Norsk Hydro ASA, one of the largest aluminium companies worldwide, has fallen victim to a severe cyber attack. In a press release on March 19, 2019, the Norwegian-based company announced, “Hydro became victim of an extensive cyber-attack in the early hours of Tuesday (CET) [March 19, 2019], impacting operations in several of the company’s business areas … Hydro has isolated all plants and operations and is switching to manual operations and procedures as far as possible.” Signs were posted at Norsk Hydro facilities advising users to not connect to the company network and to disconnect all devices from the network.
“This is a classic ransomware attack,” Chief Financial Officer Eivind Kallevik said during a news conference. “The situation is quite severe.”
The ransomware that has infected Norsk Hydro networks is known as LockerGoga. Let’s take a look at the ransomware behind this attack, and discuss the potential damages this ransomware could have on critical infrastructure.
What is LockerGoga?
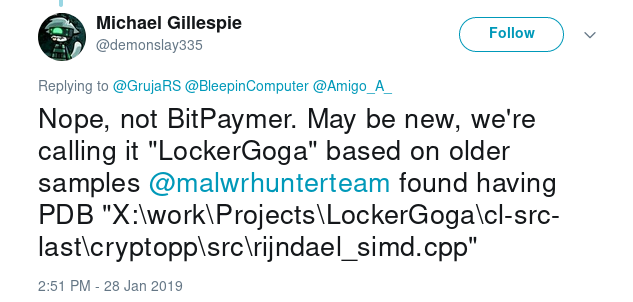
LockerGoga is a new ransomware targeting Windows systems that was first encountered by the @malwrhunterteam early this year. LockerGoga became known after it was used in a cyberattack in late January against Altran Technologies, a French engineering company.
Windows portable executable (PE) ransomware samples of LockerGoga have included debug metadata in the form of Program DataBase (PDB) file path names. The PDB paths extracted from the binary contained the malware authors local system paths which state the name of the ransomware:
`X:\work\Projects\LockerGoga\cl-src-last\cryptopp\src\rijndael_simd.cpp`
Malware researchers noted similarities between LockerGoga and the BitPaymer ransomware, which infected the PGA of America last year. The ransom note, extortion methods, file names, and encrypted file extension are all very similar to techniques used by LockerGoga. However, according to malware researchers, these similarities are only found at the surface:
An early LockerGoga variant from the Altran attack can be seen here (submitted on January 25th).
Upon execution the LockerGoga ransomware encrypts many well-known file types including:
.doc, .docb, .docx, .dot, .dotx, .pdf, .pot, .potx, .pps, .ppsx, .ppt, .pptx,. sldx, .wbk, .xlm, .xlsb, .xlsx, .xltx, .xlw
These encrypted files are renamed with a .locked extension.
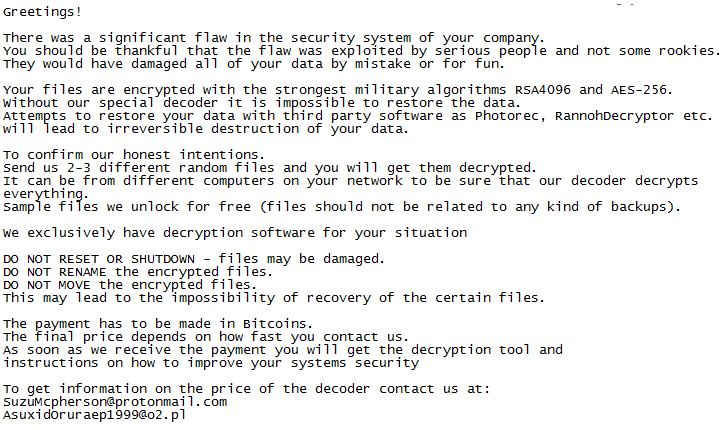
A ransom note is placed on the users Desktop (C:\Users\<User>\Desktop\README_LOCKED.txt), which demands victims to email the extortionists to pay a Bitcoin (BTC) ransom. The email addresses used for the extortion include ProtonMail (a Swiss privacy-oriented email provider) and o2 (a Polish internet services company).
