Everything you need to know about SOC benefits, roles, responsibilities and more.
Security Operations Center (SOC) Overview:
What does SOC stand for? A security operations center (SOC) is a centralized security operations center that monitors and analyzes an organization’s network to detect and respond to threats and vulnerabilities. A SOC isn’t always a physical place — it’s a philosophy, approach and process that can be housed in a number of physical or virtual locations. A SOC typically includes analysts, managers, and tools to monitor security events and alerts in real-time across multiple systems and applications.
In a cyber security operations center, all security events are monitored by security teams, sometimes with the help of security automation tools. The goal of a SOC is to respond to alerts as quickly and thoroughly as possible before data is compromised.
A well-managed SOC can help improve cyber defenses by providing visibility into your network activity across all systems, applications and cloud environments. It should also be able to detect when systems or applications are compromised before they cause damage or allow attackers access to other parts of your environment.
Benefits of a SOC
The primary benefit of a SOC, security operations center, is that it keeps an organization’s data, employees and assets secure. To do so, the SOC detects and responds to security threats in real-time. The benefits of a SOC include:
Better visibility into your network:
Monitor alerts and identify anomalies in real-time to improve visibility into your network traffic patterns. This information enables you to detect threats and respond quickly when they arise.
Faster Incident Response:
The ability to analyze data in real-time provides faster response times when incidents occur, enabling you to quickly identify risks and take action before it’s too late.
Reduce Costs
Data breaches cost an average of $4.24 million in the United States alone. The SOC is key to preventing costly attacks. Clear SecOps processes and security automation solutions help drive efficiency, which results in reduced costs for enterprise teams.
Ensure Compliance
For organizations in sectors with strict compliance requirements, a SOC can help ensure security standards are upheld. With the proper security solution, compliance and reporting can even be automated.
Maintain Customer and Consumer Trust:
The SOC is central to fostering a culture of security and data protection. And with consumers growing more concerned about private data security, an established SOC is a signal of trustworthiness.
What Does a SOC do?
The SOC’s goal is to protect the organization by minimizing the damage caused by cby different types of cyber security attacks while also keeping security operations running smoothly.
The SOC’s job is to monitor all security systems and networks within an organization – whether they’re on-site or remote – 24/7 to ensure that they’re operating properly and aren’t compromised by hackers. They also watch for any suspicious activity that might indicate an incoming attack or intrusion attempt. These environments can be monitored at any scale, like remote and worldwide with a global security operations center (GSOC).
