Insider threats occur when an individual with ties to an organization misuses their access for malicious intent, such as stealing intellectual property or other data. Detecting insider threats can be difficult. But by using a security information and event management (SIEM) system or data loss prevention (DLP) products, you can create alerts to detect the exfiltration of data leaving your organization that is unauthorized or unexpected.
Once you have detected these events, your security operations center (SOC) needs to investigate rapidly. Utilizing Swimlane and our Insider Threat Use Case, you can investigate and respond to these insider threats swiftly and accurately.
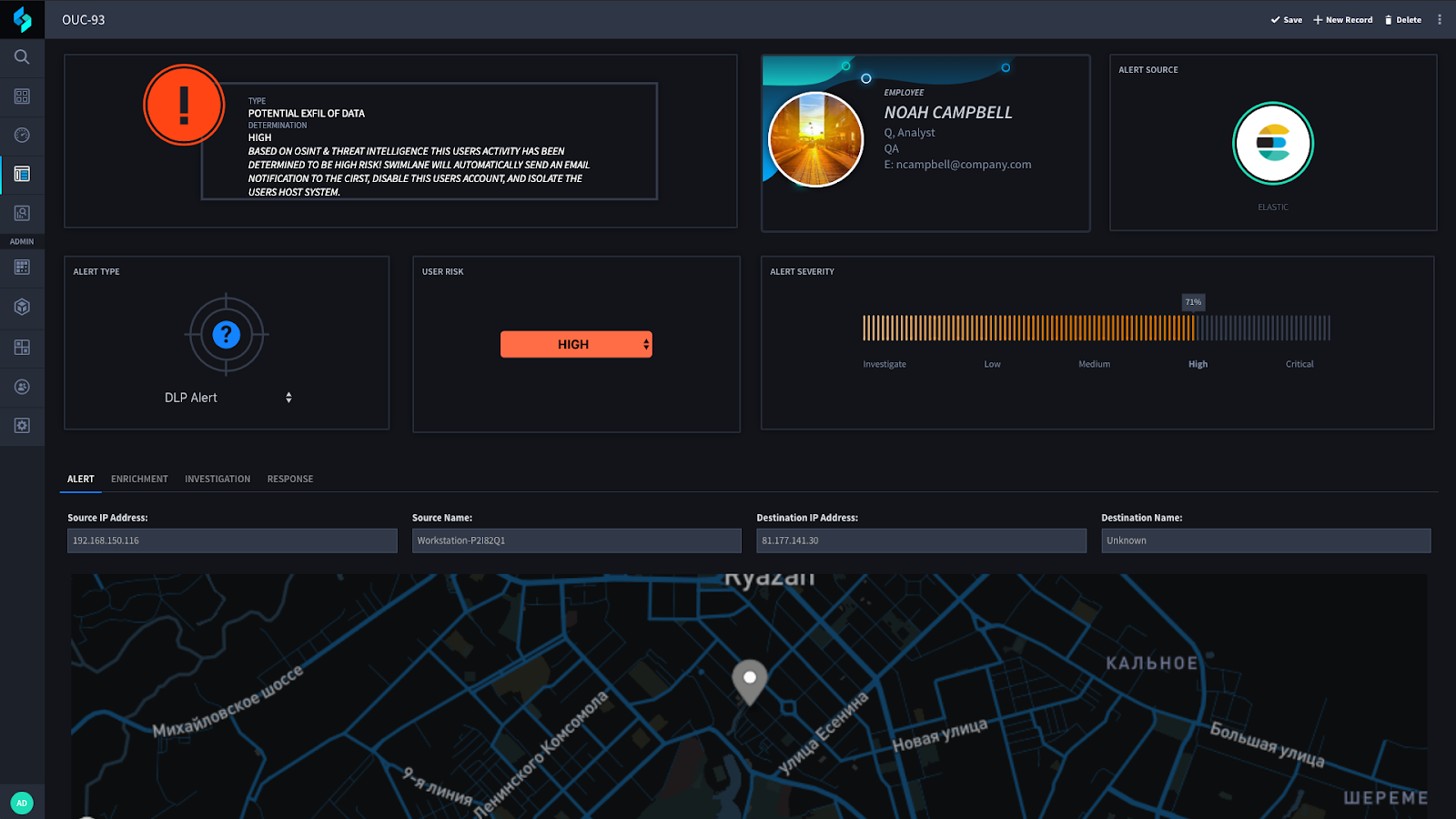
Whether an alert is received from your SIEM or DLP product, Swimlane can ingest and begin investigating the alert automatically. The first step in this use case is automatically querying Active Directory for information about the user that generated the alert. Once that step is complete, Swimlane will automatically begin enrichment using multiple open-source intelligence (OSINT) and threat intelligence sources to determine the likelihood that the destination IP address is malicious (or known malicious).
