Endpoint detection is an important part of a modern enterprise security posture. As encrypted traffic dominates the net and continues to gain in market share, network-based intrusion detection and binary identification become more and more difficult.
Manual EDR
An endpoint detection and response (EDR) platform—while it offers beneficial visibility into endpoint activity and binaries—introduces its own analysis process, workflow and reporting changes to a security operations center (SOC). Additionally, analysts trained on traditional network traffic analysis may be less familiar with the research and analysis techniques related to EDR.
A common manual analyst EDR workflow may resemble the following:
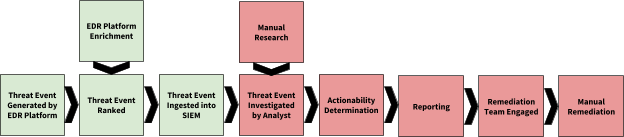
As the chart shows, the majority of the workflow requires direct manual intervention. Research, investigation, final determination, reporting and engagement of a remediation team fall to a SOC analyst in most cases, and then remediation (such as restoring a workstation or adding IPs to a firewall blacklist) falls to another team. This process leaves significant room for automation.
Automation-assisted EDR
With an automation platform, such as Swimlane, much more of the EDR workflow can be automated—including time-consuming steps, such as research and reporting.
An EDR workflow using Swimlane may resemble the following:
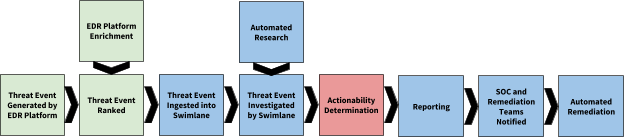
