Operational Technology (OT) security has gained prominence across the majority of business verticals. Equipment initially designed solely for manufacturing a product is now required to be a connected device, forming part of the Internet of Things (IoT). This connectivity and the potential vulnerabilities it introduces pose a challenge for traditional OT. These critical infrastructure environments rely heavily on physical equipment, devices, and environments to maintain 100% uptime.
The European Union (EU) has introduced new legislation, NIS2, to underscore the importance of securing OT environments. NIS2 aims to enhance the cyber resilience and incident response capabilities of public and private entities, competent authorities, and the EU as a whole. The success of NIS2 will depend on vital collaboration across member states.
Keep reading to learn more about who is impacted by NIS2, the requirements necessary for the directive and how AI enabled low-code security automation is paramount in ensuring seamless compliance by October 2024.
Who Does NIS2 Apply To?
The NIS2 regulation in Europe applies to a wide array of sectors and industries. Primarily targeting operators of essential services (OES) and digital service providers (DSPs), NIS2 casts a broad net over critical sectors such as energy, transport, healthcare, finance, and digital infrastructures. OES and DSPs within these domains are mandated to implement robust cybersecurity measures to ensure the resilience and security of their network and information systems. See below:
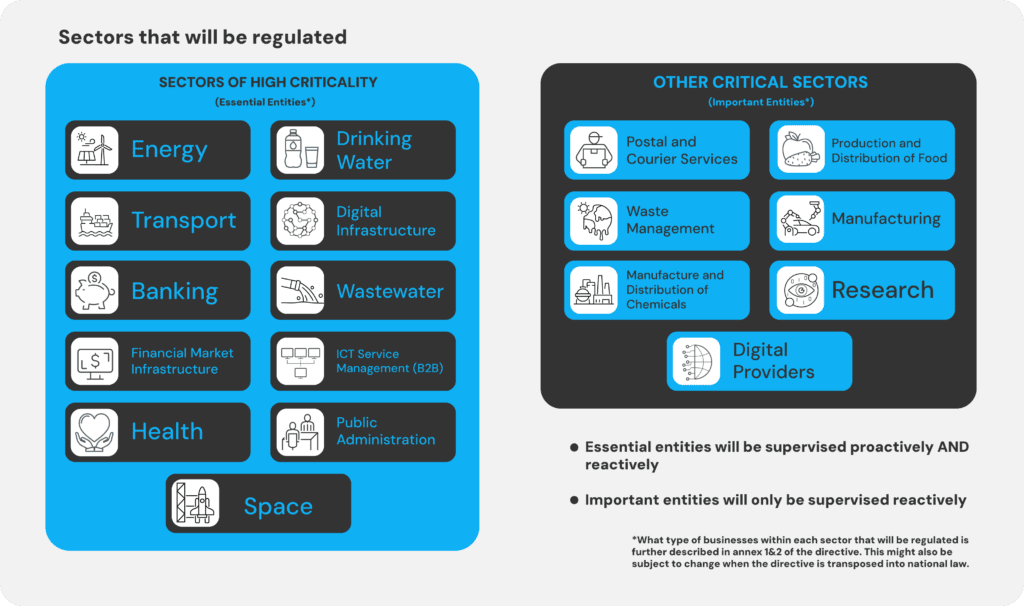
The Significance of Critical Infrastructure and Application Security
Amidst the current geopolitical landscape, this directive aims to counter the rising threat of cyber-attacks on businesses providing crucial services. This impacts various facets of security infrastructure, emphasizing network security, secure development practices, and identity management. The directive necessitates the adoption of policies related to cryptography and encryption, ensuring enhanced security for communications and critical information. NIS2 compels companies to fortify HR security, implementing measures for data storage, employee onboarding/offboarding, and emphasizing cybersecurity in HR operations and asset management. Multi-factor authentication (MFA) is also a key component of the directive.
Why NIS2 Compliance is Important
Failure to comply with the directive could result in:
- Fines of up to 10 million EUR or 2% of their global annual turnover.
- Management liability for any breaches of the directive.
- Senior management may be subject to temporary bans.
- Services could be temporarily suspended as a consequence of non-compliance.
Greater emphasis is placed on management’s insight into the prevention and handling of cyber alerts and incidents. According to a survey from BlueVoyant that interviewed 1,200 CIOs, CISOs, and Chief Procurement Officers on cybersecurity issues, 97% of companies have been “negatively impacted” by a cyber incident.
