As the sophistication and frequency of security attacks continue to rise, security teams are feeling strained. Even as security budgets increase, most enterprises can’t find enough talent to manage it all.
Large organizations see as many as 10,000 security alerts per day.
Industry-wide staffing shortages, coupled with an explosion of new threats and vulnerable entry points, make it impossible for security teams to handle potential threats manually. With so many constant threats, security teams simply can’t investigate the vast majority of potential attacks.
Because of this, many teams are looking towards automation tools that promise to lessen the burden of threat investigation and increase efficiency. Integrating these automation tools with human analysts is where the potential of security operations management gets to shine. Plus, utilizing automation with advanced security orchestration leverages the strengths of both solutions to sharpen security oversight and reduce mean time to resolution (MTTR).
What should you be looking for in a security automation and orchestration solution?
Proactive threat hunting and assessment
In today’s threat environment, it’s no longer enough to be passively vigilant. Successful security strategies don’t wait for a problem to be reported before acting. Due to the sheer number of potential threats, less than 1 percent of critical security alarms are ever investigated manually. That’s why the best tools use automated workflows to continuously look for potential threats, investigate alerts, and relay findings to the security team in a single, centralized system. This approach leverages the best skills of your human teams and your technological tools with:
- Automated threat hunting, providing analysts with better, more comprehensive information about potential threats before they become a problem
- Smarter triage tools that review SIEM software alarms automatically, integrating event context to reduce time-consuming manual research
- Better threat intelligence to constantly update current processes with changing Indicators of Compromise (IOCs) so analysts can act faster
Comprehensive internal threat monitoring
While keeping a close watch on potential external attacks, enterprises must also prevent internal breaches, which pose their own unique sets of challenges. For instance, internal attacks are particularly difficult to catch because they tend to be spread over several systems and look much like normal user activity.
But manually checking user permissions to identify aberrant behavior is slow and time-consuming. Your team doesn’t have time to manually validate all user activity. Therefore, you need a way to shift some of this work to automated systems that can:
- Identify insider threats before they can cause major damage with rapid verification
- Disable user accounts and trigger immediate quarantine
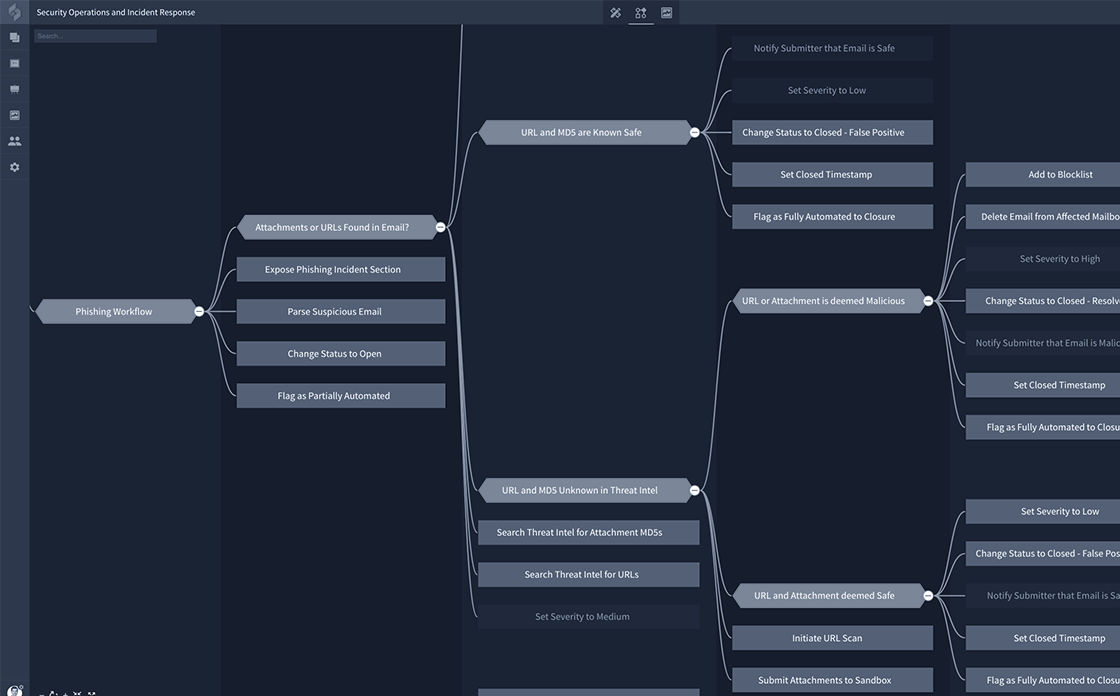
- Automate phishing analysis to combat the impossibly high volume of potential phishing emails received daily
Although external threats are the main focus of many security strategies, organizations must also be aware of suspicious internal activity.
Increased data gathering for immediate and long-term insight
Combining security automation and orchestration provides security operations management with more data and better management of automatically gathered research.
In the current landscape, data is both a vital tool and a huge liability, depending on how well your tools manage to find and store information. Investigators are typically required to gather evidence from multiple third-party systems during forensic investigations, requiring too much manual effort and taking a significant amount of time. Having access to long-term threat intelligence data helps SecOps teams come up with long-term security strategies. Security teams that can integrate automation into the investigation process are able to respond faster to real threats, drastically reducing MTTR and minimizing risk by:
- Automating forensic data collection from multiple tools and storing evidence in a centralized repository
- Integrating case management for immediate, intuitive access to all forensic detail necessary, significantly decreasing the time it takes to conduct an investigation
- Using metrics gathered over time to identify opportunities for more targeted uses of automation and orchestration
Swimlane security automation and orchestration
Security automation and orchestration is key to improving security operations management. Swimlane offers a comprehensive solution that is easy to setup and intuitive to use. The robust tools streamline incident response workflows, improving overall security operations by leveraging an organization’s existing security infrastructure and improving upon it.
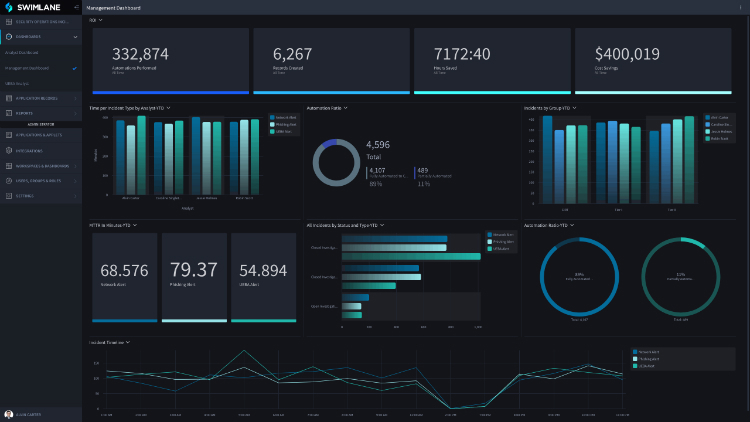
The solution can be used to:
- Identify and defend against phishing attacks
- Improve SIEM triage
- Support better threat hunting
- Assist with insider threat detection
- Compile better threat intelligence
- Enforce identity verification
- Complete comprehensive forensic investigations
- Increase endpoint protection
Analysts no longer have to waste time gathering information and sifting through alerts, freeing them up to spend less time performing administrative functions and more time actually investigating potential threats.
For more on improving security operations management through security automation and orchestration, contact us.