Inside Our AI SOC: How Swimlane Cut MTTR in Half
At Swimlane, our Security Operations Center (SOC) isn’t just a defensive line; it’s our real-time innovation lab. We leverage this environment to push the boundaries of security operations (SecOps), unifying global cloud operations, enterprise IT, and risk & vulnerability management into a single, centralized program powered by the Swimlane Turbine agentic AI automation platform.
Inside our team’s operations, every alert, investigation, and resolution is an opportunity to refine our processes. With all our security workflows unified in Turbine, our analysts collaborate closely, experimenting with new processes and pushing AI capabilities to the limit. We are constantly asking: “How can we make this process faster, smarter, and more autonomous within Turbine?”
Before AI: Manual Steps and Repetitive Investigations
Before we centralized our operations on Turbine, our mean time to resolution (MTTR) hovered around six hours. Even as our automation and orchestration matured, my team still faced friction from manual triage steps, repetitive investigations, and context switching across disparate tools. We knew we had a ceiling we needed to break through.
Our Journey to a More Autonomous SOC
Between 2021 and 2025, our SOC progressively automated alert triage and case management workflows, reducing our MTTR from 6 hours to 30 minutes. The next phase, and the real game-changer, came with the introduction of Hero AI, a collection of agentic and generative AI capabilities available within Turbine.
We were the first to deploy these Hero AI agents directly within Turbine. It felt like adding autonomous experts to our team, providing context-aware reasoning in real-time through the incident lifecycle, which drastically accelerates triage and eliminates routine manual overhead.
What are Hero AI Agents? Hero AI Agents are autonomous AI entities embedded within the Turbine platform. Unlike reactive tools, these agents are capable of understanding complex security goals, planning multi-step solutions for threat detection and response, and executing actions with minimal human intervention. They are designed to move security operations from passive tools to proactive collaborators.
We rely on four primary agents to drive our autonomous operations:
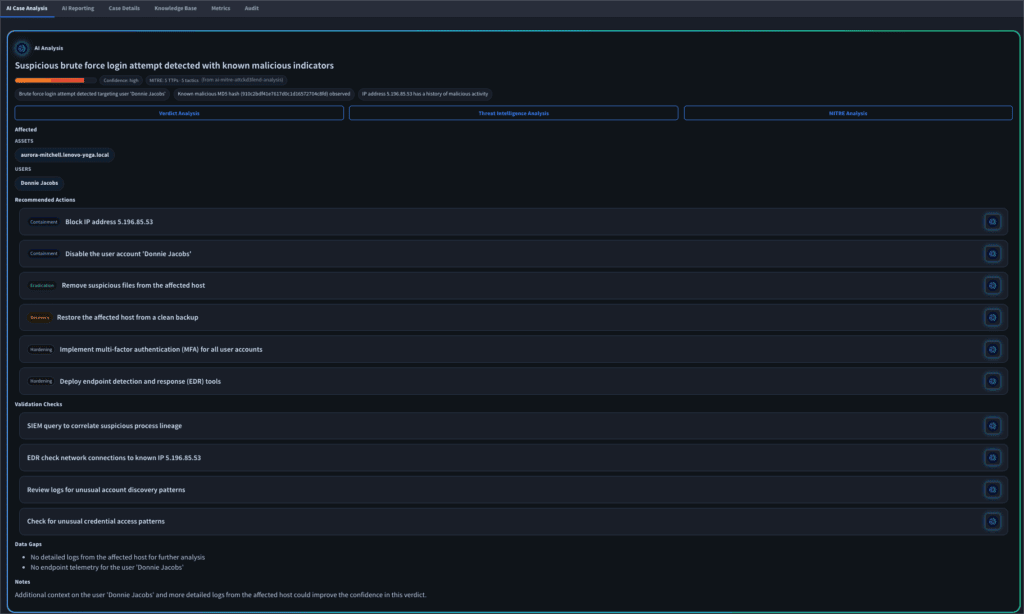
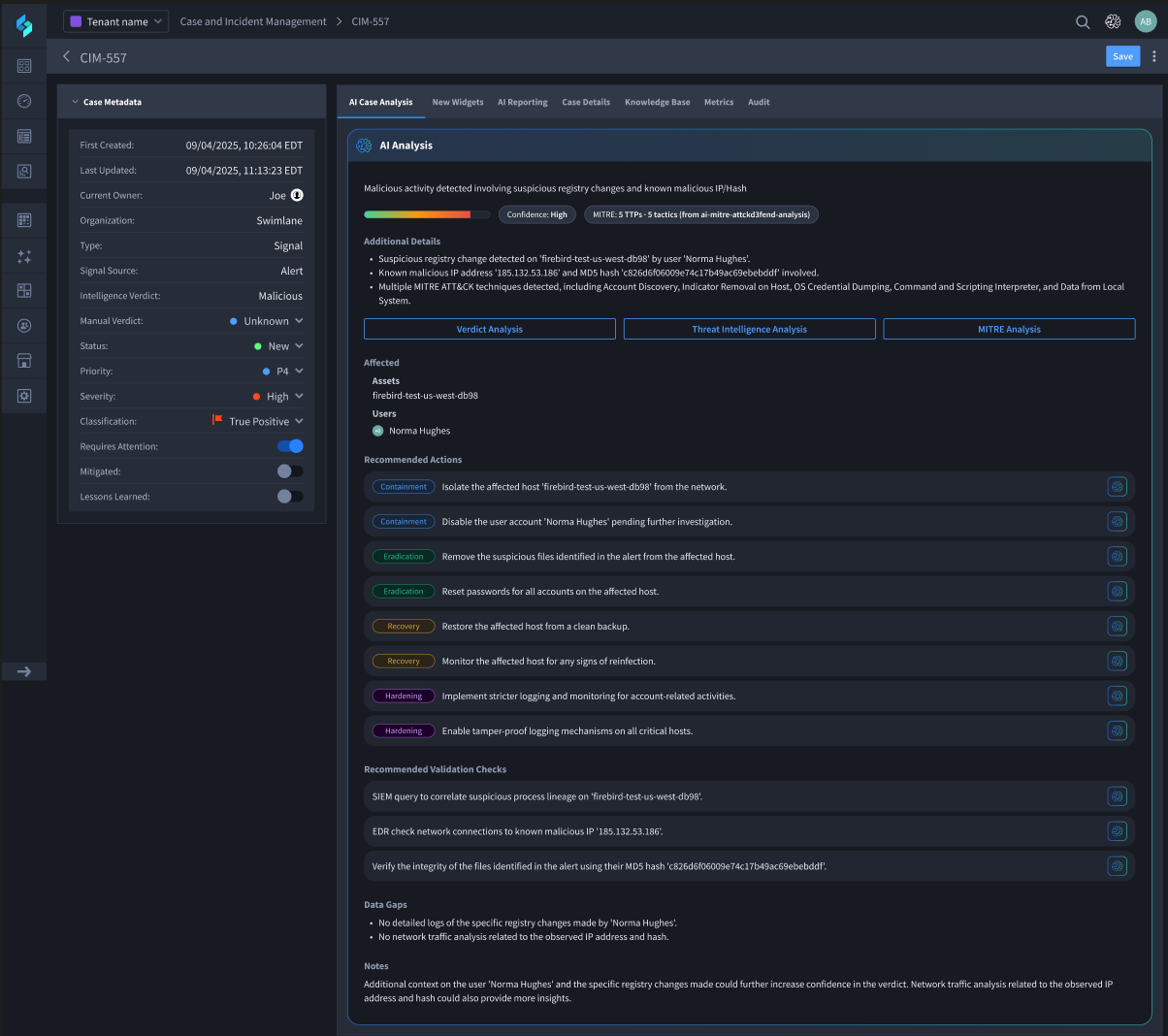
- Verdict Agent: This agent is probably the one we leverage the most. It utilizes all available current, linked, and historical case context, including Knowledge Base articles, linked case history, threat intelligence, and analyst notes, to autonomously generate a verdict, mirroring analyst judgment.
- Threat Intelligence Agent: This agent is a game-changer for threat intel. It’s built to aggregate and analyze data from all our utilized sources, including VirusTotal, Cisco Umbrella, and RecordedFuture, and provides a unified, cross-source analysis directly in the case file.
