The world of security threats is ever-shifting, and the stakes couldn’t be higher. Security professionals – analysts, SOC managers, CISOs and more – stand on the frontlines to defend organizations from the relentless onslaught of cyber threats. But what happens when the enemy breaches your defenses? How do you respond when chaos strikes and your digital fortresses are under attack?
That’s where incident response comes into play. From IR plans to popular frameworks and tools, it’s important to stay informed and prepared.
What is Incident Response?
To put it simply, incident response is a systematic approach to addressing and managing security events within an organization. It encompasses the processes, tools and strategies employed to detect, respond to and recover various types of security incidents.
The primary goal of incident response is to minimize the impact of an incident and swiftly restore normal operations while safeguarding essential assets and data.
How Incident Response Works?
Incident response involves a systematic approach to addressing and managing security events within an organization. It encompasses the processes, tools, and strategies employed to detect, respond to, and recover from various types of security incidents. The main goal of incident response is to minimize the effect of an incident and restore normal operations while safeguarding assets and data.
Different Types of Security Incidents:
- Phishing Attacks: These encompass deceptive efforts to acquire sensitive information, like usernames, passwords, or financial data, by posing as a reliable entity through misleading communication.
- Ransomware: Ransomware incidents encrypt a victim’s data, demanding a ransom in exchange for the decryption key. It can disrupt operations and compromise data integrity.
- Supply Chain Attacks: These exploit weaknesses in the supply chain, seeking to undermine the software or hardware essential for organizational functions, frequently for disseminating malicious code.
- DDoS Attacks: Distributed Denial of Service (DDoS) attacks overwhelm a target’s network or website with excessive traffic, causing service disruption or downtime.
- Insider Threats: Insider threats contain malicious or unintentional actions by individuals within an organization, which can potentially lead to data breaches or security incidents.
By offering a precise definition of incident response and outlining various security incident types, you enable your audience to grasp the significance and extent of incident response. This also fosters an awareness of the necessity for a proactive security approach, like Swimlane Turbine’s AI enabled low-code automation.
What is an Incident Response Plan?
An incident response plan (IRP) is a documented set of guidelines and procedures that outlines the steps to be taken during a security incident. It provides a structured approach to effectively handle event and ensures action is swift, efficient and consistent across the organization.
An IRP can include predefined roles and responsibilities, communication protocols, incident categories, escalation procedures and technical steps.
Why is an IRP Important?
An IRP is important for many reasons:
Minimizes Damage: A timely and well-executed IRP can help minimize the impact of a security incident, reducing downtime, financial losses, and potential damage to the organization’s reputation.
Compliance and Legal Requirements: Many industries and regulatory bodies require organizations to have an IRP in place to meet compliance standards. A robust plan demonstrates a commitment to security and can assist in fulfilling legal obligations.
Rapid Recovery: An IRP enables organizations to recover swiftly from security incidents, restoring normal operations and mitigating any disruption to critical services.
Stakeholder Confidence: By demonstrating a proactive and competent approach, organizations can instill confidence in their customers, partners, and stakeholders, reinforcing trust and maintaining a positive reputation.
Examples of Incident Response Plan Templates
Security professionals can save time and kickstart their processes faster with IRP templates. Various providers and institutions have created templates to gain inspiration from:
Incident Response Playbooks are essential when it comes to identifying and responding to security breaches. Learn more in our guide on IR playbook templates to understand how incident response templates can be utilized.
Different Phases in Incident Response Frameworks
The incident response lifecycle consists of several interrelated phases that guide security professionals through the process of managing and resolving security incidents.
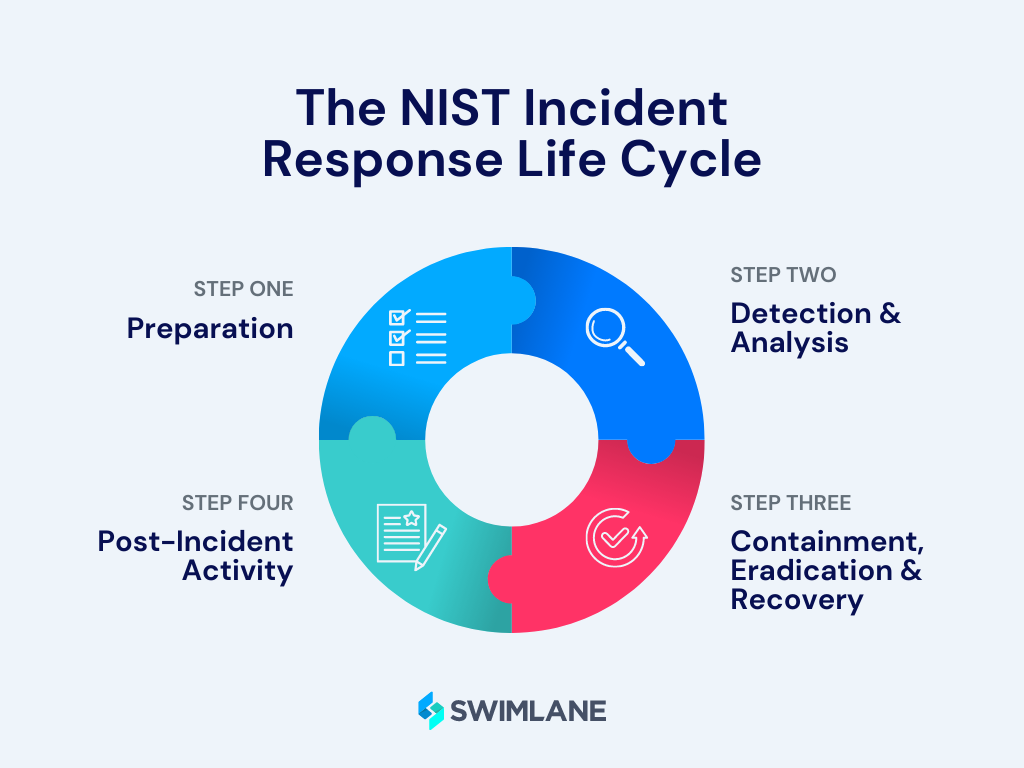
NIST Incident Response Framework
For instance, The National Institute of Standards and Technology (NIST) framework includes:
1. Preparation: Establish an IRP, define roles and responsibilities, assemble an incident response team and implement necessary security controls and technologies.
