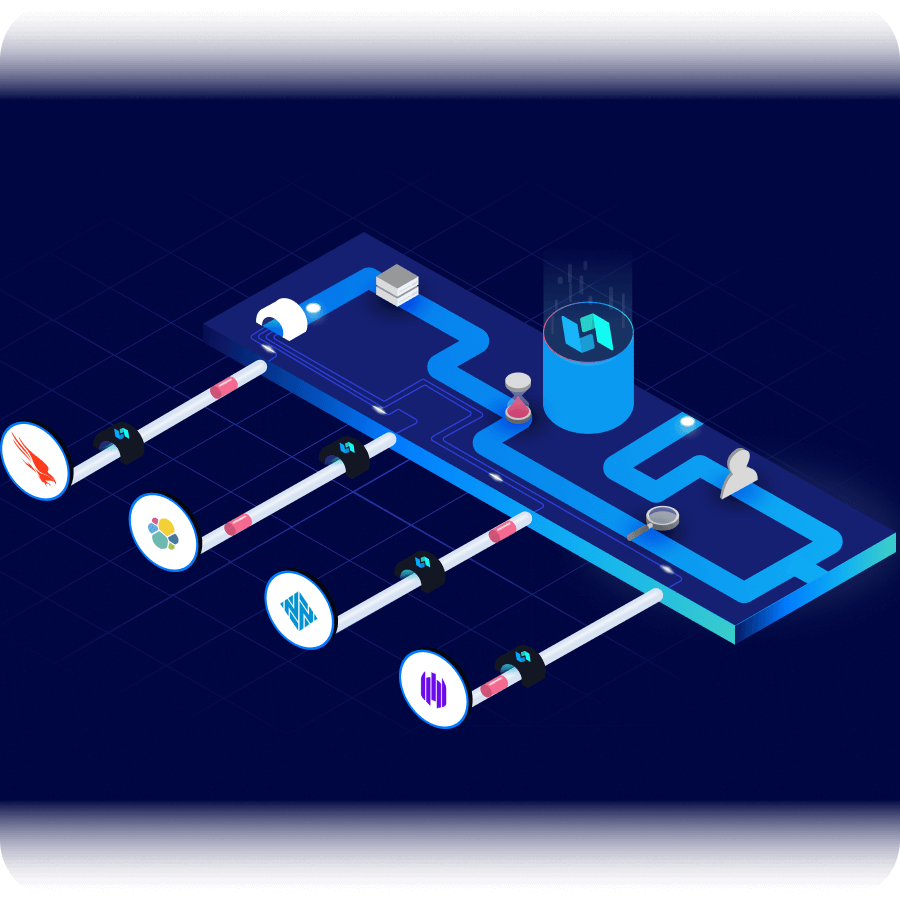
Why Automate Breach Prevention?
As security teams strive for better ways to defend their organizations, attackers find new ways to break through those defenses. Whether it’s traditional attacks like phishing, or incidents beyond the SOC like fraud and insider threats, the frequency and sophistication of attacks increases – and so do the alerts. Analysts are already busy monitoring up to 10,000 alerts a day, with zero room for error. Your team needs a solution to triage the growing deluge of alerts, quickly identify false positives, and respond to threats faster.
