Find out how security automation helps triage phishing alerts for faster remediation.
Phishing continues to be a dangerously effective attack method. Roughly 91% of successful attacks start with phishing. On average, 30% of the phishing emails sent get opened and viewed. Considering the minuscule cost and effort involved to create and send an email, it is no wonder this method continues to be so popular for attackers.
And it’s becoming increasingly difficult to spot a phishing attempt. Attackers sending phishing emails can expect between 10% and 15% of the time that the malicious attachment or link will be accessed in some companies.
Without phishing automation, an analyst must manually receive a potentially malicious email through some system of detection or by notification from a user. The analyst must then inspect the email and manually extract details to validate them.
This means looking at every part of the email in detail (headers, body, everything) and identifying anything that could potentially be an indicator of compromise (IOC). To determine the IOC’s risk, analysts must then access various threat intelligence and enrichment sources. This usually requires copying and pasting information into additional windows or browser tabs to investigate the IOCs and determine their risk.
These steps are tedious, time-consuming, monotonous, repetitive and easily messed up. Executing the response and any remediation actions adds even more steps and more time to the whole task of handling a single potential phishing message.
In this article, you’ll learn:
What is Phishing?
Phishing is a type of social engineering cyber attack that uses various methods to trick victims into disclosing personal or business information. Malicious actors will use email, SMS messages, phone calls, voicemails and in-app messaging to target victims. Much like the bait on a fishhook, as phishing attempts are often disguised as messages from a legitimate business or organization.
The most common types of phishing include:
-
Email phishing: the most common type of phishing attack. Phishing emails can be sent from fake domains, and often include malicious links to fake domains.
-
Spear phishing: a personalized form of phishing. Malicious actors will use your name, job title, employer, email address and more to trick victims.
-
Whaling: an attack method that imitates senior-level employees at your enterprise. Often, this will look like an urgent email from the CEO asking you to transfer money or share private information.
-
Smishing and vishing: phishing attacks that target victims with text messages and voicemails. This style of phishing is especially hard for security teams to catch before damage is done.
Phishing scams can be sent individually to an unsuspecting target, but they’re usually sent in large batches to increase the chances of catching someone at the right time – when they’re more likely to click on one of the links.
It’s easy to see how the frequency of phishing attacks has grown to be too much for security teams to manually triage.
The Problem for Security Teams: Too Many Alerts
Phishing, in particular, can produce more alerts than any other type of cyber attack simply because it is such a rampant problem. It is one of the oldest types of cyber attacks and has become exceedingly sophisticated over the years. When managing potential phishing attacks, organizations face numerous problems:
-
Millions of phishing emails are sent every day
-
Investigations require analysis between multiple security platforms
-
It takes an average of 27 minutes to manually triage one phishing email
-
Many organizations lack the manpower necessary to investigate the high volume of daily phishing alerts
-
Poor Mean Time to Resolution (MTTR) increases risk and potential damages
The number of organizations targeted by phishing attacks grew by 28% in 2021.
Automated Phishing Alert Triage Tools
There aren’t enough hours in the day for SOC analysts to manually triage all phishing attempts. To combat this problem, security leaders rely on security tools to triage phishing alerts faster. Security automation tools can be used to automate a phishing attack investigation which will significantly improve security and ensure protection for your organization.
Automated Investigation with SOAR
Security orchestration, automation and response (SOAR) platforms are commonly used to automate the investigation process and to quarantine suspected phishing emails. SOAR platforms remove the need for human intervention unless absolutely necessary. By automating the repetitive, mundane tasks around phishing, you can reduce the number of alerts SOC analysts receive, which allows them to focus on more serious threats.
If a possible phishing email triggers an alert, SOAR technology can automatically pull suspected phishing emails from the inbox to prevent users from opening them. The IPs and URLs are then extracted and researched using threat intelligence tools.
If the threat is a known malicious phishing attack, then an IT ticket is automatically opened, the endpoints quarantined, and all emails in the system containing the malicious file are deleted. If the threat is unknown, then the attachment is first submitted for sandbox inspection. If it is then found to be malicious then it follows the same protocol and will be quarantined and deleted.
See phishing automation in action with Swimlane, below.
The Benefits of Low-Code Security Automation
Low-code security automation expands upon the capabilities of legacy SOAR solutions to provide faster, more adaptable phishing automation. By using low-code security automation to combat phishing attacks, security teams can reduce MTTR and handle any threat at machine speeds.
Incident response processes throughout your organization are more clearly defined and executed consistently with automation. This reduces the possibility of human error, and workflows can be modified as new anti-phishing techniques are implemented within an organization. Plus, incident reports can be automatically generated so that analysts can understand the breadth of the phishing attack without spending too much time manually weeding through the systems and steps necessary to resolve it.