2. Detection and Analysis: In this phase, security incidents are detected through various monitoring and alerting mechanisms. Incident analysts investigate the incidents, gather evidence and assess the impact and severity of each incident.
3. Containment, Eradication and Recovery: Once an incident has been confirmed, immediate action is taken to contain the incident, prevent further damage, eradicate the threat and recover affected systems and data.
4. Post-Incident Analysis: After the incident has been resolved, a comprehensive analysis is conducted to determine the root cause, identify any weaknesses in the security posture and implement measures to prevent similar incidents in the future.
SANS Incident Response Framework
There are similar steps in the SANS incident response plan, which is broken up into six key steps:
- Preparation: This phase involves setting the groundwork for incident response, including policies, response plans, team member assignments, access controls, and training, ensuring the readiness of the Computer Incident Response Team (CIRT) for efficient incident handling. It’s an important phase to determine the effectiveness of an organization’s response strategy and communication channels, equipping the CIRT with the right tools and knowledge to mitigate the impact of security breaches.
- Identification: The identification phase is centered on promptly detecting and verifying security incidents using log files, monitoring tools, intrusion detection systems, and firewall data to assess the nature and scope of the incident. Identifying these early enables rapid response, minimizing costs and damages.
- Containment: This is the immediate response phase aimed at limiting the incident’s scope and preventing further damage, following early detection or identification. SANS advises implementing thorough containment measures, including preserving evidence for possible legal action, as effective containment is crucial for minimizing harm in a security incident.
- Eradication: This phase involves eliminating the root cause of the incident while ensuring that affected systems are cleaned and secure. This stage centers on reinstating systems to their prior state with minimal data loss and involves eliminating malicious elements to prevent re-infection.
- Recovery: Recovery encompasses testing, monitoring, and validating systems before they’re reintegrated into production to ensure they remain uncompromised. It involves deciding when to resume operations, conducting thorough system tests, vigilant abnormality monitoring, and utilizing diverse tools to verify post-incident system behavior.
- Lessons Learned: This is a critical post-incident phase where organizations review the entire incident response process, documenting insights and improvements for future incident handling. This stage provides valuable data for updating incident response plans, improving training materials, and setting benchmarks for future incidents, which promotes continuous improvement in incident response capabilities.
Although different frameworks may present these phases in slightly different ways, the core stages remain consistent.
Role of Incident Response Teams
Incident response teams are crucial in protecting an organization’s digital assets and responding effectively to cybersecurity incidents. They perform diverse tasks to minimize incident impact and uphold a secure environment. Here’s a summary of their typical responsibilities:
- Incident Detection
- Incident Triage
- Containment
- Forensic Analysis
- Notification
- Mitigation
- Documentation
- Continuous Improvement
- Training & Preparedness
By performing these critical tasks, incident response teams enhance an organization’s overall cybersecurity resilience. Their capacity to promptly identify, respond to, and recover from security incidents is vital for minimizing potential damage and ensuring business continuity. Coupled with incident response automation and the adoption of modern incident response trends, these teams are better equipped than ever in defending against evolving cyber threats and safeguarding critical assets.
Automating Incident Response Processes
Incident response automation involves leveraging technology and tools to streamline and accelerate the incident response process. Automation can assist in several areas, including incident detection, data collection, analysis, containment, and recovery.
By automating repetitive tasks, security teams can focus on higher-value activities, such as triaging more complex alerts and threat hunting. Additionally, automation can improve response times, reduce human error and enhance overall incident management efficiency.
Learn more about automated incident response.
Incident Response Automation Solutions & Tools
Incident response automation has emerged as a valuable solution to streamline security incident management. It enables security teams to respond swiftly and effectively to security incidents. Some standard incident response tools that organizations can leverage include:
- Low-Code Security Automation
- Security Orchestration, Automation and Response (SOAR)
- Security Information and Event Management (SIEM)
- Extended Detection and Response (XDR)
- Endpoint Detection and Response (EDR)
Learn more about Managing Security Alerts with an Incident Response Platform.
Latest Incident Response Trends
Recent trends in incident response underscore a significant focus on automation, integration of threat intelligence, and improved collaboration. Automation is streamlining processes for incident detection and response, facilitating rapid threat detection and mitigation. The integration of threat intelligence feeds and platforms empowers organizations to proactively identify emerging threats and vulnerabilities. Collaboration is evolving with increased focus on cross-functional teams, breaking down silos between IT, security, and business units to improve incident resolution. The adoption of artificial intelligence (AI) and machine learning is improving the accuracy and speed of incident identification and response. This helps ensure organizations are prepared to defend against evolving cyber threats.
In today’s ever-evolving threat landscape, incident response is critical to a company’s security strategy. Modern security teams should implement a well-designed incident response plan and leverage automation to help minimize the impact of incidents, protect critical assets and maintain a secure environment.

Gartner: Selecting the Right SOC Model
‘Security and risk management leaders often struggle to convey the business value of their security operations centers to nonsecurity leaders, resulting in reduced investment, poor collaboration and eroding support…’ — Access this Gartner SOC Model report – courtesy of Swimlane.

