Out-of-the-box Swimlane integrations automate Cisco AMP ThreatGrid malware defense processes
A common repetitive task performed in a Security Operations Center (SOC) is to submit suspicious files to a malware sandboxing technology. These technologies then execute the binary in a safe environment and report back with valuable details about how that particular bit of malware works. Analysts follow up by reviewing the results and taking various actions like gathering additional information from threat intelligence sources, updating rule sets, performing remediation procedures like isolating a host and more. Unfortunately, other than the sandbox running itself, these are very time-consuming manual processes.
Swimlane’s out-of-the-box integration with Cisco ThreatGrid allows you to automate a large part of the malware investigation and response process. It can submit suspicious binaries for execution in ThreatGrid’s sandboxing technology, retrieve the resulting report and then automatically execute an appropriate response.
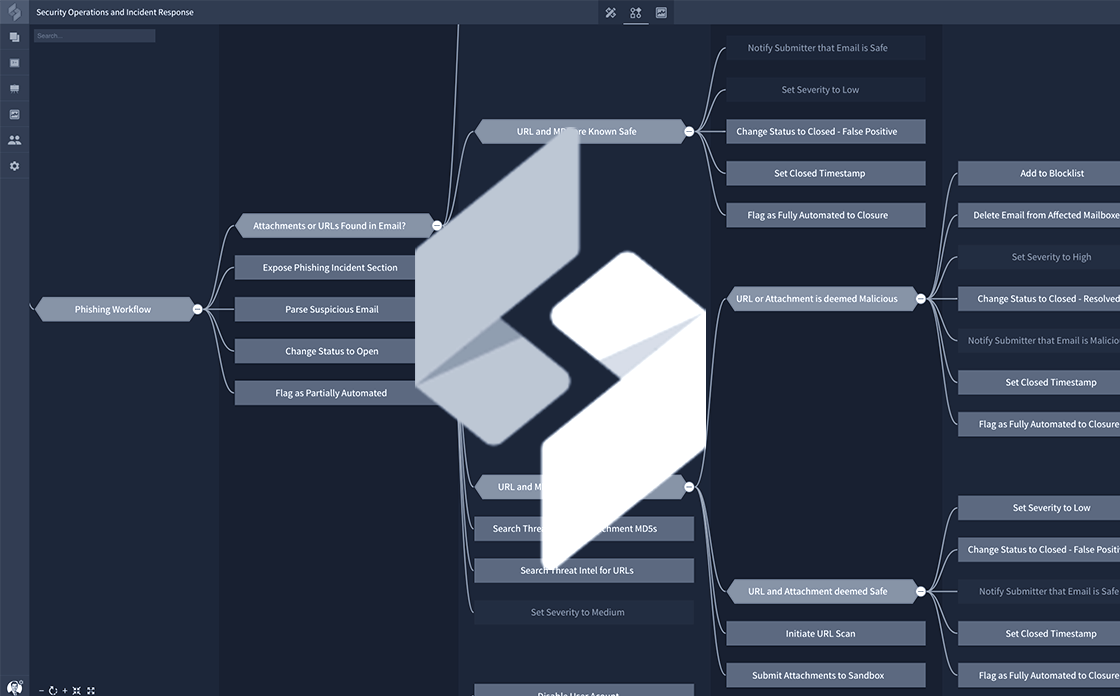
Driven by Swimlane’s built-in, automated workflow capabilities, different sets of remediation actions can be taken based on the results of ThreatGrid’s sandbox report. An example of this is depicted in the workflow below.
A common specific use case for leveraging Swimlane integrations with a sandboxing technology like ThreatGrid is to analyze suspicious email attachments. Often a security team will implement a program that allows users to submit suspicious emails to the SOC for analysis. Manual analysis of these emails can take quite a bit of time – extracting headers, pulling URLs out of the body, grabbing attachments, submitting these to sandbox technologies and querying threat intelligence sources for the indicators.
And that’s just to determine whether the email is an actual Phishing attempt. Response actions are completely separate set of typically manual tasks that a security analyst must perform. But they can now be intelligently automated using Swimlane’s data-driven workflow in conjunction the full collection of integrations available in Swimlane.
If you’re interested in learning more, watch a live demo of our integrations with Cisco Security products in an on-demand webinar “Stop Phishing Attacks with Automated Incident Response” presented by Cisco AMP ThreatGrid and Swimlane.