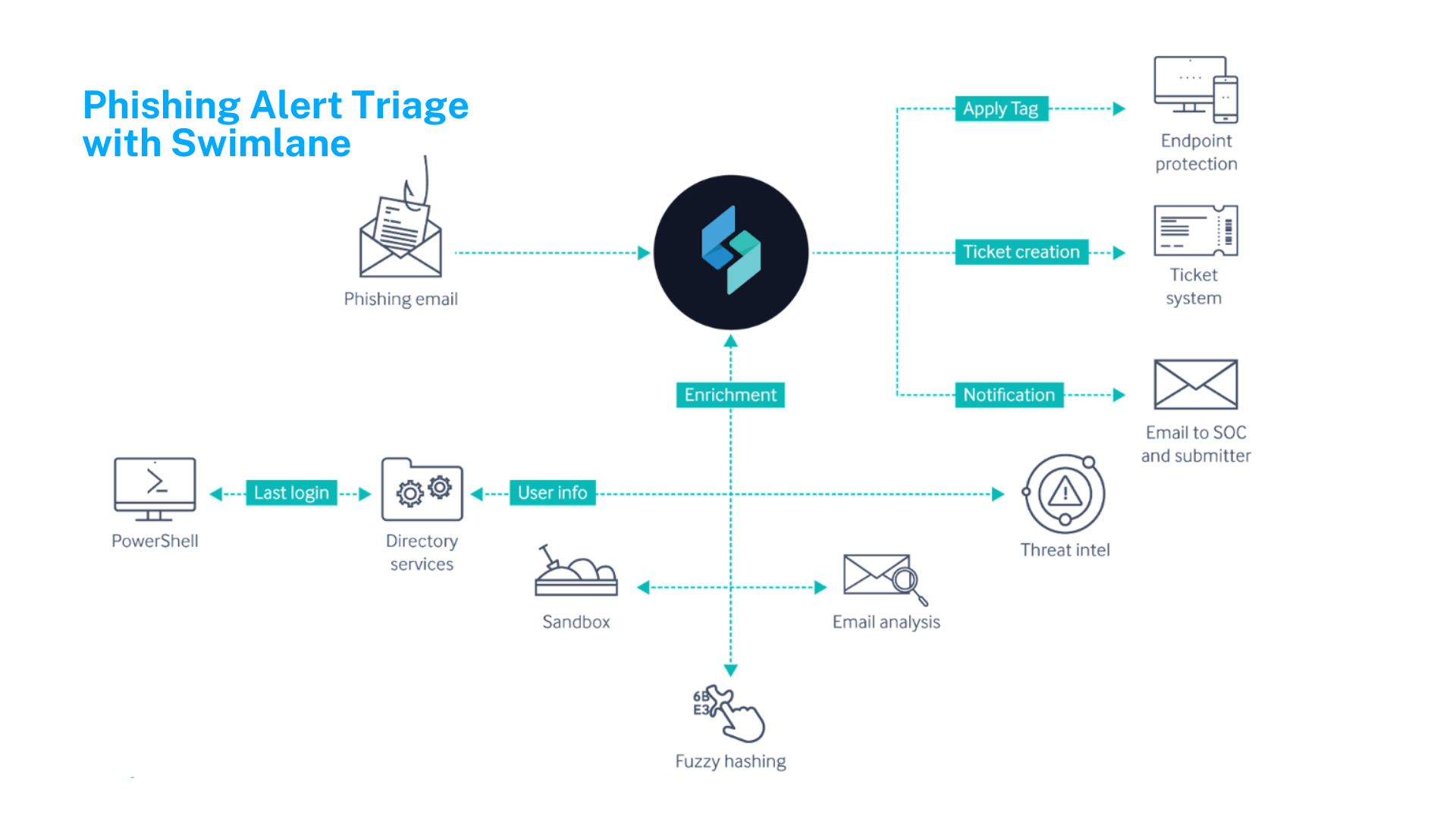
Low-Code Security Automation with Swimlane
Swimlane Turbine helps integrate your existing security solutions and tools into a centralized platform that streamlines incident response. Powerful data integration and user-friendly playbook building enable domain experts to become automation builders. It can automate the investigation and quarantine of suspected phishing emails, as well as help organizations:
-
Centralize all security data into dashboards for more accessible reporting
-
Standardize incident response processes
-
Track security tasks across the enterprise
-
Reduce MTTD and MTTR
-
Prioritize threats to ensure that all alerts are investigated thoroughly
-
Automate various processes and workflows
-
Improve security performance
Automated phishing investigation and response is only the beginning with low-code security automation.

A Buyer’s Guide for Modern Security Automation
Enterprise SOC teams recognize the need for automation but often struggle with the automation solutions themselves. Security Orchestration, Automation and Response (SOAR) solutions commonly require extensive scripting. This guide analyzes the wide range of security automation platforms available today, so you can identify the type of solution that fits your needs the best.


