If you’re a security professional, you know the chaos that is vulnerability management all too well. Security teams struggle with prioritizing which vulnerabilities to remediate first, leading to delays, compliance risks, and potential breaches. While vulnerability scanners do a great job at detecting issues, they don’t provide actionable insights on which vulnerabilities pose the most significant risk or facilitate efficient remediation. That’s where Swimlane’s Vulnerability Response Management (VRM) solution comes in.
The Swimlane VRM AI Automation Solution picks up where traditional vulnerability management tools stop. Instead of just listing vulnerabilities, it delivers intelligence-driven prioritization that considers unique business contexts. Once findings are scored and prioritized, VRM facilitates seamless cross-functional collaboration and automation-powered remediation The result? Faster, more effective vulnerability management that reduces risk and improves operational efficiency.
Are Current Vulnerability Management Solutions Keeping Up?
Despite the clear need for effective vulnerability management operations, many organizations remain concerned about the business impact of ineffective vulnerability management. According to Swimlane’s latest report, Under Pressure: Is Vulnerability Management Keeping up, security leaders are concerned with:
- Reputational Damage – 40% of security leaders believe the biggest risk of ineffective VM is reputational damage and loss of customer trust.
- Business Downtime – 38% of security leaders believe the biggest risk of ineffective VM is business disruption and operational downtime.
- Financial Penalties from Regulations – 29% of security leaders believe the biggest risk of ineffective VM is financial penalties and fines due to being out of compliance with regulations.
- Regulatory Scrutiny – 19% of security leaders believe the biggest risk of ineffective VM is increased scrutiny from regulatory bodies.
- Legal Liabilities – 22% of security leaders believe the biggest risk of ineffective VM is legal liabilities and lawsuits.
Why Current Vulnerability Management Operations Fall Short
The sheer volume of vulnerabilities, disconnected tools, ineffective prioritization, and inefficient remediation workflows create a perfect storm of risk. Teams waste valuable time on low-priority issues without a streamlined approach while critical vulnerabilities remain unaddressed.
- Overwhelming Volume of Vulnerabilities – With tens or hundreds of thousands of vulnerability findings detected daily, teams often lack the bandwidth to assess and prioritize them effectively.
- Siloed Tools & Data – Vulnerability scanners, IT ticketing systems, and security tools often operate in isolation, making it difficult to see the full risk landscape.
- Lack of Risk-Based Prioritization – Without clear insights into exploitability, asset criticality, and compliance impact, security teams waste time on low-priority issues while critical vulnerabilities go unaddressed.
- Complex Remediation Workflows – Coordination between security and IT teams is often inefficient, slowing down response times and increasing exposure to attacks.
The Most Intelligent Vulnerability Response Management Solution
The Swimlane VRM solution is designed to eliminate these challenges by providing a comprehensive AI automation solution for vulnerability response that goes beyond detection by picking up where scanners leave off. Here’s how it stands out:
1. Swimlane Vulnerability Threat Intelligence
Swimlane VRM is more than just a management tool—it’s a fully automated response system. With Swimlane Intelligence, it enriches vulnerability findings using over 30 out-of-the-box enrichment sources as well as custom organization risk criteria, including:
- Temporal CVSS scores, tracking how risk changes over time.
- Exploit information such as sample code
- Vulnerability research resources
- Asset and zone criticality
2. Intelligent Risk-Based Prioritization
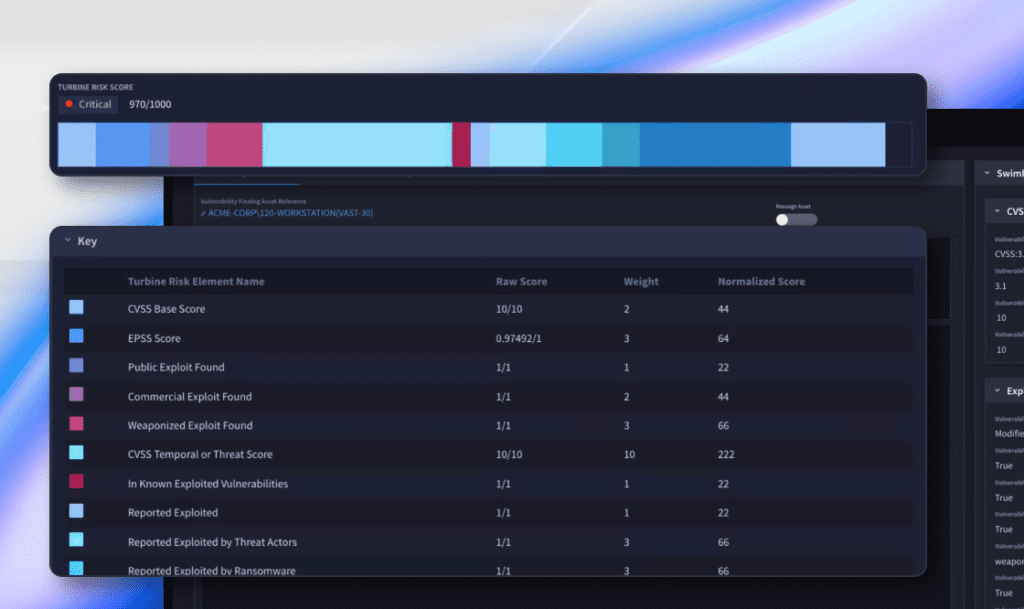
The Swimlane VRM solution automatically assigns a Turbine Risk Score and Prioritization Rank to every vulnerability finding by analyzing multiple factors, including:
- Common Vulnerability Scoring System (CVSS): Scoring system.
- Exploit intelligence: Whether and how a vulnerability is actively exploited in the wild.
- Asset criticality: How important the affected system is to business operations.
- Compliance requirements: Ensuring regulatory adherence. This risk-driven approach ensures that security teams focus on the vulnerabilities with the highest business impact.

