reduction in MTTD and MTTR
%
SecOps cut critical Mean Times after Security Orchestration and Response is deployed.
great actionability
x
SecOps increase exponential growth in security actionability
of alerts are missed
%
without SOAR the SOCs can be overwhelmed by the proliferation of alerts
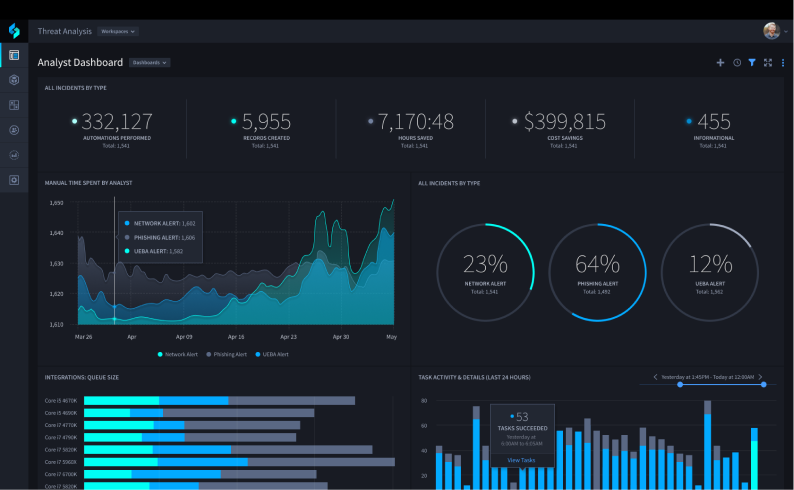
Security Orchestration Enables Machine-Speed Decision Making
Overcome vendor lock in and closed ecosystems by selecting a security orchestration, automation and response (SOAR) platform that can integrate with anything. Comprehensive security orchestration ensures that SecOps teams can access the information they need to execute incident response processes faster.
FEATURES
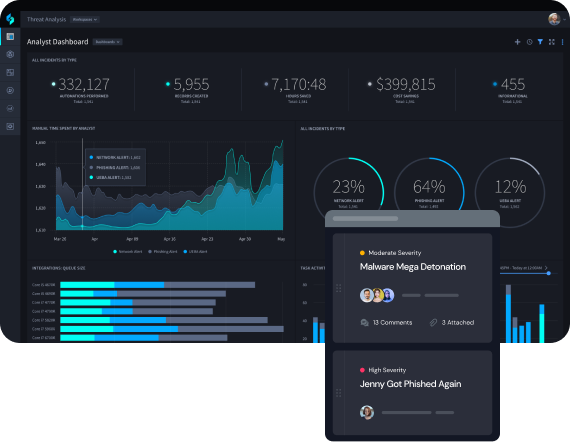
Gain a System of Record for SecOps
Security orchestration combines human and machine data derived from SecOps processes to centralize all disparate data into a single interface that enables faster decision making. This makes it easier to access the data you need to make decisions to quickly mitigate threats and protect your organization.
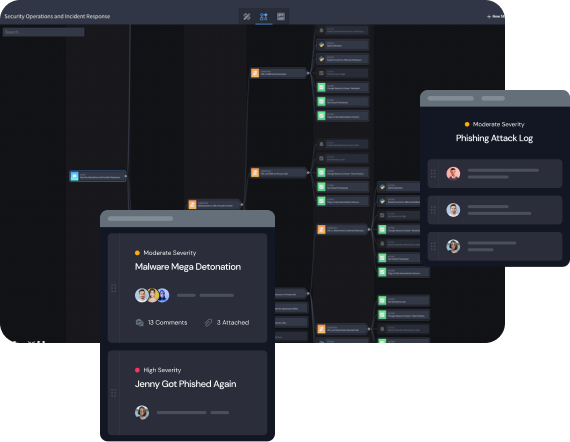
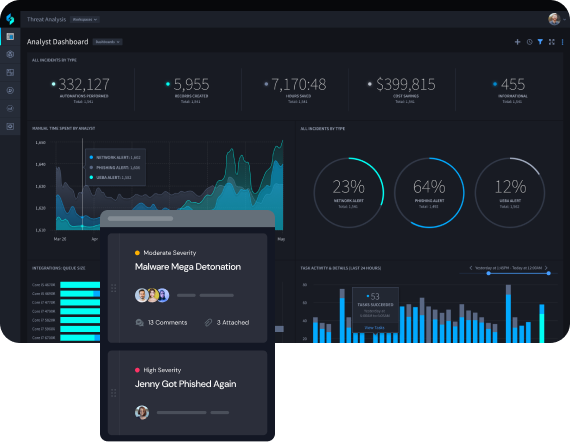
Gain Enhanced Context to Prioritize Alerts
Avoid wasting time and resources by filtering out false positives to immediately highlight critical threat insights. When an attack is part of a broader pattern, Turbine pulls information from threat intelligence and other IOC platforms to quickly understand the problem and facilitate prompt action.
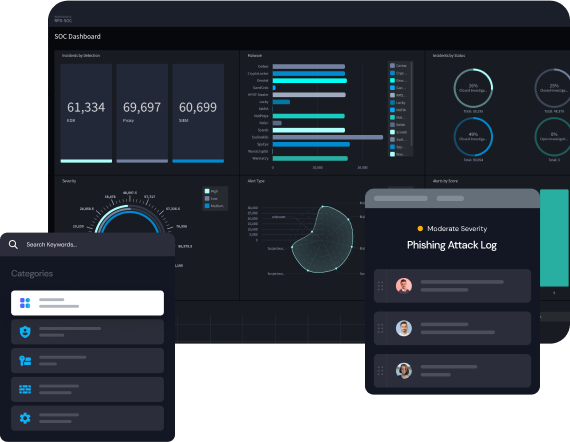
Trigger One-Click Remediation
Security orchestration enables interoperability and management of activities across the entire range of security platforms and related operational tools from a central management console. Turbine’s bi-directional integration makes it so any alert can be responded to with defense-in-depth measures at machine speeds.
Ready to Get Started?