One of the most valuable solutions in a SOC environment is a Security Orchestration, Automation and Response (SOAR) platform. It was designed to add that missing layer of action needed to quickly and efficiently triage alerts, reduce false positives, and provide analysts with the security intelligence they need.
SOAR platforms help security operations (SecOps) teams increase their efficiency by aggregating the proliferating amount of data, turning that data into actionable insights, and then automating a significant percentage of the incident response process.
With SOAR, analysts are enabled to respond to every alert while reducing mean time to resolution (MTTR) with a comprehensive dashboard presenting a full view of alerts and tools along with insights and metrics to help monitor performance—simplifying, automating and documenting the entire incident response process.
But not all SOAR platforms are created equal. When it comes time to evaluate a SOAR platform, here are the 11 questions to ask.
1. What use cases can this solution automate?
One of the biggest things to consider when evaluating a SOAR platform is what use cases it can help your SecOps team with. A good SOAR platform will be able to automate a variety of use cases. Common SOAR use cases include:
-
Automated phishing investigation and response
-
SIEM & EDR alert triage
-
Automated threat intelligence management
-
Malware containment
These use cases are a good starting point, but there may be industry-specific use cases your organization needs to automate. Look for less common (yet equally important) use cases such as fraud investigation and response, insider threats, employee onboarding/offboarding and more.
2. Can it integrate with any API?
Ensure that the SOAR platform can integrate with a diverse range of formats and sources – especially your current tech stack. An ecosystem-agnostic SOAR solution should also be able to integrate with elements that aren’t in a typical SecOps environment.
It should go beyond SIEM, EDR and threat intelligence tools to include telemetry from cloud and IoT devices, data centers and edge computing sources. Be mindful of any vendor lock-ins and integration limitations.
3. Is there a dependency on developers to integrate with APIs?
Similarly, consider how dependent integrations are on developer support. Will you need to budget for dedicated in-house or outsourced developers to integrate with specific APIs? That reduces the overall return on investment (ROI) you could expect from the SOAR platform.
Modern SOAR platforms utilize stable, portable and reliable connections to any API to simplify integrations.
4. How much coding is required by analysts?
Historically, SOAR solutions have been complicated, rigid and hard to work with. Success with legacy SOAR platforms relied on developer involvement. In today’s security climate, staffing shortages and the global skills gap make it harder to find analysts with advanced coding capabilities.
Security leaders should look for a SOAR platform that removes coding demands from analysts’ workloads. Not only will this save security analysts time, but also improve job satisfaction by allowing analysts to investigate business-critical threats.
5. What is the process for building playbooks?
A valuable SOAR platform’s playbooks will be simple enough on the technical side for tier-one analysts and domain experts to build. At the same time, it won’t compromise the sophistication of automation power. Look for a solution that utilizes a human-readable playbook builder so security teams can practice their craft in an efficient, customizable environment.
Your SOAR solution should have a drag-and-drop UI for building and modifying playbooks, without getting bogged down by scripting.
6. Can playbooks be customized to your business processes?
A robust workflow builder should work with custom code as well as out-of-the-box content to allow for adaptation to any organizational environment. Look for SOAR vendors that have other customers in your industry, such as Critical Infrastructure, Financial Services and MSSPs. The demands of these organizations require customized solutions for successful visibility across unique systems.
7. Does the platform have built-in case management?
Case management should be more than just a repository. Individual case records should be fully interactive, automatically adapting to show the data you need. Much like Salesforce for sales, Workday for HR professionals or ServiceNow for IT, your SOAR platform should act as a centralized management hub for all security. It should be able to capture machine data and automated functions, as well as human decisions during response processes.
A SOAR platform should truly be a “system of record” across the entire tech stack. Make sure it can provide visibility and reporting across ecosystems to provide actionable intelligence to stakeholders across the organization.
8. Can dashboards be created to present Key Performance Indicators (KPIs)?
You should have unlimited ability to create and modify dashboards to display data to fit your needs. Dashboards should be intuitive and easy to customize for a range of users, such as SOC managers, CISOs and even the Board of Directors.
Worthwhile SOAR platforms combine human and machine intelligence through case management, dashboard, and reporting functionalities. This makes it easier for SecOps to gain actionable insights through KPI metrics like MTTD, MTTR, and MITRE ATTACK framework benchmarks.
9. Will it be able to still meet KPIs if we grow or scale?
Make sure the SOAR platform is able to ingest bigger and more diverse data sets from hard-to-reach places. Ensure that your solution can speed up security performance like Mean Time to Resolution (MTTR) and reduce dwell time; this will require throughput and processing power beyond what most SOAR solutions offer.
A SOAR platform should have a long shelf-life that grows and scales with your SOC. The most capable SOAR solutions will be able to ingest great volumes and diverse types of datasets. Look for solution features that help with this, such as distributed big data ingestion, inline enrichment, pre-processing and related functionality.
