In a world where the workplace has gone almost fully mobile and digital (click here for a more comprehensive digital workplace definition), one thing should be at the top of your priority list: security.
Ensuring that all your mobile data, systems, and networks are always protected from potential threats is paramount to keeping your business running smoothly and efficiently. Whether you habitually access a VoIP contact center from mobile, use a video conferencing platform on your smartphone, or leverage any other mobile device, you need to be aware of the main threats you might incur – and how to prevent them.
Want to learn more about this all-important topic? Our guide illustrates the five major security issues of mobile devices and suggests ways to prevent them – and safeguard your business.
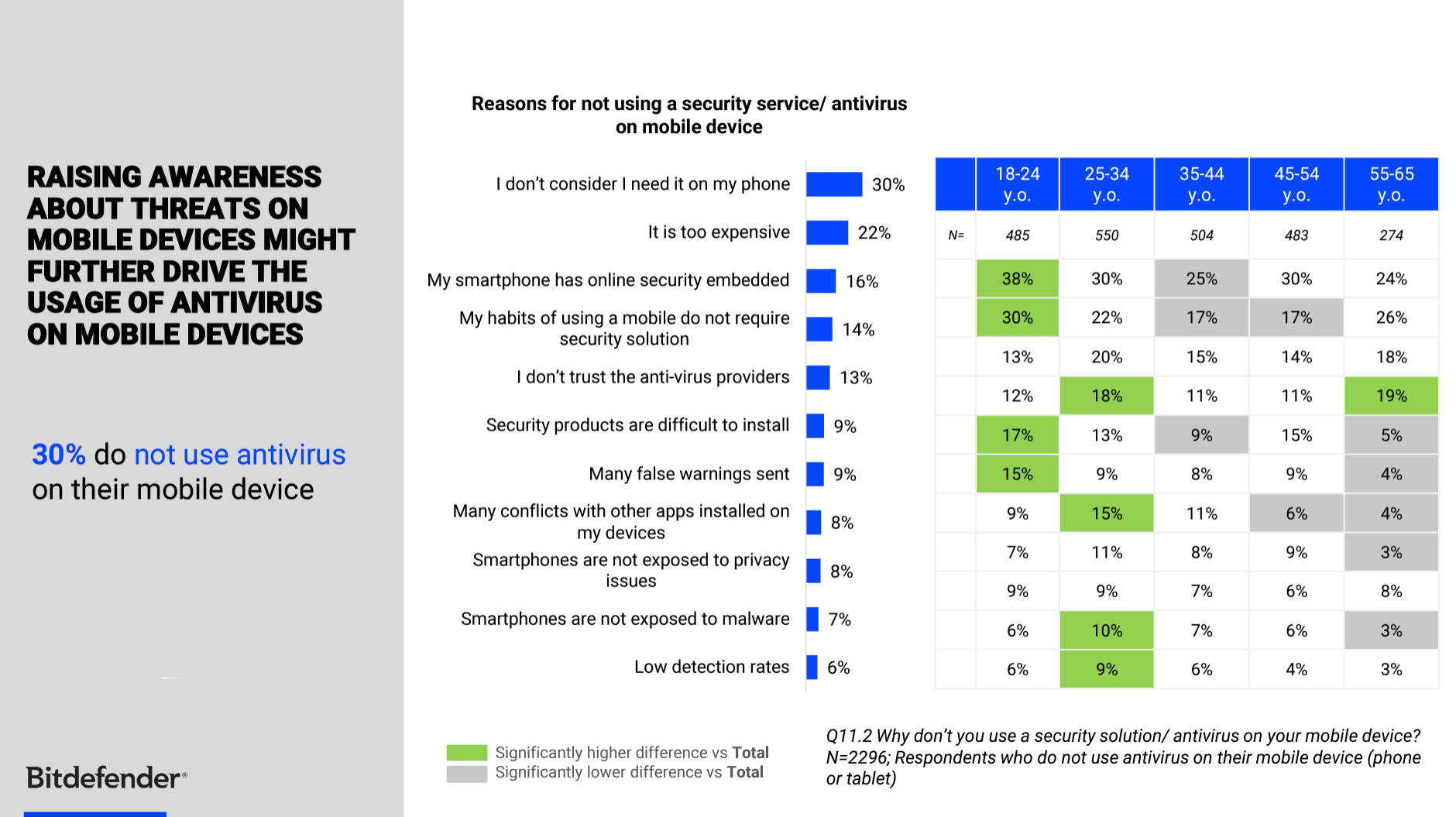
Source – 2021 Bitdefender Global Report: Cybersecurity and Online Behaviors
What Is Mobile Device Security?
