A step-by-step guide on how to use open source data to automate threat intelligence enrichment and IoC lookup processes.
What is Cobalt Strike?
Cobalt Strike is a popular penetration testing tool used by cybersecurity professionals to simulate attacks on networks and systems. It provides a wide range of features such as command and control, payload generation, and post-exploitation modules, making it a versatile tool for both offensive and defensive security purposes.
However, as with any powerful tool, it can also be misused by malicious actors for conducting real-world attacks. This is where Threat Intelligence comes into play.
One such Threat Intelligence source is the C2IntelFeeds repository hosted on GitHub, which is a collection of open-source feeds that provide data on Cobalt Strike and other Command and Control (C2) servers. By leveraging this repository, analysts can proactively identify malicious IP addresses, bad domains, and other indicators of compromise that may be associated with Cobalt Strike attacks.
How to Easily Enrich Cobalt Strike Data with Turbine
We’re going to use our built-in HTTP connector to gather the data from the URLs below, since it gives us the flexibility of not writing any code. The HTTP connector can be used like Postman where you can use GET, POST, DELETE, PUT and PATCH. We can use all different kinds of authentication such as OAuth, Basic, None, Bearer Token, Header, and some other things like Scopes.
Step 1: Get the Data.
Gather the URLs for each feed:
https://raw.githubusercontent.com/drb-ra/C2IntelFeeds/master/feeds/domainC2s-30day-filter-abused.csv https://raw.githubusercontent.com/drb-ra/C2IntelFeeds/master/feeds/domainC2s-30day.csv https://raw.githubusercontent.com/drb-ra/C2IntelFeeds/master/feeds/domainC2s-filter-abused.csv https://raw.githubusercontent.com/drb-ra/C2IntelFeeds/master/feeds/domainC2s.csv https://raw.githubusercontent.com/drb-ra/C2IntelFeeds/master/feeds/domainC2swithURL-30day-filter-abused.csv https://raw.githubusercontent.com/drb-ra/C2IntelFeeds/master/feeds/domainC2swithURL-30day.csv https://raw.githubusercontent.com/drb-ra/C2IntelFeeds/master/feeds/domainC2swithURL-filter-abused.csv https://raw.githubusercontent.com/drb-ra/C2IntelFeeds/master/feeds/domainC2swithURL.csv https://raw.githubusercontent.com/drb-ra/C2IntelFeeds/master/feeds/domainC2swithURLwithIP-30day-filter-abused.csv https://raw.githubusercontent.com/drb-ra/C2IntelFeeds/master/feeds/domainC2swithURLwithIP-30day.csv https://raw.githubusercontent.com/drb-ra/C2IntelFeeds/master/feeds/domainC2swithURLwithIP-filter-abused.csv https://raw.githubusercontent.com/drb-ra/C2IntelFeeds/master/feeds/domainC2swithURLwithIP.csv
Then, break down the URLs above to make it more automation friendly:
- URL = https://raw.githubusercontent.com
- EndPoint = /drb-ra/C2IntelFeeds/master/feeds
- Then, each file:
- “domainC2s-filter-abused.csv”,
- “domainC2s.csv”,
- “domainC2swithURL-30day-filter-abused.csv”,
- “domainC2swithURL-30day.csv”,
- “domainC2swithURL-filter-abused.csv”,
- “domainC2swithURL.csv”,
- “domainC2swithURLwithIP-30day-filter-abused.csv”,
- “domainC2swithURLwithIP-30day.csv”,
- “domainC2swithURLwithIP-filter-abused.csv”,
- “domainC2swithURLwithIP.csv”
Step 2: Create a Playbook.
With the data gathered from Step 1, let’s build a playbook in Swimlane Turbine.