The security operations center (SOC) is the hub of your organization’s security infrastructure. The SOC is responsible for collecting, analyzing and responding to alerts. The SOC usually includes a wide array of tools, such as SIEM and SOAR solutions, firewalls, IDPs, backup tools and many others.
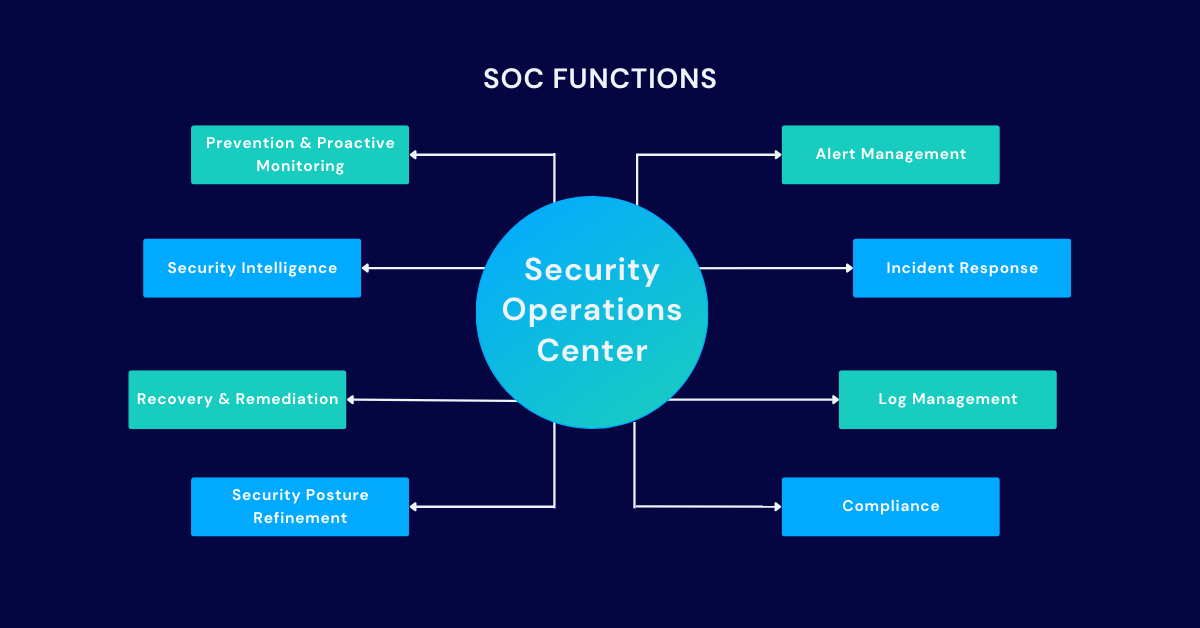
SOC Functions
Prevention and proactive monitoring:
Prevention is the best offense when it comes to cyber-attacks. The SOC team will stay up-to-date with the latest cybercrime trends, create incident response plans, patch vulnerabilities and other major preventative measures.
Alert management:
The primary function of a SOC is to collect and manage alerts generated by its monitoring tools. This includes technologies like firewalls, IDPSs and SIEMs.
Security intelligence:
The SOC provides real-time or near real-time information about threats that have been detected by its security tools.
Incident response:
A key role of the SOC is to respond to incidents as soon as they occur. This includes following IR processes and procedures, such as isolating endpoints, triaging threats, as well as properly documenting cases to refer to later.
Recovery and remediation:
The SOC is also responsible for post-incident recovery and remediation, like in the event of a data breach. This includes restoring systems and recovering lost data. In worst-case scenarios, like ransomware attacks, this could also mean deploying backups when necessary.
Log management:
It’s the job of the SOC to collect, maintain and review all activity and communications throughout the whole organization. Managing these logs helps SOC teams identify normal and abnormal behavior to find threats.
Security posture refinement:
Security posture is vital to the safety of business assets. It’s up to the SOC to identify and actively refine an organization’s overall security posture.
Compliance:
Many industries – especially public and government sectors – must comply with new regulatory requirements. It’s the responsibility of the SOC to ensure security regulations are followed.
Types of SOCs
Internal SOC: An internal SOC has a physical location and on-premises staff that monitor security operations.
Outsourced SOC: An outsourced SOC is almost entirely managed by an external vendor, such as a Managed Security Service Provider (MSSP). These vendors offer a variety of services to support different business needs.
Hybrid SOC: A hybrid SOC is a combination of an in-house security team and outsourced support, like with an MSSP. This type of SOC offers smaller SecOps teams the support they need, without expanding staff headcounts.
Virtual SOC: A virtual SOC is exactly as the name suggests – virtual. This type of SOC relies on support that’s not on-premises and instead focuses on process guidelines and security parameters to successfully triage alerts.
Staff Roles and Responsibilities in a SOC
The SOC team is responsible for ensuring the security of your organization’s network, data and users. To do this effectively, they must be able to detect threats and respond quickly. Security operations center jobs range in experience, skill set and responsibilities. Below are some of the common SOC team roles and responsibilities.
Security Operations Center Jobs:
- Security Analyst Tier 1: Tier 1 security analysts’ work centers around alert triage and reporting. They typically review and categorize security alerts and potential threats.