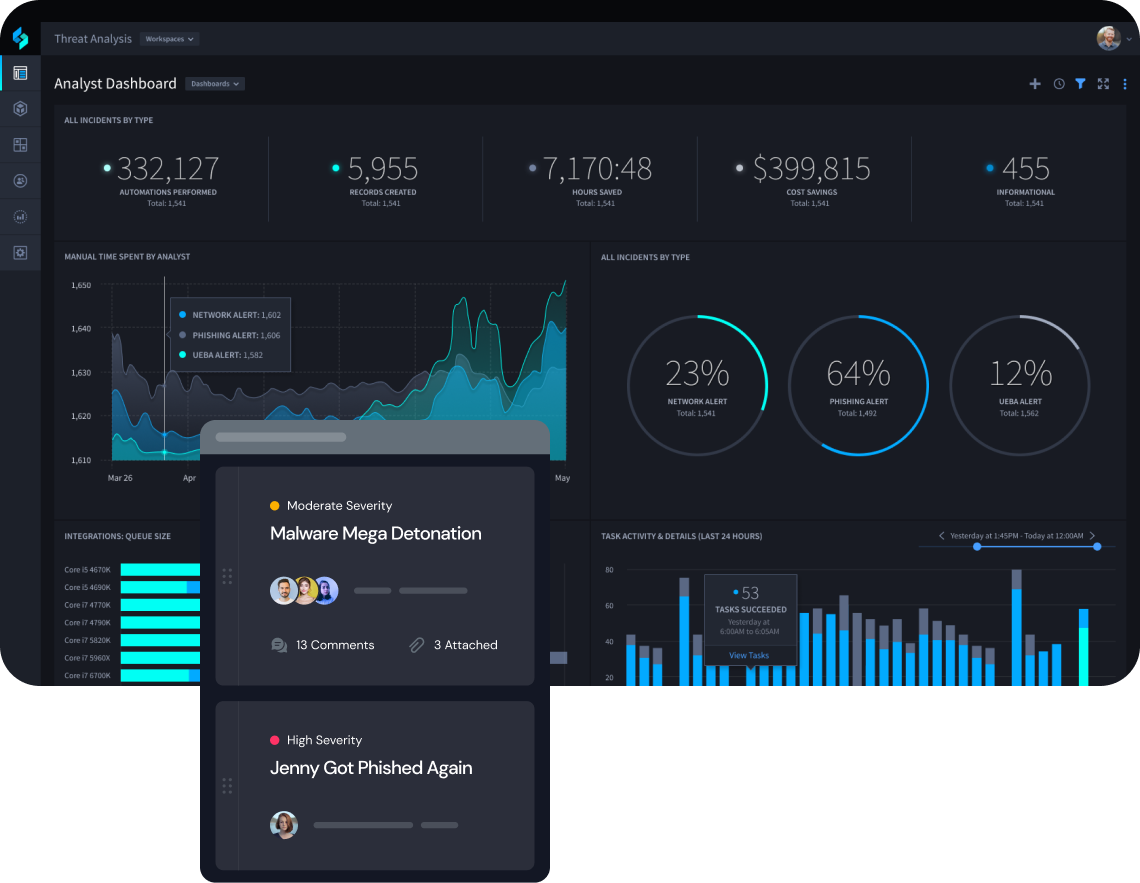
Automate 70% of SecOps Tasks
Automatically detect, identify and respond to threats in real-time. Reduce human error and empower your analysts to focus on complex, high-level threats.
Reduce MTTD and MTTR by 50%
Speed security performance with automated incident response both in and beyond the SOC. Minimize the time required to filter, sort and visualize data.