Tuesday morning, @malwrhunterteam identified a signed LockerGoga sample uploaded to VirusTotal from Norway, and it is speculated to be a sample of the LockerGoga variant that infected Norsk Hydro. The sample was signed with a valid certificate issued by Sectigo RSA Code Signing CA, the certificate was later revoked just hours after the attack:
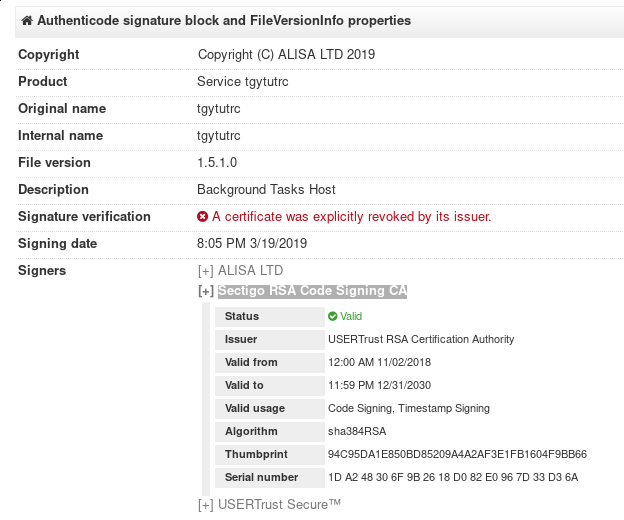
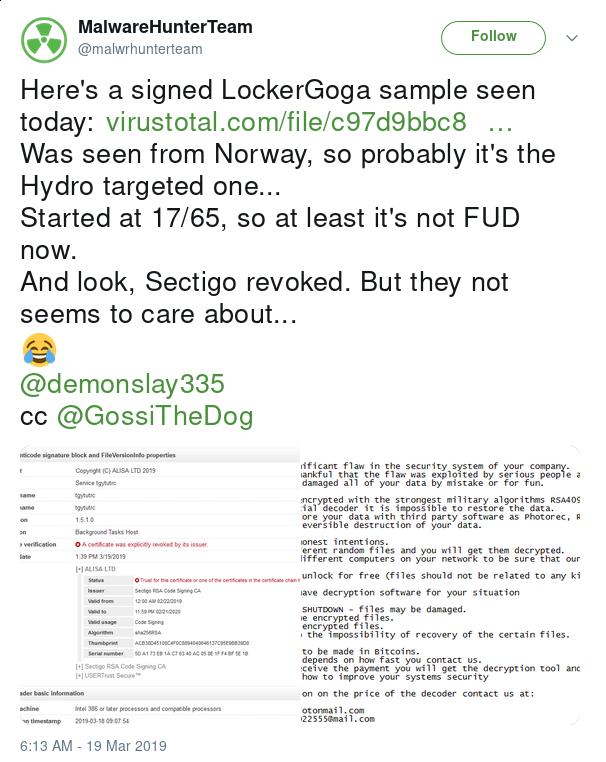
However, additional variants of LockerGoga are actively being found in the wild signed by valid certificates from Sectigo RSA Code Signing CA.
Propagation
The LockerGoga ransomware is surprisingly bare-bones. It doesn’t use any network communications. There’s no C2, DNS, or propagation methods used by the malware at all.