- Security Analyst Tier 2: Tier 2 analysts are the first line of incident response. They’ll review and respond to alerts that can’t be handled by Tier 1.
- Security Analyst Tier 3: The highest level of analysts are qualified threat hunters. These security operations center analysts are in charge of proactively hunting and uncovering complex threats within an organization’s systems.
- Security Engineer: Security engineers are responsible for designing, implementing, and maintaining the technical controls and defenses that are used to protect the organization’s assets and systems.
- Compliance Auditor: A compliance auditor ensures that an organization complies with industry and federal security regulations.
- SOC Manager: The SOC manager is directly responsible for the SOC team and operations. They will hire, train, and execute the overall security strategy.
- CISO: A Chief Information Security Officer (CISO) is a senior-level executive who is responsible for overseeing an organization’s cybersecurity strategy and operations. The CISO is typically part of the organization’s leadership team and reports directly to the CEO or other executive-level manager.
Top SOC Challenges
Challenges arise across every organization, and the SOC is no different. SecOps teams face a range of SOC challenges in the SOC, including:
- Too many alerts: 56% of enterprise security teams deal with 1,000+ alerts a day. The rise of threats means more alerts created by Security Information and Event Management (SIEM) tools.
- Security skills shortage: Security teams will likely face 3.5 million unfilled cybersecurity positions globally by 2025. There simply aren’t enough security professionals – especially not ones with extensive experience.
- Lack of clear incident response procedures and policies: The security industry evolves rapidly to keep up with expanding threats. SOC teams struggle to create documented processes and procedures, which leads to inconsistent alert triage and incident response.
- Limited security budgets: Despite the explosion of high-profile cyberattacks, SOC teams survive off of limited security budgets. It’s difficult to keep pace without a budget for more staff or updated solutions.
- Compliance and regulatory requirements: SOC teams in certain industries, like Critical Infrastructure sectors, must follow strict regulatory requirements. In fact, 69% of security teams admit that regulatory compliance is a big part of their security spending. Unless SOC teams have adequate staffing or security automation solutions, it’s difficult to keep up with rigid regulations and compliance standards.
Building a Winning Security Operations Center (SOC)
Identify Your SOCs Needs
To build a SOC, the first step is to identify the specific security needs of the organization. Know what you’re protecting and your strategy to do it. Then, determine the resources that will be required to meet those needs. This may include hiring additional staff, purchasing security software and hardware and establishing protocols for monitoring and responding to security incidents.
Create a Security Operations Center Framework
Once the necessary resources have been identified, the next step is to establish the infrastructure for the SOC. This may involve setting up a dedicated space for the team, as well as installing and configuring the necessary security software and hardware. The team should also establish processes and protocols for monitoring the organization’s security posture, as well as for responding to and investigating security incidents. Identify any security operation center frameworks to follow, such as the NIST Cybersecurity Framework or MITRE ATT@CK Framework.