How to Embrace the NIST Framework for Robust Governance and Risk Management
NIS2 defines cybersecurity as a coherent strategy that will help provide objectives and priorities in cybersecurity and governance. This includes:
- Cybersecurity frameworks
- Awareness and training
- Cyber risk management and compliance
The National Institute of Standards and Technology (NIST) Framework is commonly known as one of the most commonly adopted cybersecurity frameworks by organizations, addressing both IT and OT security. NIST Framework is a structured approach to help organizations manage and improve their cybersecurity practices. The framework encompasses five key areas:
- Identify:
- Understand and prioritize assets, data, and systems.
- Assess and manage risks to the organization.
- Protect:
- Develop and implement safeguards to ensure the delivery of critical services.
- Manage access controls and secure data.
- Detect:
- Put measures in place to identify and detect cybersecurity events promptly.
- Establish continuous monitoring for potential security incidents.
- Respond:
- Develop and implement an effective response plan for dealing with a cybersecurity incident.
- Mitigate the impact of incidents and learn from them to improve future responses.
- Recover:
- Establish and implement plans to restore capabilities affected during a cybersecurity incident.
- Improve resilience and recover quickly from disruptions.
Organizations can use the NIST framework as a guide to assess and enhance their cybersecurity posture. It’s a flexible and adaptable tool designed to apply to a wide range of industries and business sizes.
Automate NIST Detection and Response
NIST Framework underscores detection and response, with key elements including people, process, and technology, incident reporting, and business continuity. Cyber resilience hinges on effectively combining these factors. To tackle the cybersecurity skills shortage, many outsource operations, sacrificing control. The winning strategy is simply defining your process and mapping it with security automation for a structured approach.
NIS2 emphasizes collaboration and incident reporting, with three stages: ‘early warning,’ ‘incident notification,’ and a ‘final report.’ Real-time visibility and reduced dwell time are vital, two areas where an automation platform excels. NIS2 also stresses the importance of a strategy for maintaining system availability during a major cyber incident, encouraging cloud backup solutions.
Security Mandates: Similar Urgencies in Europe and the United States
While NIS2 does not apply to the United States, similar security-centric mandates apply to the US Federal Government agencies and public sector. In early 2022, the Biden Administration issued M-22-09 and M-21-31 which required that all federal agencies in the United States comply with Zero Trust standards by the end of fiscal year 2024. This similar urgency is echoing throughout Europe with NIS2 regulations. What do both have in common? Both call for robust security measures. A security automation platform like Swimlane Turbine, an AI enabled low-code automation platform, serves as a vital facilitator, enhancing operational flexibility and breaking down the barriers between security teams enhancing transparency and visibility, and ultimately boosting efficiency and effectiveness.
Although cybersecurity awareness and training are imperative to protecting organizations, so is security automation. Co-Founder and Chief Strategy Officer of Swimlane said, “I have so much conviction in the fact that security automation is required for effective SecOps. Security automation capabilities are considered a “practical necessity” for enhancing overall cybersecurity effectiveness.”
SecOps First Ever Automation-Centric Framework
Although cybersecurity is rich with frameworks like NIST, there was a noticeable gap when it comesame to a universally adapted standard for automation. Enter Swimlane’s Automation Readiness & Maturity of Orchestrated Resources (ARMOR) Framework. This approach mirrors industry best practices observed in NIST, providing a robust framework for integrating automation seamlessly. The ARMOR framework features a maturity matrix that empowers security professionals to establish their organization’s maturity baseline, evaluate security operations (SecOps) capabilities on a five-level scale, and determine the next steps in the automation readiness process.

AI-Enabled Low-Code Automation for Continuous Compliance
Automation is an important contributor to how organizations can boost their compliance. By automating GRC, detection and response, infrastructure, and application security, teams will meet stringent compliance levels, become proactive, and free up time for analysts. To achieve effective protection and defense, an organization requires a thoughtful combination of human judgment and state-of-the-art automation strategies. Turbine Canvas, the industry’s inaugural ultra-simple low-code automation studio is designed to facilitate an uncomplicated creation of concise, logical playbooks. Learn more about Turbine Canvas today to help achieve compliance by October 2024.
Request a demo
If you haven’t had the chance to explore Swimlane Turbine yet, request a demo.