3. Private Agentic AI Companion
Additionally, Hero Companion, a private agentic AI companion available anywhere in Turbine, assists security teams with vulnerability management. Directly in the VRM solution, teams can ask natural-language questions like:
- “What are my highest-risk unpatched vulnerabilities?”
- “Which CVEs on this system have active exploits?”
This allows security teams to get instant, actionable insights without manually digging through data.
3. Seamless Multi-Scanner Integration
One of the biggest challenges in vulnerability management is consolidating findings from multiple scanners. Swimlane VRM integrates with leading vulnerability assessment tools such as Rapid7, Tenable, Lacework, and many others, normalizing data across all sources into a comprehensive view. No more jumping between dashboards—everything security teams need is in one place.

4. End-to-End Vulnerability Case Management
Managing vulnerabilities isn’t just about identifying and prioritizing them—it’s also about making sure remediation happens efficiently. Swimlane VRM includes built-in case management capabilities, enabling:
- Automatic ticket creation in ServiceNow, Jira, and other ITSM tools
- Direct collaboration through Slack, Microsoft Teams, and email
- Workflow automation to ensure vulnerabilities are addressed in a timely manner

5. Unified Asset Inventory
Swimlane’s VRM provides a real-time, centralized system of record for all assets with vulnerabilities, helping organizations:
- Track which systems are affected
- Maintain compliance with regulatory frameworks like NIST, ISO 27001, and GDPR
- Prove due diligence during audits by demonstrating a proactive vulnerability response

Why Swimlane’s Vulnerability Response Management is the Most Intelligent Solution on the Market
Unlike traditional vulnerability management solutions that focus solely on detection, Swimlane VRM closes the loop by providing:
- Proactive Risk-Based Prioritization – Ensuring the most dangerous vulnerabilities are addressed first.
- AI-Driven Decision Making – Giving security teams immediate, intelligent recommendations for remediation.
- Seamless Collaboration & Automation – Speeding up response times and reducing manual effort.
- Single-Pane-of-Glass Visibility – Integrating with multiple scanners and IT tools for a complete, real-time security posture view.
Take Control of Your Vulnerability Chaos Today
Security teams can no longer afford a reactive approach to vulnerability management. Swimlane VRM provides the intelligence, automation, and collaboration tools needed to stay ahead of threats, reduce risk, and ensure compliance.
Ready to transform your vulnerability management strategy? Request a demo today at swimlane.com/demo.

Are You Keeping Up with Vulnerability Management?
Fragmented data, siloed risk scoring, and poor cross-team collaboration are leaving organizations exposed. 68% fail to fix critical vulnerabilities within 24 hours, leading to breaches, compliance failures, and costly penalties. It’s not just about patching anymore; it’s about prioritizing the right vulnerabilities. Manual processes are costing businesses an estimated $48K per employee annually. There is a better way.
Join us for actionable insights from Swimlane’s latest research report “Under Pressure: Is Vulnerability Management Keeping Up?”, and discover how Swimlane hyperautomation for vulnerability response management can help you.