
SANS Product Review: Swimlane for Incident Response and Visibility
UNLOCK AI-DRIVEN PLAYBOOK ACTIONS
From integrations to playbooks, and dashboard widgets to full-blown solutions, Swimlane Marketplace features the most extensive collection of AI automation building blocks.
ROW - 01
Exchange, Teams, Sentinel, Graph, AD, Azure, 365 Security & more

Over 40 capabilities across Checkpoint R-80 API + Reputation API
EC2, IAM, CloudWatch, Config, GuardDuty, SecurityHub, S3 & more
IronPort, ThreatResponse, AMP, Umbrella, Meraki, Firepower & more

CrowdStrike Falcon, Hybrid Analysis Sandbox & Identity Protection

Integrated with FortiSIEM, FortiGATE, FortiMANAGER, and FortiEDR

Elastic Security, Elasticsearch (V6, V7, V8), and Elastic Endgame
NetskopeAPI (V1/V2) to manage events, alerts, reports & policies
Turbine alert ingestion for automated early warnings use cases

VirusTotal, Workspace, Chronicle, Compute, Big Query & Mandiant
Vulnerability Management and Response for Operational Technology
ROW - 02
Okta API integration to manage users, applications, and groups

Ingesting users, teams, services, policies & creating incidents

CortexXDR, AutoFocus, Wildfire, Panorama, URLFiltering, and more!
Deep integration on intelligence, vulnerabilities, and cred dumps
Singularity XDR Platform, DataSet, & BOTsink (Formerly Attivo)
Integrates Tenable.io, Tenable.SC & Nessus Vulnerability Scanner
Integrate Vision One, Deep Discovery, Apex Central & TippingPoint
Integration for IOC filtering, blocklists, lookups & reporting
Get data, edit notable events, and perform oneshot with Splunk

Elastic Security, Elasticsearch (V6, V7, V8), and Elastic Endgame
Integrations with Workspace ONE & 6 VMware Carbon Black Products

