of data breaches are caused by insiders.
%
Employees/ individuals with authorized access may leak data because they are oblivious, negligent, or malicious.
average annual cost of insider threats.
$
M
With security automation, SecOps teams can quickly act when alerted to malicious human behavior.
for SecOps teams to manage insider risk
System of Record
SecOps teams have the integrations and information they need to better defend against potential insider threats.
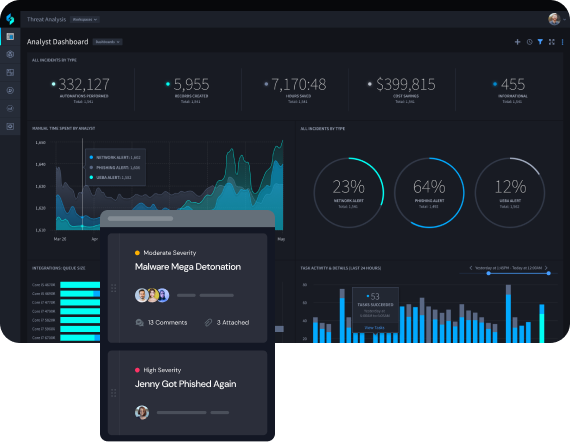
Speed Insider Threat Investigations
Insider threat investigations are nuanced and time-intensive. Bring humans in the loop of automation to speed manual information gathering, and collaborate on active insider threat cases.
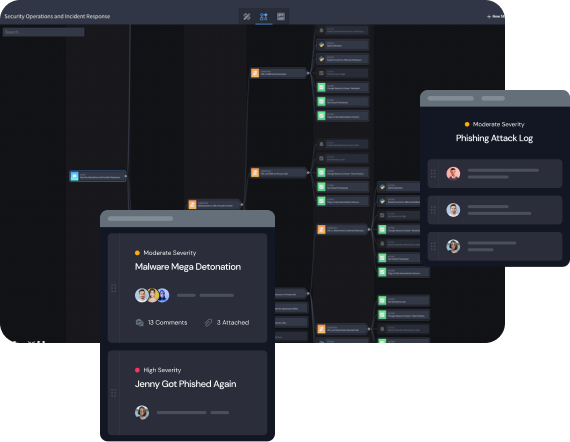
Improve Insider Risk Posture
Security teams who leverage low-code automation for insider threat use cases gain the scale and efficiencies to reduce insider risk holistically. This means that they address risks introduced by employees with elevated access, malicious insider threats, third-party risk, shadow IT use, and more.
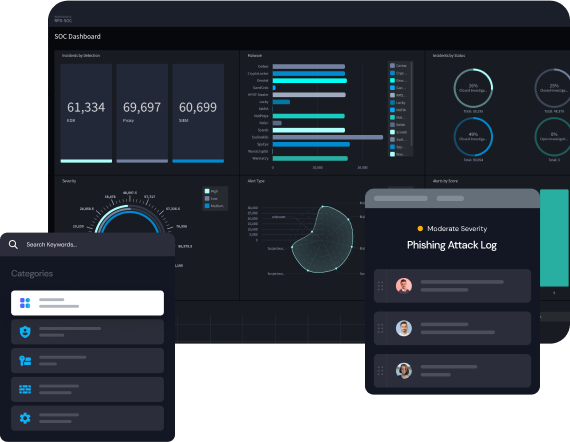
Protect Future Profits
Nothing puts future profits in jeopardy like leaked source code, roadmaps, customer lists, vendor contracts, or regulated data. Establish a system or record for insider risk to validate that your security controls are effective at protecting valuable and regulated data.
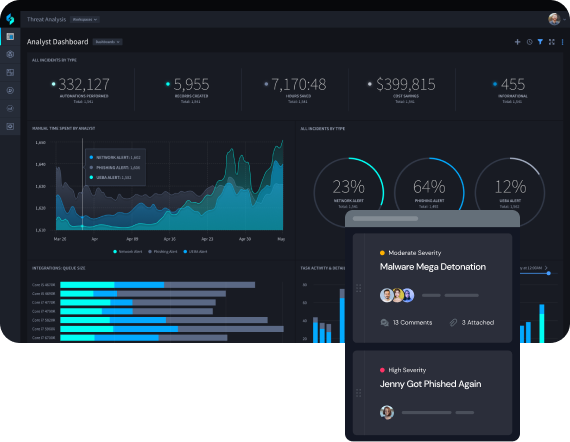
Improve Cross-Functional Collaboration
Insider threat programs require the right combination of people, processes, and technology. User-centric dashboards, reporting, and case management help to bring non-security stakeholders like legal and HR into insider threat response processes.
Automate Insider Threat Detection with Swimlane
The world’s most capable security automation platform