
How to Respond to Threats Faster with Active Sensing Fabric
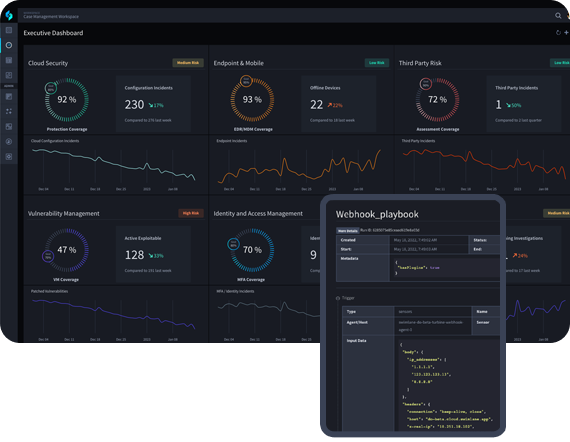
Modern infrastructure must account for various data streams with webhooks, poll requests, pub/sub, file creation, SMS messages, email messages, and IoT. Turbine listens across the entire security ecosystem, taking immediate action directly at the source.
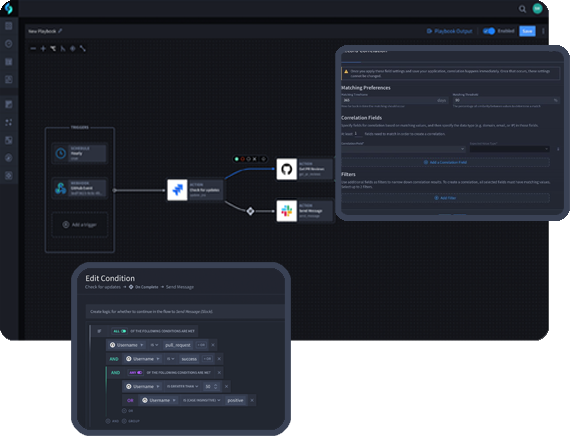
Every organization has unique business logic and processes. Turbine uses custom filtering, pre-processing, deduplication and inline enrichment to harness this logic while it executes thousands of concurrent automations.





