How to Build an Incident Response Playbook in 9 Steps
To build an incident response playbook, systematically outline the steps your organization will take from detecting an incident to its full recovery, ensuring clear roles, communication protocols, and escalation paths. It serves as a critical resource for maintaining business continuity and minimizing the impact of security incidents.
Having an incident response playbook is essential to helping your enterprise investigate and respond to data breaches. But what is it exactly, how do you build one and why do you need one?
What is an Incident Response Playbook?
An incident response playbook is a set of rules that describes at least one action to be executed with input data and triggered by one or more events. It is a critical component of cybersecurity, especially in relation to security automation platforms and security orchestration, automation and response (SOAR) solutions. It’s meant to represent a basic security process in a generalized way that can be used across a variety of enterprises.
At its core, an incident response playbook outlines not just one, but a series of actions to be executed in response to specific input data or triggered by various events. This playbook acts as a critical cornerstone in the realm of cybersecurity, particularly in the context of security automation platforms and the broader domain of SOAR solutions. Understanding the different types of cyber attacks is crucial for developing effective playbooks that can distill complex incident response processes into a generalized, yet highly adaptable framework. This framework is intentionally designed to be flexible and applicable across diverse enterprises, irrespective of their size or industry.
Key Components of an Incident Response Playbook
According to IACD, Incident response playbooks “bridge the gap between an organization’s policies and procedures and a security automation [solution].”
While an incident response plan highlights overall roles and communication requirements, a playbook tells you what actions to take for threats. Time is of the essence when a threat occurs. It’s critical to eliminate unnecessary steps and information from the incident response process.
Incident response playbooks (IR playbooks) can be shared across organizations and include common components, such as:
- Initiating condition: The first event of the playbook triggers the rest of the steps. It’s often the security issue addressed by the entire playbook.
- Process steps: This includes all major activations organizations should conduct to satisfy the policies and procedures triggered by the initiating condition. This is the core component of an IR playbook and includes key steps like generating response actions, authorizing responses, quarantining, etc. These steps typically encourage future automation (with human oversight), even if the organization does not currently have those capabilities.
- Best practices and local policies: These are dependent on your specific industry. It includes activities that may be conducted in addition to the core process steps.
- End state: This is the end goal of the incident response playbook. It is the desired outcome based on the initiating condition that represents the playbook’s completion.
- Relation to governance and regulatory requirements: This component relates key process steps to those required for various compliance and regulatory laws.
How to Build an Incident Response Playbook in 9 Steps
Here are the steps the IACD recommends following to construct an incident response playbook:
1. Define the Initiating Condition and Incident Types
Clearly identify the specific triggers or events that initiate the playbook, such as a security alert, user report, or system anomaly. Categorize these by incident type (e.g., malware infection, data breach, mobile phishing attempt, DDoS attack) to create targeted playbooks.
2. Outline All Potential Actions and Dependencies
List every conceivable action that might be taken in response to the initiating condition, considering both technical and non-technical aspects. Map out the dependencies between these actions to understand the logical flow.
3. Prioritize Actions (Required vs. Optional)
Categorize each action as “required” (must occur to mitigate the threat and achieve a defined outcome) or “optional” (best practices, enhancements, or additional steps that improve the response but aren’t strictly necessary for initial mitigation).
4. Construct the Core Process Workflow
Design the primary process flow using only the “required” elements identified in step 3. This forms the backbone of your playbook, ensuring critical steps are always followed. Visualize this flow using flowcharts or swimlane diagrams for clarity.
5. Integrate Optional Activities by Function
Review the “optional” actions and group them by activity or function (e.g., monitoring, enriching data, automated response, verifying, mitigating, communicating). This helps organize supplementary steps effectively.
6. Embed Optional Processes within the Workflow
Modify the core process created in step 4 to indicate logical points where any optional processes or activities could be initiated or integrated. This ensures flexibility while maintaining the core response.
7. Document Optional Actions with Clear Guidance
Detail the categorized optional actions, providing clear instructions and criteria for their execution. Include these in an “options box” or appendix, referencing them from the main workflow.