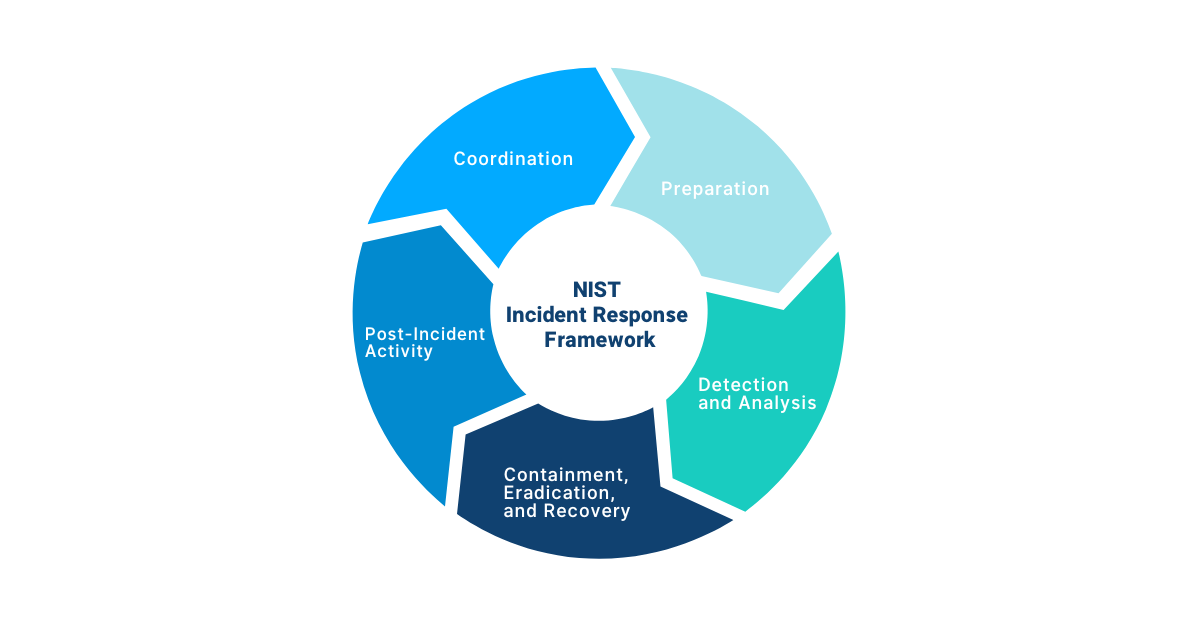
Establish Strong SOC Communication and Coordination
In addition to the technical aspects of building a SOC, it is important to establish clear lines of communication and coordination within the team, as well as with other departments within the organization. This may involve regular meetings and briefings, as well as the development of incident response plans to ensure that the team is prepared to handle a wide range of security incidents.
Building a security operations center requires a combination of technical expertise, strong organizational skills, and clear communication and coordination within the team. By taking the time to carefully plan and establish the necessary infrastructure and processes, a security team can build a SOC that is effective at protecting the organization from a wide range of security threats.
Take Advantage of SOC Security Tools
Security teams turn to a variety of tools to streamline security operations and improve efficiencies across people, processes and other technologies. The specific tools that are used in a SOC can vary depending on the organization and its specific security needs. Some common tools that are used in a SOC include:
- Security information and event management (SIEM) systems: These are specialized software systems that collect and analyze log data from various sources across an organization’s network. SIEM systems can help security analysts identify potential security threats and incidents. Learn more about the differences between SIEM vs SOAR.
- Security Orchestration, Automation and Response (SOAR): These solutions help SecOps teams automatically executive repetitive tasks in the SOC, like responding to phishing alerts, SIEM and EDR alert triage. SOAR platforms help improve SecOps performance metrics including MTTD, MTTR and dwell times. Certain security automation solutions help teams maintain security operations center best practices as well.
- Vulnerability assessment and management tools: These tools are used to scan an organization’s network and systems for vulnerabilities, such as unpatched software or weak passwords. Vulnerability assessment tools can help organizations prioritize their patching and remediation efforts.
- Network monitoring and analysis tools: These tools are used to monitor network traffic and behavior, and can help security analysts identify potential security threats and anomalies.
- Threat intelligence platforms: These are specialized systems that collect, analyze, and disseminate information about known and emerging cyber threats. Threat intelligence platforms can provide security analysts with valuable insights and context for investigating and responding to security incidents.
