We all know that security operations (SecOps) teams are overwhelmed by the extreme number of alerts they receive on a daily basis. Organizations are being attacked from all fronts, whether they know it or not. These attacks vary from social engineering, malicious emails, vulnerable services and applications, misconfiguration (job fatigue), etc.
Traditionally in a security operations center (SOC), malware analysis—more specifically reverse engineering—is conducted by a highly trained member of the security team. Depending on your team size, this may be multiple individuals. A SOC can receive hundreds – even thousands – of alerts about potentially malicious files from users reporting malicious messages to EDR, to workstations and server event logs.
With the overwhelming amount of incoming alerts, malware analysts (or reverse engineers) only receive a small percentage of an organization’s total potentially malicious binaries to review. As malware authors evolve and the use of more sophisticated techniques increases, security teams need to act upon every alert – not just the aforementioned small percentage – by automating their malware analysis.
What is Malware Analysis?
Malware analysis is the process of dissecting and understanding malicious software (malware) to identify its behavior, functionality and potential impact on a system or network. The objective of malware analysis is to develop an understanding of the malware’s inner workings, including its purpose, capabilities, and attack vectors.
Benefits of Automating Malware Analysis with Low-Code Security Automation
Automating malware analysis with the help of a low-code security automation platform can provide several benefits, including:
Increased speed and efficiency: Manual malware analysis can be time-consuming and requires significant human resources. By automating the process, security teams can analyze large volumes of malware samples quickly and efficiently, which allows them to identify and respond to threats faster.
Consistency and accuracy: Automating malware analysis can eliminate human error and provide consistent and accurate results. Automated tools can follow the same process for every sample, which reduces the risk of mistakes or oversights.
Better resource allocation: Automating malware analysis can free up security professionals to focus on higher-level tasks, such as developing new countermeasures and improving the organization’s overall security posture.
