are prepared for Zero Trust
%
Not all federal agencies are prepared to meet the U.S. government Zero Trust requirements.
Rely on low-code security automation
%
Many federal agencies have the tools in place to help them to meet all the criteria of implementing Zero Trust.
Deployment models with feature-parody
models
Complete deployment control. From on-premises to air-gapped or cloud-native Swimlane is full-featured.
Comply with the zero trust mandate
The Biden Administration executive order M-21-31 states that security automation orchestration and response (SOAR) is required in order to comply with the 2024 zero trust mandiate. More than half of federal agencies already use low-code security automation in order to implement zero trust and comply with federal regulatory requirements.
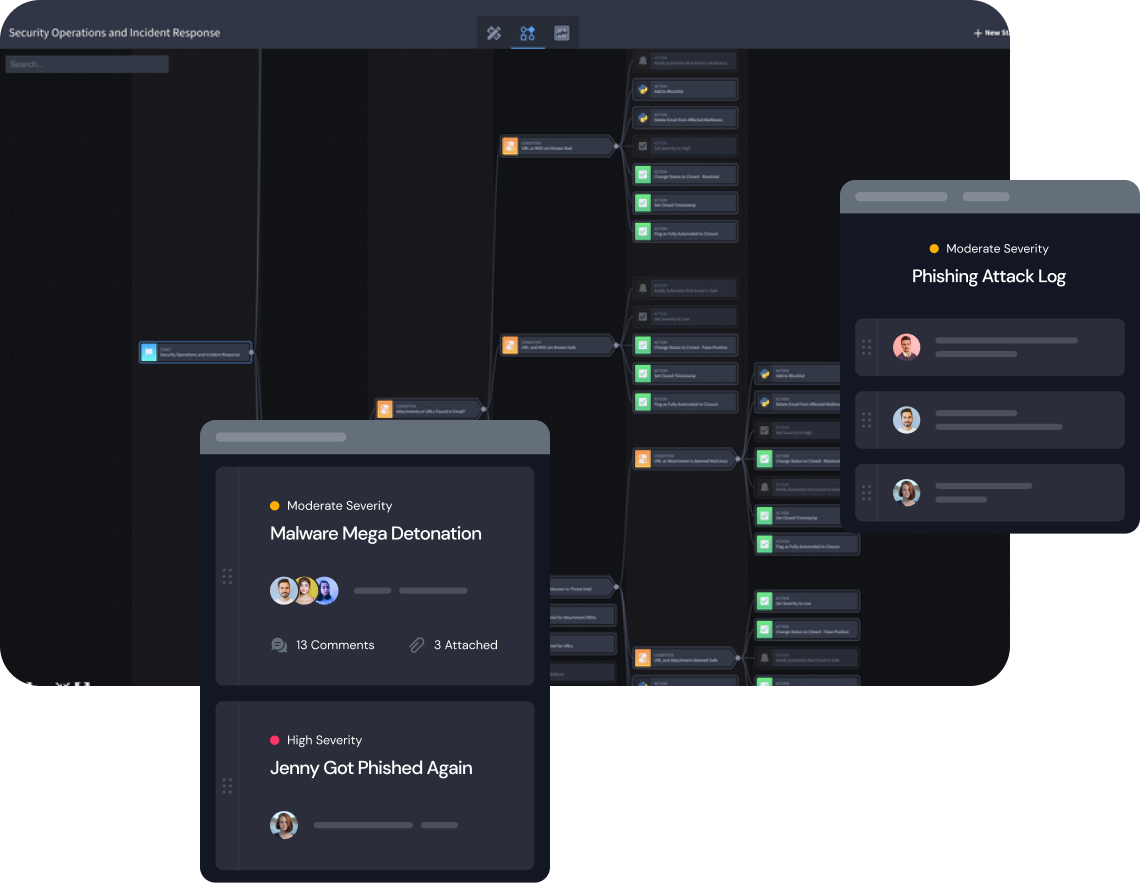
Strengthen defenses against nation-state attacks
Governments across the world are often the targets of advanced persistent threats (APT) and nation-state actors. The Cybersecurity and Infrastructure Security Agency (CISA) offers open-source intelligence to help organizations defend against malicious state-sponsored adversaries. Many federal agencies rely on security automation platforms to integrate and orchestrate their defenses against these sophisticated attacks.