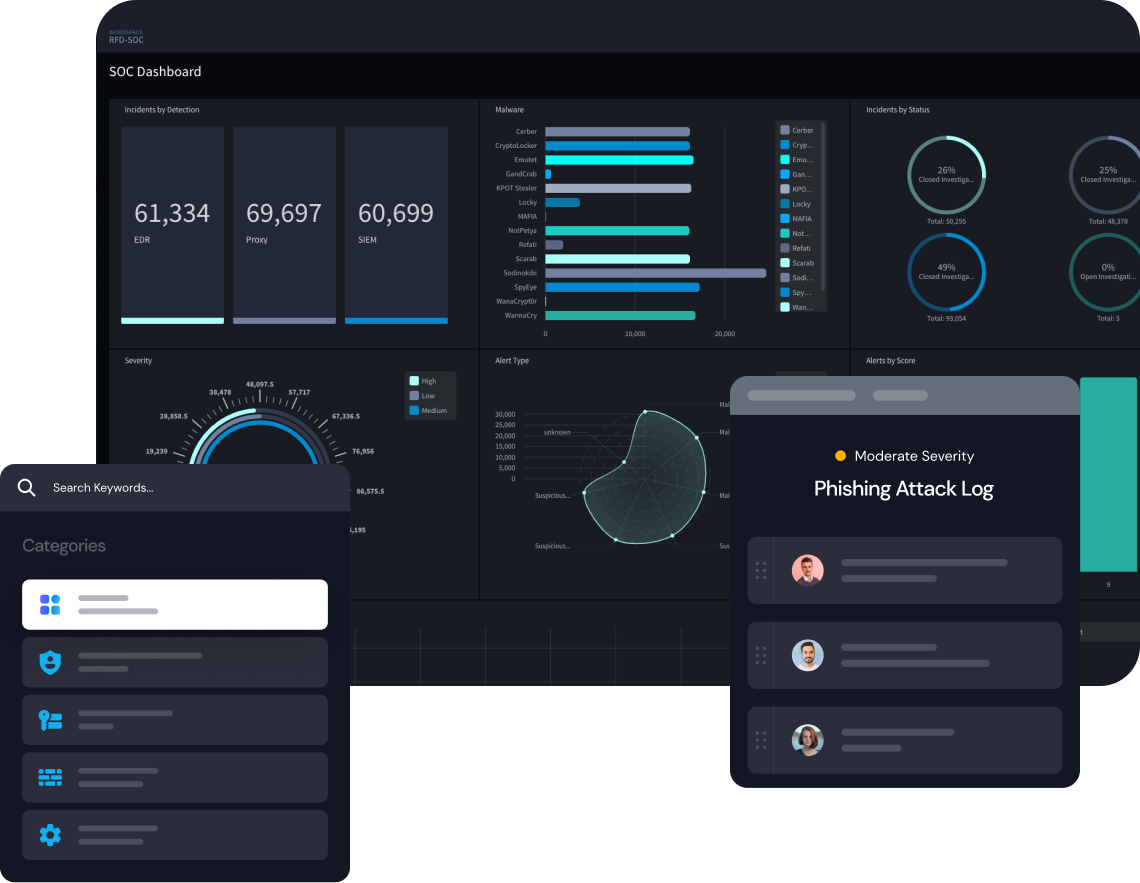
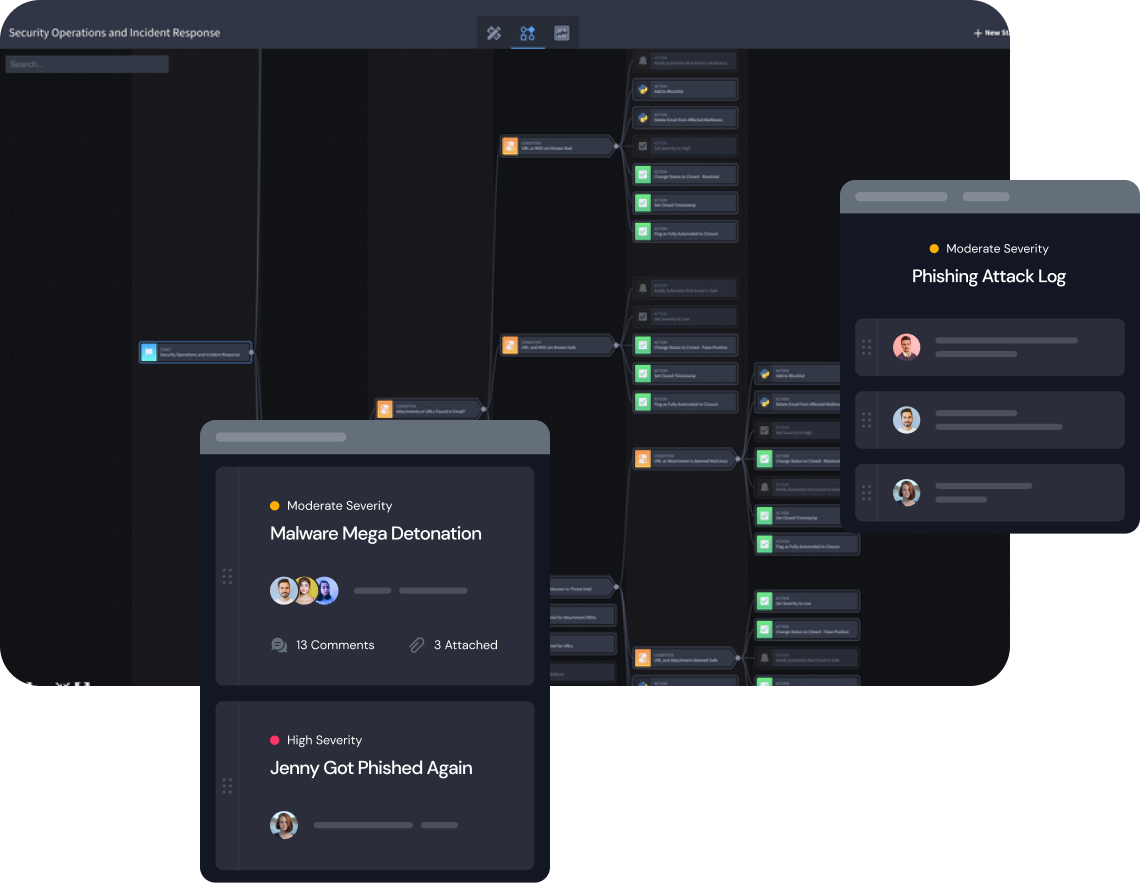
Increase SecOps Actionability by 20x
Save time on investigations with robust case management that organizes incident data. Autonomous integrations provide the necessary connection points you need to understand and defend against attacks no matter where they originate.