8. Define End States, Escalation, and Handoffs
Clearly identify the possible end states of the playbook (e.g., incident resolved, mitigated, escalated to another team or playbook). Define escalation paths and criteria, as well as clear handoff points to other teams or processes.
9. Identify Regulatory Compliance and Reporting
List all relevant regulatory laws and industry requirements that the playbook helps satisfy (e.g., GDPR). Include specific reporting requirements and timelines that must be met during and after an incident.
When to Use an Incident Response Playbook
An incident response playbook is a valuable resource that should be utilized strategically in response to a spectrum of cybersecurity incidents. Its role extends beyond just major breaches to encompass a wide range of scenarios where a structured and efficient response is essential. Here are some key instances when deploying a security incident response playbook is highly advantageous:
- Ransomware Attacks: Incident response playbooks are indispensable when dealing with ransomware attacks, where immediate and coordinated actions are crucial to prevent data loss and mitigate financial and operational risks. Playbooks guide the organization on ransomware containment, communication protocols, and potential decryption procedures.
- Phishing Attacks: In the event of phishing attacks, where deceptive emails or communication attempts can compromise sensitive information, an IR playbook provides clear steps for incident handlers. These steps may include identifying compromised accounts, quarantining malicious emails, and informing affected users.
- Malware Infections: Incident response playbooks are vital when malware infiltrates an organization’s systems. They outline procedures for isolating infected devices, conducting malware analysis, and implementing remediation steps, which are essential for preventing further spread and damage.
- Compromised Applications: When an organization’s applications are compromised or vulnerabilities are exploited, IR playbooks come into play to swiftly address the issue. They may guide the process of isolating affected applications, patching vulnerabilities, and conducting security assessments.
- Distributed Denial of Service (DDoS) Attacks: DDoS attacks can disrupt online services and impact customer experience. Playbooks provide a structured approach for handling DDoS incidents, including traffic analysis, traffic diversion, and communication strategies to maintain service availability.
- Insider Threats: IR Playbooks are also useful in scenarios involving insider threats, where employees or insiders intentionally or unintentionally compromise security. They help organizations investigate the incident, mitigate risks, and implement measures to prevent future insider threats.
- Incident Triage: Beyond specific attack types, security incident response playbooks can be used for general incident triage. They assist in determining the severity of an incident, activating appropriate response teams, and initiating containment measures.
- Continuous Improvement: Additionally, IR playbooks can be employed for continuous improvement efforts in cybersecurity. Regularly reviewing and refining playbooks ensures that they stay up-to-date with evolving threats and technologies.
Incident Response Playbook Template: Phishing
Just as a conductor guides an orchestra through a symphony, an incident response playbook template orchestrates your security team’s actions when a cyberattack strikes. Imagine a clear, visual roadmap, like the diagram below, that lays out every step, from the moment an alert sounds to the full restoration of your systems. This template isn’t just a static document; it’s a dynamic blueprint that assigns roles, defines communication channels, and even integrates automated responses, ensuring that every team member knows their part and that critical actions are taken swiftly and efficiently. It’s designed to be the single source of truth, minimizing chaos and maximizing your ability to mitigate threats, no matter how complex.