Cost savings: Manual malware analysis can be expensive and requires significant time and resources. Automating the process can help organizations reduce costs and improve the overall efficiency of their security operations.
Automating Malware Analysis of Malicious Files
By taking alerts you already receive, low-code security automation can automate the malware analysis process to determine if further action is required. See automated malware analysis in action, below.
Security automation platforms like Swimlane Turbine expand upon basic malware analysis workflows with composable UI for a more approachable automation experience. Once integrated into your current services, you can use both internal (e.g. Cuckoo Sandbox, etc.) or external (e.g. Hybrid-Analysis, SNDBOX, Joe Sandbox, McAfee Advanced Threat Defense, etc.) sandbox/analysis processes to automate the triaging of alerts related to potentially malicious files and URLs.
How it Works:
When you upload a malicious file, the security automation platform can return basic file information (hashes, name, type, etc.) but will also begin malware analysis in the background. You can automate the submission of potentially malicious files to both internal and external sandbox services (e.g. Cuckoo Sandbox, Hybrid-Analysis, etc.). Additionally, you can scan the file using our VirusTotal bundle.
Once the analysis is complete, both the sandbox and VirusTotal integrations will return their respective results. Based on the returned values we will calculate both individual integration scores, but also an overall total threat score based on the analysis done.
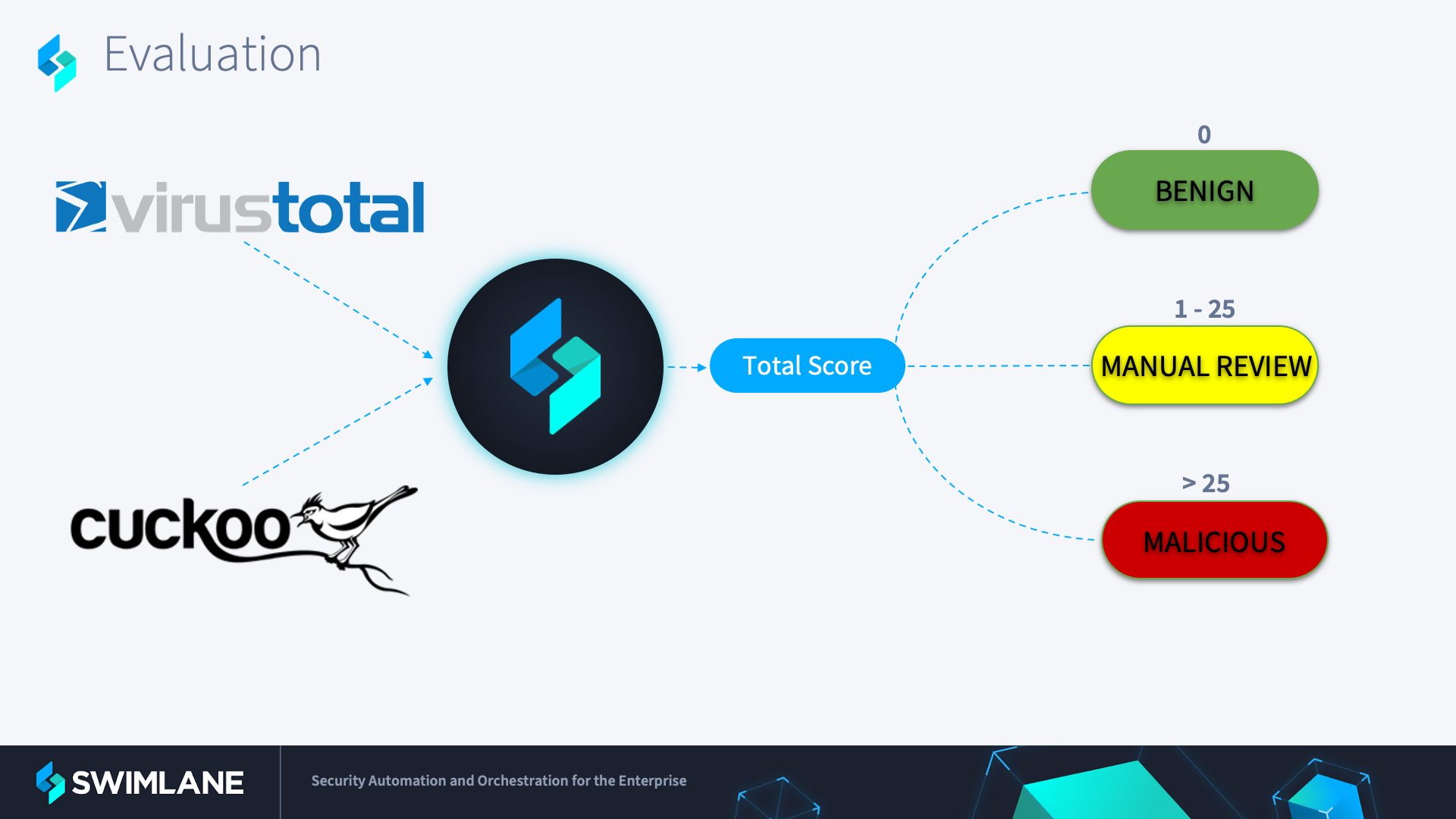
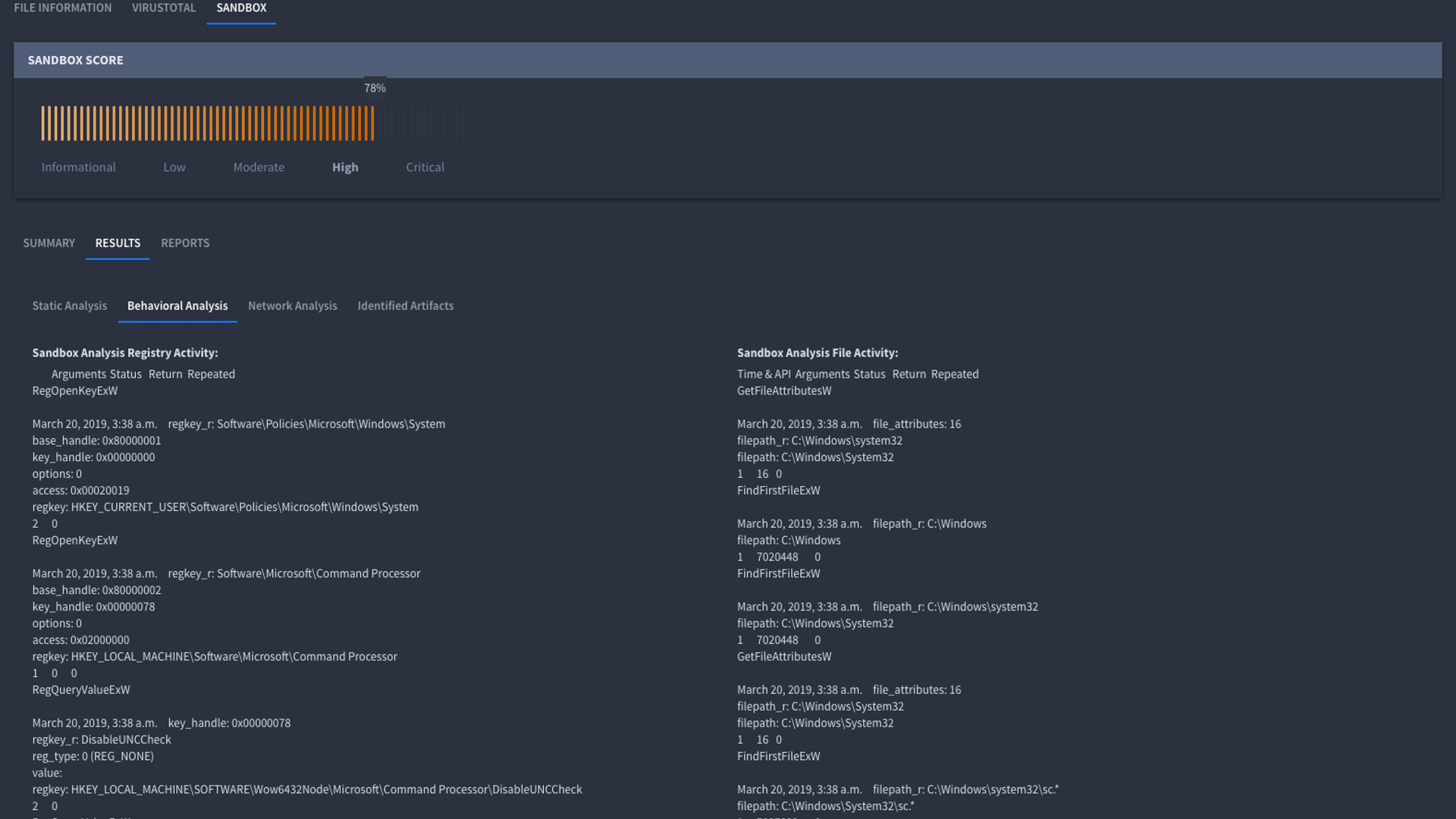
Automating the initial malware analysis of incoming alerts ensures that your SecOps team is not busy with VirusTotal lookups and manual analysis—they can focus on more proactive efforts instead of being reactive. And that’s only the beginning. Explore more use cases for low-code security automation.
SOAR Use Case Webinar: Automated Malware Analysis
Learn more on automated malware analysis. Watch the on-demand webinar where Rickard is joined by automation expert Jay Spann for a more in-depth discussion on automating the malware analysis process with low-code security automation.