The best cybersecurity programs blend two basic security concepts: defense in depth and the business impact risk “heat map.” Defense in depth is the practice of building layers of countermeasures to prevent a breach in one layer from putting an entire system at risk. This approach might include firewalls, rules-based controls, identity and access management, physical security, biometrics, encryption, incident management and so forth.
The best cybersecurity programs blend defense in depth and the business impact risk “heat map.”
In contrast, the heat map cuts across these layers of defense and focuses cyber defense resources on the most critical data assets. If a breach of a particular database could cause the most damage to the business, it should get the best defense.
These components result in a matrix of countermeasures and controls of varying intensity for each of the organization’s particular security tools and playbooks.
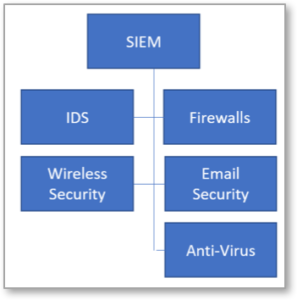
Figure 1 – Integration between a SIEM system and security tools which feed data into it.
Integrating cybersecurity tools for better defense
No single cybersecurity tool can do everything. Separate tools each play a role in a broader, integrated security solution. The organization’s specific needs determine how each tool functions and interacts with one another, but to function collectively, they need to be integrated.
Imagine that an organization employs:
- Firewalls
- Wireless network security appliances
- An Intrusion Detection System (IDS)
- Email-based security
- Anti-virus software
While each tool performs specific duties, unless integrated, its efforts will be isolated, and the impact on the organization’s overall security posture will be limited. A Security Incident and Event Management (SIEM) system can help. SIEMs assimilate inputs from each of the security tools. Figure 1 shows a way to visualize these connections.
A SIEM solution analyzes multiple data feeds and identifies potential threats by correlating data points amongst the different tools. This is made possible through application integration. Each tool integrates with the SIEM solution to share its data feeds. This integration between tools enables better security than an individual tool provides on its own.
It’s possible to take the security-through-integration scenario further with a Security Automation and Orchestration (SAO) solution. SAO automates the processes of analyzing threats and responding to incidents in a single platform. Figure 2 shows how it looks. SAO can take inputs from SIEMs, as well combine data feeds from external threat intelligence sources. Then, through its case management and automation interface, it executes preset, orchestrated playbooks through ticketing apps like JIRA.
Making security integration simple
For this to work, integration must be simple, fast and inexpensive. If the technologies and processes are cumbersome and proprietary, integration may be too costly for a security environment. There are simply too many moving parts and changes to make proprietary or professional services-heavy integration a reality.
Instead, security integration relies on open standards. While the details vary by vendor, most modern security tools, SIEM systems and SAO solutions use RESTful Application Programming Interfaces (APIs) and the JSON language over HTTP. With these widely-accepted APIs, languages and protocols, it is possible and easier to connect and reconnect the elements of an integrated security environment at will.
If the integration technologies and processes are cumbersome and proprietary, integration may be too costly for a security environment.
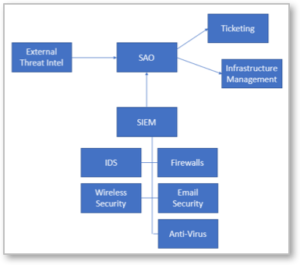
Figure 2 – An SAO solution takes data from SIEM and its integrated security tools and provides a centralized, automated management process for incident response.
Integrating the Swimlane SAO solution
Swimlane’s SAO solution automates security operations for enterprise teams. It delivers centralized security alerts and real-time security orchestration and automation to respond to incidents automatically—at machine speeds. This drastically lowers MTTR and provides additional context in which to evaluate any given alert.
Plus, analysts can automate repetitive tasks using Swimlane to manage incidents more efficiently. This increases job satisfaction while making every security analyst much more productive.
Swimlane is delivered with pre-configured integrations with leading cybersecurity technologies using common scripting languages and a RESTful API. Wherever an organization is with its heat map and defense in depth capabilities, this standards-based open integration capability is extremely useful in equipping organizations with the most effective cybersecurity possible.