As the chart demonstrates, the only manual step remaining is determining whether or not and event is actionable enough to require remediation. The initial alerting and enrichment feeds into Swimlane—which performs additional research and investigations—then presents all of the relevant information (threat scores, VirusTotal rankings, WHOIS lookups, etc.) to the analyst on one screen, allowing for a rapid determination of whether remediation is required.
If remediation is required, the analyst can simply engage automated remediation (via the EDR platform’s system rollback ability, firewall/gateway blacklisting, etc.) from within Swimlane, as well as generate an automated report containing the alert details, research results, and final determination and remediation results.
EDR is—in this way—a well-suited candidate for automation via Swimlane, allowing the analyst to maximize their effectiveness, minimize arduous manual research, and avoid engaging busy networking or systems teams for low-level remediation actions. A multi-hour process involving multiple teams can be trimmed down to a few minutes. See below:
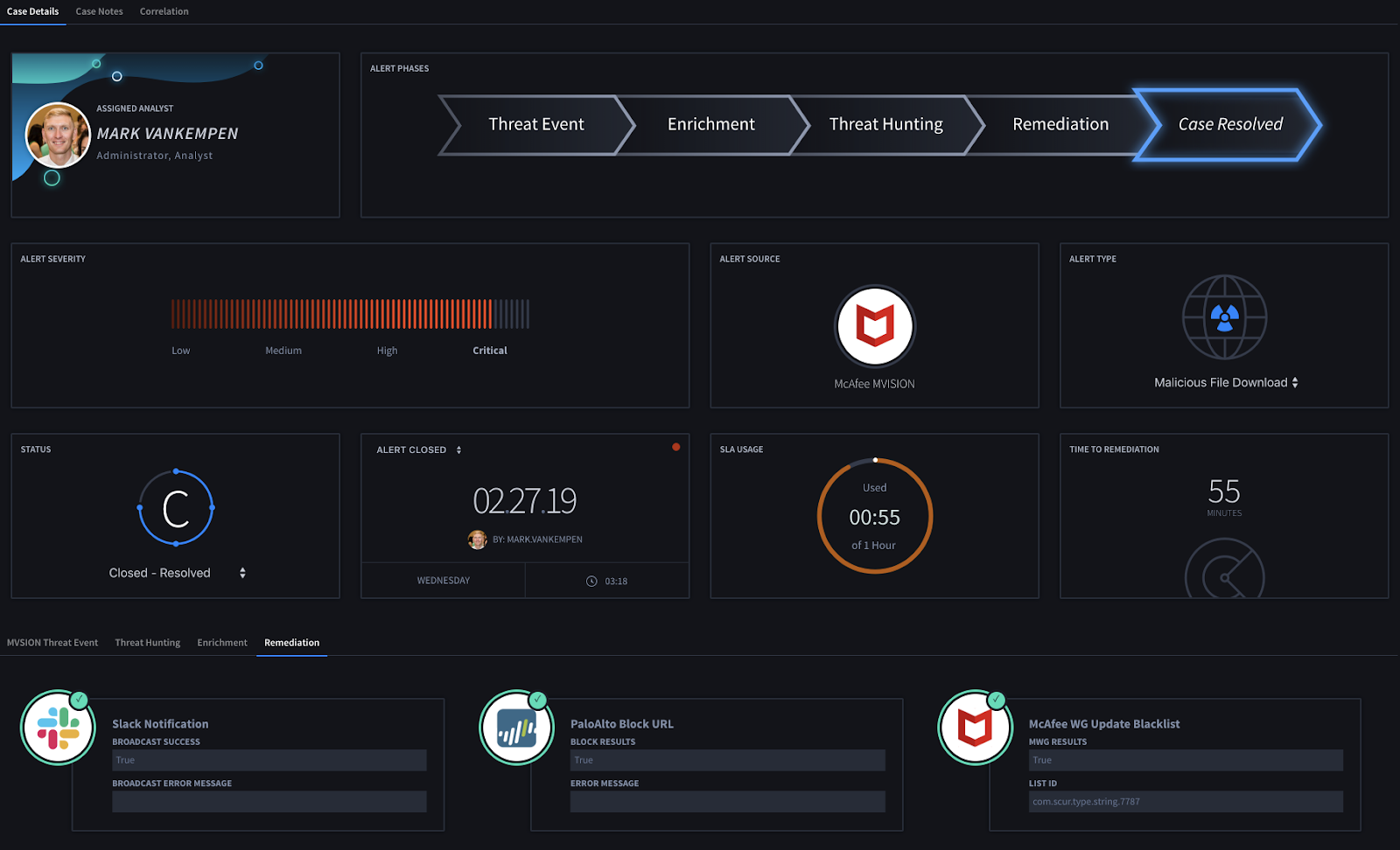
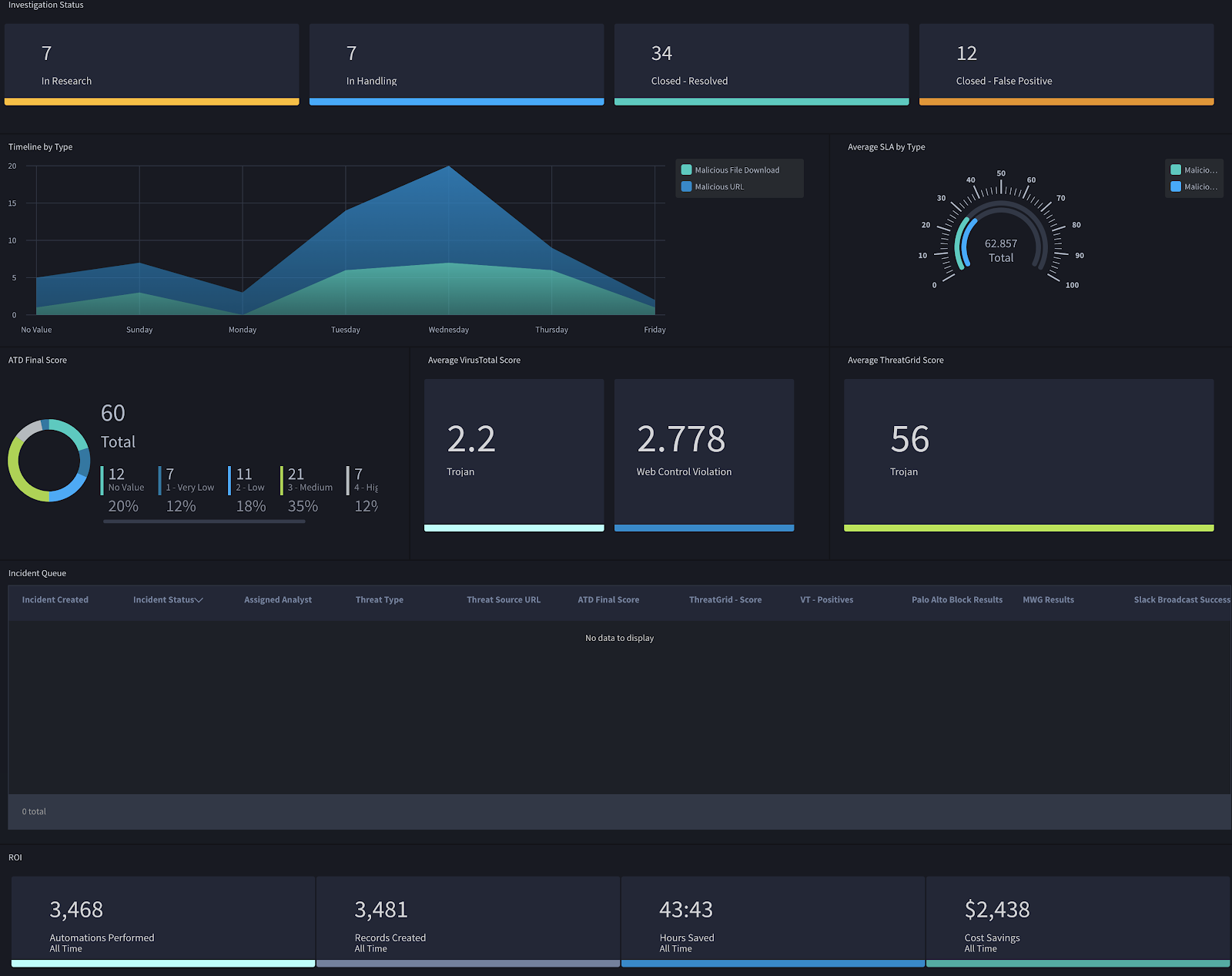
Watch our on-demand webinar on automated EDR.
EDR is often performed in an ad-hoc, manual and labor-intensive fashion as analysts are often required to toggle between tools to review binaries, sandbox them and perform open source intelligence research. Much of this process can be automated with SOAR. Watch this on-demand webinar for a detailed use case on automated EDR with SOAR.