- MITRE ATT&CK & D3FEND Agent: This one is critical for operational clarity. It’s trained to automatically map vendor security alerts to standardized attack and countermeasure techniques, giving my team a universally understood language for tactics and defense across the board. This standardization is huge for a consistent response.
- Investigation Agent: The key to our efficiency. It automatically builds and executes a full investigation plan, providing end-to-end analysis from a single unified interface. This is how we eliminate all that wasted context switching and accelerate triage with valuable AI-generated summaries, timelines, and recommended actions.
Measurable Impact from Hero AI
Since deploying our Hero AI agents in Turbine, our internal SOC has seen significant operational efficiencies and cost savings.
- In 30 days we observed:
- MTTR was dramatically cut by 51%, falling from 18 minutes to 8.75 minutes.
- MTTR was dramatically cut by 51%, falling from 18 minutes to 8.75 minutes.
- Weekly:
- We saved roughly 60 hours of “human time”
- The operational cost savings amounted to $2,600, a figure equivalent to the annual labor cost of one Tier-1 analyst when extrapolated.
- We saved roughly 60 hours of “human time”
- Current:
- We autonomously close ~350 cases per week
From Assisted to AI Security Operations
Hero AI doesn’t just accelerate resolution; it builds confidence through consistency and explainability. The Swimlane SOC team utilized the data from ~35,000 human investigations Hero AI to benchmark, verify and tune our prompt. We are currently at 10 use cases with fully autonomous operations. We observed notable improvements in trust, accuracy, and cost optimization, thanks to better token efficiency and expanded context windows.
Ready to Scale? Your AI SOC Blueprint is Here
The convergence of AI and advanced automation in Turbine truly empowered our SOC to comfortably reach a sub-15-minute MTTR and accelerate our move toward autonomous case closure at scale. What started as a focused push to reduce manual work has now evolved into a clear blueprint for an AI SOC, where AI agents deliver real-time triage, explainable verdicts, and one-click response, all from a unified interface.
As I was reflecting on our incredible milestones, I asked Kevin Mata, our Director of Cloud Operations, for his thoughts: “Hero AI has transformed how we run our SOC, accelerating operations while continuously learning and improving. Every case we close makes the next one faster, smarter, and increasingly more autonomous.”
If my team can achieve these results internally, any organization looking to scale security operations will succeed, leveraging Turbine. This model is the proven future of security operations.
Swimlane AI Agents Demo
Get a live demo of the Swimlane Turbine agentic AI automation platform to see how it can help you handle 99% of your tier 1 SOC tasks.



