Monitoring, Evaluating, and Responding to Credential Dumps
Across the many ways users can leverage Swimlane and Recorded Future products together, there are many unique and powerful use cases that can be implemented. Monitoring identity exposure is one new use case worth highlighting.
First things first, you’ll need Swimlane and Recorded Future’s new Identity Intelligence Module offering. This feature is designed to provide users with the latest credential dump information from around the web. Using Recorded Future’s proprietary sources, users can be notified anytime their information is found in a new credential dump. This is incredibly important because an unknown credential leak could cause havoc in the wrong hands. Recorded Future’s new Identity Intelligence Module offers analysts all of the information they need to proactively prevent bad guys from finding active credentials.
Swimlane and Recorded Future teamed up to speed the time to remediate compromised credentials through low-code automation, and recently co-hosted a webinar on the topic together. It goes without saying that responding to alerts of compromised credentials is a time sensitive process. Our goal for joint customers is to enable the analyst to transfer as much of the process as possible to Swimlane’s low-code automated workflows. As a result, automated use cases like this will help analysts speed the mean time to and free their time for more strategic security tasks..
Let’s see how it works
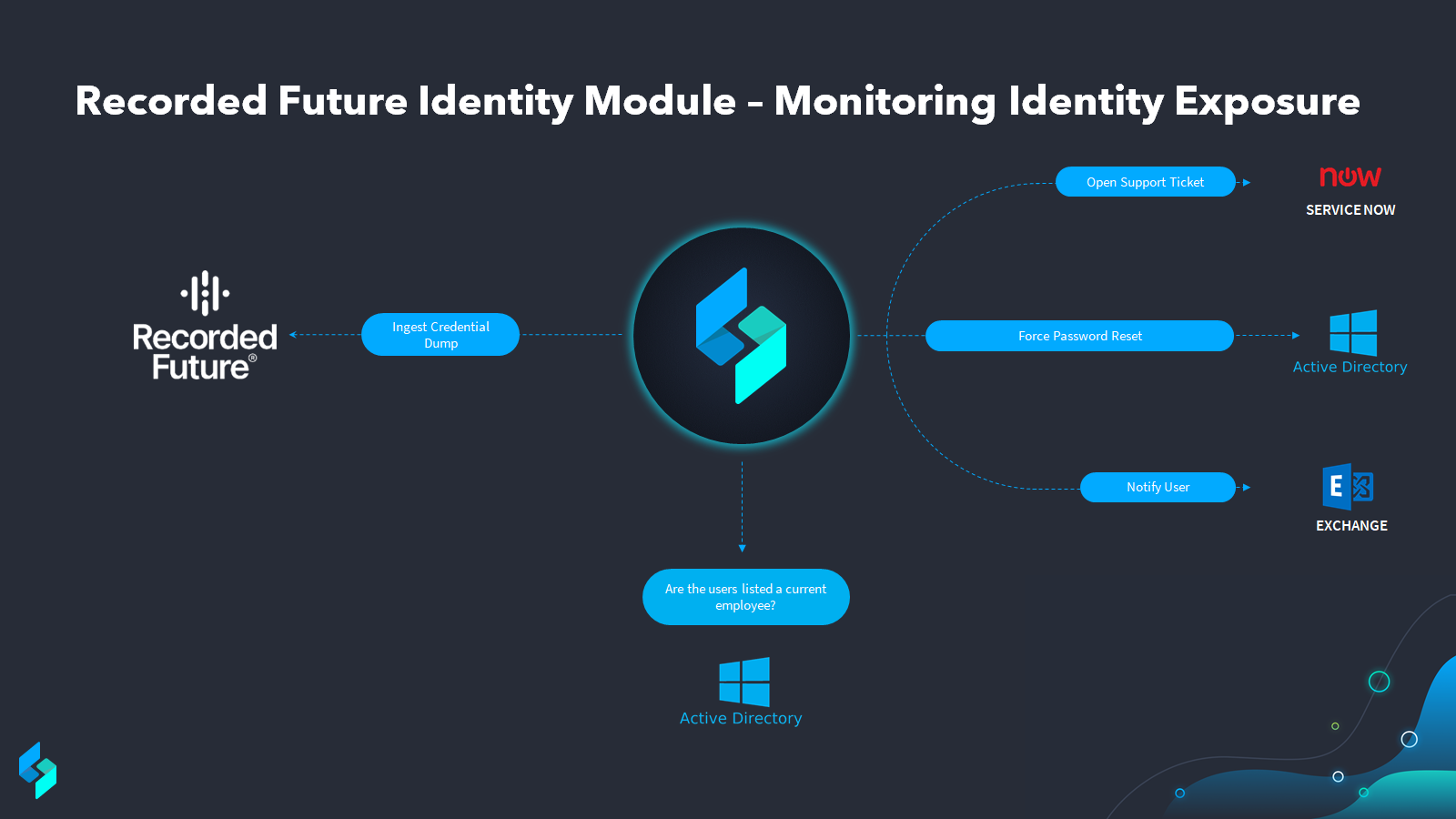
The use case graphic above displays the general flow of how these credentials dumps can be automated. For a more detailed break explanation, we have broken the use case down into 4 simple steps.
