Here are two questions to get you thinking.
- Are you hindered by having multiple disconnected endpoint vulnerability scanners?
- Does your vulnerability management process feel like a guessing game due to a lack of context on which vulnerabilities are critical?
If you answered yes to either of these questions, you should keep reading because it’s time to turn your vulnerability management chaos into clarity.
At Swimlane, we know that vulnerability management isn’t just a process; it’s a race against attackers who only need to be right once, while you have to be right every time. But if you’re struggling to prioritize threats because you’re lacking context or juggling a million different alerts and several tools that don’t talk to each other, you’re not alone. The latest data shows that security teams like yours face serious roadblocks, from delayed remediation to overwhelming complexity.
So, what’s slowing you down? To help us find out, we partnered with Sapio Research to survey 500 cybersecurity decision-makers across the U.S. and the U.K. In our latest report, Under Pressure: Is Vulnerability Management Keeping Up?
In this ongoing series, we’re diving into the latest findings from our report. This blog focuses on the first two challenges organizations face today when managing vulnerabilities—lack of context and overall complexity.
The Vulnerability Clock Is Ticking: Lack of Context Fuels the Urgency
Do you ever feel like you’re just a few puzzle pieces short of the bigger picture or unsure which vulnerabilities truly matter? Add the pressure of racing against time and attackers, and the clock starts really ticking.
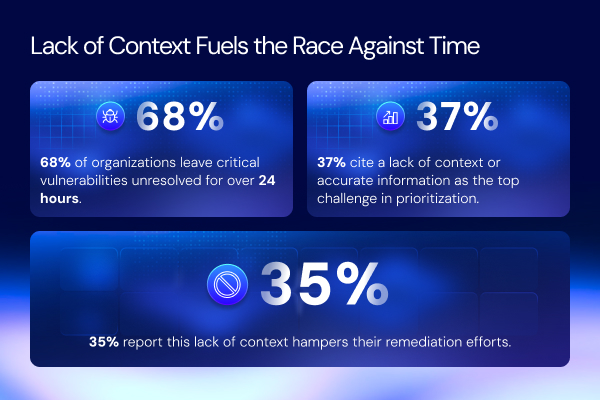
One of the survey respondents’ most significant challenges in vulnerability management is the lack of context. A staggering 68% of organizations report leaving critical vulnerabilities unresolved for over 24 hours, giving attackers a significant window to exploit weaknesses. This delay often stems from an inability to prioritize effectively due to missing or inaccurate context.
- If you answered yes, you’re not alone—37% of organizations cite a lack of accurate information as their top challenge when prioritizing vulnerabilities. Without the proper context, you struggle to assess the severity of vulnerabilities, making it harder to focus on what matters most.
- Additionally, 35% of respondents say this lack of context hampers their remediation efforts. Without clear insights into how vulnerabilities impact the broader system, remediation becomes a guessing game, delaying action.
These findings highlight the urgent need for a more contextualized, informed approach to vulnerability management. Having the right tools and processes to gather and analyze context is the missing puzzle piece for you and your team, which is essential for reducing the time vulnerabilities stay open and minimizing the risk of exploitation.
For a deeper look into how a well-structured process should flow from detection to remediation, check out this guide to the vulnerability management lifecycle.
Escape the Complex Web of Disjointed Systems
If you’ve gotten this far, you’re likely familiar with the overwhelming complexity of vulnerability management systems. Many teams like yours struggle with fragmented approaches, juggling a mix of manual and automated processes that don’t always integrate smoothly.
- 55% of organizations don’t have a comprehensive system to prioritize vulnerabilities. This lack of cohesion makes it difficult for you to manage vulnerabilities efficiently, leading to increased risk and wasted resources.
- Despite the growing reliance on automation, 45% of teams still combine manual and automated processes. While automation is crucial for efficiency, many still find manual efforts necessary, leading to inefficiencies and errors.
- To complicate things, you’re likely using a variety of specialized tools. 71% of organizations rely on cloud security posture management (CSPM) tools, 60% use multiple endpoint scanners, and 59% deploy web application scanners for vulnerability detection. Each tool has its purpose, but using multiple systems can create a fragmented landscape, making vulnerability management even more complex.

These challenges prove that while many teams invest in tools and technologies to manage vulnerabilities, many still lack an integrated, cohesive system to streamline efforts. The complexity of working with disparate systems can slow your response times, leaving you vulnerable to threats. Like I said before, attackers only need to be right once, but you must be right every time.
So how can you be right every time? Well, we’re happy you asked.
Control Your Chaos with The Swimlane Vulnerability Response Management Solution
By embracing Swimlane’s Vulnerability Response Management (VRM) solution, you can implement the five strategies discussed in the first part of this blog series, streamline your processes, and make data-driven decisions. Take control of your vulnerability management challenges and focus on what truly matters: your data, your job, your organization, and YOU.

The Swimlane Vulnerability Response Management Solution Demo
In this demo, Josh Roback, Principal Security Solution Architect, will showcase how the Swimlane VRM Solution picks up where vulnerability scanners leave off, providing enterprise-level intelligence for real-time action. Watch the 5-minute demo to discover how Swimlane VRM goes beyond traditional vulnerability management.


