Why Assess SecOps Efficacy?
The cost of compromised systems quickly stack up. Data loss, equipment replacement, legal fees, 3rd-party incident response, ransom payments, fines and more. The average cost of a data breach has risen to nearly $4.24 million and continues to grow. CISOs must quickly identify security trends in their SOC and easily access metrics to communicate effectively with the C-level and board members. Unfortunately, this is time-consuming and labor-intensive.
Actionable Insights
- Dynamic case management and collaboration hub
- Highly composable dashboards
- Real-time reporting for CISOs and stakeholders
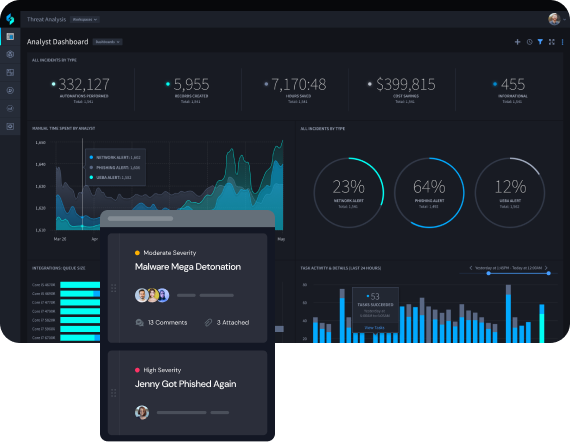
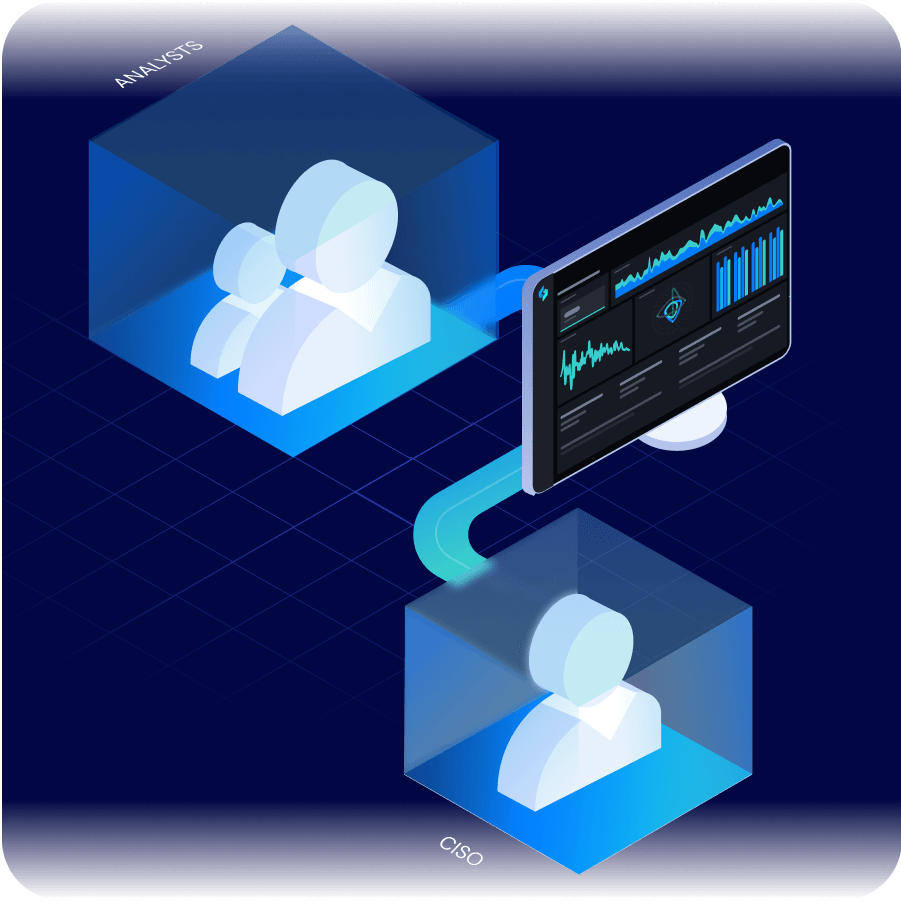
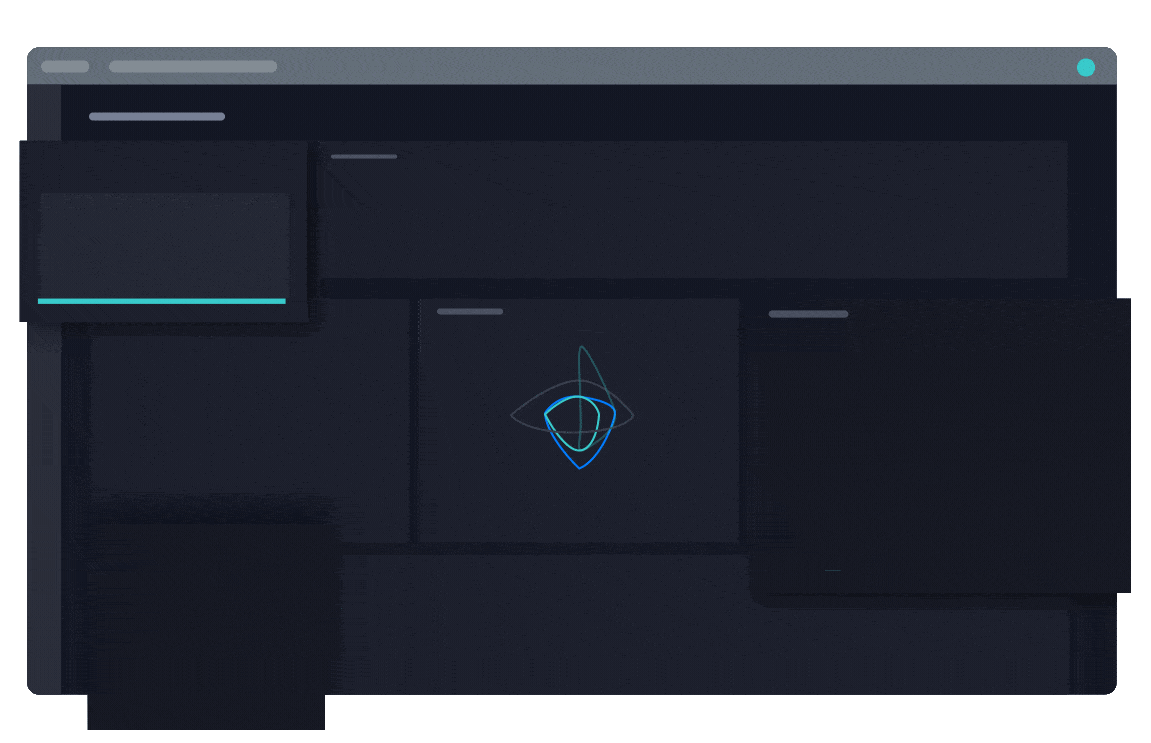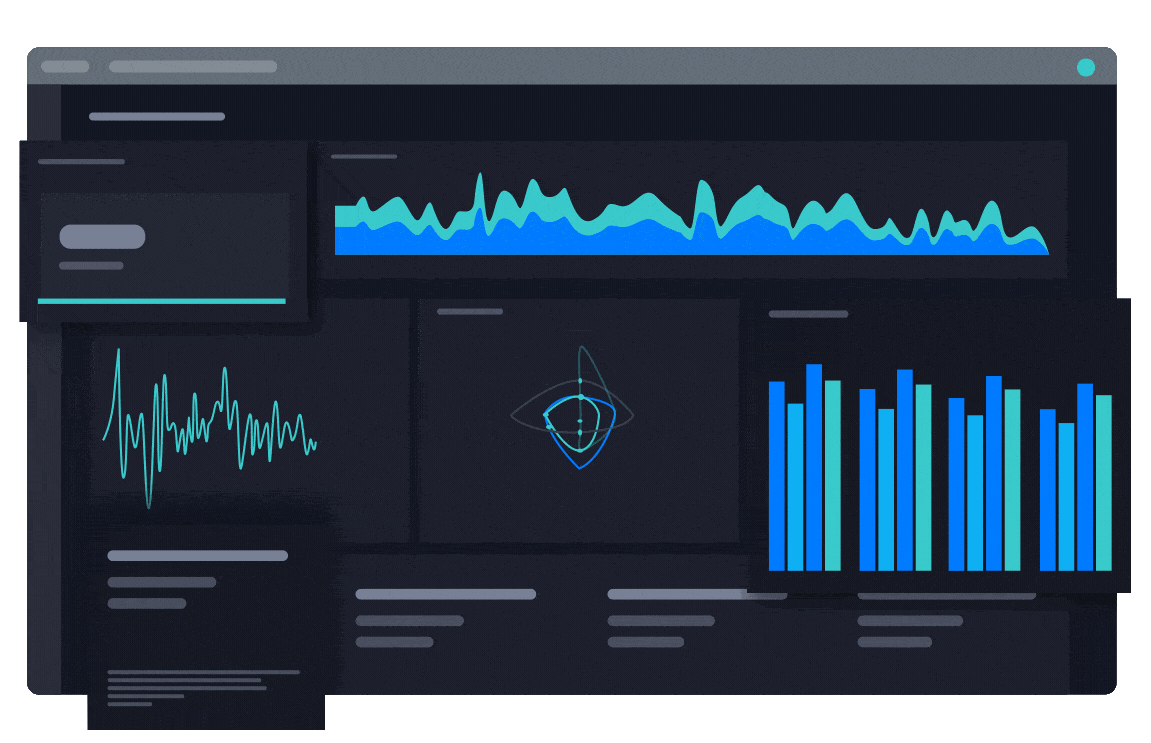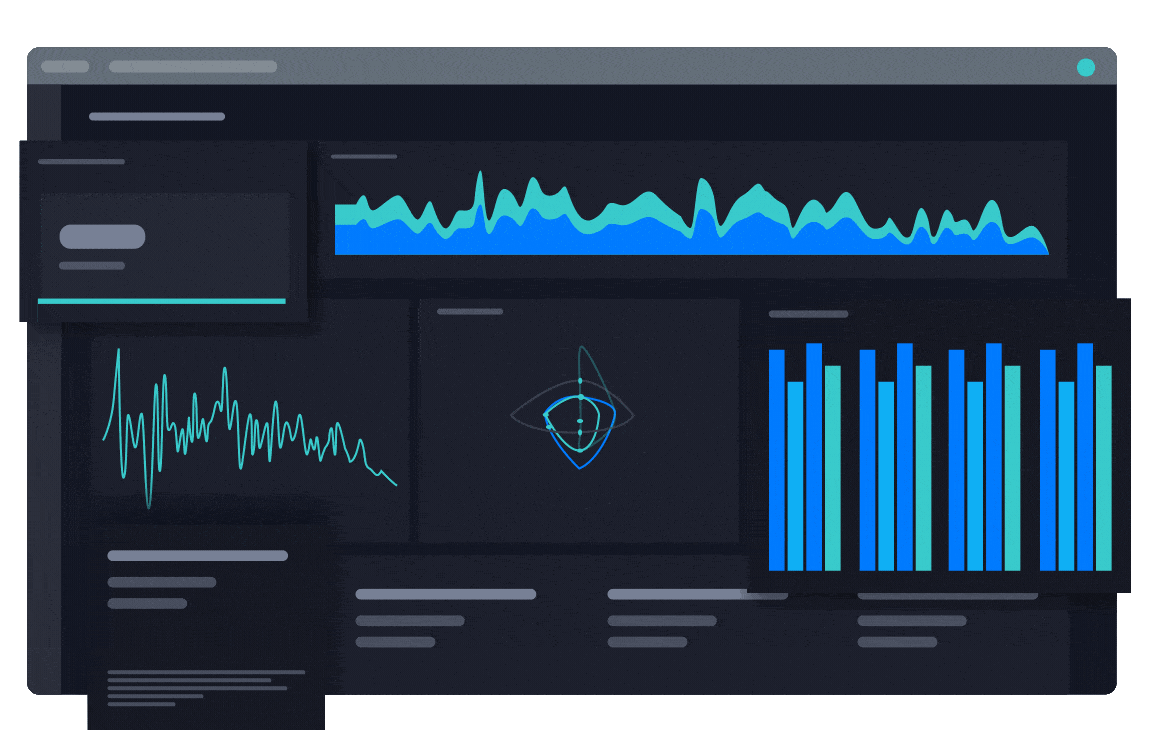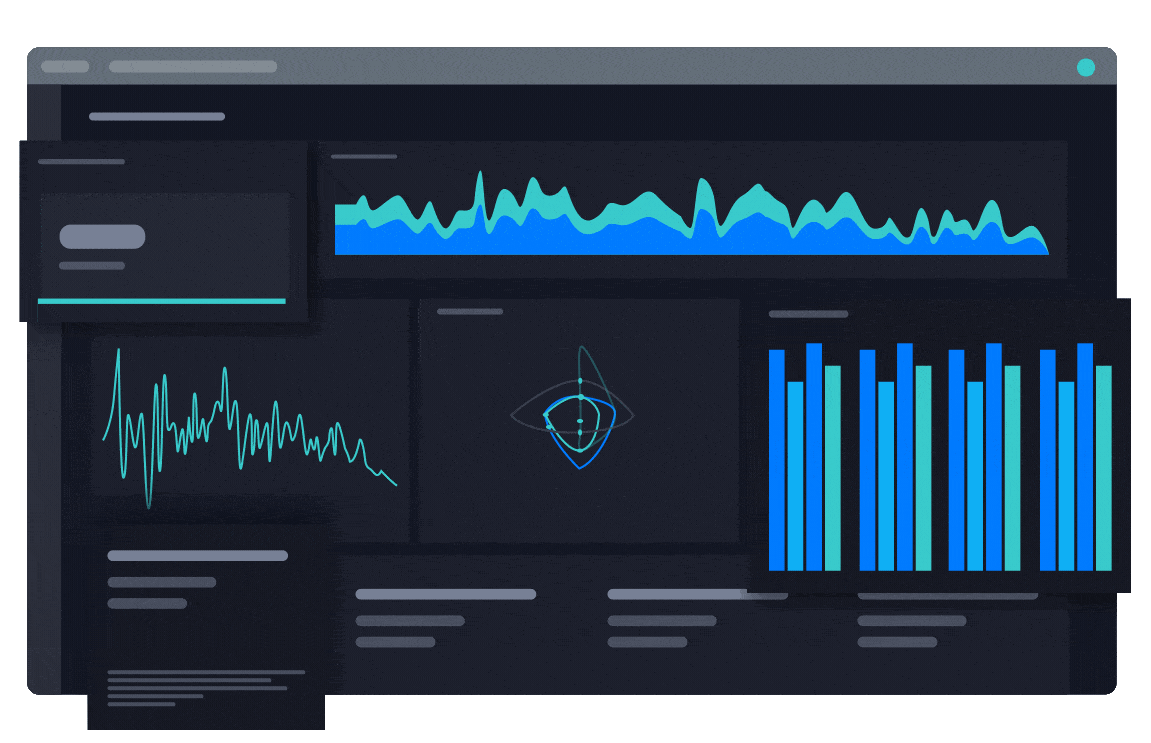
Customizable Dashboards and Reporting for Every Stakeholder
Configurable dashboards and automated reports deliver a system of record for security leaders. Combine