Average cost of a data breach in 2022
$
M
Attackers use automation, so level the playing field with SOAR.
framework helps hunters identify threat actors
MITRE ATT&CK
Swimlane provides potential commands, queries and even detections for specific techniques.
and Entity threat hunts
Situational
Swimlane automates analysis of vulnerabilities and external attack data to identify trending TTPs.
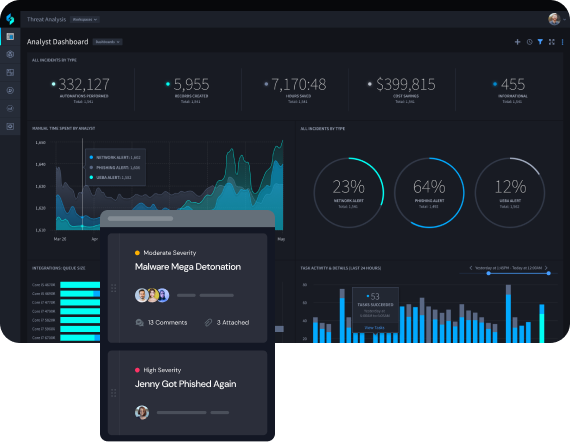
Integrate Tools for Better Visibility
Swimlane Turbine’s Autonomous Integrations provide an ecosystem-agnostic orchestration solution without requiring developer resources. This improves hunting capabilities and response, while effectively protecting the organization from attacks.
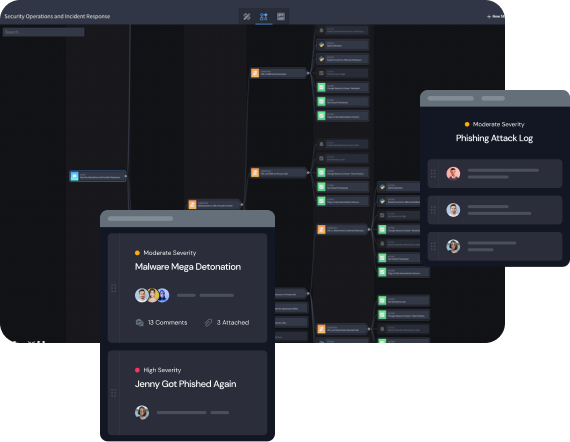
Reduce MTTD and MTTR by 50%
Automate repetitive tasks to help continuously hunt for threats at machine speed, enabling your security team to focus on more complex threats quicker while also reducing mean time to detection (MTTD) and response (MTTR).
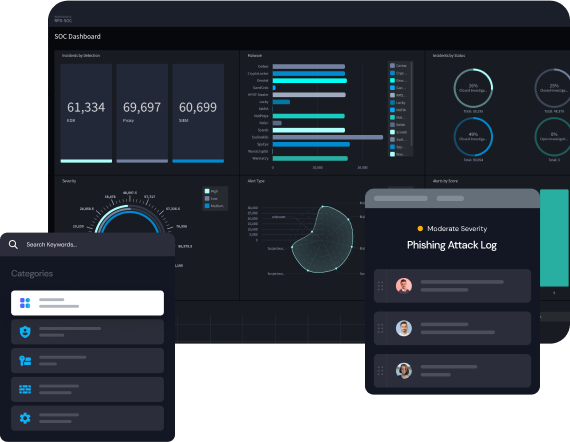
Streamline the Threat Hunt Process
Align your processes and procedures with industry best practices with fully-customizable, automated playbooks and workflows. Use Swimlane’s adaptable low-code playbook builder to create the necessary automations to accelerate the hunt workflow and sift through the noise.
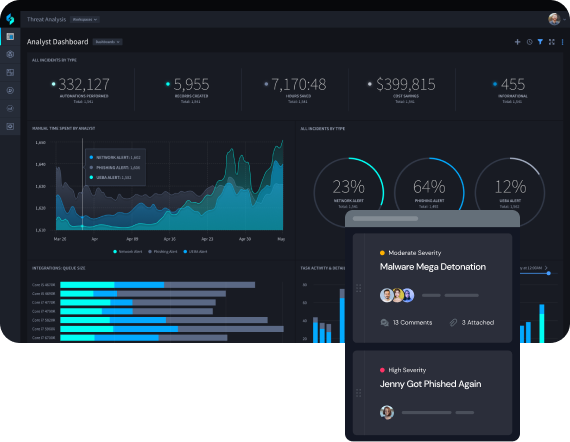
Mitigate Analyst Burnout
Swimlane handles the mundane and time-consuming tasks required for threat hunting, so that analysts can allocate their time to strategic work. Swimlane Turbine also helps SecOps standardize and scale critical security processes.
Automate Threat Hunting with Swimlane Turbine
The world’s most capable security automation platform