As a sample of different enrichment sources, this use case includes integrations with the following products:
- VirusTotal
- Hybrid Analysis
- AlienVault OTX
- Maltiverse
- ThreatMiner
- Apility
- IPINFO.io
- VirusTracker
If you would like to add different sources, internal and external threat intelligence, you can add them using any of our 200+ integrations, and if we do not have an integration for your product, we probably have it in our backlog. You can also request an integration (our integrations team is excellent!).
Using the results, Swimlane will tally and score the enrichment sources. Next, Swimlane queries your SIEM (Elastic in this example) to check for any other systems that may be communicating with this IP address. The combination of the enrichment sources score, as well as additional logs, generates a low, medium or high determination status. The following diagram outlines this process:
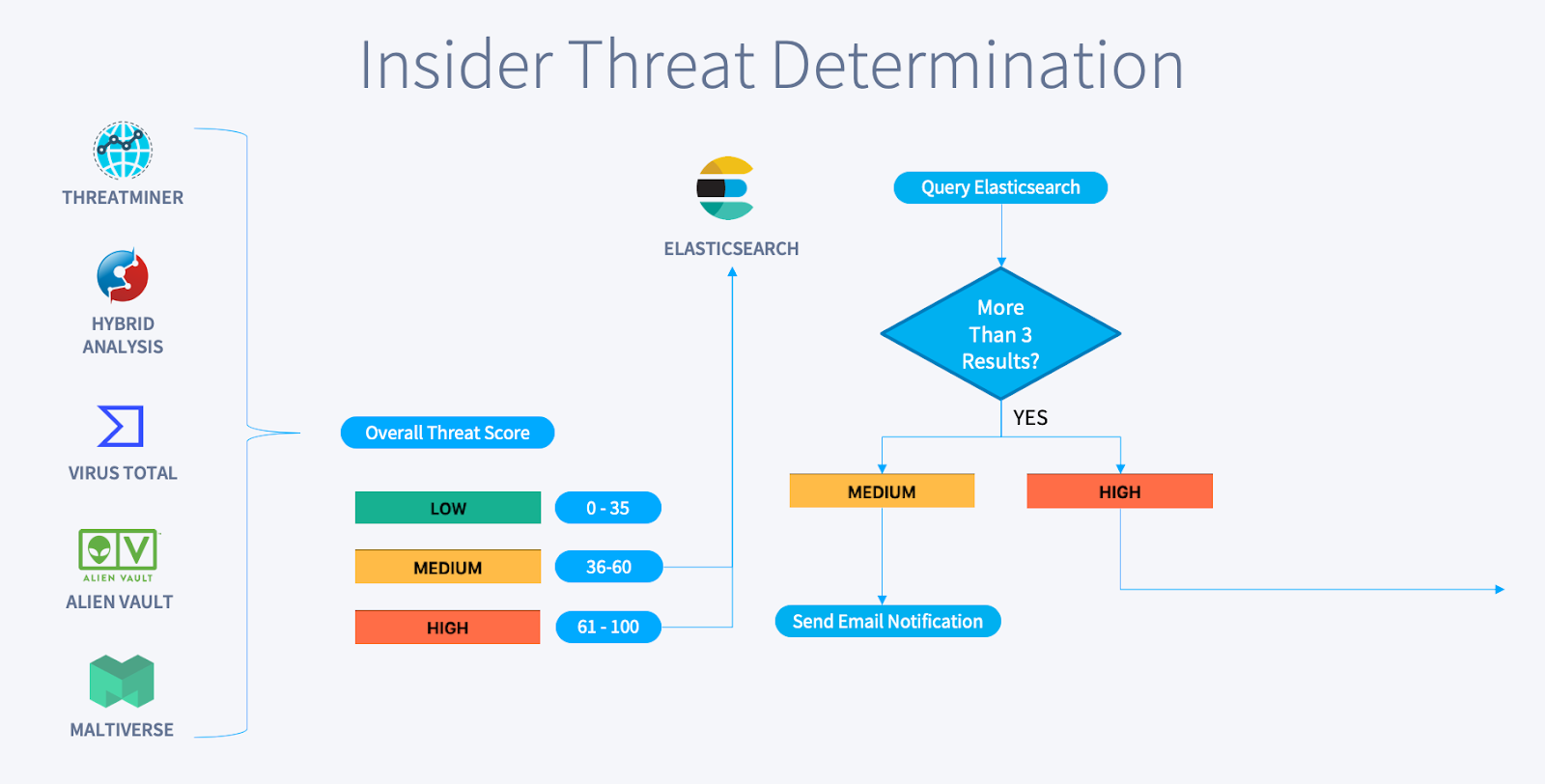
If the overall determination is considered medium, Swimlane automatically sends automated email notifications to the desired parties, such as the incident response team. If the determination is considered high, Swimlane takes additional actions on top of sending the email notifications:
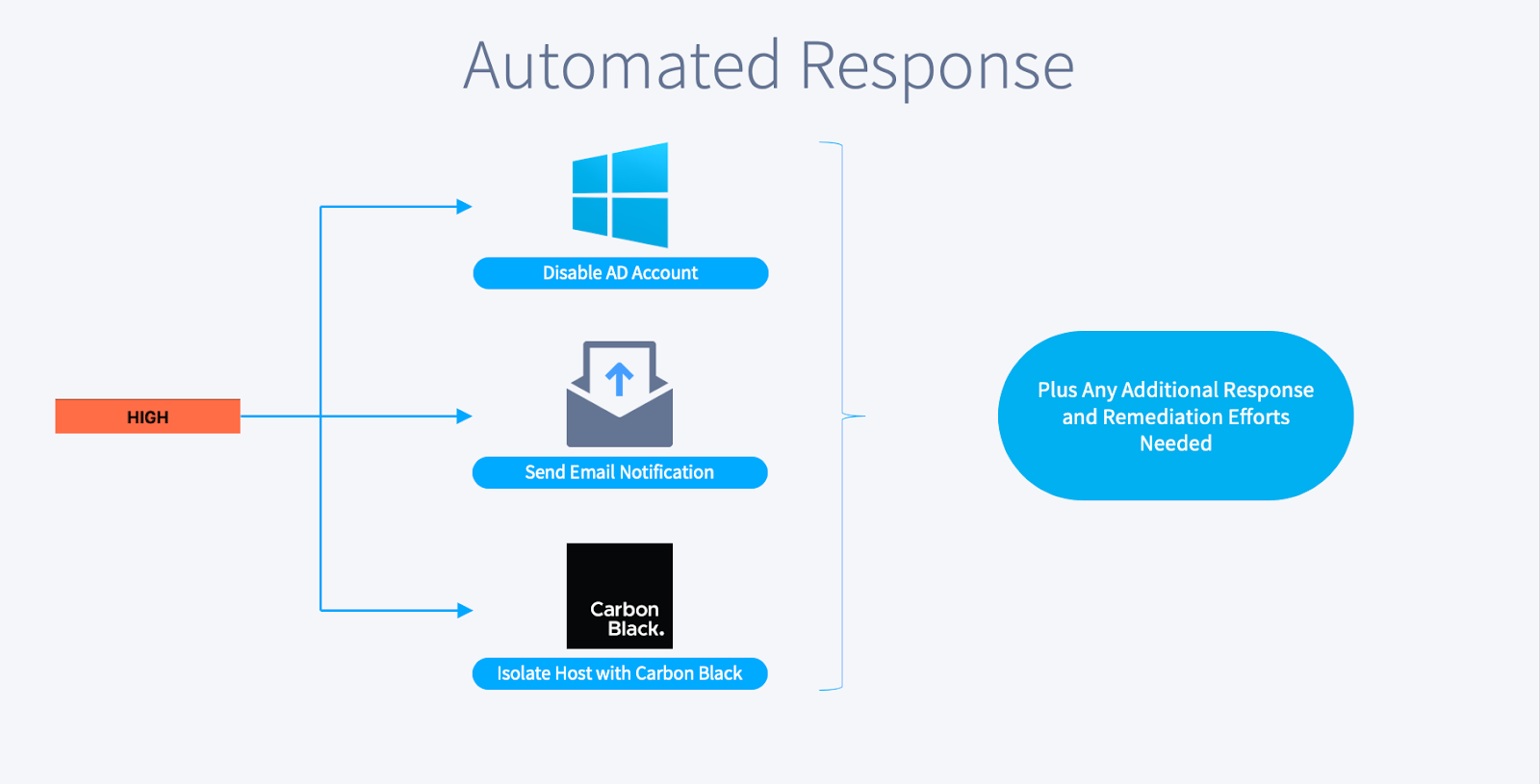
Swimlane will automatically disable the user’s accounts in Active Directory and send notifications via email to the appropriate individuals defined by your organization. Finally, Swimlane will isolate this host using your EDR product (Carbon Black in this case). If any additional response and remediation efforts are needed/wanted, you can add them to the workflow easily.
