Challenges
- Manual phishing processes
- Unsustainable email triage workload
- Limitations of the previous SOAR
Outcomes
- 5x faster automation development
- Zero downtime migration from SOAR
- 25 minutes saved per phishing incident
- 40% auto-remediation for phishing cases
- 6-8 hours saved by automating the threat containment process
About Bayside Solutions
Bayside Solutions Incorporated, a cybersecurity specialist and value-added reseller (VAR), delivers critical security software and tools, with a core focus on phishing email analysis. They stand at the front lines, analyzing suspicious emails that bypass traditional defenses and land in user inboxes. We recently connected with Mike Pilcher, Senior Cyber Security Specialist at Bayside, to learn more about their journey.
With a lean team of high-level engineers and a commitment to a human-first approach, Bayside sought an automation platform that could provide both plug-and-play simplicity and deep customization. Their previous SOAR solution was too costly and lacked essential functionality, driving their search for a solution that would truly empower their analysts and streamline operations for their 24/7 service.
This case study examines how Bayside utilizes Swimlane to enhance its phishing email analysis service. It highlights their incredible achievement of transitioning two years of playbook work to Swimlane Turbine in just five weeks, all without any downtime. This rapid migration was made possible by leveraging Swimlane’s dedicated Technical Account Manager (TAM) services.
Cybersecurity Challenges
AI AUTOMATION SOLUTION
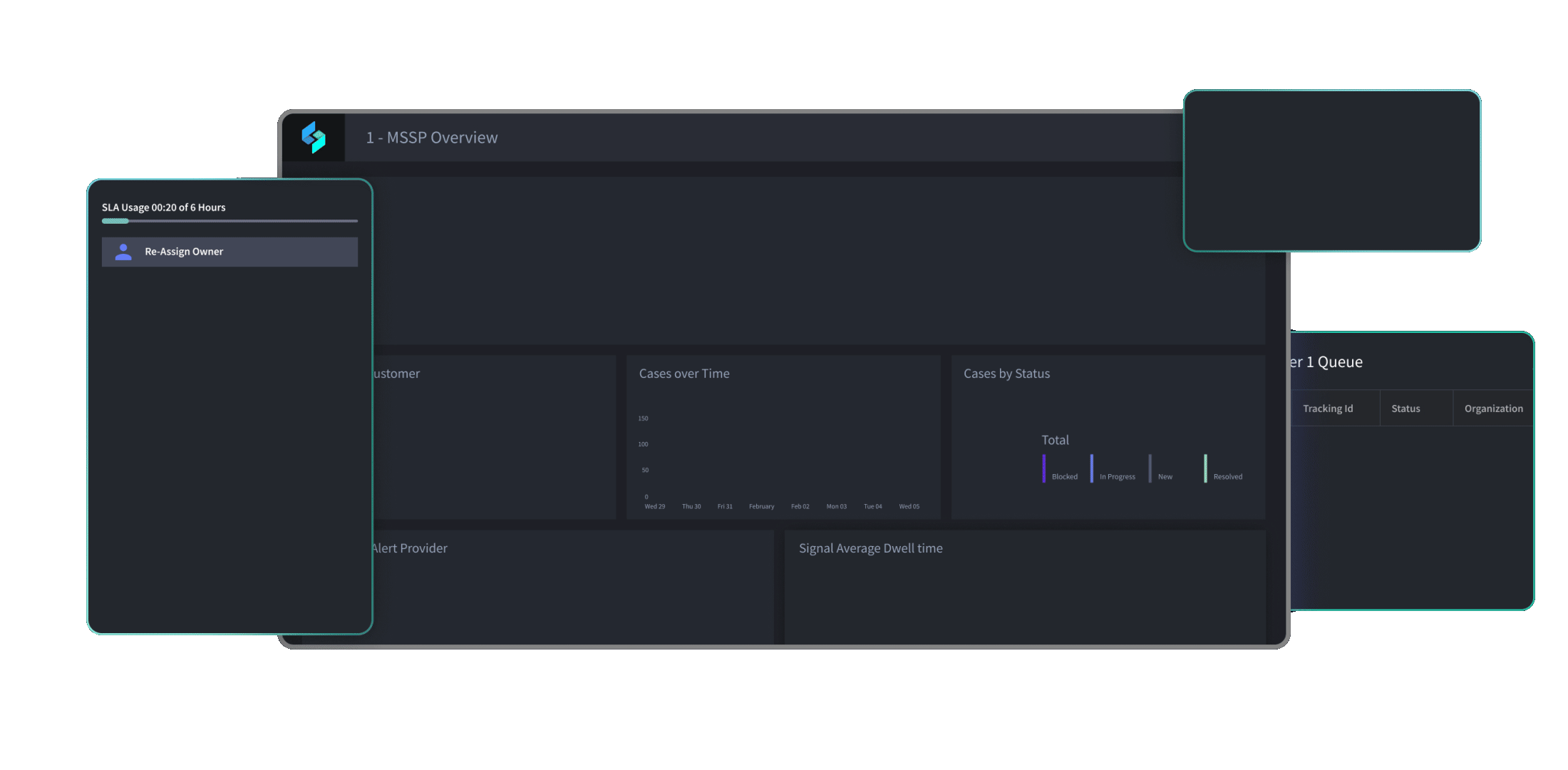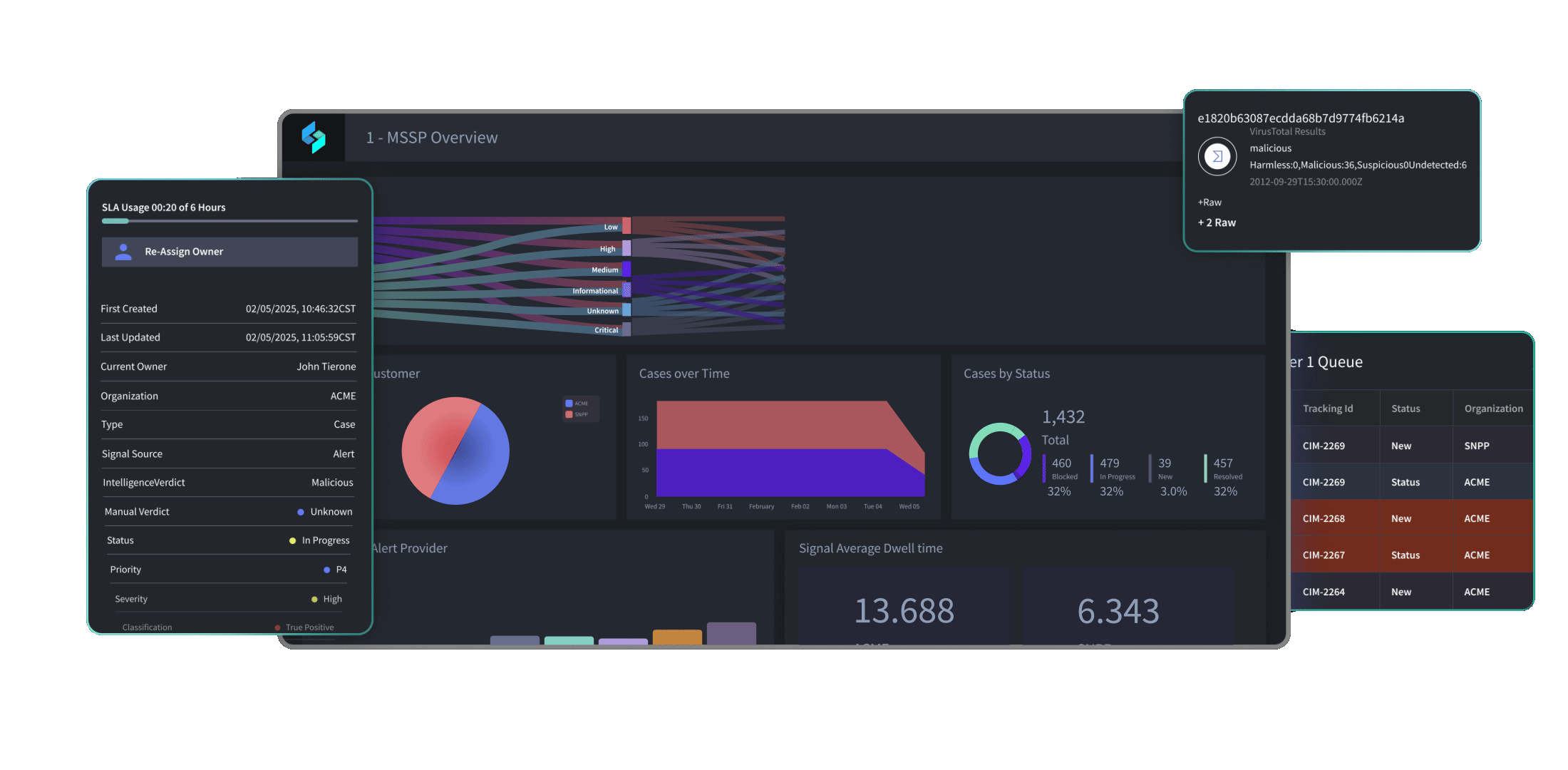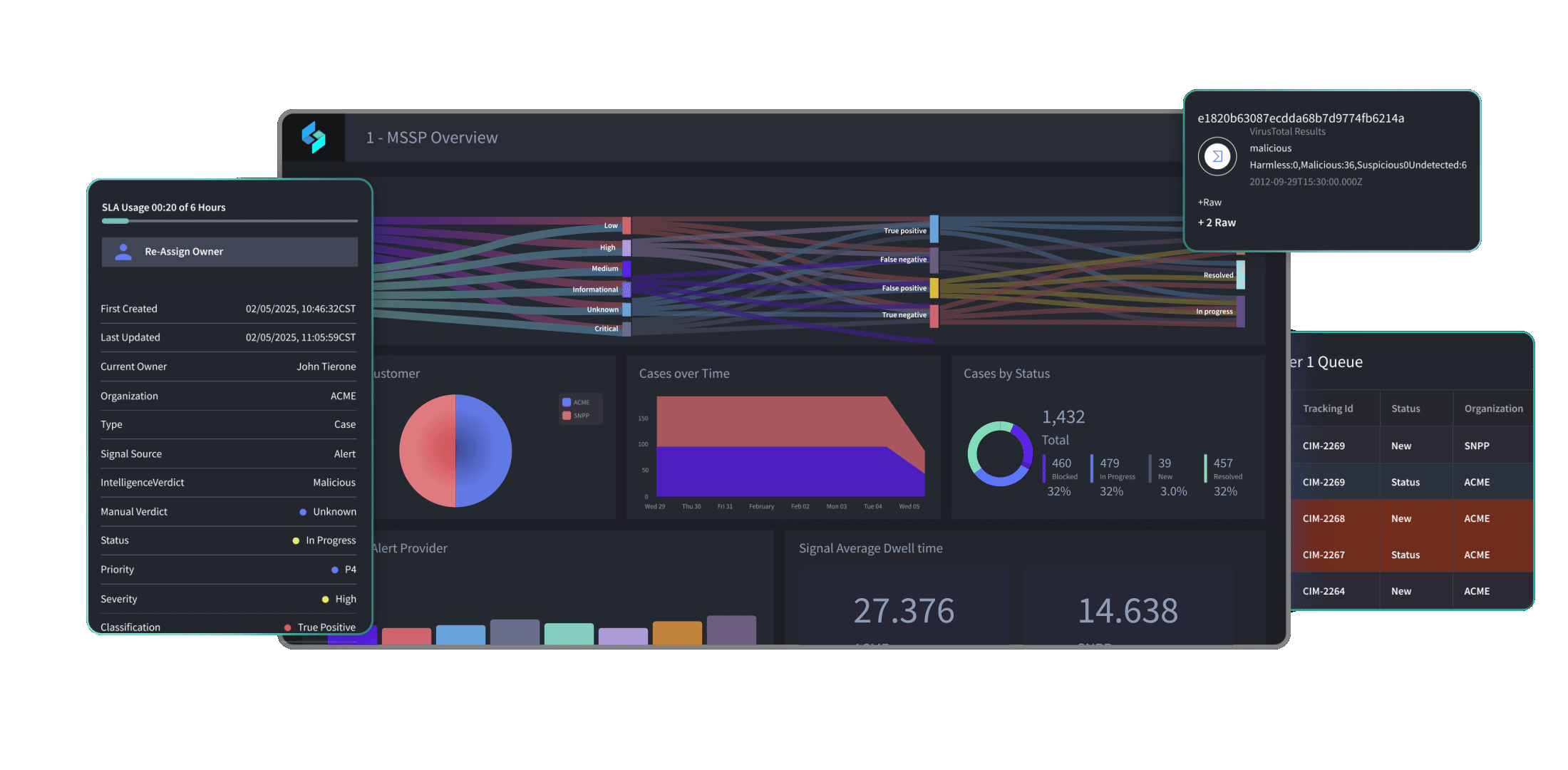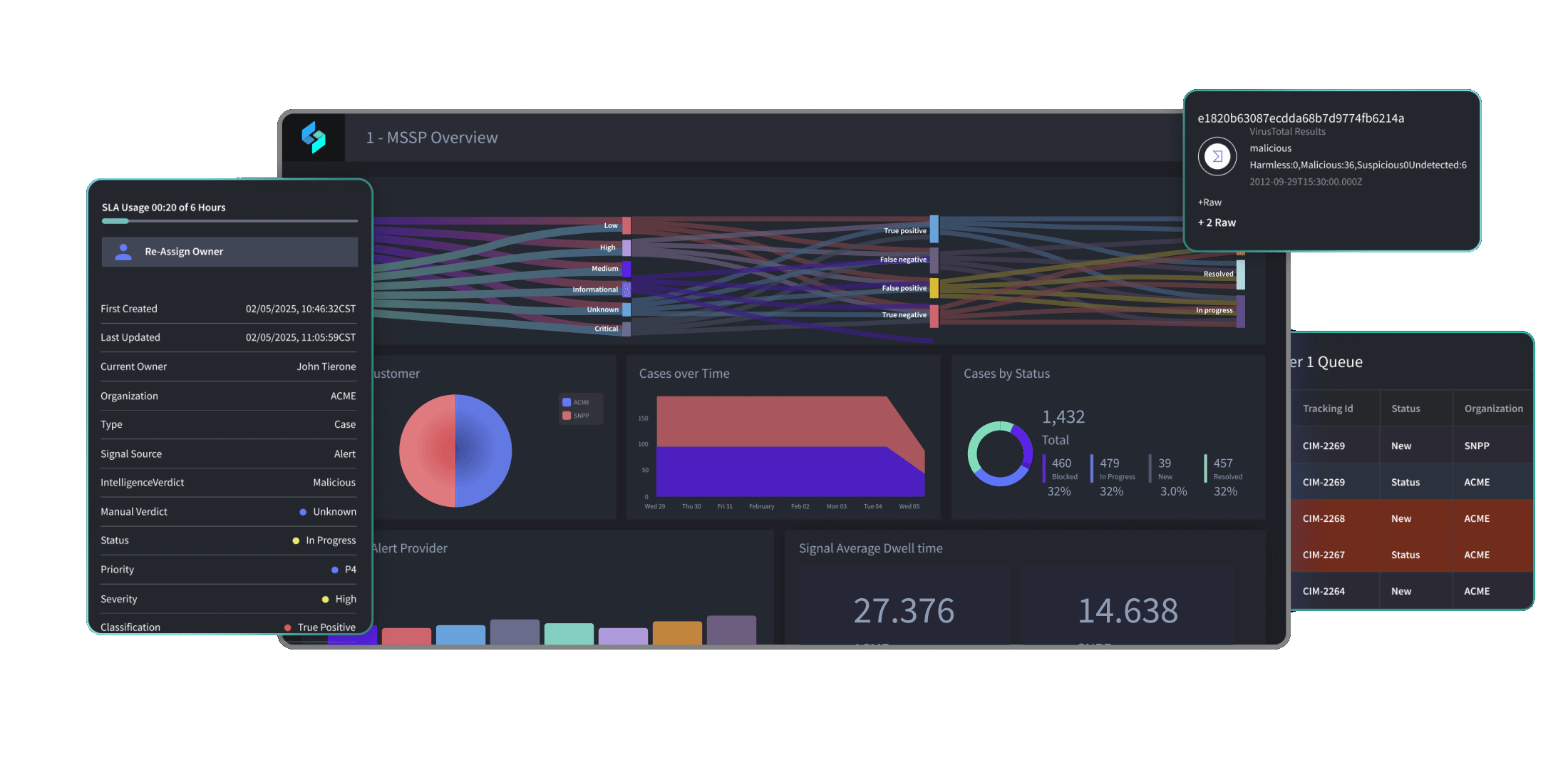
Accelerated migration to Turbine
Bayside needed to migrate two years of automation work to Turbine in just five weeks, over the holidays. Turbine’s cloud-native architecture, combined with the work of the Swimlane Technical Account Managers (TAM) team, enabled them to efficiently translate existing workflows and rebuild. This streamlined process ensured Bayside successfully completed the transition on time, maintaining continuous operations with zero downtime. Pilcher comments: “I did not think this transition was going to happen but it worked, and we were able to keep everything up and running.”
