What low-code security automation is, why we need it and how it helps security operations teams.
Automation is meant to make our lives easier. Self-driving cars help us drive safer. Automated checkout at the store makes grocery trips faster. But what about security automation?
It seems counterintuitive to make security automation simpler – shouldn’t cybersecurity be sophisticated and complex?
Just as automation doesn’t remove the need for people, automation doesn’t remove sophistication from your security operations center (SOC). The goal of security automation is to take a powerful, complex security ecosystem and make it simple to use by whole teams.
What is Low-Code Security Automation?
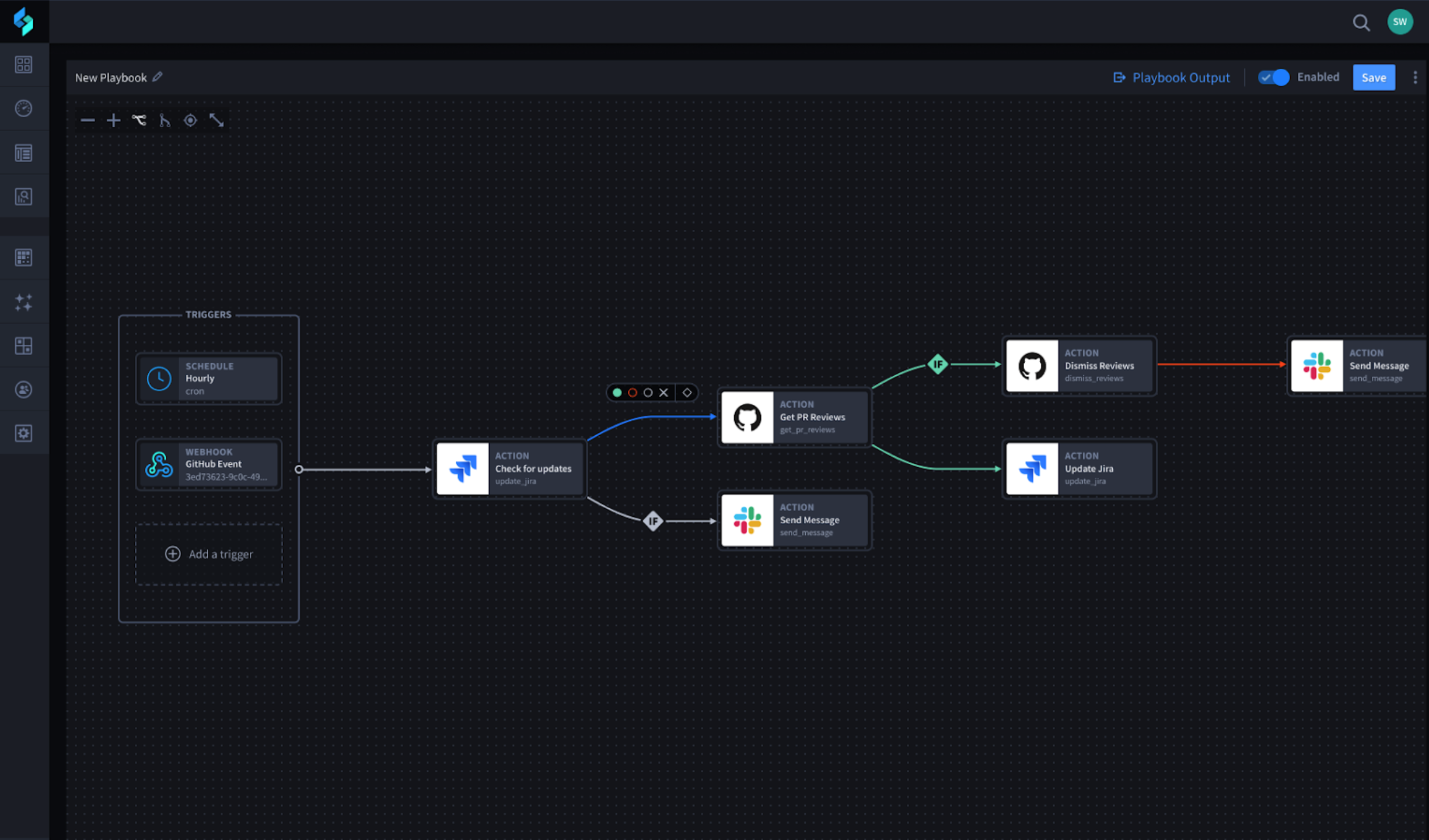
Low-code security automation automatically executes SOC best practices, defined by your SecOps team, at machine speeds. This allows you to standardize your processes to mitigate risk, speed resolution, and streamline communications.