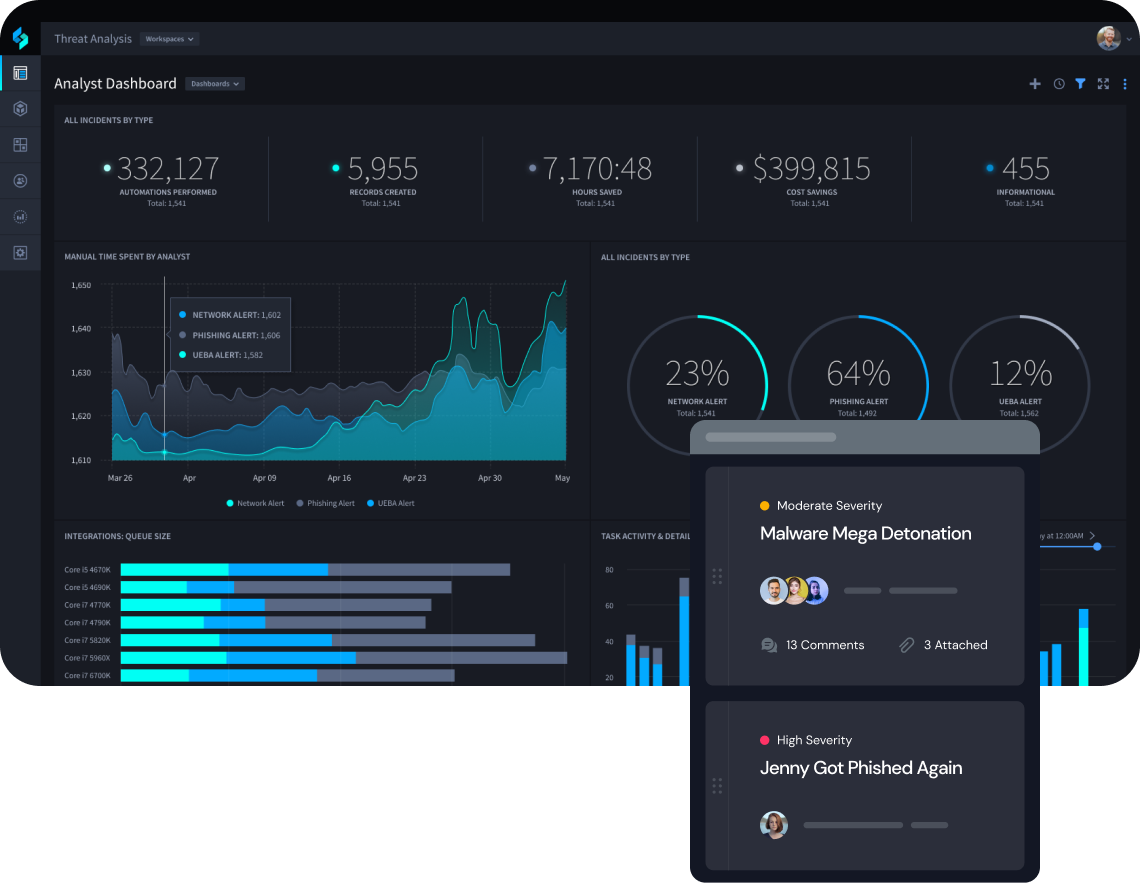
Build Playbooks in Half the Time
Quickly create playbooks that take action in real-time in conjunction with Swimlane’s robust case management system. Best practices and business logic are built in to avoid errors and save analysts time.
Ready to Get Started?