Top Case Management Capabilities Every Analyst Needs
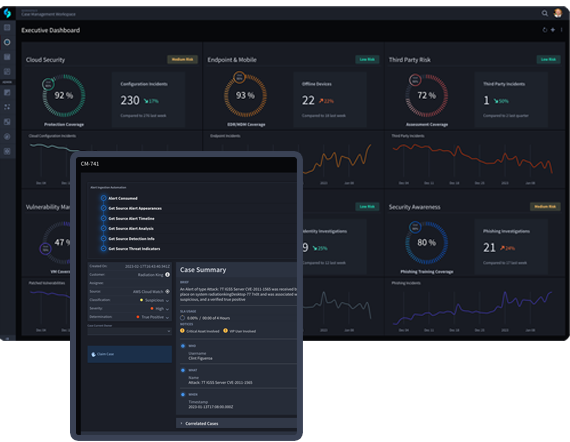
Analyze and enrich incident data in real-time so that analysts can spend time making decisions instead of gathering information manually. This helps analysts institutionalize unique business processes while ensuring that compliance standards are enforced.
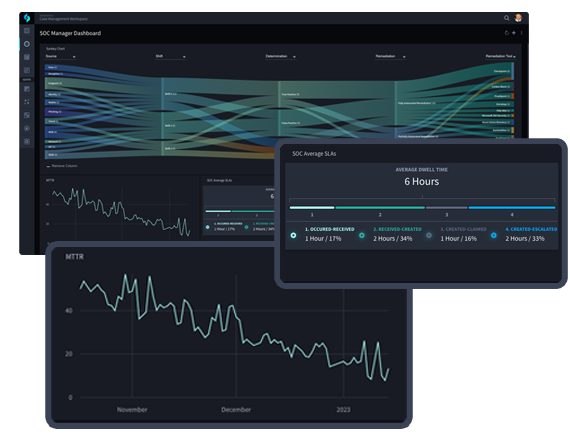
Swimlane Turbine’s dashboards are populated by self-documenting playbooks to provide security teams with visual models to easily see actionable insights like MTTR, MTTD, ROI or where they need to reallocate resources to avoid employee burnout.
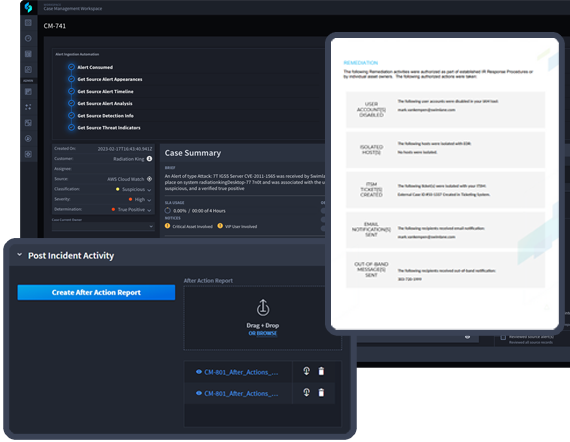
Turbine offers a low-code visualization studio which makes it easy for anyone to build custom reports. These reports can be exported on a scheduled cadence to inform CISOs or other stakeholders.