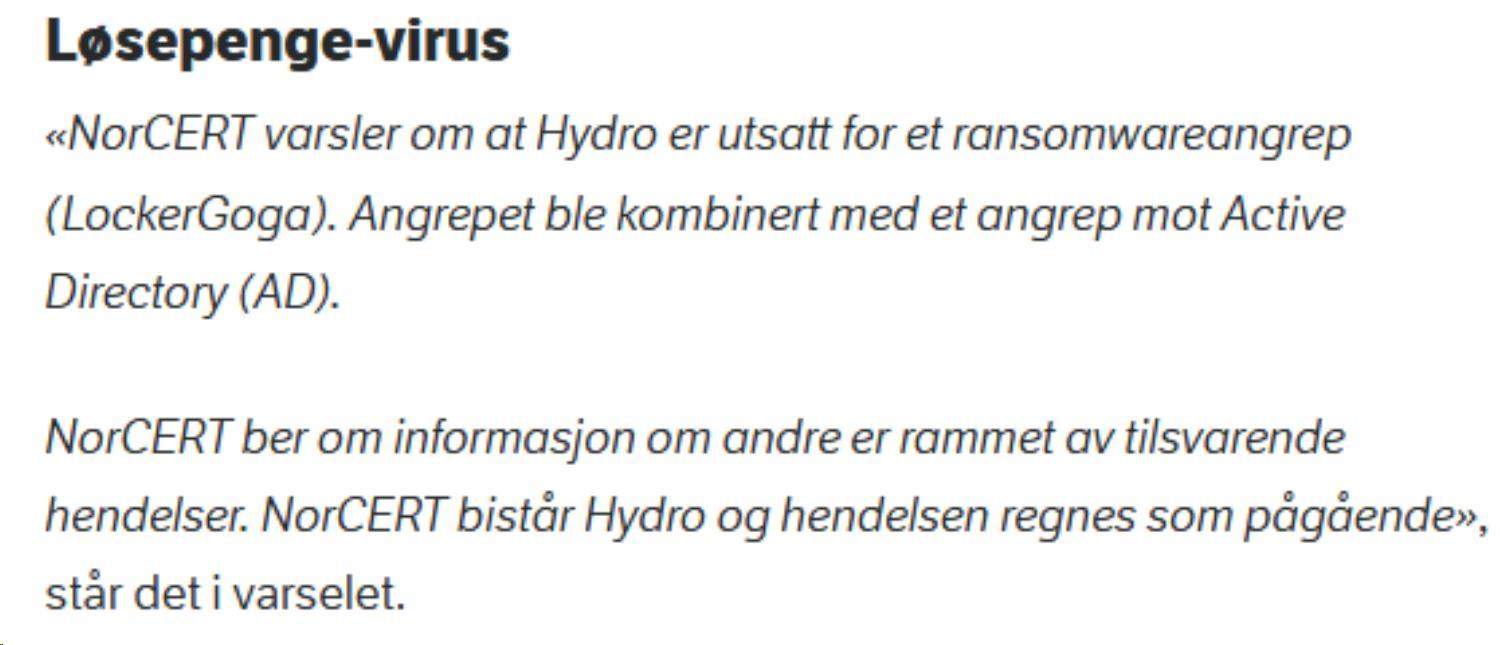
NorCert (Norway’s National Computer Emergency Response Team) stated in an announcement about the attack that the perpetrators used Windows Active Directory (AD) to spread the ransomware:
“NorCERT warns that Hydro is exposed to a LockerGoga attack. The attack was combined with an attack on Active Directory (AD).
NorCERT asks for information from others affected by similar events. NorCERT is assisting Hydro and the incident is considered ongoing.”
If the attackers were able to compromise a system to gain Domain Admin access, the LockerGoga ransomware could have been scripted to propagate across Domain Controllers to infect systems domain-wide using a forced GPO (Group Policy Object) update.
Potential Effects of a Cyber Attack on an Aluminium Plant
More recent press releases from Norsk Hydro have indicated that industrial control systems were not affected in the attack. However, PLC’s (Programmable Logic Controllers), ICS engineer laptops, and SCADA (Supervisory Control and Data Acquisition) systems that often interact, control or monitor ICS systems commonly run Windows operating systems, and it wouldn’t be unheard of for these systems to be—regrettably—connected to the same domain as the userland.

The potential effects of a cyberattack on ICS infrastructure at an aluminium plant would be particularly disastrous. Aluminium smelting involves an electrolysis process that requires immense amounts of electricity. This is why aluminium smelters are commonly found close to hydroelectric power plants. The immense amount of electricity is required due to the amount of heat that’s needed to smelt aluminium. Aluminium smelters have many cells—sometimes called pots— in which electrolysis takes place, these pots are required to be kept hot during operation. For perspective, damage begins to occur when the pot has been cooled to 900°C.
If a power outage, disruption, or other event occurs which allows these electrolysis cells to cool it can cause serious damage to the cells. Repairing or replacing these cells can be a heavy financial burden for a company.