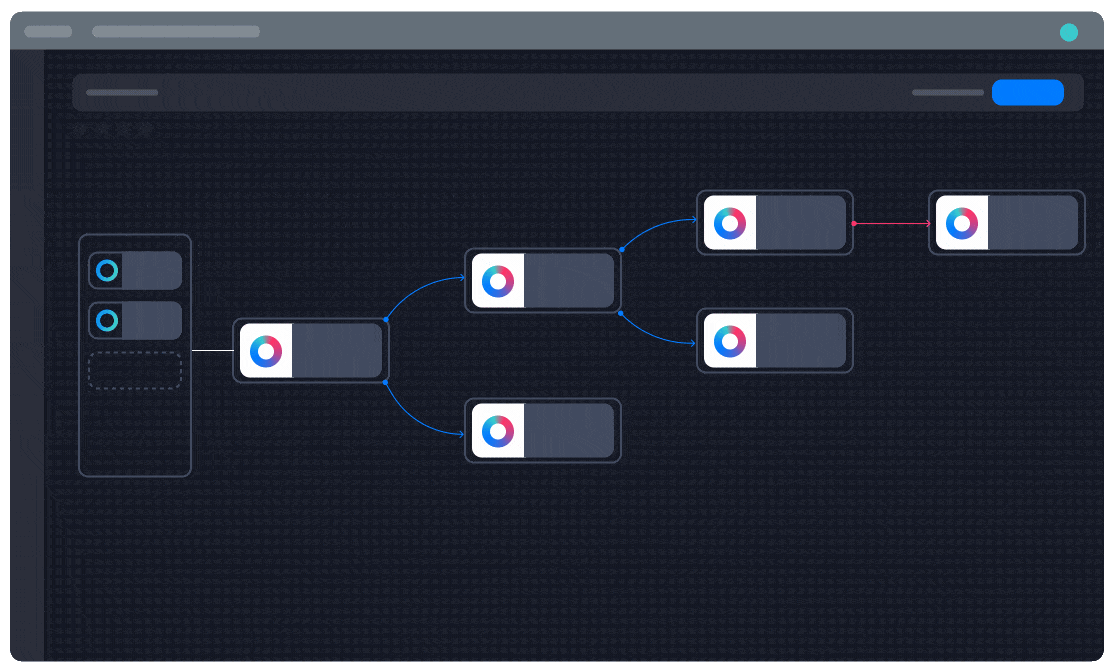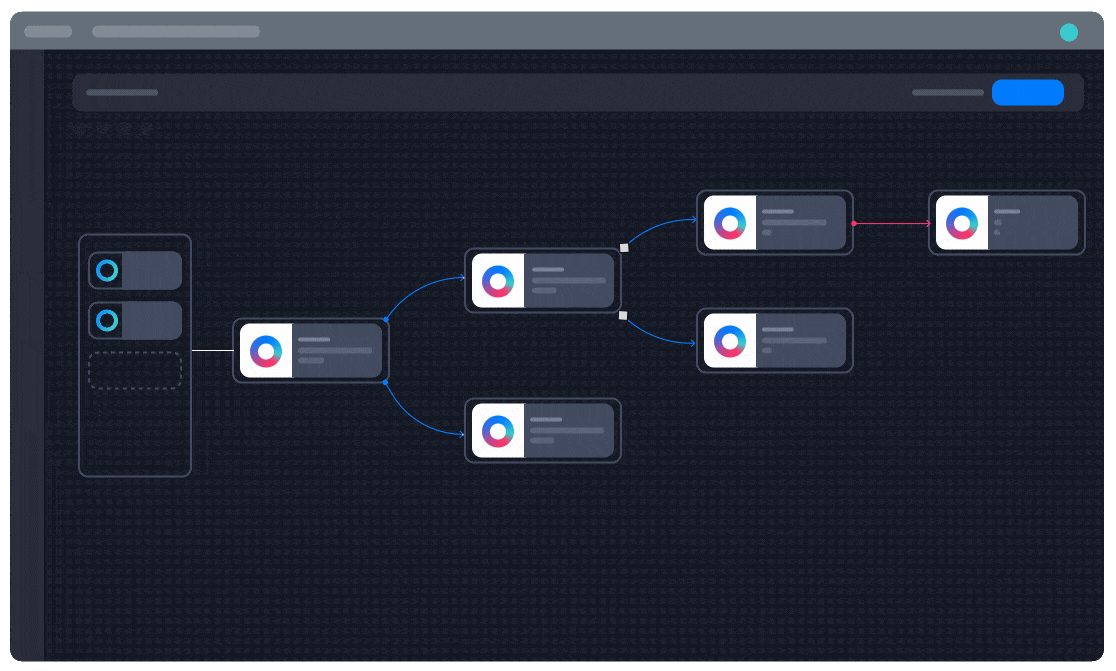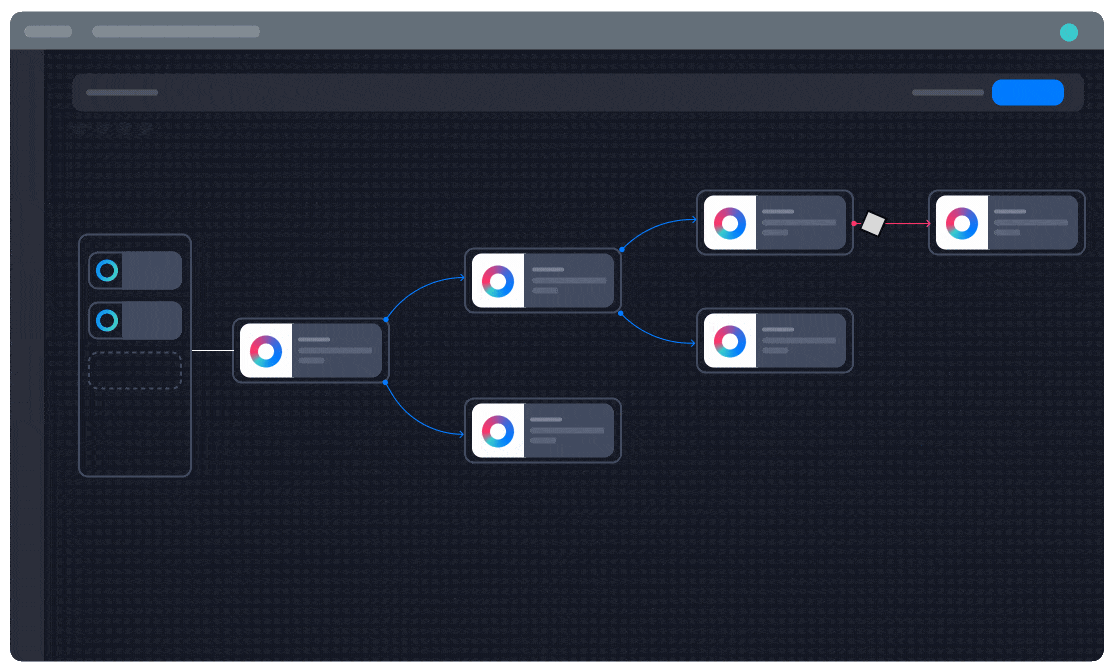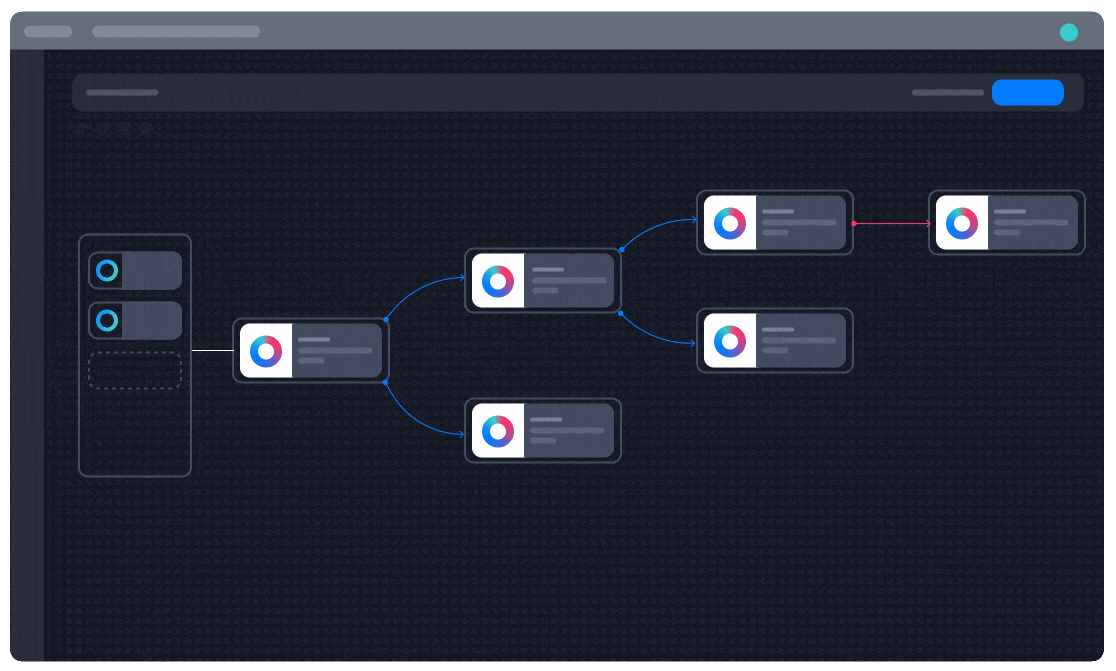
Unparalleled flexibility in automation building
“One of my favorite aspects of Turbine is how easily you can build a playbook and how advanced you can get in the same step,” Pilcher says. Turbine Canvas makes it easy for Bayside to create custom automations by installing pre-built solutions and integrations from Swimlane Marketplace or writing custom Python scripts for entirely unique functionality.
“I recommend Swimlane to my peers because of its incredible automation flexibility. You can go from building playbooks with simple plug-and-play ‘Lego blocks’ to 100% custom Python