The first playbook action will be to use the data transformation feature to pass in a list of the files from above, shown here:
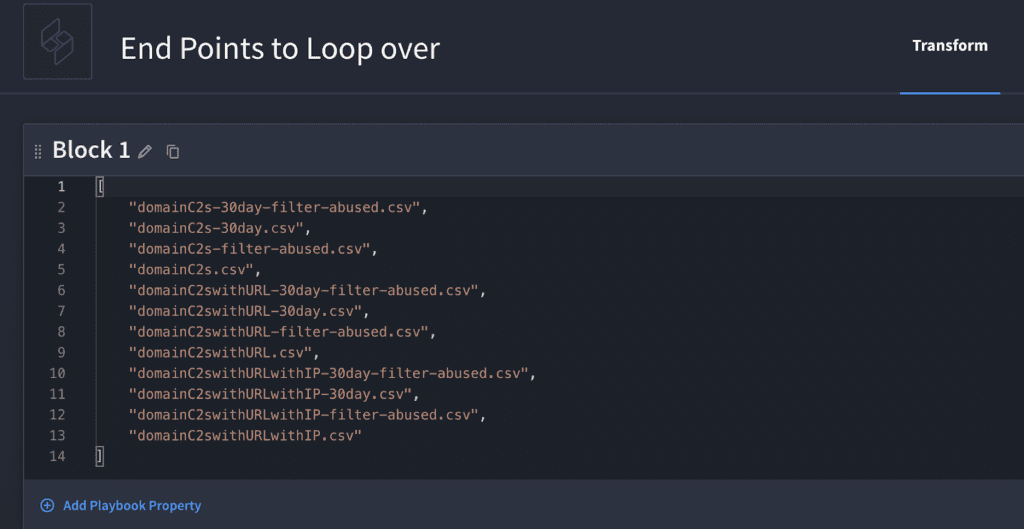
Tip: We can add these items as a list and loop over each file with our magical HTTP connector in a sub-playbook loop has just one action, “Get Data via HTTP”, where we are passing in the “URL”, “Endpoint” and “Filename”.
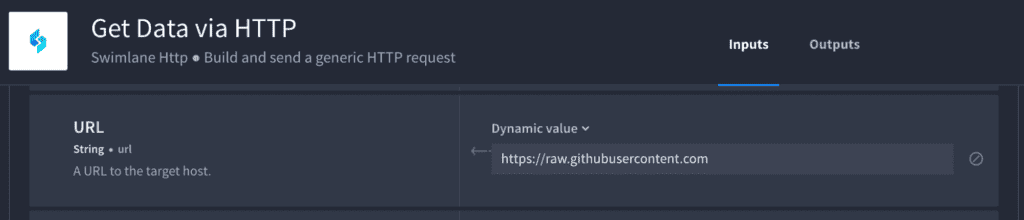
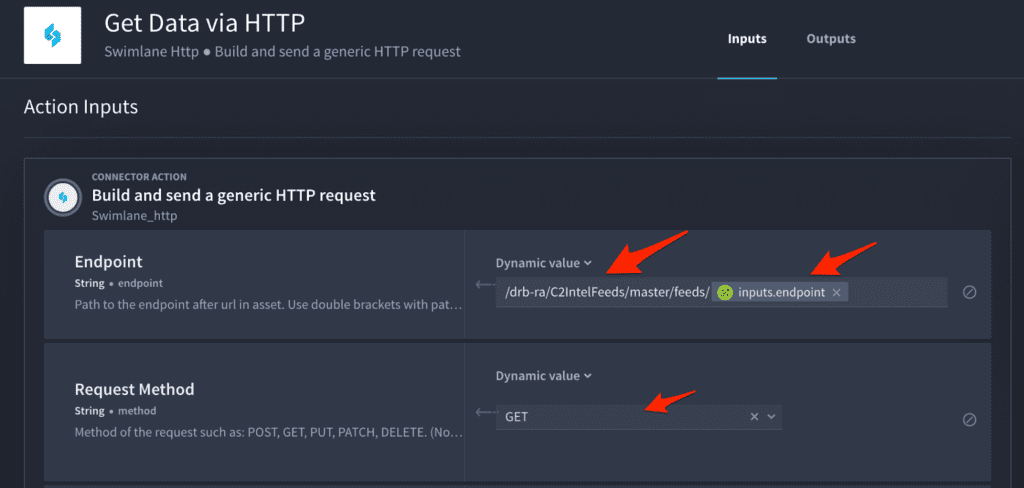
Notice we are using playbook inputs to pass in the “Filename” from the parent playbook.
