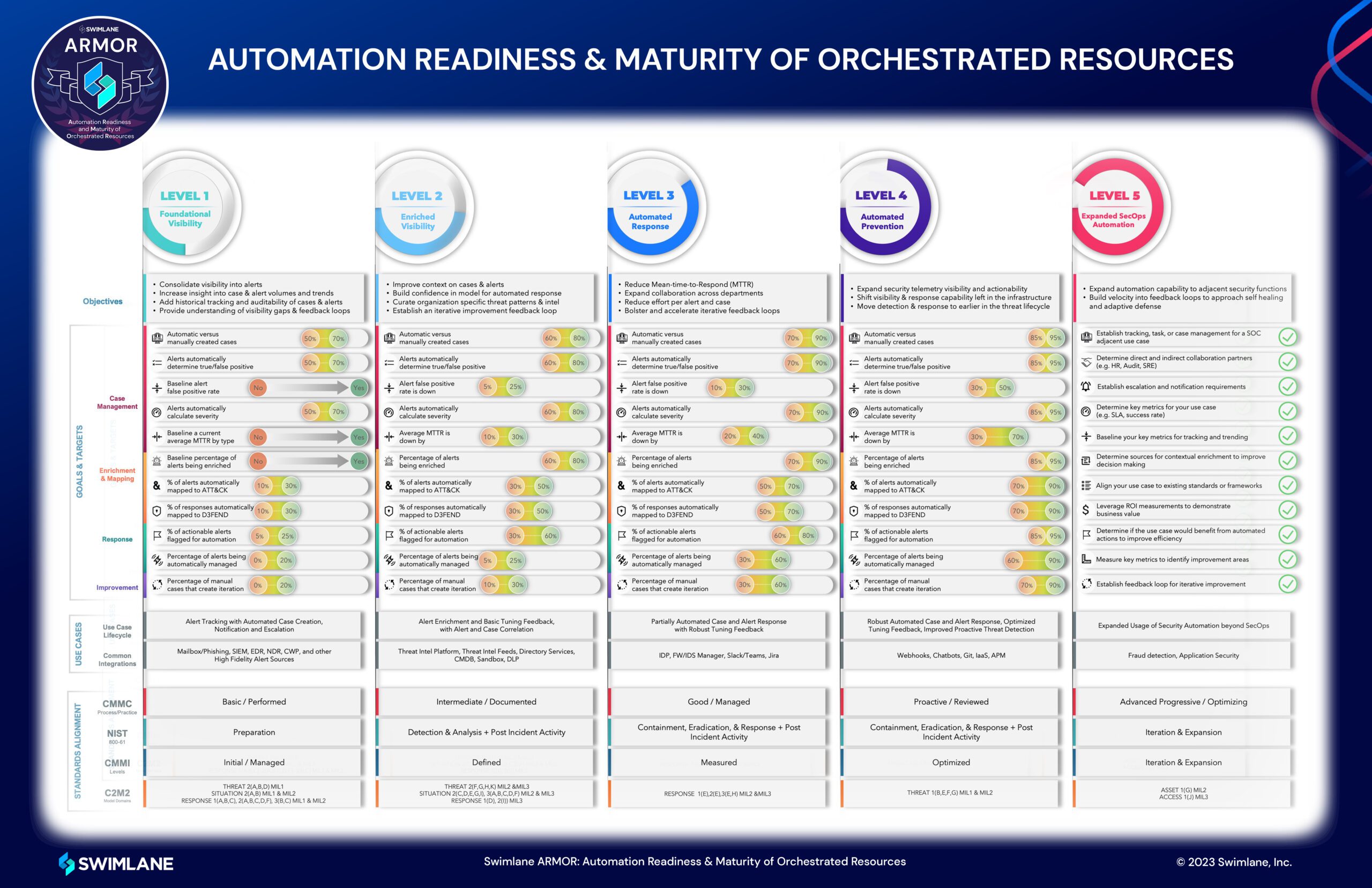
Automation Readiness & Maturity of Orchestrated Resources (ARMOR)
Global Cyber Threat Readiness Report reveals alarming misalignment between execs and security analysts. To help pave the way forward, organizations can follow the ARMOR Framework.
Contact us Now.
of executives across the globe believe all alerts are being handled.