10. How does it align with the sector-specific regulatory laws and industry standards?
Organizations across industries struggle with an ever-growing list of industry rules and compliance requirements. To address this challenge, the SOAR platform should automate beyond security controls and procedures. It should capture and automate the document and reporting of all security activities to ensure compliance and avoid regulatory violations.
Look for a SOAR platform that offers simplicity in documentation and compliance reporting. This is the key to less headache down the road.
11. What is the expected ROI?
Security budgets continue to be constrained, so every new investment must be worthwhile. The value of a SOAR platform should speak for itself – if it’s valuable. Estimated savings from staff salaries, staff support (including training, tools, etc.), additional security tools and response costs should all be worthwhile. A trusted SOAR vendor will provide transparency into upfront and recurring costs to help calculate the solution’s ROI.
SOAR is an integral security product within most organizations, serving to automate key security processes and respond to incidents. To ensure the SOAR platform your organization chooses will provide the greatest ROI, it’s important to ask yourself (and your vendor) questions that will help you select the best platform for your needs.
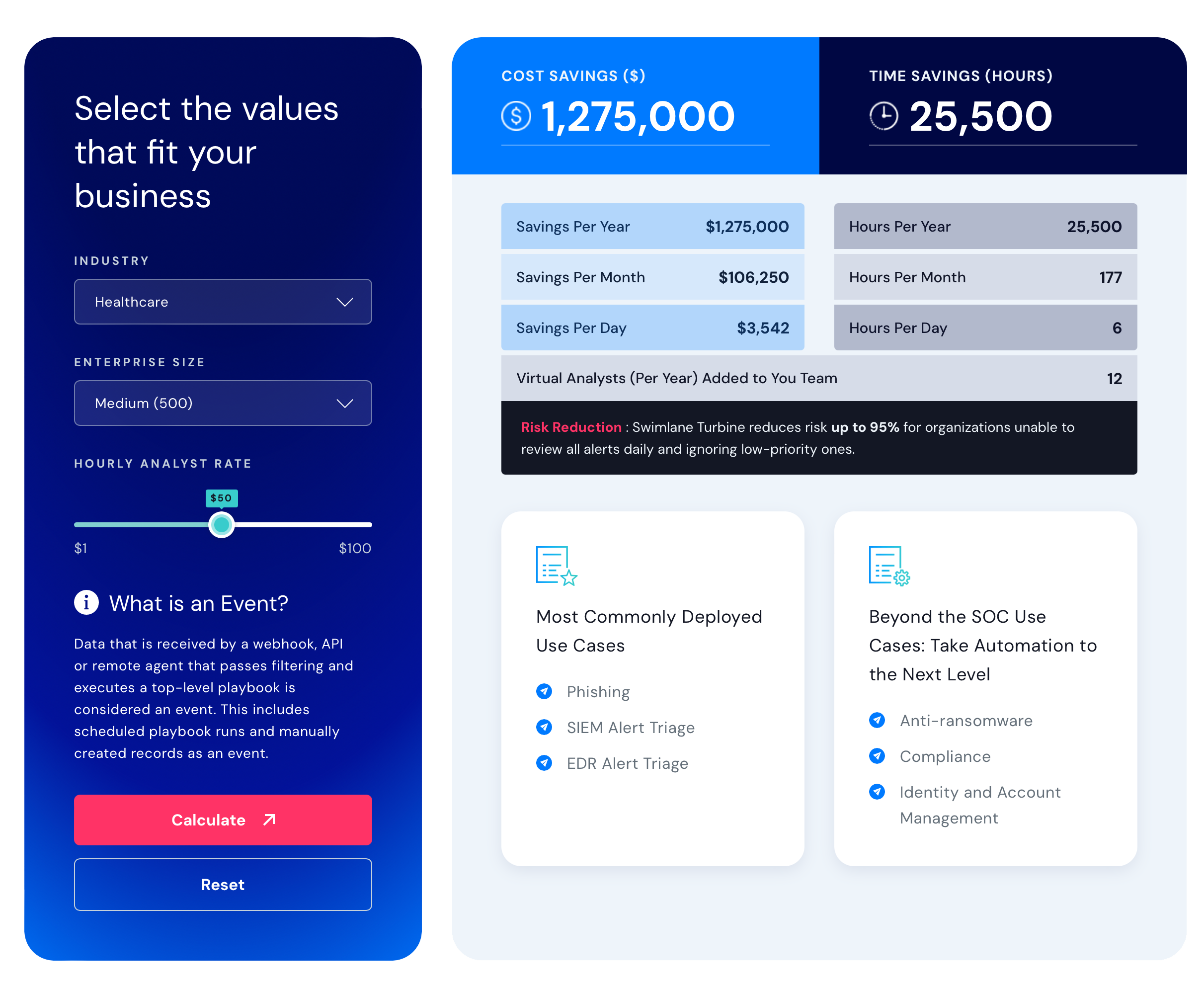
Swimlane ROI calculator
Estimate the savings you can achieve with Swimlane Turbine.