Next, merge all the data into one “string” so we can use a JSONata action to find the IoC faster.
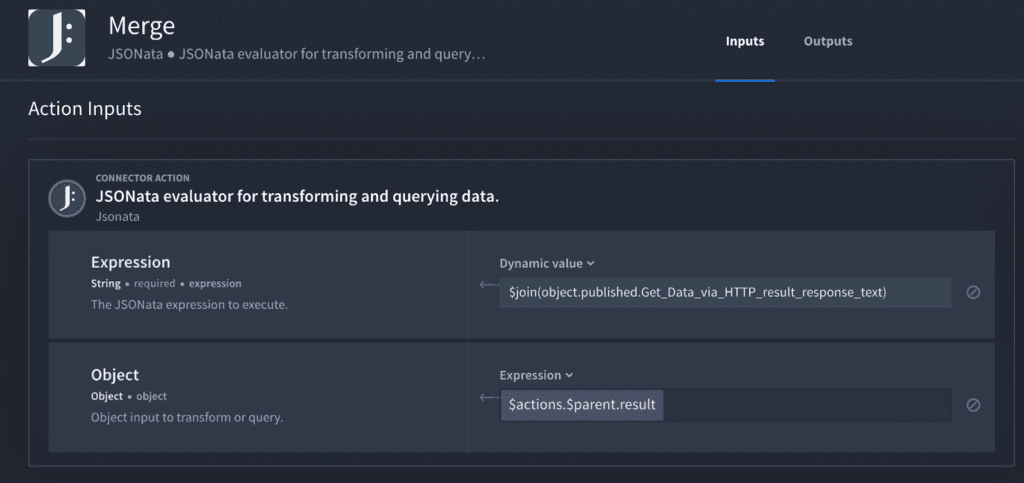
Now, let’s take apart that expression above: “$join(object.published.Get_Data_via_HTTP_result_response_text)”
The “join” syntax is from JSONata. We’ll enrich all the data that returns for each file and combine them into a single string. Notice the “response_text” from above with the [.] notation and the JSON key below:
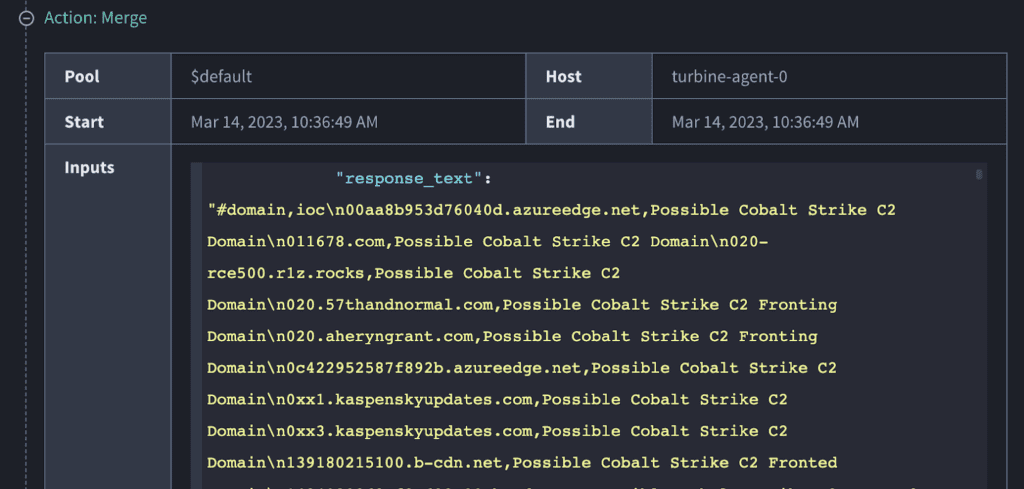
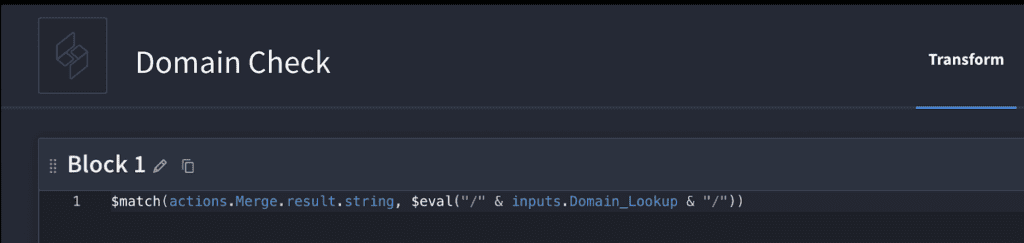
Next, we need to look up a domain to see if it’s in the “response_text” string.
