Swimlane and Blackberry Cylance have partnered to offer a new use case that combines the power of security orchestration, automation and response (SOAR) with Cylance PROTECT’s integrated threat prevention solution. The Proactive Endpoint Threat Response use case utilizes our integration to take a proactive response to detections identified by Cylance PROTECT.
By ingesting detections from Cylance PROTECT, Swimlane can automate and orchestrate the enrichment of detections using multiple open source intelligence (OSINT) platforms to identify malicious files proactively that are similar or related to a specific variant identified by Cylance. Swimlane then automatically pulls the related samples and feeds them back into Cylance to enhance your protection from future threats.
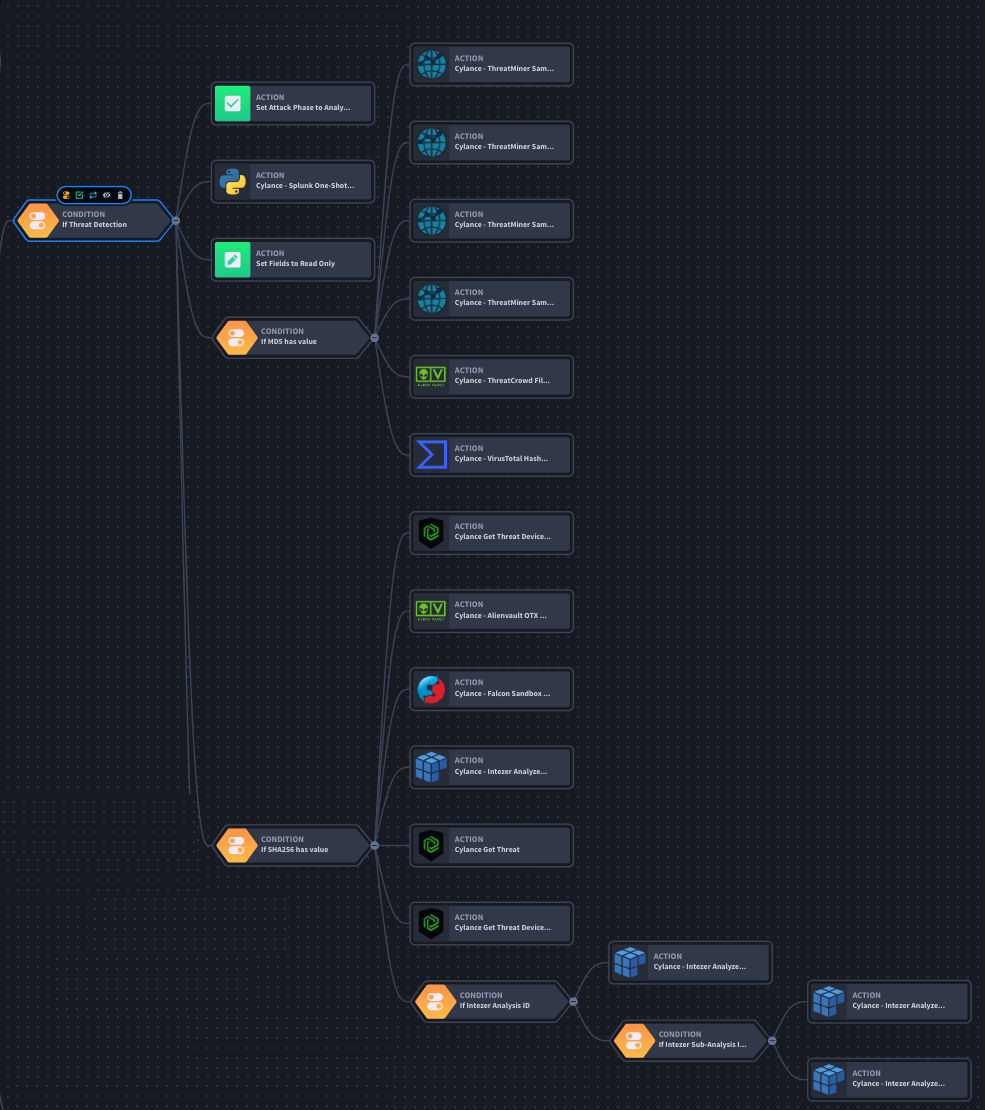
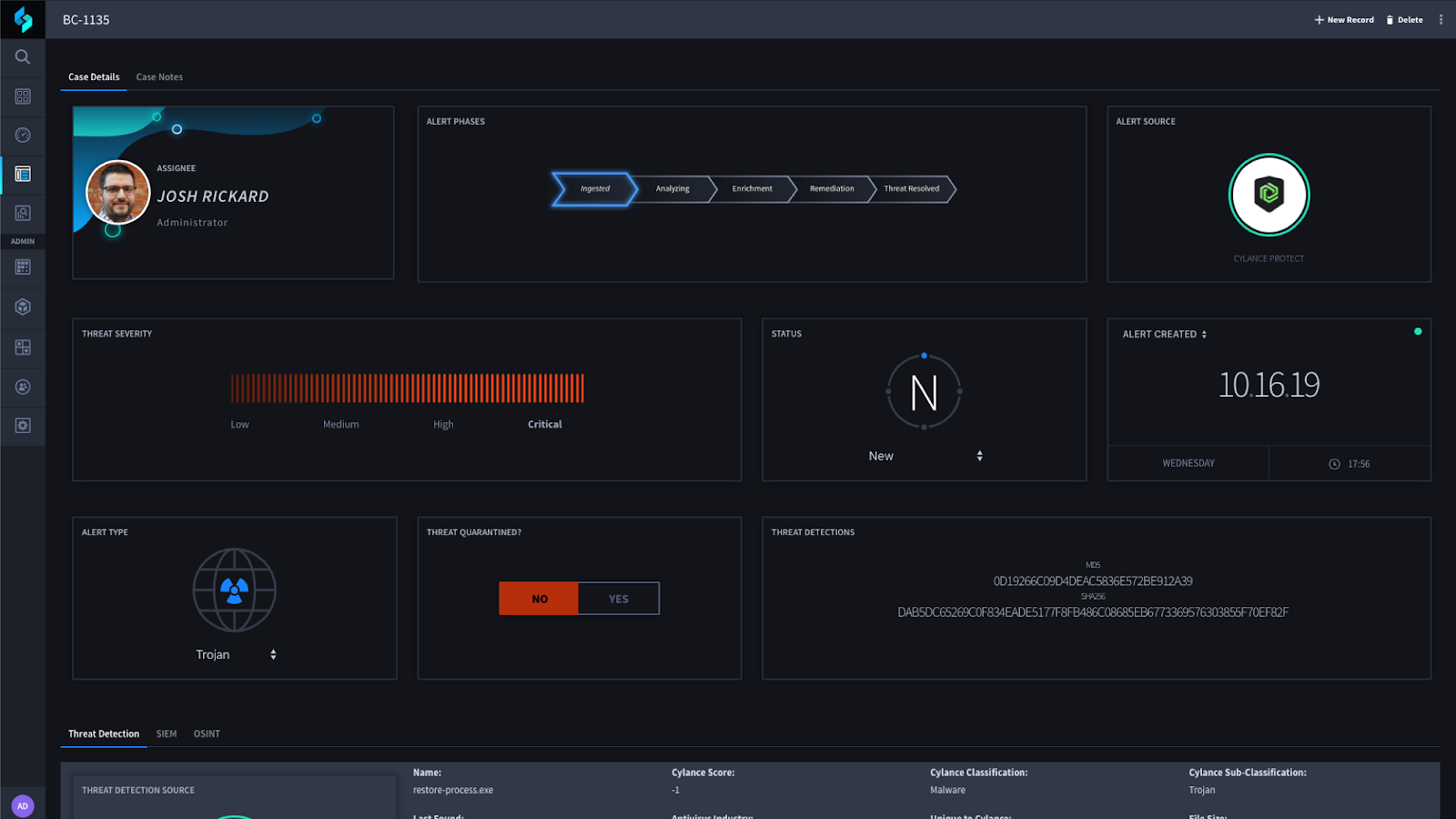
By utilizing widgets within your Swimlane applications you can easily display the relevant information about the detection without having to continually review multiple different text fields. This enables a security analyst to quickly view the problem and any actions that need to be taken.