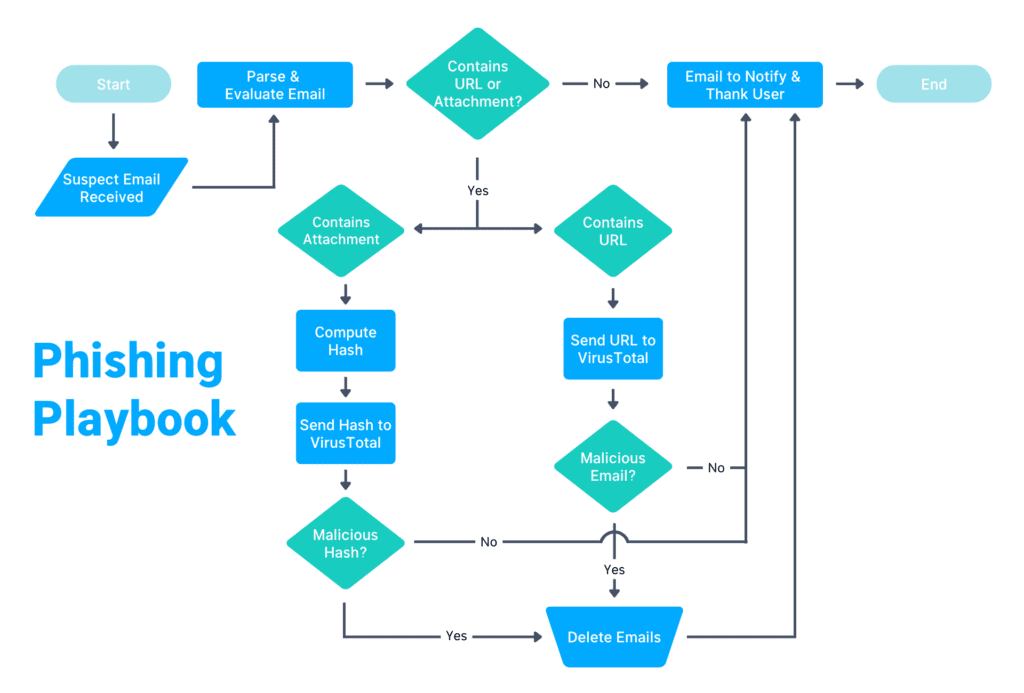
Incident Response Automation
An automated incident response solution provides your organization with the tools to model and automate manual and time-consuming response processes.
Tasks that can be automated with security automation, orchestration and response (SOAR) include:
- Reviewing and analyzing threat intelligence sources
- Investigating incidents involving log gathering and analysis
- Updating tickets
- Gathering metrics and creating reports
- Sending email alerts
- Resolving alerts
Every automated step can save minutes for each alert, saving time and improving your organization’s incident response.
Incident response automation and SOAR playbooks allow your organization to handle more threats in the same amount of time. Plus, by automating responses, your cybersecurity team can focus their training and skills on serious threats instead of mundane tasks. This force multiplier has the additional positive effect of increasing morale and reducing analyst burnout.
TL;DR How to Build an Incident Response Playbook
A well-structured incident response playbook is crucial for minimizing damage and ensuring business continuity during cyberattacks. It outlines clear, step-by-step actions for your security team, from initial detection to full recovery, and is enhanced by automation, particularly with SOAR solutions. Effective playbooks define roles, standardize communication, and incorporate continuous improvement based on past incidents and evolving threats.
Automated Response Playbook FAQs
What is an example of incident response playbooks in action?
An example is a phishing playbook automatically blocking malicious IPs, isolating affected endpoints, and notifying security teams upon a user reporting a suspicious email.
What are the steps for a ransomware incident response playbook?
Key steps include: detection and containment (isolate affected systems), eradication (remove ransomware), recovery (restore from backups), post-incident analysis, and communication with stakeholders.
How does the NIST incident response playbook guide organizations in their response efforts?
The NIST incident response playbook provides a standardized framework encompassing four phases: Preparation, Detection & Analysis, Containment/Eradication/Recovery, and Post-Incident Activity, offering a structured approach for all incident types.
What should be included in a malware incident response playbook to effectively handle infections?
It should include steps for identifying the malware type, containing spread, eradicating the infection from all systems, restoring affected data, and implementing preventative measures.
What are the unique considerations for a cloud incident response playbook?
Unique considerations include shared responsibility models, ephemeral cloud resources, API-driven environments, rapid scalability, and integration with cloud-native security tools for visibility and control.

SANS Product Review: Swimlane for Incident Response and Visibility
Deep dive into how Swimlane Turbine, the agentic AI automation platform, delivers unprecedented efficiency and effectiveness in incident response and visibility.