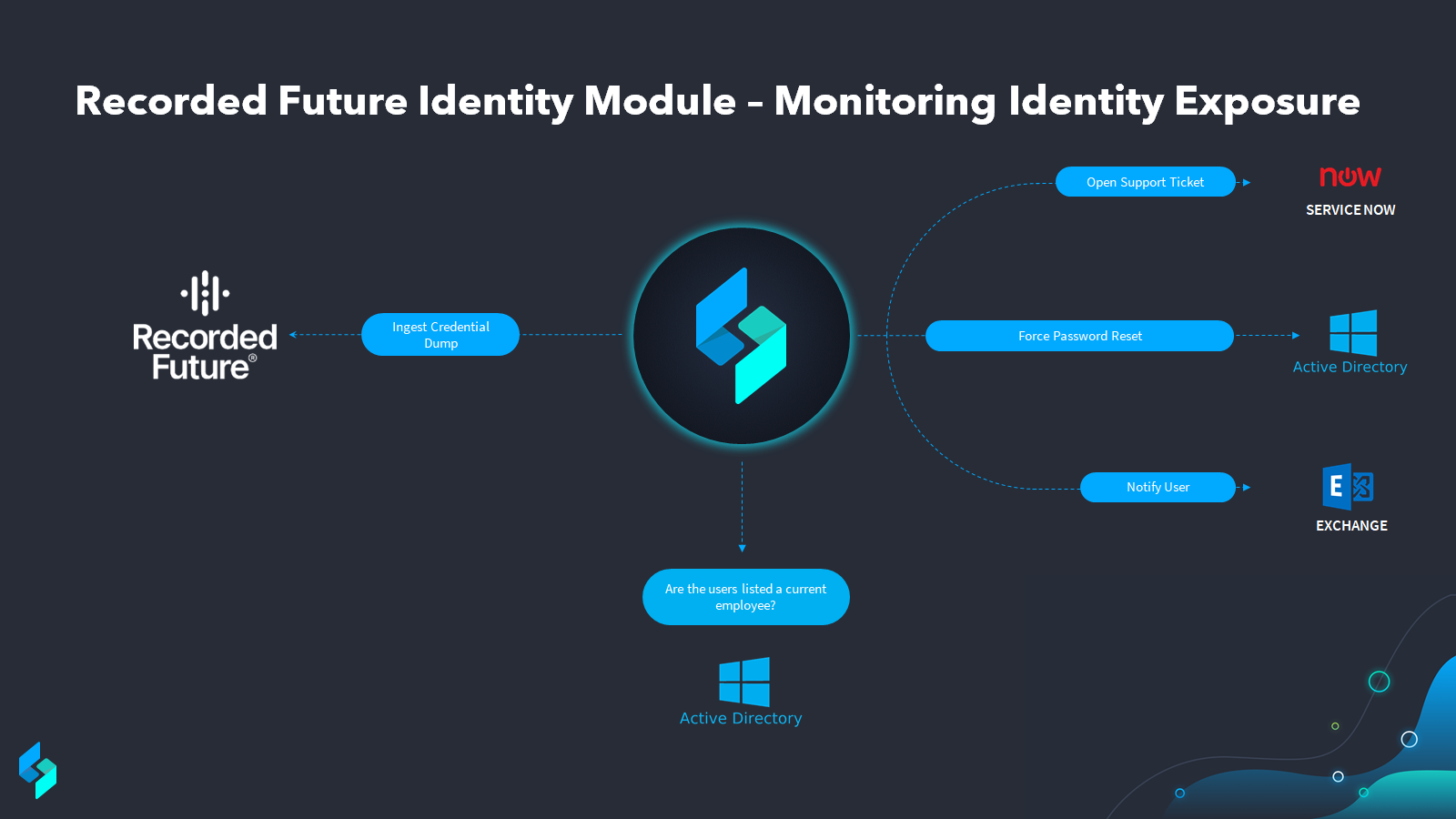
Recorded Future Identifies a Credential Dump:Our workflow begins when Recorded Future’s Identity Module picks up a new credential dump from any of its many sources for the domain we have asked it to monitor.
Recorded Future sends detected credentials to Swimlane: This credential dump list is then ingested into Swimlane automatically on a timed basis. Once Swimlane has ingested, it will automatically create a record for each and kick off the enrichment process.
Swimlane enriches the threat intelligence:With the list now in hand and knowing they are all for the right company domain, we can now start to check the list against Active Directory or another directory tool to ensure we are looking at just the credentials for our current employees. For all others, the automation can kick off actions to ensure those credentials are already de-authorized.
Analysts receive actionable intelligence and deprecate exposed credentials: Once we have narrowed to just our active employees who showed up in the credential dump, analysts can then leverage Swimlane automation in a few different ways depending on what works best for their organization. The simplest way would be to force password resets across all of the current employees who appear on the credential dump list like in the diagram shown above. This will ensure all of the credentials exposed are deauthorized no matter who should find them. When configured this way, the entire use case can be automated. For those seeking to investigate the exposed credentials a bit deeper to ensure they are not old passwords of current employees, rainbow tables can be leveraged to get down to the individual hash level.
Low-Code Security Automation Outcomes
Across all of the area’s automation can be used within this use case, time saving really adds up across the use case lifecycle making this a much more manageable task for security teams. All enrichment and actions can be done right from within the Swimlane platform, so time normally spent jumping in and out of a number of tools to further investigate or take action is fully optimized. As more and more of these credential dumps make it to the web:
To learn more about this integration register for our upcoming webinar!
Swimlane Turbine
Schedule a Swimlane Turbine live demonstration with our experts! Learn how our AI-enabled security automation platform can help you solve the most challenging problems across your entire security organization.