Just last week blackouts in Venezuela have brought the Venezuelan aluminium industry to it’s knees:
“State-owned aluminium smelter Venalum’s remaining operational units and state-owned Bauxilum’s
alumina production units were destroyed by the blackout and likely will not be repaired for at
least a year, a senior Venalum official said. ‘The primary aluminium and alumina sectors are
dead for the foreseeable future.'”
However, smelting can, of course, be controlled manually and that’s what Norsk Hydro was forced to do today:
“As Hydro wanted to prevent the virus from spreading to several parts of the company’s infrastructure,
the industrial giant cut the contact with the computer systems, and thus had to factory-communicate
the telephone and keep the operation running manually.
So it was the older employees who showed the knowledge today? ‘Yes, it was the old wolves who remembered how it was done in the past,’ says an employee at a Hydro
factory in Høyanger.”
Additional Details
Associated Emails:
[email protected] [email protected] [email protected] [email protected] [email protected] [email protected] [email protected] [email protected] [email protected] [email protected] [email protected] [email protected]
File names:
tgytutrc7290.exe yxugwjud6698.exe LockerGoga.exe LockerGoga Lockergoga.exe
Hashes:
tgytutrc7290.exe
MD5 - e11502659f6b5c5bd9f78f534bc38fea SHA1 - b5fd5c913de8cbb8565d3c7c67c0fbaa4090122b SHA256 - c97d9bbc80b573bdeeda3812f4d00e5183493dd0d5805e2508728f65977dda15 ssdeep - 24576:645Rt4El7fc/TFJzjJUgrrCq5sNIwQsUGy1q7a9DlIACTp+kqGslRG:Rjt4El7fc/TFJWstwQsPdSDuACTpqhG authentihash - 8b94b05081c3b6f4518461f884199cd092762762704cf37d06793393d9b82dcb imphash - ce51c671c94cce6379a0f6823fad4112
yxugwjud6698.exe
MD5 - 16bcc3b7f32c41e7c7222bf37fe39fe6 SHA1 - a25bc5442c86bdeb0dec6583f0e80e241745fb73 SHA256 - eda26a1cd80aac1c42cdbba9af813d9c4bc81f6052080bc33435d1e076e75aa0 ssdeep - 24576:uj/6CtkHRos9l+zan4Q6eQqF5ZgQibE2zkMiJHic9OuTw258tox6T9G0SKoRl:A/NtkHRos9l+zan4QTB/2zkPtBq2itoP authentihash - 6d0054dc32616687d9dbbc3cfe7148be157751b9bdfe55ace21a7aa46dd32be3 imphash - 5ac063140bb65ee6bf5852bb45b1e9b6
Sources
- https://techcrunch.com/2019/03/19/norsk-hydro-ransomware/
- http://www.correodelcaroni.com/index.php/economia/1506-apagon-liquido-las-73-celdas-de-reduccion-de-aluminio-de-venalum-y-alcasa
- https://www.bloomberg.com/news/articles/2019-03-19/hydro-says-victim-of-extensive-cyber-attack-impacting-operations-jtfgz6td
- https://www.bleepingcomputer.com/news/security/new-lockergoga-ransomware-allegedly-used-in-altran-attack/
- https://devblogs.microsoft.com/cppblog/whats-inside-a-pdb-file/
- https://www.bleepingcomputer.com/news/security/the-pga-possibly-infected-with-the-bitpaymer-ransomware/
- https://www.forbes.com/sites/leemathews/2018/08/09/pga-computers-hit-by-ransomware-infection/#22f3bad565a4
- https://twitter.com/GrujaRS/status/1089964491725590528
- https://www.nrk.no/norge/skreddersydd-dobbeltangrep-mot-hydro-1.14480202
- https://www.aluminiumtoday.com/contentimages/features/Oyeweb.pdf
- https://www.argusmedia.com/en/news/1863707-venezuelas-fragile-power-grid-partially-restored
- https://e24.no/boers-og-finans/norsk-hydro/dataangrepet-lammet-fabrikk-nettverkene-vi-maatte-gaa-tilbake-til-penn-papir-og-kalkulator/24585470


