Use security automation to simplify security processes and protect future profits.
The growing threat landscape has made organizations rethink the way they handle business processes like onboarding and offboarding. These processes can be tedious and time-consuming for an enterprise – and the risk is real. Insider threats from disgruntled departing employees are more than an IT issue. They’re a business issue.
And enterprise leaders see the importance of cybersecurity in situations like onboarding and offboarding. According to a recent survey:
“Eighty-eight percent of Boards of Directors (BoDs) view cybersecurity as a business risk, as opposed to a technology risk.”
It’s no longer enough to secure your technology, now your team needs to secure the processes around that technology.
That’s why enterprise security teams are turning to automation. With automation, you can streamline repetitive tasks and dive deeper into complex security alerts. We’re already seeing its widespread adoption, especially in cases outside of the security operations center (SOC).
Continue reading to learn how your team can utilize security automation platforms to improve employee onboarding and offboarding.
What is Onboarding Automation? Offboarding Automation?
Onboarding automation is used to streamline necessary tasks and documentation that happen when an employee starts working at your company. This includes creating accounts, setting up email software, configuring the right permissions, and even creating access badges for building entrances. The goal of automating the onboarding process is to make sure every new hire gets set up as efficiently and securely as possible.
On the flip side of the coin, offboarding automation speeds the exit process when an employee leaves. Accounts need to be locked, access restricted and data protected. Offboarding automation protects enterprise data from being leaked, whether intentionally or unintentionally. Automating the offboarding process is a surefire way to ensure all loose ends are tied up with exiting employees.
Manual Security vs Automated Onboarding/Offboarding
When your team manually approaches onboarding and offboarding, the chance for human error grows. Gaps in the employee offboarding process – caused by limited visibility, manual processes, and weak access controls – leave enterprises at risk of a data leak. This risk can have a detrimental impact when employees with elevated access credentials leave the organization, or when they move to competitive companies.
Some common challenges from manual onboarding/offboarding include:
-
Increased risk of human error
-
Delayed response when an employee departs
-
Lack of visibility into the employee’s access and permissions
-
Higher chance of miscommunication among departments
Automating onboarding and offboarding look completely different. You can include your HR system in the automation loop so the security team is aware of new and departing employees. When an employee leaves, it triggers a set of processes and access controls to prevent data leaks.
SOC analysts gain visibility into what applications and systems departing employees have access to. Access can be automatically revoked as part of the offboarding checklist.
In the event of a disgruntled employee, low-code automation makes it easy to collaborate on insider threat use cases in real-time.
How to Use Security Automation for Onboarding & Offboarding
As soon as the offer letter is signed or the resignation letter received, it’s time for automation to kick in. A few key ways automation platforms help maximize the success of onboarding and offboarding include:
-
Includes HR stakeholders in the automation loop to know when an employee departs
-
See what applications or systems employees have access to
-
Automatically revoke access controls on the employee’s last day
-
Investigate and collaborate on insider threat cases
-
Build a system of record for all insider data risk
Benefits of Automated Onboarding & Offboarding
Low-code security automation platforms help SOC analysts by automating mundane, repetitive tasks. Security leaders can maximize the performance of their team without increasing workload or team size. Benefits also include:
-
Save More Time: 80-90% of employee onboarding and offboarding processes can be automated. SOC analysts can regain time spent on tedious, error-prone tasks to triage higher-level alerts.
-
Harness Institutional Knowledge to Reduce Risk: low-code security automation brings business intelligence to enrich data. Bring HR, legal, and managers into the automation loop to insert business logic that can prevent data leaks.
-
Protect Future Profits: Low-code security automation can be a system of record for security teams. Investigate insider risk and validate your security controls in one place. This helps prevent leaked source code, customer lists, and regulated data, which saves future profits.
-
Save Money with Automated De-Provisioning: Avoid the costly mistake of delayed de-provisioning of your SaaS tools. Automate IT off-boarding processes to make sure this manual step is never missed.
Low-Code Security Automation Tools for Onboarding/Offboarding
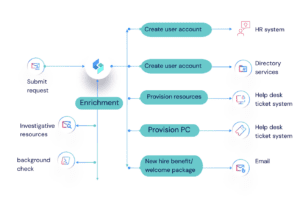
Looking to automate your security onboarding and offboarding processes? Low-code security automation is a strong choice. Swimlane Turbine combines the power of high-code and the accessibility of no-code for the best of both worlds. It’s a fierce security defense that empowers anyone to be an automator.

Top 13 Automation Use Cases for Your SOC and Beyond
Did someone say Automation Beyond the SOC? Yes, you heard that right! As attacks become more frequent and sophisticated, security teams require automation to mitigate alerts, unify telemetry sources, and enhance overall SecOps effectiveness. Automating use cases within and beyond the SOC helps organizations keep up with alerts and maximize their return on investment (ROI) for all their security technologies.