Did you know: you can save 9 minutes by using the “match” option in Turbine’s data transformation builder feature, instead of looping over each item in the files? Doing so reduces the time to just 2 seconds to find the IoC. 🤯
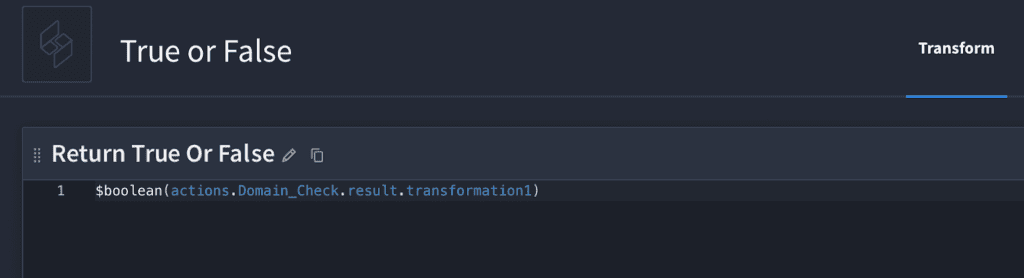
Now, we want to return True or False to our case management system. To do that, we’re going to use JSONata “boolean”.
Once we have True or False, we also process it through our threat enrichment playbook that feeds the case mananagment.
And there you have it. Cobalt Strike is a powerful tool used by both security professionals and malicious actors. However, by leveraging open-source threat intelligence sources such as C2IntelFeeds and automating the detection and remediation process using Turbine, organizations can better protect themselves against advanced cyber threats and improve their overall security posture.
Why You Should Automate Threat Intelligence Enrichment
Threat intelligence feeds are an essential tool for organizations looking to proactively identify and mitigate potential cyber threats. By leveraging these feeds, security teams can gather critical data on malicious IP addresses, bad domains and other indicators of compromise, enabling them to quickly detect and respond to potential threats.
The Swimlane Turbine security automation platform enables organizations to streamline their security workflows by integrating with various threat intelligence feeds, including C2IntelFeeds, and other security tools. This allows security teams to automatically collect and analyze data from multiple sources, enabling them to quickly identify and remediate potential threats, regardless of their origin.
Whether it’s Cobalt Strike or other sophisticated attack vectors, leveraging threat intelligence feeds with Swimlane’s automation capabilities can help organizations better protect themselves against advanced cyber threats. By taking a proactive approach to security and automating their incident response processes, organizations can reduce response times and improve their overall security posture, ultimately ensuring the safety of their data, systems and users.

ROI Report of Swimlane Turbine
To help companies evaluate the potential financial impact of the potential investment, TAG Cyber conducted an extensive study on the Swimlane Security Automation Solution. This independent study reveals 240% ROI for the Swimlane Turbine security automation platform.