The expression “mobile device security” refers to all those activities aimed at safeguarding data and information stored, accessed, or shared on mobile devices. Mobile devices are not just smartphones; they also include tablets, laptops, smart watches, services like magicJack, and IoT devices.
All the data that these devices deal with is constantly under potential threat. It is particularly concerning when those devices are used in a business context. Establishing a solid mobile security framework ensures all your mobile devices are protected.
This consists of identifying specific security metrics to measure, monitoring your mobile devices 24/7, and acting proactively whenever a potential issue is detected. Failure to take swift action if something suspicious occurs can be catastrophic.
The Potential Consequences of Mobile Security Attacks
Consider this – when working in your office, you don’t want anyone unauthorized to enter the building, as this can pose a potential threat. That’s why you have likely installed some form of right access control security to protect your physical workspace and the people inside it.
The same concept should apply to your digital devices. When an unauthorized individual succeeds in their malicious attempt to access your systems and networks and wreak havoc on them, it is incredibly problematic. Read on to uncover the four significant effects that cyberattacks can have on your devices.
1. Loss of Profits
Once a hacker has gained access to your systems, you could experience a substantial loss of money. It can happen in two different ways:
-
The hacker might gain control of sensitive information, such as internal and client credit or debit card details, and therefore perform financial transactions that are out of your control.
-
As a result of the security breach, you have to close your business while you deal with the attack. You lose billable hours, profits and have to pay for legal fees. In fact, the average total cost of a data breach in 2020 was $1.52 million. This says nothing of the potential damage to your company’s reputation and loss of future earnings.
The bottom line? Your business could lose millions in just a matter of minutes.

Source – IBM Security: 2020 Cost of a Data Breach Report
2. Loss of Data
Another significant risk of a cyberattack on your mobile devices is data loss. Hackers can either delete data permanently, expose it to the public, or hold it for ransom via ransomware. This can have an enormous impact on businesses.
Think about, for example, companies that are in the business of augmented reality, banking, and even local government entities. These firms handle massive amounts of data daily – their business largely depends on it. If one of those organizations were hacked and its data were to be erased or stolen, it would face disastrous consequences.
3. Loss of Brand Reputation and Confidence
You have worked hard to gain your customers’ trust and strengthen your brand reputation as a credible, authoritative, and reliable leader in your field. Losing all that would be a formidable issue – and losing it due to poor mobile security would be even more frustrating.
Major cyber attacks on corporations go public (and viral) in a matter of hours, which leads customers of those corporations to distance themselves from those companies – whether by closing their accounts, ending their memberships, or simply stopping doing business with them. In fact, according to research 83% of customers will stop spending with a company for several months after a breach and over 20% say they will never purchase from that company again.
4. Loss of Compliance
If your company operates in a highly regulated sector – such as healthcare, finance, or insurance – you will need to ensure that you comply with specific regulations in matters of security. Failing to follow standards and guidelines can not only have a catastrophic effect on your business and its operations but might also cause you to fail your regular security audits and incur fines and penalties.
Now that we have highlighted the importance of mobile security, let’s find out the five most common types of mobile security threats, and how you can avoid them.
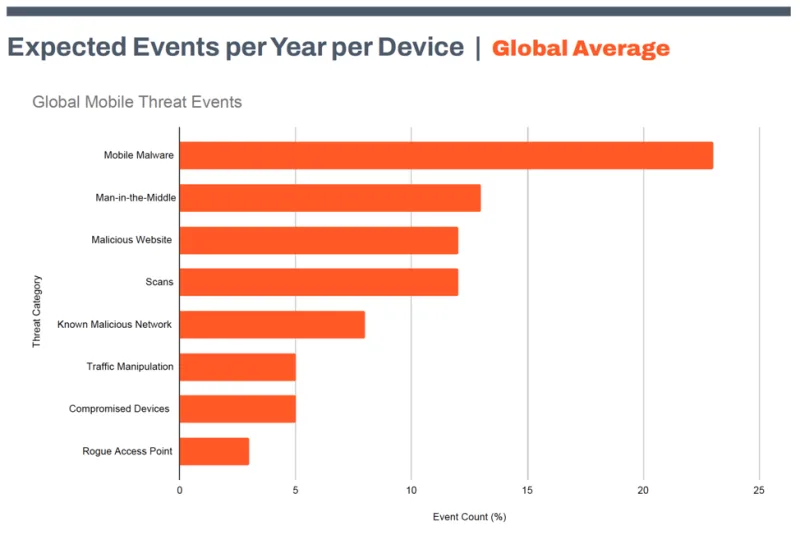
Source – Zimperium 2022 Global Mobile Threat Report
1. Unsecured, Public Wi-Fi Networks
How many times have you found yourself having to use your business smartphone or laptop when you are in a public area, and quickly accessing the only Wi-Fi network available? Well, we have bad news: if you’re used to doing this often, you put your company at increased risk of attack.