Low-code security automation platforms adapt to your organization’s unique security requirements and operational processes to automate tasks that are typically time-consuming and require constant monitoring of third-party systems. This significantly speeds up the incident response process, improving your organization’s ability to respond to more incidents in less time without adding unnecessary overhead.
Why Do We Need Security Automation?
One of the biggest challenges security teams face is disparate technologies. When thousands of alerts fire from multiple tools with little cross-communication, it quickly overwhelms analysts with too much data.
Security automation gathers these disjointed tools into a single place. It creates connections and automates workflows to help build out business processes quickly. When you introduce automation into your security operations center (SOC), you reduce the number of steps your team has to take to accomplish tasks.
Building Robust Automation Isn’t Always Easy at First
In reality, most automation isn’t ‘set it and forget it’. Legacy security automation platforms come with their own limitations and problems like a high barrier to entry, complex workflows, overwhelming processes, and too many steps.
It’s common for CISOs to want automation for its list of perks, but then quickly realize they don’t have the staff to get started. Building use cases takes expertise and time with complex automation platforms, which also need to be regularly maintained to function properly. Countless steps and moving pieces lead to decision fatigue when creating workflows.
Security teams deserve a simple way to start small with automation and then grow at a pace that supports their process. At Swimlane, we like to say that our AI-enhanced low-code security automation platform is the sweet spot. It’s important to find an automation platform that is simple enough for your entire security organization to use yet scalable as your SecOps team grows. Most teams can’t dive into the deep end with security automation – you need to take baby steps.
No-Code vs Low-Code vs Full-Code Security Automation?
Security automation can be broken down into three main categories: no-code, low-code, and full-code (think traditional SOAR platforms). Each comes with its own degree of flexibility and requirements.
What is Full-Code Automation?
Full-code automation requires dedicated coding experts to create workflows and processes, but you have more full customization options. The barrier to entry is high, though, and requires significantly more time to fully operate.
What is the Difference Between Low Code and No Code Automation?
No-code automation offers codeless access to the basics of security automation. However, it limits you to pre-made use cases and workflows, which leaves minimal customization in the future.Low-code automation is the sweet spot between no-code and full-code. You can still expect robust application development capabilities for various customizable use cases but with more user-friendly features like drag-and-drop data entry and built-in business logic. With low-code automation, you can operate at any level of coding you prefer – do you want no-code, some-code or more-code? The choice is yours.
Learn more about low-code vs. no-code security automation.
What are the Four Main Benefits of Low-Code Automation?
Low-code is the future of security automation. SecOps teams need more visibility, more power, and more data ingestion to succeed. At the same time, automation platforms need to be simple and flexible enough for small security teams to benefit from. There are four main areas that SecOps teams need help in, where low-code automation can help.
Gain True Visibility
Low-code security automation enables visibility and actionability at scale without making things complicated. Visibility across all tools, both inside and outside the SOC, is possible.
Streamline Data Ingestion
Bring in larger and broader data sets at machine speeds. The closer detection can get to the source of alerts, the faster threats can be stopped.
Cost Savings
Low-code automation reduces development costs as it requires fewer resources and less time compared to traditional development methods. Completing an ROI calculator will help you determine.
Simplify Playbook Building
Robust case management capabilities allow you to build playbooks that respond in real-time quickly. Best practices and business logic are built in to avoid errors and save SOC analysts time.
As platforms continue to evolve, low-code security automation stands out for its simplicity and sophistication. With low-code security automation, teams can customize automation workflows that adapt to their unique needs – not the other way around.
When to Use a Low-Code Platform
An organization should consider using a low code automation platform to:
- Increase efficiency and streamline SOC processes, as this helps standardize procedures to mitigate risks, speed up resolution times, and facilitate smoother communication within teams.
- Handle a high volume of alerts when your security team is overwhelmed by various tools. A low-code platform can consolidate these alerts and automate responses, reducing the burden on SOC analysts.
- Create a customized approach to security as low-code security automation can adapt to specific operational processes without extensive coding.