As with all of our use cases, we have a predefined workflow for insider threat investigation and response that is easily modifiable to fit your organization’s needs. If you would like to change the way the risk score is calculated, or set a weighted value on certain enrichment sources over others, you can do so easily. You can also easily make changes to the timing for when certain automated actions are performed (in addition to any other desired actions).
Here is the Swimlane Insider Threat Use Case workflow at a glance:
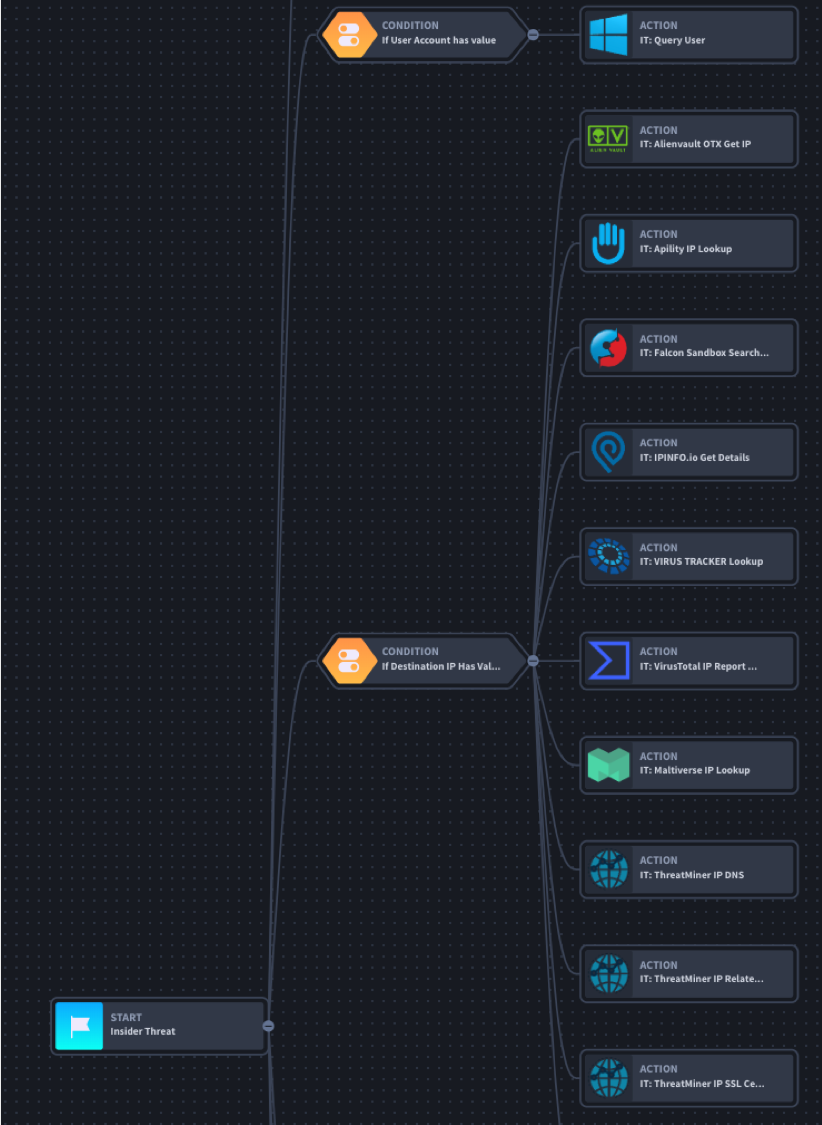
Now that we’ve introduced you to the Insider Threat Use Case workflows, it’s time to see the use case in action! Register for the upcoming Swimlane webinar now!

SOAR Use Case: Insider Threats
During this webinar, Security Research Engineer Josh Rickard and SOAR Evangelist Jay Spann will show you three use cases for SOAR to detect, analyze and respond to potential insider threats.


