Security incidents
Billion
are caused by phishing attacks on an annual basis.
Dollars lost globally
Trillion
is an estimate of the annual financial losses from phishing.
Manual triage time
mins
Is how much time analysts waste when automation isn’t used for phishing.
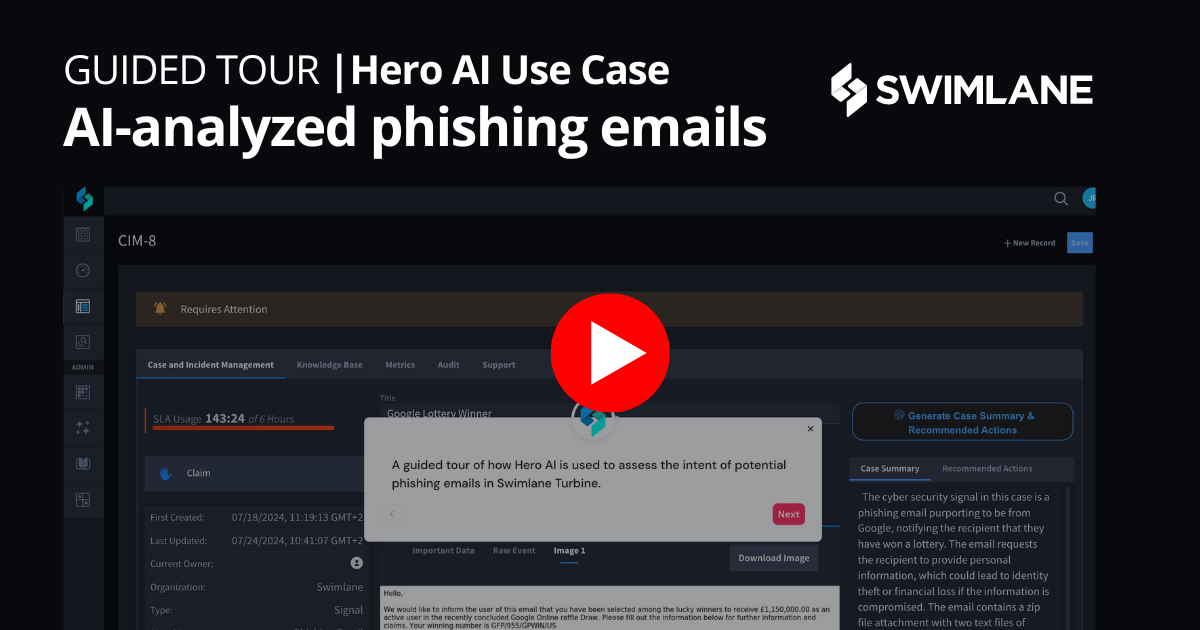
Stop Threats in Real-time
False positives are far too common. They lead to human error and alert fatigue over time. With Swimlane, security teams can build entirely automated workflows to block phishing attempts and filter false positives automatically.
Save Analysts Time
Automatically investigate and quarantine phishing emails so analysts don’t have to. This shifts their time from administrative, repetitive, and error-prone tasks, to strategic work like running investigations and case management.
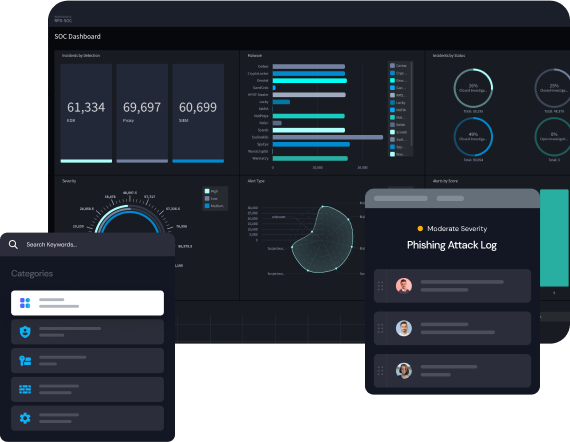
Improve Incident Response
Utilize automated incident response workflows and playbooks to consistently execute when phishing attempts occur. Swimlane Turbine improves phishing MTTR by rapidly sifting through the noise of false positives.
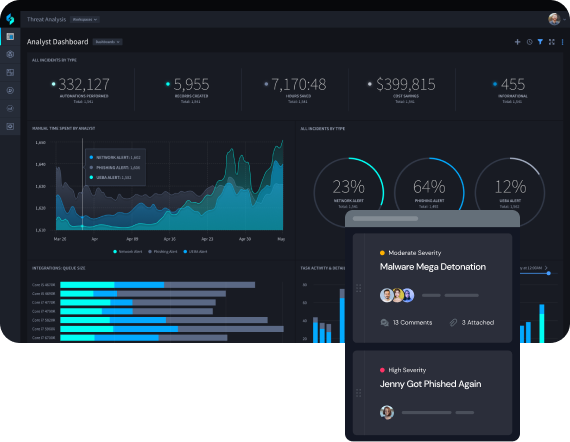
Customize Reporting on Response
Extensive, fully-customizable reporting allow analysts and security executives to illustrate efficiency gains and celebrate increased resilience.
Swimlane Transforms The DIGs Phishing Defense
Don’t take our word for it. Swimlane customer, The Digital Investigative Group (DIG) is a managed security service provider (MSSP) who transformed their phishing defense with Swimlane. Phishing was the number one attack vector for the DIG’s customers.
FEATURES
Address Phishing with Swimlane Turbine
The world’s most capable security automation platform