Add automation with Tanium and Tanium's Threat Response package
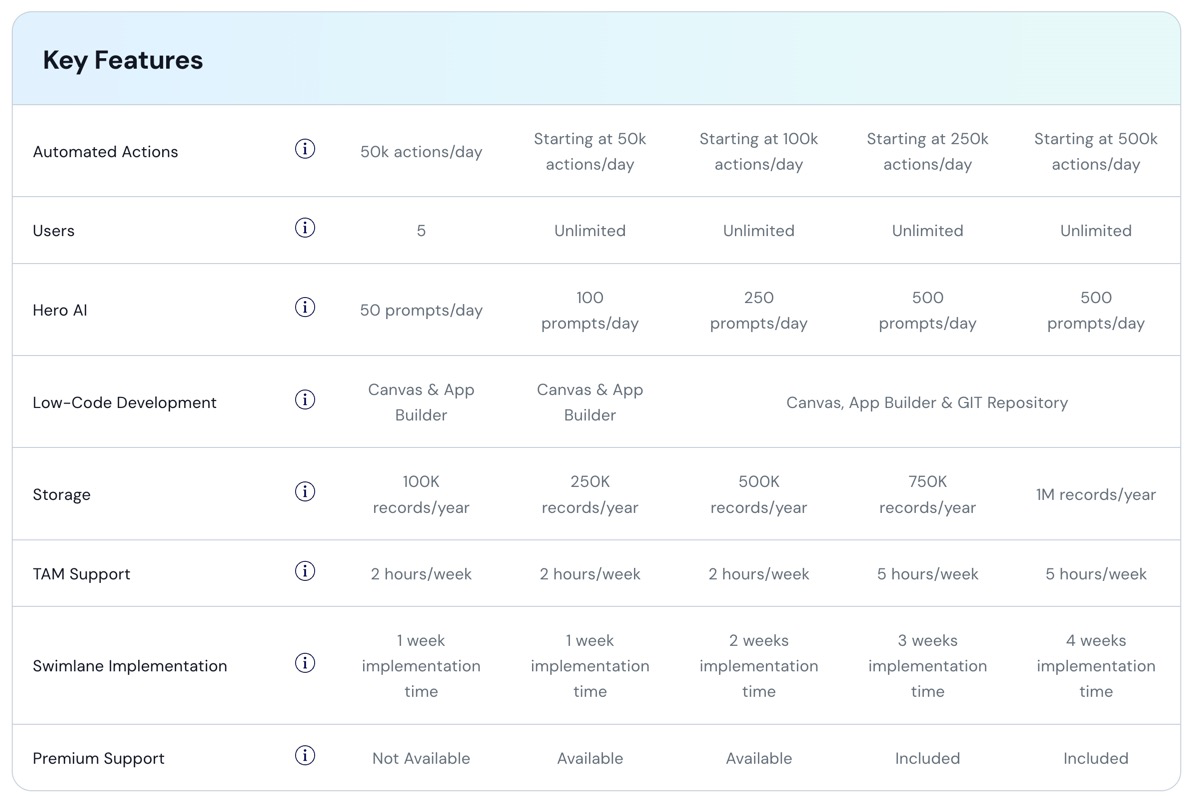
We know automation isn't one-size-fits-all, and neither is our pricing. Most customers discover their ideal, cost-effective solution within our tiered enterprise and MSSP pricing options below. Need something unique? If you're looking for a custom plan or user-based pricing, simply contact our sales team. We're here to help you find the perfect fit!
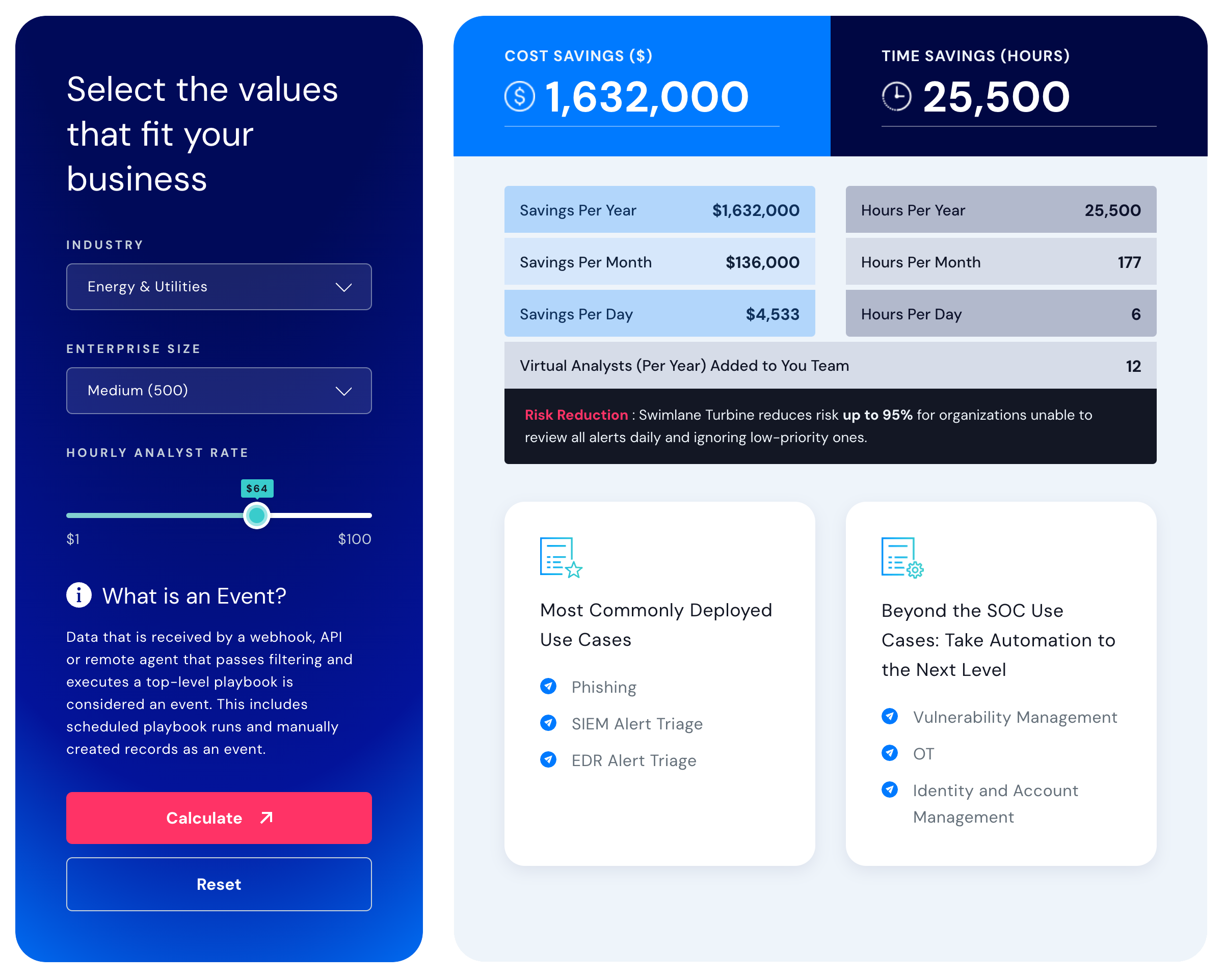
An independent return on investment (ROI) study conducted by TAG Cyber revealed 240% ROI for the Turbine agentic AI automation platform. Try this calculator to quickly estimate your organization's ROI with Swimlane.
Swimlane.
Major security-forward organizations including Bloomberg, Sagicor and Toshiba are advancing the operations of their security organization with Swimlane.
Trusted By