- Improve incident response by allowing for quicker reactions to security incidents, potentially reducing the impact of breaches.
- Reduce complexity and costs as low-code platforms can simplify operations without sacrificing effectiveness.
- Scale security operations as your organization grows by easily handling increased workloads without needing proportional increases in staff or resources.
- Bridge the skill gaps when your team lacks in-depth coding skills, low-code platforms provide a user-friendly interface for creating and managing workflows.
- Rapidly deploy solutions to enable faster roll-out of security automation processes compared to traditional coding methods.
- Ensure compliance with industry regulations and facilitate transparent reporting by help by automating these processes and maintaining accurate records.
- Integrate disparate security tools and systems to create seamless workflows, enhancing overall security posture.
What is the Best Low Code Platform?
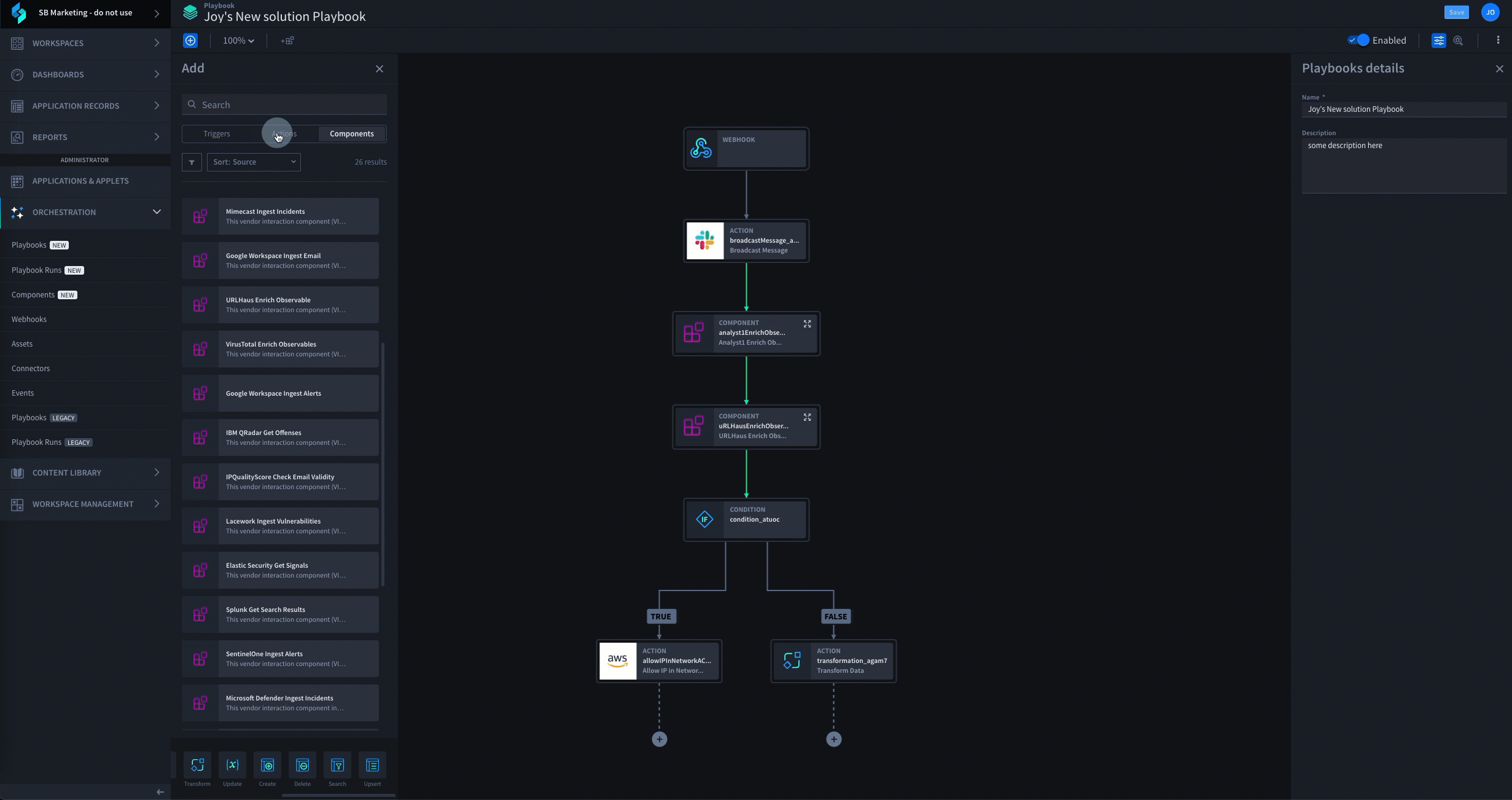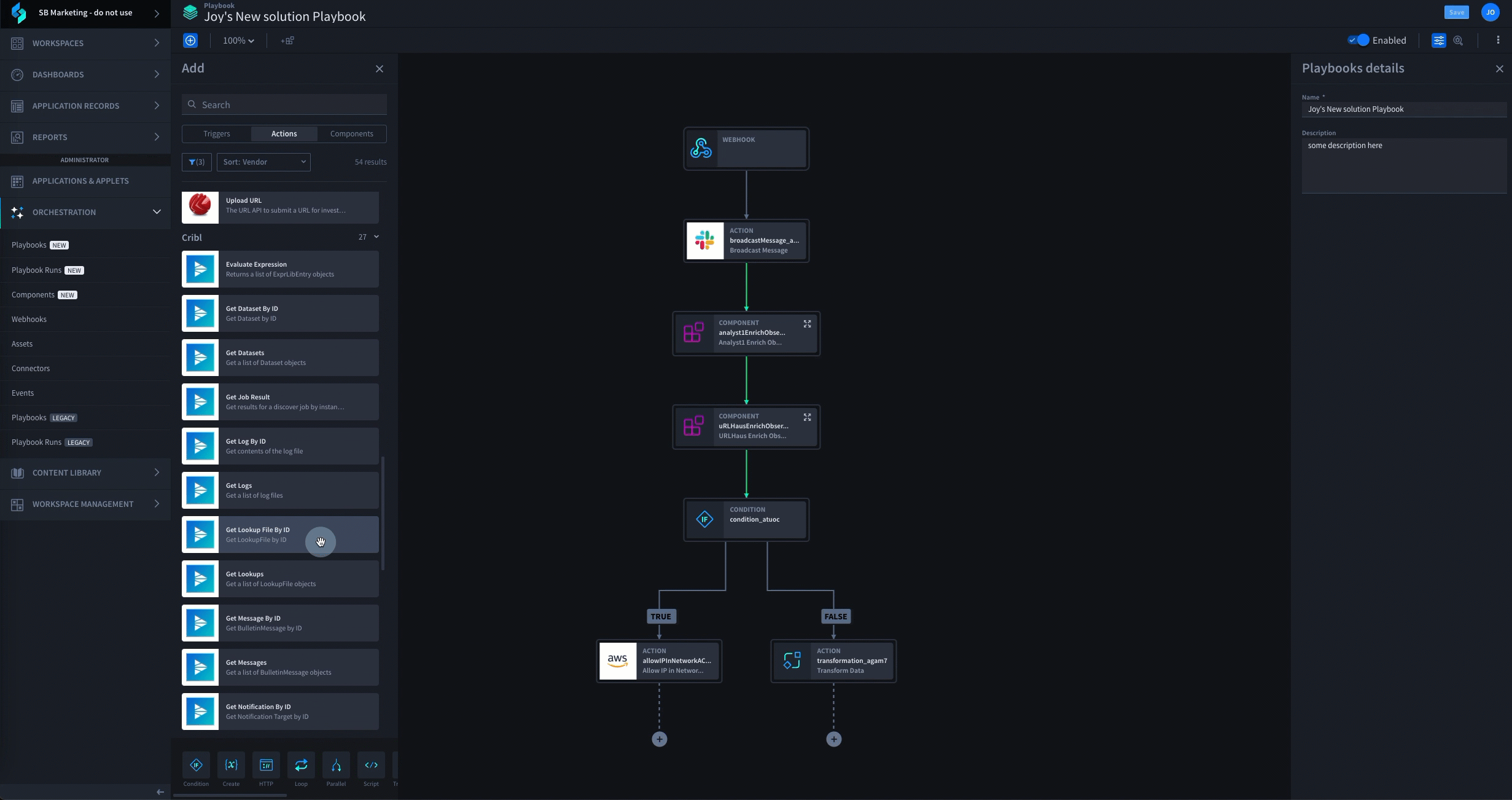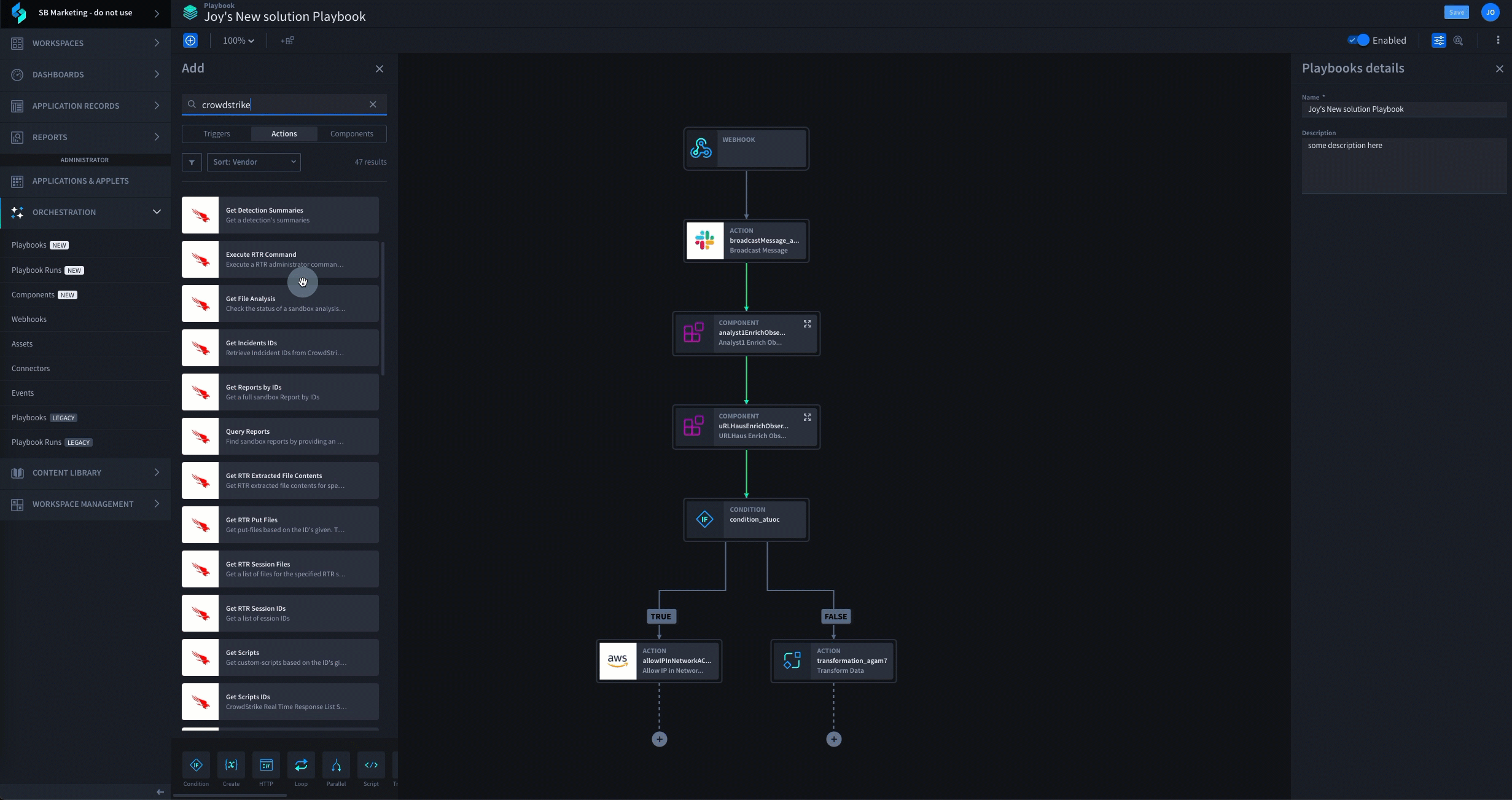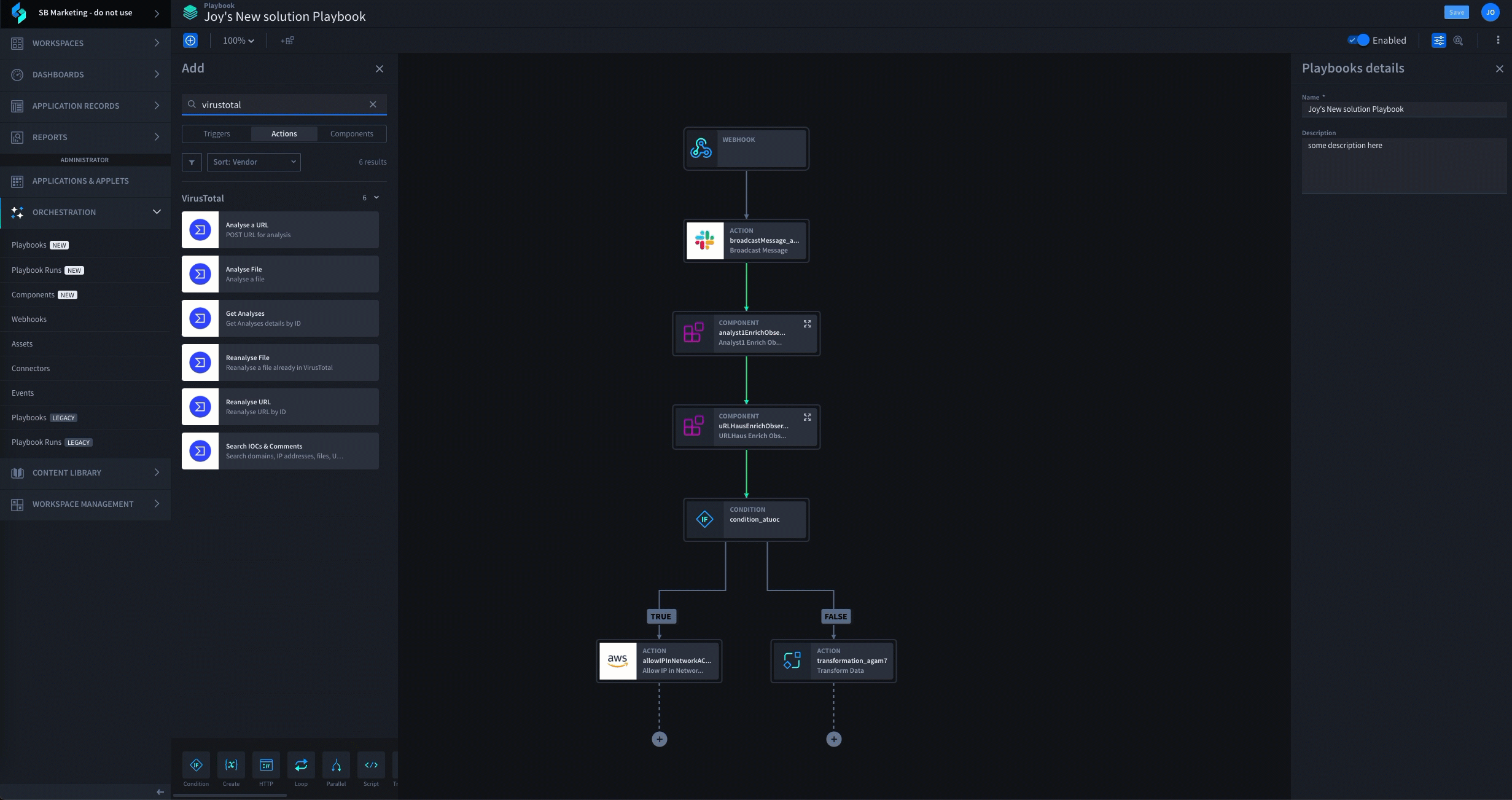
Swimlane Turbine stands out as the best AI-enhanced low-code platform due to its unparalleled efficiency, flexibility, and comprehensive approach to security automation. Our low-code automation platform automates three times faster than any other technology, can integrate with any tool that is typically siloed, has a user-friendly interface to demonstrate ROI and outcomes and also ensures enterprise-grade scalability.
Choose Swimlane Turbine for Your Low Code Automation Needs
Discover the power of Swimlane Turbine, the fastest and most scalable security automation platform in the world. With Turbine, you can execute 25 million actions per day, which is 10 times faster than any other platform, provider or technology. Turbine is designed to meet the evolving needs of SecOps and can adapt to your environment, ensuring that your SOC team can keep pace with modern security operations.
Swimlane Turbine Demo
See how Swimlane Turbine can help you and your SecOps team hyperautomate by requesting a demo below.