the human and machine data needed to justify security investments to the CEO and board.
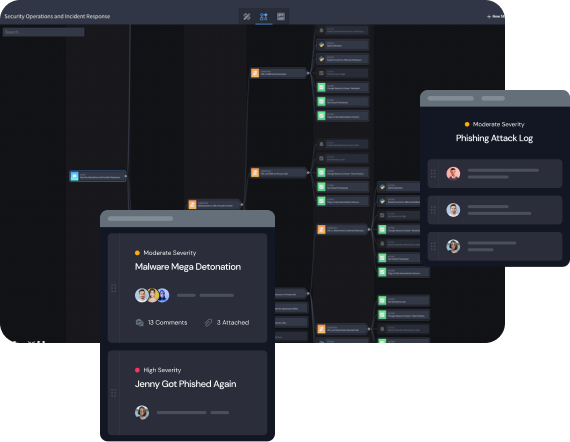
Expand Automation Across Your Enterprise
Unlock the potential of automation beyond the SOC. Automate use cases around fraud, employee offboarding and more to save nearly $900k per year with Swimlane.
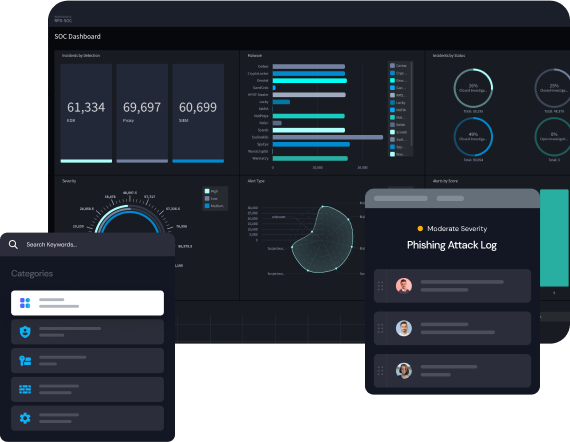
Force-Multiply Your Security Team Without Hiring
Do more with less. Swimlane Turbine enables SecOps teams to automate manual tasks to reduce hours of work down to seconds. Security leaders can free up analysts’ time to respond to threats and apply more focus to proactive defense measures.
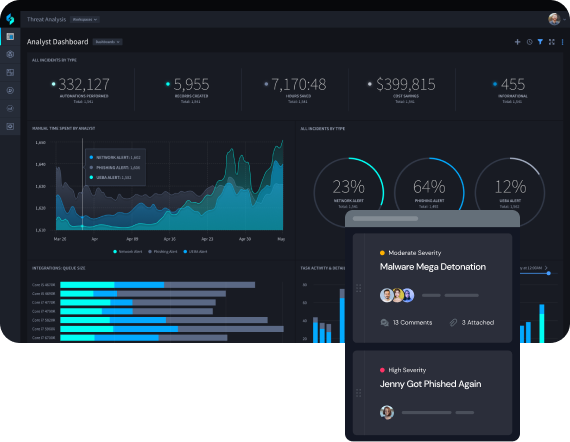
Reduce Incident Response Times by 90%
Bring in larger and broader data sets faster. Swimlane ingests data at the source for immediate action and faster response times, eliminating the wait from delayed data aggregation.
Explore Swimlane Turbine
The world’s most capable security automation platform and security system of record.