%
of organizations are actually addressing every single alert.
%
of organizations that handle every alert use low-code security automation.
%
Automation Benchmark
Compare Your Security Posture in Real Time
- What stakeholders are engaged in your security automation program?
- How do you manage Service Level Agreements (SLA’s) and performance metrics?
- To what extent do you use automation for visibility into your security posture and performance?
- What is the current automation level of your processes?
- Which security tools do you have in place currently? (Check all that apply)
- What stakeholders are engaged in your security automation program?
-
No one 0%
-
The Security Operations Center (SOC) team 0%
-
The SOC and adjacent departments (ex. IT, DevOps, HR, Legal) 0%
-
Complete company-wide engagement 0%
-
- How do you manage Service Level Agreements (SLA’s) and performance metrics?
-
SLAs and metrics are not defined 0%
-
SLAs and metrics are tracked by each individual security tool 0%
-
SLAs and metrics are tracked from a central location 0%
-
SLAs and metrics are centrally tracked with customizable dashboards & reports 0%
-
- To what extent do you use automation for visibility into your security posture and performance?
-
Not at all 0%
-
Inconsistently applied 0%
-
Fully integrated and aligned to goals 0%
-
Fully integrated and continuously optimized for maximum results 0%
-
- What is the current automation level of your processes?
-
100% Manual 0%
-
Minimal automation (<20%) 0%
-
Moderate automation (20-60%) 0%
-
Majority automated (>60%) 0%
-
- Which security tools do you have in place currently? (Check all that apply)
-
Network Security (FW, IDS/IPS, NDR, WAF) 0%
-
Endpoint Detection Response (EDR) or Endpoint Protection Platform (EPP) 0%
-
Security Information Event Management (SIEM) 0%
-
Data Loss Prevention (DLP) 0%
-





What stakeholders are engaged in your security automation program?
- No one
- The Security Operations Center (SOC) team
- The SOC and adjacent departments (ex. IT, DevOps, HR, Legal)
- Complete company-wide engagement
- No one
- The Security Operations Center (SOC) team
- The SOC and adjacent departments (ex. IT, DevOps, HR, Legal)
- Complete company-wide engagement
How do you manage Service Level Agreements (SLA’s) and performance metrics?
- SLAs and metrics are not defined
- SLAs and metrics are tracked by each individual security tool
- SLAs and metrics are tracked from a central location
- SLAs and metrics are centrally tracked with customizable dashboards & reports
- SLAs and metrics are not defined
- SLAs and metrics are tracked by each individual security tool
- SLAs and metrics are tracked from a central location
- SLAs and metrics are centrally tracked with customizable dashboards & reports
To what extent do you use automation for visibility into your security posture and performance?
- Not at all
- Inconsistently applied
- Fully integrated and aligned to goals
- Fully integrated and continuously optimized for maximum results
- Not at all
- Inconsistently applied
- Fully integrated and aligned to goals
- Fully integrated and continuously optimized for maximum results
What is the current automation level of your processes?
- 100% Manual
- Minimal automation (<20%)
- Moderate automation (20-60%)
- Majority automated (>60%)
- 100% Manual
- Minimal automation (<20%)
- Moderate automation (20-60%)
- Majority automated (>60%)
Which security tools do you have in place currently? (Check all that apply)
- Network Security (FW, IDS/IPS, NDR, WAF)
- Endpoint Detection Response (EDR) or Endpoint Protection Platform (EPP)
- Security Information Event Management (SIEM)
- Data Loss Prevention (DLP)
- Network Security (FW, IDS/IPS, NDR, WAF)
- Endpoint Detection Response (EDR) or Endpoint Protection Platform (EPP)
- Security Information Event Management (SIEM)
- Data Loss Prevention (DLP)
ARMOR Assessment
Many organizations are overwhelmed by the people, processes and technology that go into automating security processes. Discover your company’s individualized security automation maturity level with our ARMOR Assessment. Take the assessment to receive a personalized report with recommendations for how to advance your security automation.
About the Methodology
People
Measure your team’s acumen for security tools and coding skills in place at your organization.
Process
Discover how well your organization has defined and implemented company wide processes and policies.
Technology
Learn how to enhance your current automation use cases in order to prevent business-ending threats.