The Security Analysts’ Pet Peeve
As security organizations grow more complex and interconnected, security practitioners often end up serving as a central point of collaboration with those outside their respective teams. This responsibility for cross-functional communication falls on top of their already busy day-to-day activities.
A day in the life of a security operations center (SOC) analyst unfolds as follows:
- The security automation platform receives an alert. It automatically processes and enhances an alert before notifying the analyst. This provides the analyst with as much pertinent information as possible for the upcoming investigation.
- After reviewing the case, the analyst must confirm the purpose and expected nature of the user’s activity. In this example, the user is within the company but outside the security department.
- Next, the security analyst reaches out to the user and updates the case, but needs to wait for the user’s response before continuing the investigation. Meanwhile, the SOC analyst moves on to the next alert.
- After an arbitrary amount of time, the user sees the analyst’s message and responds.
- Only then, the security analyst can continue the investigation. After task switching the analyst needs a refresher on the case details.
This process proves frustrating for analysts and causes delays in the entire alert resolution. Analysts lack visibility regarding the timing for the user to reply, adding to their workload as they need to re-familiarize themselves with the case.
Power for the Practitioner: The Value of Seamless Communication
Swimlane Turbine offers a collaboration module as an extension of its security automation platform capabilities. The collaboration extension uses modular and reusable components to create predefined templates to send context-aware messages to external messaging systems, such as email, Slack, or Microsoft Teams. These messages can trigger an action based on an arbitrary amount of user-defined choices, such as approve, confirm, deny, or request contact. These capabilities included in the collaboration extension make it so that non-Swimlane users easily respond to Turbine-generated messages and participate in security workflows.
Keep reading to learn about the top 3 ways to take advantage of the Turbine collaboration extension.
1. Enhance Detection Signals with User-Centric Triage
First, the concept and scope of “detection” is worth explaining. Detection is the aggregation and correlation of one or many events into an actionable alert. With the introduction of security automation into a modern Security Operations (SecOps) tech stack, there is an additional phase called alert decoration. Additional lookups, enrichments, and other automated activities take place to improve the understanding of the alert for the analysts.
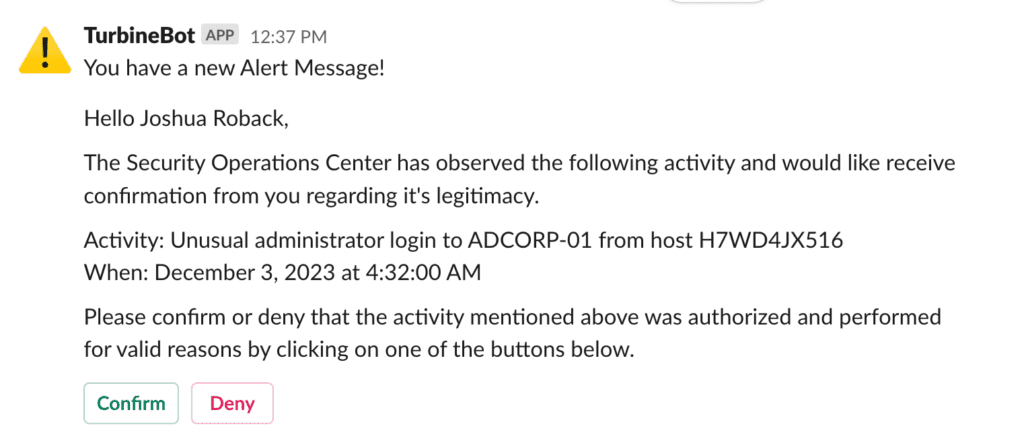
The Turbine collaboration extension adds another additional layer of detection analysis to modern SecOps capabilities – the user-centric triage layer. The system automatically loads a predefined template, enhanced with context from the alert. The impacted user in the organization receives a message that asks questions such as “Did you perform this activity?” or “Did you log in from this location at this time?”. Subsequent automation activities are triggered based on the user’s selection from a predefined list of options.
This user interaction extends the scope of detection while saving time and manual effort for the SOC analyst. This example scenario alone can save analysts hours of effort every week.
2. Automate Approved Actions
Not only is a security organization increasingly interconnected, but so is the information technology (IT) department as a whole. The increasing use of microservices makes it harder to completely understand how individual efforts to reduce problems are affecting the broader system. Because of this interconnectivity and complexity, it’s common for threat mitigation activities to cause business disruption. A SOC analyst can’t also be the subject matter expert of this interconnected infrastructure. Therefore, many security teams have to propose mitigation actions to key stakeholders before acting. This lag between asking, getting an answer, and taking action based on the answer increases the critical time for threat mitigation.
The Turbine collaboration extension empowers analysts to send automated approval requests to subject matter experts in a fast and efficient way. Upon receiving a response from a predefined list of options, Turbine can automatically execute the mitigated action, without the need for additional analyst intervention.

3. Streamline Team Notifications
The analyst’s role, assisted by automated detections, can be compared to finding a needle in a haystack. But as telemetry sources and their volume continue to grow, the number of automated detections also increases, transforming the challenge from a needle in a haystack into a needle in a needlestack. In light of this, it is very difficult for an analyst to identify the most critical needle.
The Turbine collaboration extension enables SOC analysts to send messages to a communication channel outside of the security automation platform such as Slack, or Microsoft Teams. This allows for quick initial actions from a list of predefined options. detect, validate, escalate!

See it in Action
For a more detailed walkthrough, check out our video demonstration. Witness how the Swimlane Turbine collaboration extension makes communication a whole lot easier.
In conclusion, Turbine reimagines collaboration at its core, prioritizing the improvement and acceleration of communication, and response times. This shift empowers practitioners by returning control to them. Turbine’s automation captures analysts’ attention, contributing to its effectiveness in the operational landscape.
If you haven’t had the chance to explore Swimlane Turbine yet, we’d encourage you to request a demo here.
Request a demo
If you haven’t had the chance to explore Swimlane Turbine yet, request a demo.