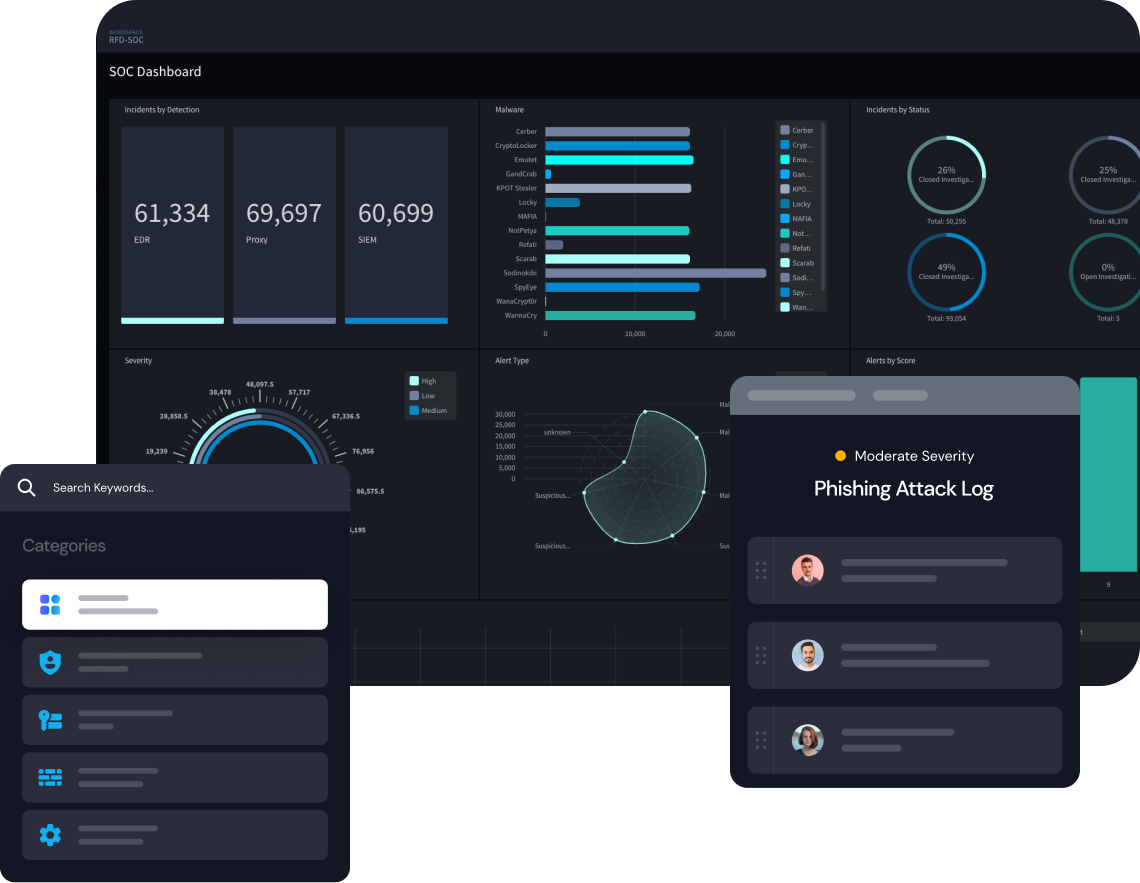
Recruit, retain and enhance security talent
35% of federal agencies believe they will never have a fully-staffed security team with the proper skills. That’s why federal agencies are levering low-code security to “lighten the load” of implementing the SOAR component of the executive order. Once implemented, security teams benefit from the efficiencies and scale that security automation offers.
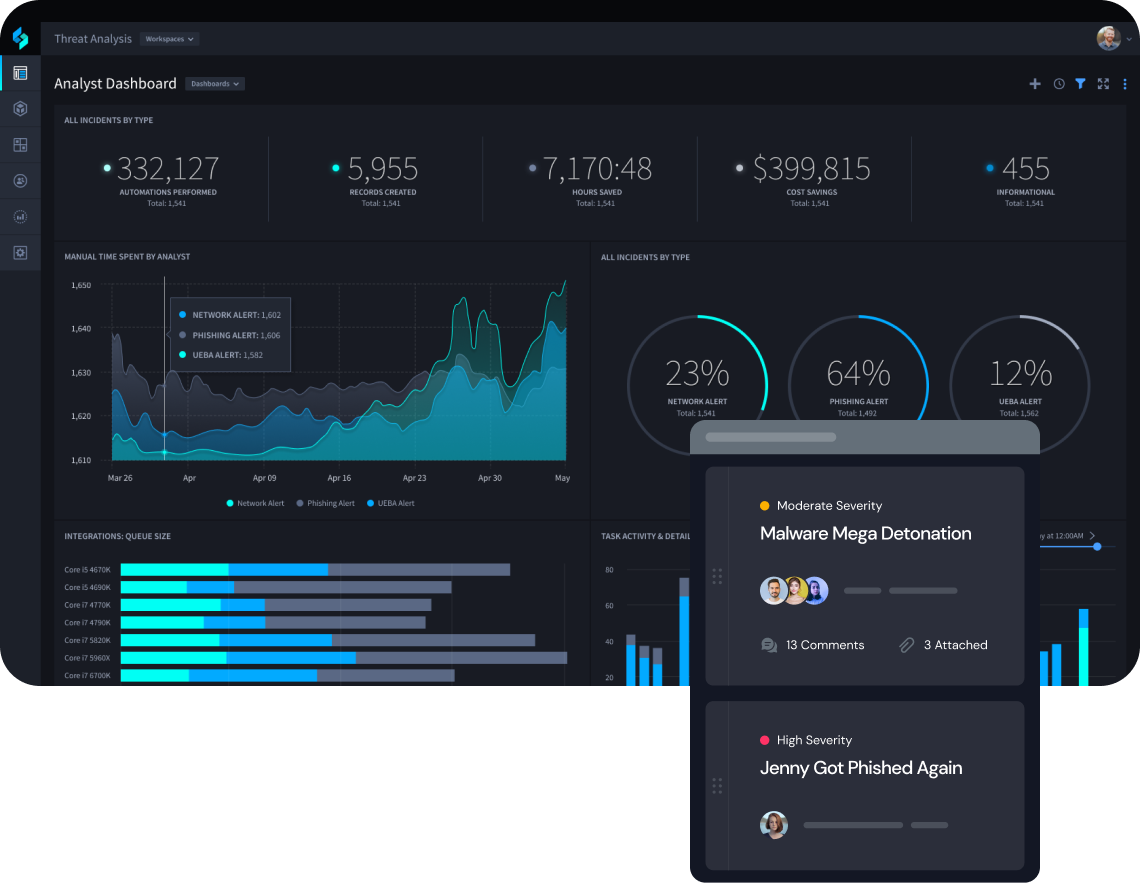
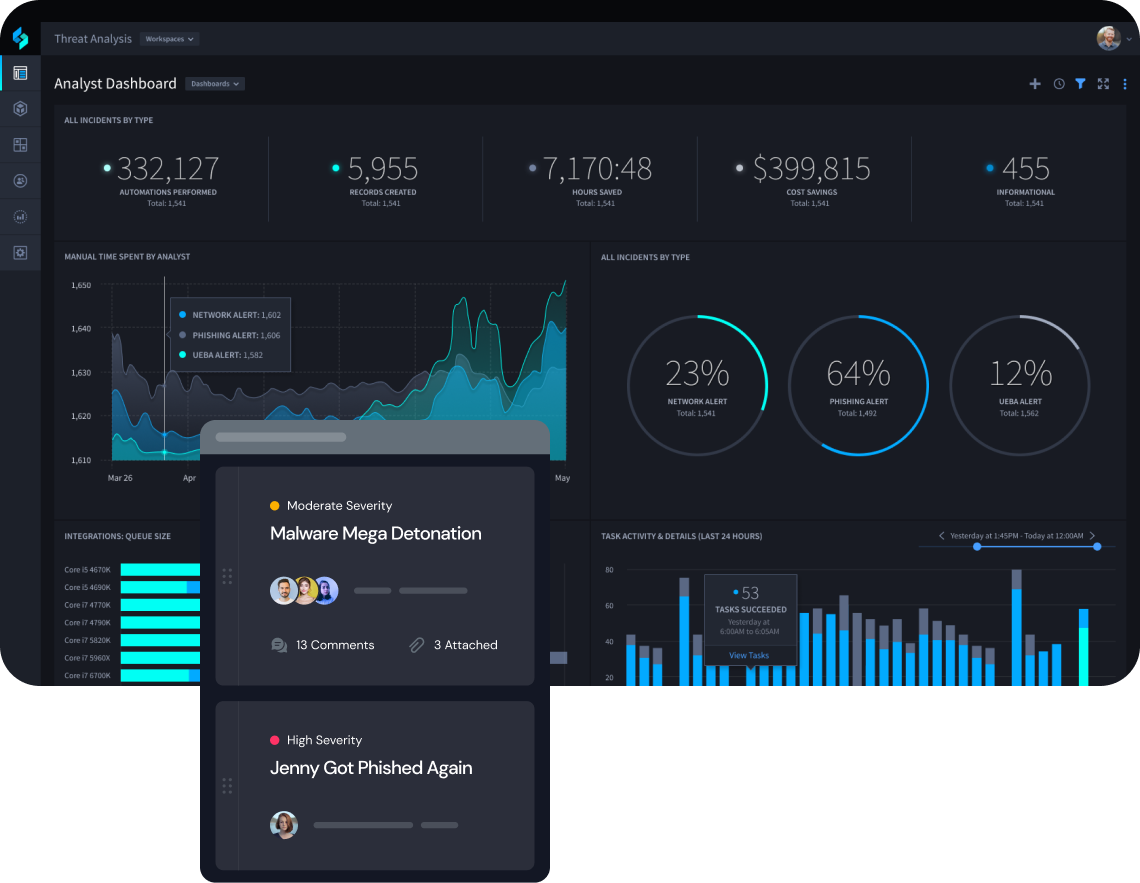
Gain intelligence-driven security insights
Integrate disparate security technologies into a single automation pipeline to gain visibility. Robust case management with customizable dashboards and reporting enable fast, precise decision making for public sector cybersecurity teams.
Case Study: US Gov Agency Security
An in-depth analysis of a a large managed security services provider (MSSP) with several 24/7 security operations centers (SOCs) located around the world that faced the common challenge of scaling a growing number of customers with limited analyst headcount and how they addressed the challenge with Swimlane’s security automation platform.
Explore Swimlane Turbine
The world’s most capable security automation platform