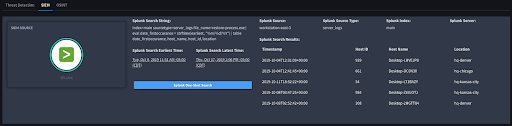
Once a detection has entered the enrichment phase within the Proactive Endpoint Threat Response application we automatically perform our enrichment utilizing OSINT, but in addition to this enrichment, this application automatically queries your SIEM. By automatically querying your SIEM, Swimlane can assist with finding additional historical context for this threat.
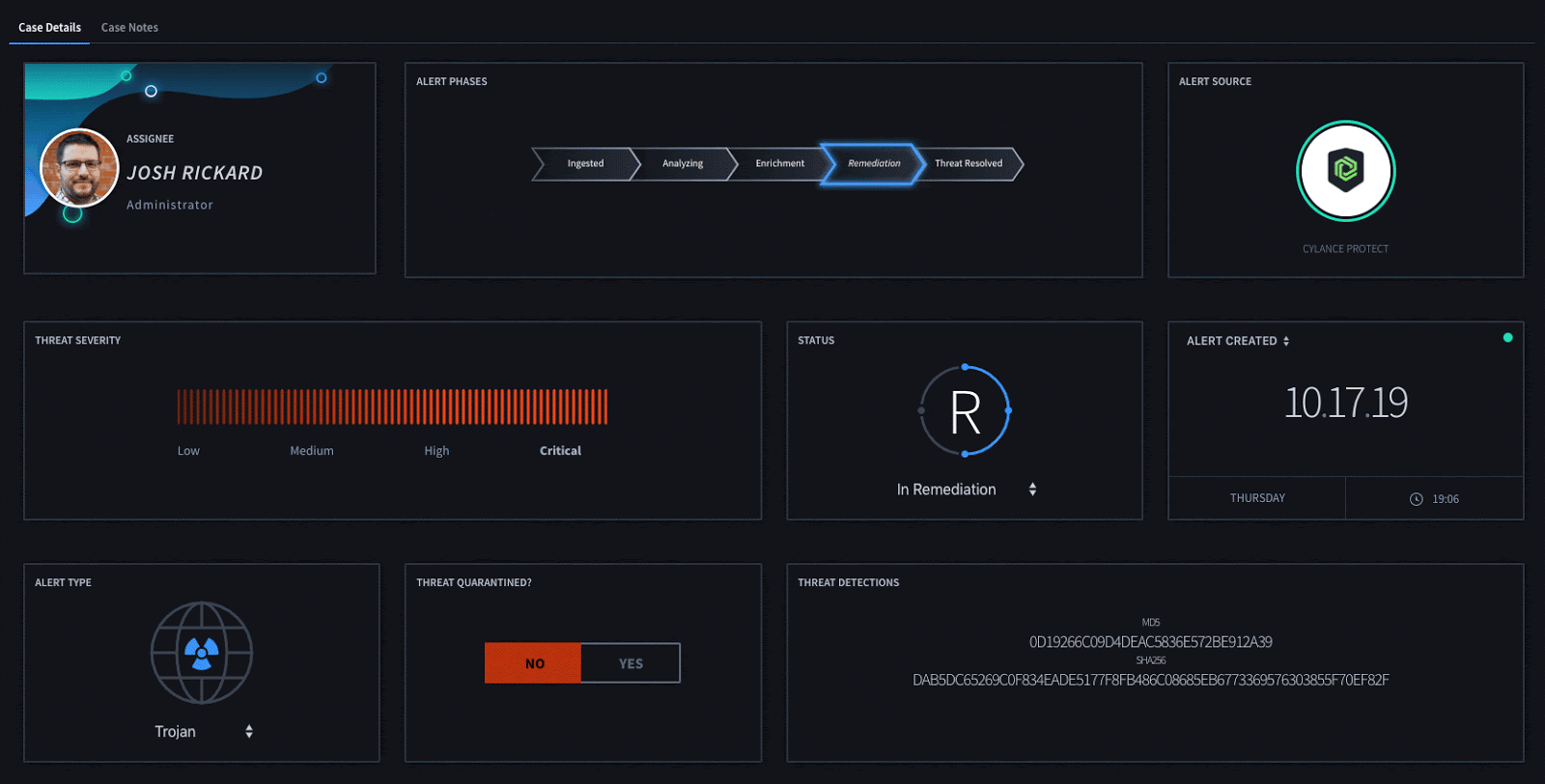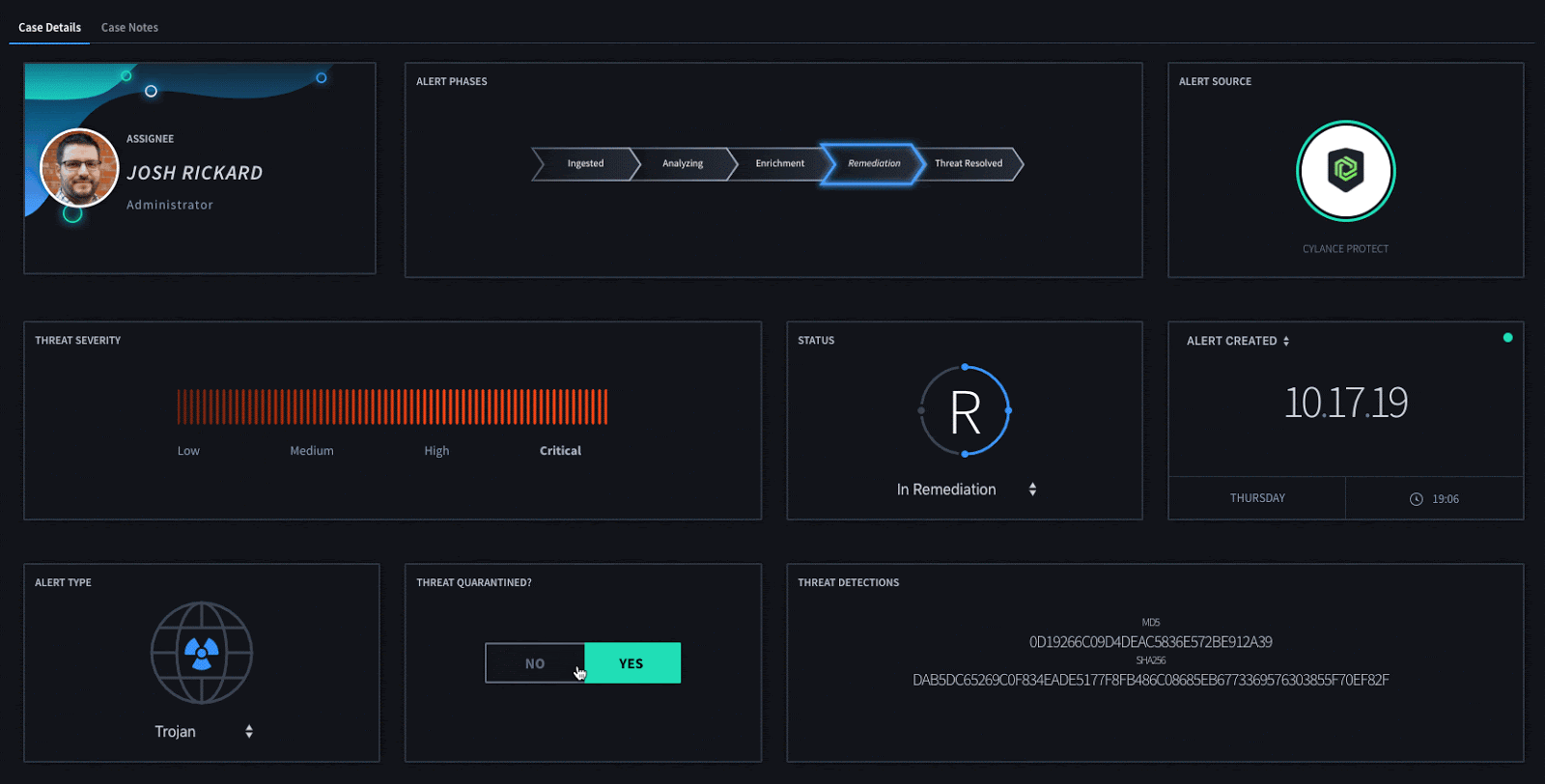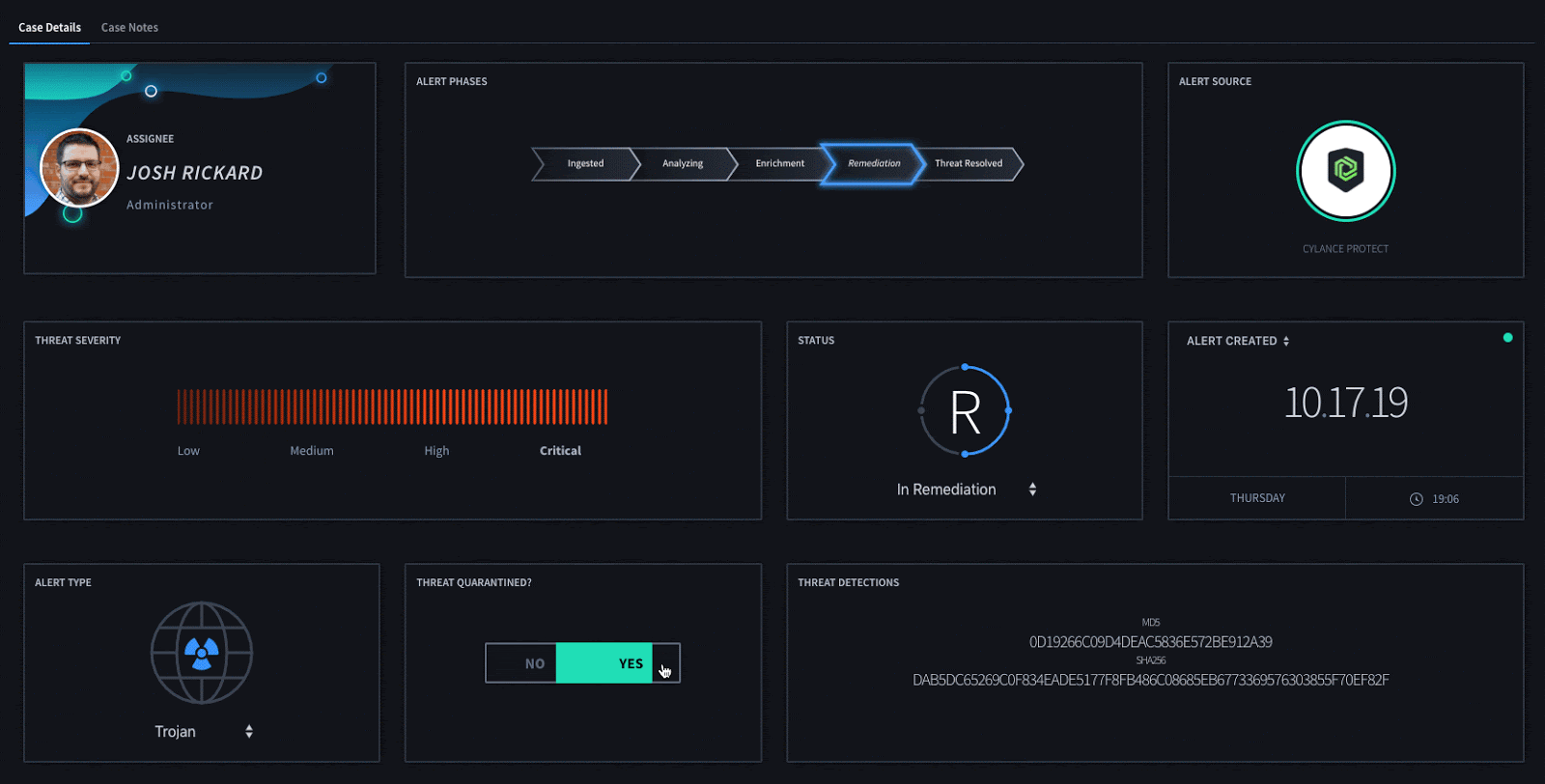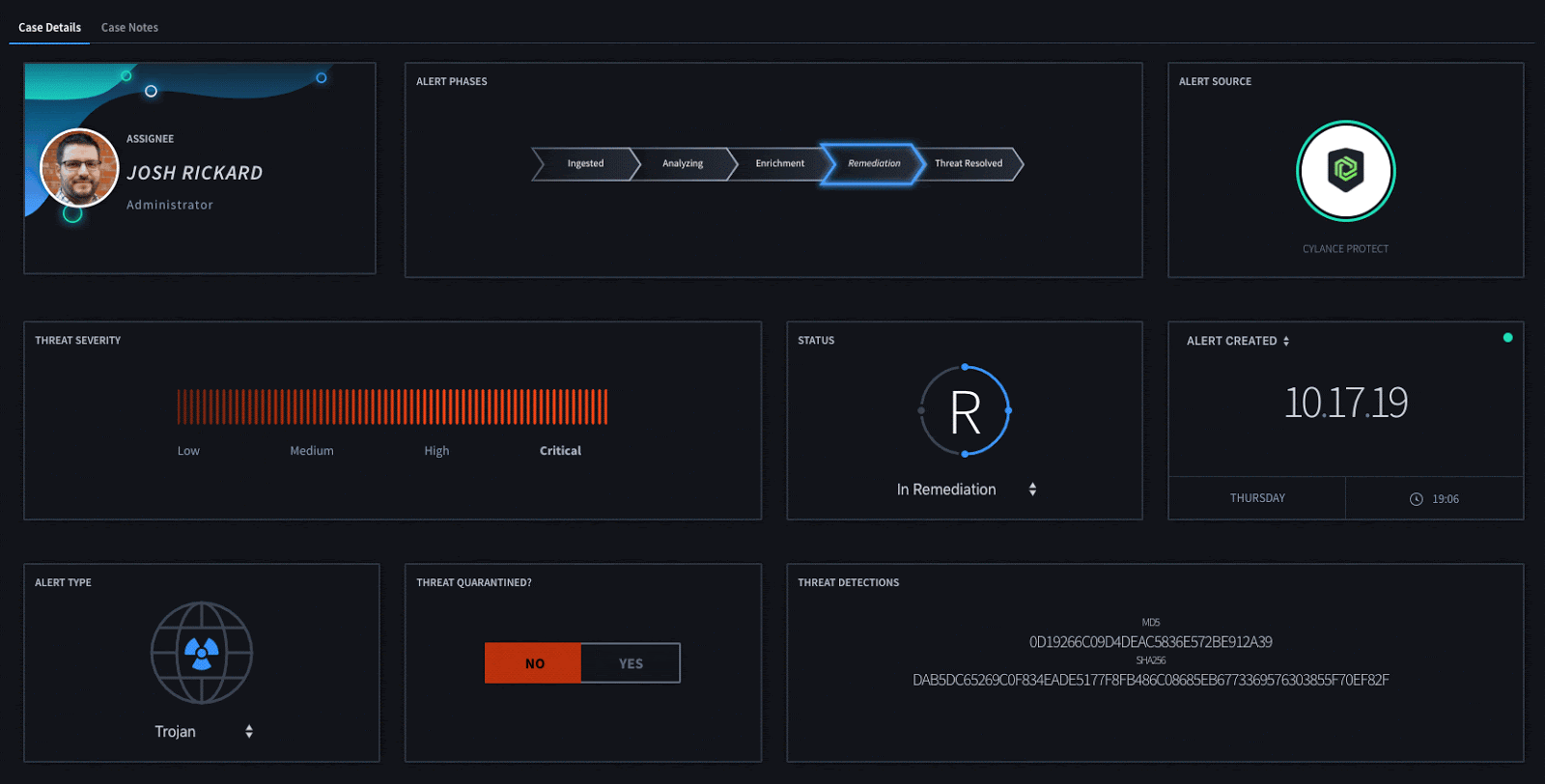
Once an overall determination has been made about this detection, Swimlane can automatically update a device threat which can either quarantine or safelist a specific threat detection. This can be done either automatically or by interacting with our Threat Quarantine widget.
Happy Hunting!
Winning Formula for Cyber Threats = SOAR + Endpoint Security
If you are interested in learning more about our Proactive Endpoint Threat Detection use case, watch the on-demand webinar with Cylance PROTECT where we will show it in action.

