Ensuring your organization is protected from the cyberattacks that threaten businesses can be a daunting task. As a result, many companies implement a composite of security solutions to protect them from all sides. Each of those solutions produces their own security alerts which require investigation by security operations (SecOps) teams. SecOps then becomes overwhelmed with alerts– which can lead to burnout, staff turnover and ultimately an organization vulnerable to threats.
Utilizing a comprehensive security automation and orchestration solution to improve your incident alert management process is the best way to ensure your organization is protected and hold onto your valuable SecOps employees.
The problem: There are too many alerts…
The importance of having security solutions in place to protect your organization cannot be emphasized enough. Just in 2017, there have been numerous cyberattacks that halted business operations and impacted companies in over 100 countries. To prevent these types of attacks, security systems must issue alerts to the SecOps team to draw their attention to potentially suspicious activity for further investigation.
Unfortunately, the number of security alerts that many solutions generate has put organizations in a “boy who cried wolf” situation. Large enterprises receive between 10,000 and 150,000 security alerts per day, making it impossible to manually investigate every alert, especially when organizations lack the staff and resources to do so. As a result, up to 70 percent of alerts are ignored and every alert ignored could lead to a breach.
…And alert triage is a popular but faulty solution.
Many organizations rely on alert triage for incident alert management. Alert triage allows SecOps teams to scan alerts based on specific criteria, quickly determine the likely seriousness of the threat, and prioritize investigations accordingly. Although this seems like a viable solution, it can easily lead to missing a real attack. It is just not possible to ignore large volumes of alerts and still fully defend your organization.
Current incident alert management processes:
- Are unable to keep up with evolving threats: Cyber threats are constantly evolving, so alert evaluation processes must evolve with them. But many organizations utilize the same criteria for alert triage for years, and can’t (or don’t) modify criteria as new attacks or techniques enter the cybersphere. The result is that they are unable to catch the latest and most dangerous threats.
- Have integration complications: All of your security tools need to integrate both with each other and your custom processes. Many tools designed to integrate disparate security solutions still require SecOps teams to complete manual research and investigations, which significantly slows down response times.
- Rely on tribal knowledge: Cybersecurity employees build up an informal knowledge base that helps them complete their job duties. Given the repetitive nature of cybersecurity work, staff turnover is common. When employees leave, that informal knowledge base is lost and every new employee has to start with incomplete and disparate information.
- Don’t provide enough context: Many solutions generate alerts but don’t provide enough information for staff to fully understand the issue, forcing them to perform manual investigations which further slows them down.
- Take place on too many disparate screens and applications: If SecOps teams use multiple solutions, it is likely that each tool generates separate alerts. Without any centralization of these alerts, understanding the complete security picture is slow and challenging.
Security automation and orchestration is the answer
Security automation and orchestration is popular in the cybersecurity field, commonly suggested as a solution to a variety of security management issues. Individually these terms are defined as:
- Security automation is the use of automated systems to detect and prevent cyber threats, while also contributing to the overall threat intelligence of an organization to help better prepare and defend against future attacks.
- Security orchestration is the process of bringing together numerous tools and resources to work together harmoniously to improve an organization’s security operations.
Working together, security automation and orchestration improves security workflows, processes and overall alert management by removing slow manual intervention tasks and replacing them with machine-speed decision making and response. It works within your security infrastructure to integrate the tools you already have to better serve your organization.
How Swimlane can help
Swimlane utilizes security automation and orchestration to help you improve your incident alert management process. It allows your organization to:
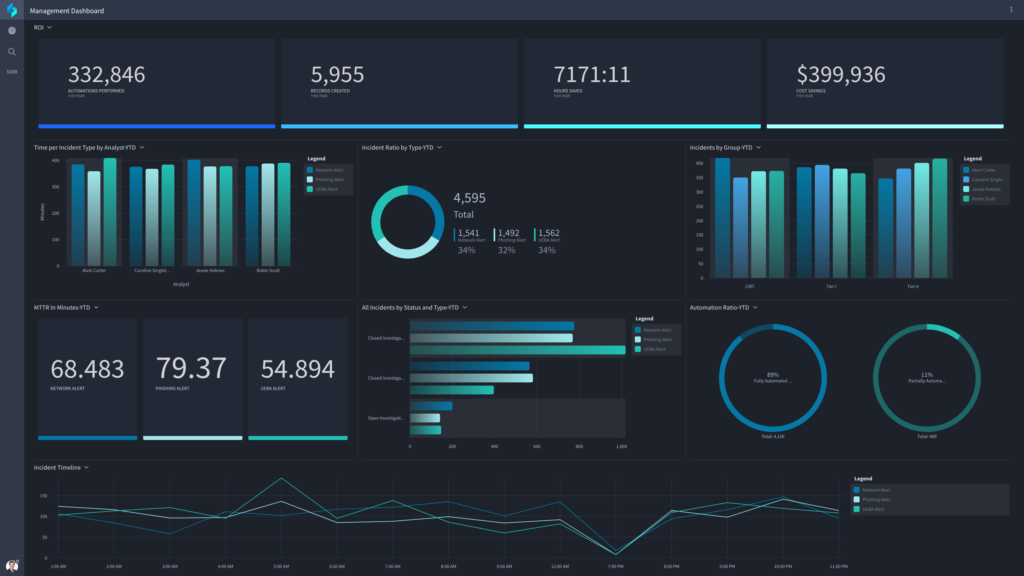
- Centralize security operations: Centralized dashboards integrate data from all of your existing solutions using API-first architecture. This provides your SecOps team with more context surrounding alerts and a more comprehensive view of the state of security within your organization.
- Automate tedious tasks: 80 to 90 percent of security tasks can be automated to some extent. Utilizing automation allows SecOps teams to handle more alerts, in the same amount of time using your existing staff.
- Reduce management complexity: Today, organizations rely on multiple solutions, vendors and teams to secure their critical systems and data, which can make managing security a nightmare. Security automation and orchestration helps you coordinate your vendors and tools and enables you to better leverage their capabilities.
All of the benefits of security automation and orchestration come together to reduce the overall mean time to resolution (MTTR) and significantly improve protection for your organization. Utilizing Swimlane is the answer to refining your incident alert management process so you can respond to every alert and defend your organization from all cyber threats.
Want to know how security automation and orchestration is utilized in the real world? Download our eBook: 8 Real World Use Cases for Security Automation and Orchestration.
Interested in learning more about Swimlane? Contact us or schedule a demo.