Find the Best SOC Solution at Swimlane
The tools used in a SOC are designed to help security analysts monitor and protect an organization’s network and systems, identify potential security threats and incidents and respond quickly and effectively to any security issues that arise. With so many security solutions on the market, it’s important to choose ones that protect your organization, support your analyst and provide valuable returns to your organization. With so many security solutions on the market, it’s important to choose ones that protect your organization, support your analyst and provide valuable returns to your organization
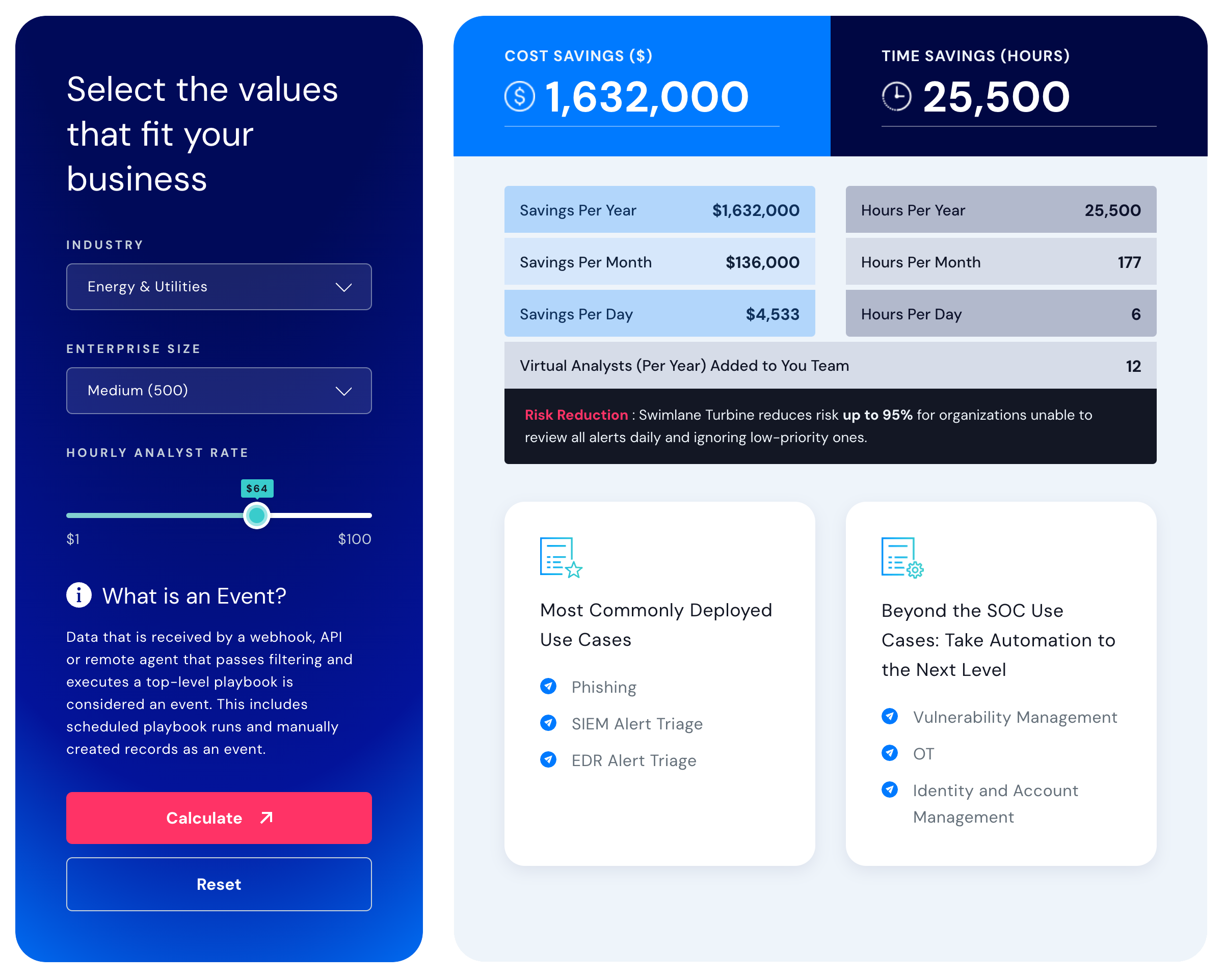
Swimlane ROI calculator
Estimate the savings you can achieve with Swimlane Turbine.