Public and free networks – those that you are likely to find in coffee shops, libraries, and airports – are also unsecured, meaning that they are much easier to access by attackers.
Prevent It Like This
The obvious way to avoid this potential risk is by not using these networks. If you really must use them, remember not to enter personal information or access anything sensitive, such as your email, social media account, or mobile banking apps. It’s also a good idea to have email threat protection on each of your mobile devices, and use VPN that offers encryption.
2. Poor (Cyber) Hygiene
The global pandemic has highlighted the importance of practicing good hygiene to stay healthy and protect ourselves and others from the COVID-19 virus. But did you know that you should apply the same concept to your cyber-life, too?
Yes, practicing cyber-hygiene is not only a thing, but it’s also one of the best ways to minimize the risk of experiencing an attack. Mobile devices with poor cyber hygiene – such as weak passwords, shared data, and out-of-date apps and operating systems – are at a much higher risk of being targeted by cybercriminals.
Prevent It Like This
Practicing good cyber hygiene requires the following methods such as email verification, automatic app and OS updates, and strong passwords. Similarly, you should never share your devices with other people, and you should always remember to log out of an app or a website when you are no longer using it.
3. Botnets
You might be familiar with chatbots, but do you know what botnets are? If the word doesn’t sound too menacing, you are in for an unpleasant surprise.
Botnets occur when two or more computers are simultaneously accessed and controlled by a hacker. With a botnet, several cyber threats can happen, including the installation of Trojans, viruses, and other malware.
Prevent It Like This
Cyber hygiene is essential to avoid your mobile device becoming part of a botnet. Only download trusted, legitimate apps and software, do not use unsecured Wi-Fi networks, and implement security automation for faster incident response.

Source – Cognyte: The Rise of Dark Web Botnet Marketplaces Report
4. Malicious Apps
Do you love apps? You are in good company, considering the average smartphone user has a whopping 40 apps installed on their device. When downloading new apps, however, you must always stick with trusted sources. Never download apps from third parties, as these can present higher risks of malware and other cyber threats.
Prevent It Like This
The best way to avoid malicious apps is to use only Google Play and the Apple App store to download them. Ensure that all apps are regularly updated to patch any security vulnerabilities.
5. Poor or Broken Cryptography
With the increasing popularity of remote work, video conferencing platforms, and note-taking software (such as Otter AI or any other Otter AI alternative), digital data sharing is the name of the game in today’s business world. And while staying in touch digitally with your co-workers is essential, it also presents potential risks.
For example, if you use software that doesn’t feature the right type of encryption or powerful algorithm, you might be more vulnerable to cyberattacks. This, in turn, means that the content of your conversations might not be protected and that information you share in them can be accessed by cybercriminals.
Prevent It Like This
Once again, one of the best ways to minimize this risk is to ensure that you and the people you are communicating with always use trusted, legitimate, and up-to-date online tools. For added security, use secure software to send and sign important documents, such as the Pandadoc software for signature.
Keep Your Mobile Devices Safe
With more and more businesses relying on mobile devices for their daily tasks and operations, improving cyber security has never been so vital. Mobile threats are always around the corner, but there are many steps that you can take to prevent them.
In this guide, we identified the five main mobile device threats and provided easy yet essential ways to prevent them from potentially destroying your business.
See Swimlane Turbine in Action
Schedule a Swimlane Turbine live demonstration with our experts! Learn how our AI-enabled security automation platform can help you solve the most challenging problems across your entire security organization.

