When you hear the word “armor” images of warriors in protective gear, defending medieval kingdoms might come to mind. But here at Swimlane, “armor” has a different meaning. It stands for automation readiness and maturity of orchestrated resources. In the age of cyber-warfare, security automation is the key to survival. The Swimlane ARMOR framework is a first-of-its-kind resource for organizations who want to leverage automation to enhance their cyber threat readiness. If your SOC team is currently struggling to combat alerts in real time or shield itself from sophisticated threat actors, then it’s time for ARMOR.
Introducing The Swimlane ARMOR Framework
The security industry has many threat detection and incident response (TDIR)
centric maturity models, like MITRE ATT&CK, MITRE D3FEND, and NIST, but there isn’t a well-defined path for how automation should be applied in order to operationalize these approaches…until now. The Swimlane ARMOR framework was built on a decade of lessons learned, institutional knowledge and best practices from our most successful customers. The framework includes two components; a readiness assessment and a maturity matrix.
Level Up the ARMOR Framework
“Always be leveling up” is one of our core values at Swimlane, and we want to share this mindset with you. The ARMOR Framework is a five-tiered model that is designed to act as a roadmap for how to “level up” security automation outcomes. It provides resources and best practices to help you get to the next level. The ARMOR framework levels are:
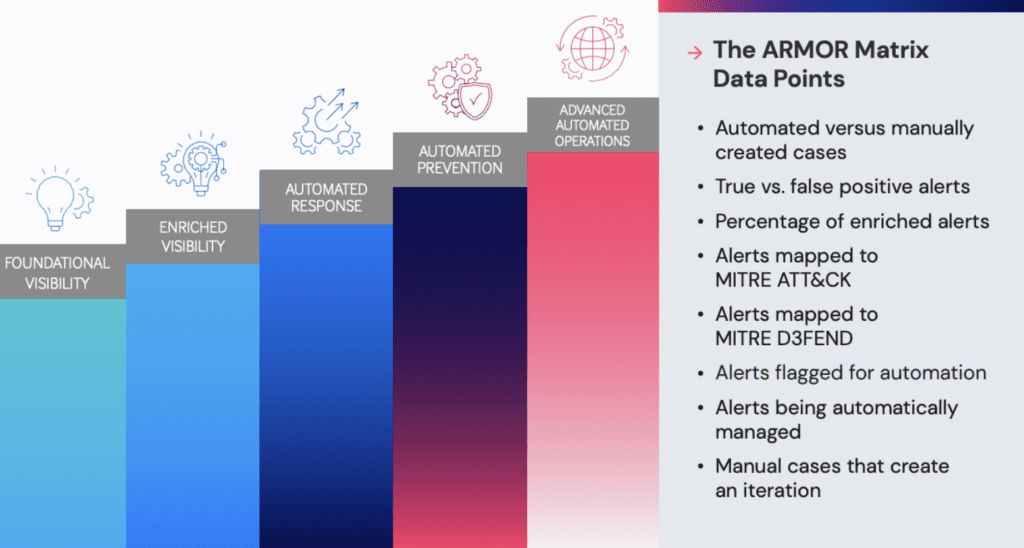
Level 1: Foundational Visibility
This means that you have low process maturity, minimal automation, low coding capability and limited log consolidation.
Level 2: Enriched Visibility
This means that you have defined some processes and have attempted to automate simple tasks. Your team has low to medium coding capability and has consolidated some logs.
Level 3: Automated Response
At this point, most of your processes are defined and you use automation where possible. Your team has medium coding skills. Security logs, events, and alerts are well consolidated.
Level 4: Automated Prevention
Your organization has well defined processes & policies. You take an automation first approach. Your team has mature coding skills and has already consolidated all logs, events and alerts.
Level 5: Advanced Automated Operations
Now, your organization is in a state of continuous improvement. Your team leverages advanced coding practices for intelligent automation and proactive threat detection and response.
The Assessment
The first step to getting started with the ARMOR framework is the assessment. It asks 20 people, process and technology related questions to evaluate your organization’s security automation program maturity. After you’ve taken 5 minutes to complete the assessment, you’ll get a summary of your results and one of our automation experts will reach out to schedule a 30 minute consultative session to review your results.
The Matrix
The ARMOR matrix is for organizations who have already implemented a security automation platform. It uses various data points to gauge the effectiveness of your technology capabilities and controls. The ARMOR matrix measures:
- Automated versus Manually created cases
- True vs. False Positive Alerts Percentage of Enriched Alerts
- Alerts Mapped to MITRE ATT&CK
- Alerts Mapped to MITRE D3FEND
- Alerts Flagged for Automation
- Alerts Being Automatically Managed
- Manual Cases That Create an Iteration
What Does Your Cybersecurity ARMOR Look Like?
Remember, you can’t improve what you can’t measure. That’s where the ARMOR framework steps in, providing the structure, guidance, and best practices you need to track, measure, and enhance automation outcomes over time. Building a security automation program on your own might take ages, but with Swimlane’s you’ll enter into today’s cyber warfare with the best ARMOR.
So now I ask you this, what does your security ARMOR look like? Take the ARMOR Assessment to find out and level up.

