving threat landscape, and ongoing staffing shortages. We partnered with Dimensional Research to survey 1000+ global security professionals to better understand these challenges and their ability to address them.
Unlock Infinite Integrations with Swimlane
Instantly connect to any API. Use our verified connectors or create
your own.
ROW – 01
ROW – 02
























