of companies experienced a physical security breach.
%
Robbery, the use of counterfeit money, and natural disasters are all forms of physical vulnerabilities.
average cost of an exploited physical asset
$
With security automation, SecOps teams can quickly act when alerted to physical vulnerability.
risk monitoring
Real-Time
Gain critical visibility throughout Swimlane Turbine’s reporting, investigation, and response.
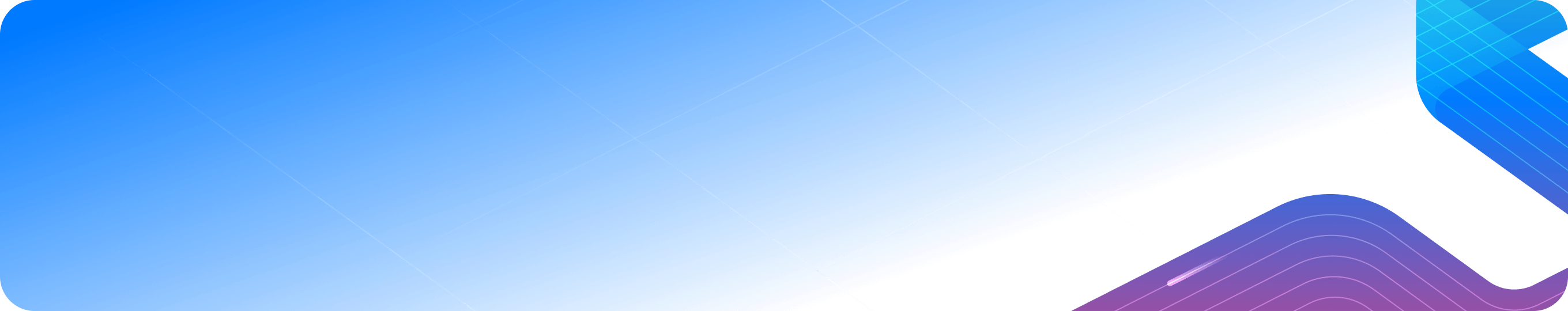
Protect Physical Assets
Respond to physical risks in near real-time through either a fully-automated response, or via a single-click triage action when human-in-the-loop interaction is required, compressing the mean-time-to-detect (MTTD) and mean-time-to-respond (MTTR).
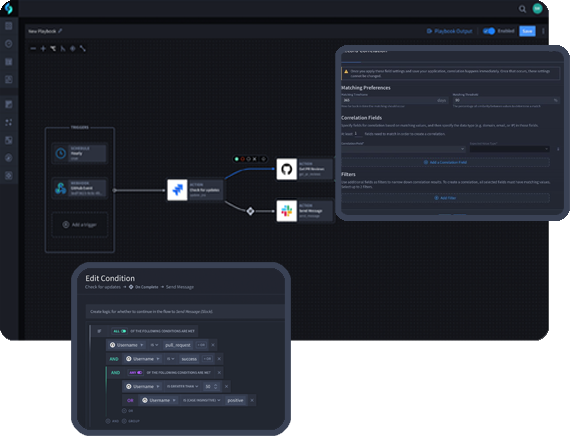
Ensure Asset Compliance and Defense
A complete and autonomous process can be deployed utilizing Swimlane to reduce attack surface for would-be attackers and support compliance reporting.
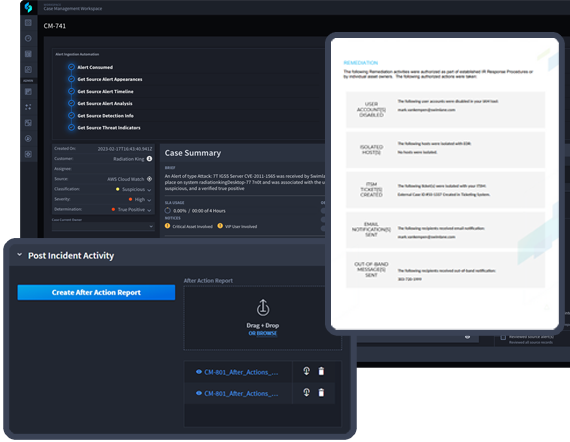
Enable Smooth Physico-Cyber Convergence
Swimlane platform serves as a centralized management hub system of record to provide increased visibility across physical and cyber assets.
Address Physical Security with Swimlane Turbine
The world’s most capable security automation platform