scripts, all within the same playbook. Turbine offers more flexibility than any other SOAR I’ve used previously.”
Cybersecurity Challenges
OUTCOMES
From 30 minutes to 5 minutes
Bayside reduced the time an analyst spends on each phishing message from 30 minutes to just 5 minutes through Swimlane automation.
40% automated case resolution
Swimlane now fully automates roughly 40% of incoming phishing emails, eliminating manual analyst reviews for those cases.
TAM delivers 5x faster building
Swimlane’s TAMs build automation five times faster, drastically cutting development time for Bayside.
6-8 hours saved by automating the threat containment process
Swimlane automates the crucial 6 to 8-hour email threat containment process, saving both Bayside’s analysts and customer security teams significant time.
Automated phishing pre-analysis
Pre-analysis automation saves 3 to 4 minutes per phishing case by automatically enriching data before analyst review.
Improved Security Posture
Automating processes beyond security, combined with advanced threat intelligence, has strengthened the company’s defenses with a unified approach.
If I had to describe my TAMs in one word, I would say reliable. They’re always there, whether for proactive guidance or immediate support. They’re our strategic partners, guiding us in building new capabilities and continuously improving. Ultimately, it’s about knowing our system is truly stable and optimized.”
Mike Pilcher
Senior Cyber Security Specialist




