Cybersecurity management is a challenge. Many organizations lack the resources and staff needed to tackle the growing number of threats to their organization. This inability to handle the volume of alerts results in many threats going uninvestigated. And that leaves organizations susceptible to serious attacks.
Up to 70% of security alerts are ignored due to staffing and workday restrictions.
Automated incident response is the solution for dealing with the overwhelming number of security threats your organization faces. With automated incident response, alert monitoring is streamlined and response times significantly decrease. Incident response automation allows you to address every alert and reduce risk exposure.
The problem: Security operations teams are overwhelmed
Currently, cybersecurity teams are overwhelmed. In large organizations they handle between 10,000 and 150,000 security alerts every day. Depending on the specific instance, it can take anywhere from 10 to 40 minutes to manually investigate a single alarm in some cases, such as a suspicious binary. That’s why as many as 70 percent of all alarms end up not being investigated.
Current security workflows are inefficient
Overwhelmed employees rely on workflows and playbooks to help streamline their alert response management, but when workflows are inefficient alert management suffers. A number of factors contribute to sub-optimal security workflows including:
- Inconsistent response processing for critical threats
- Triage methods ignore a large number of threats
- Failure to integrate people with available technology
- Loss of security knowledge due to staff turnover
- Changing compliance regulation on security policy
The answer: Automated incident response
An automated incident response solution provides your organization with the tools to model and automate many of your manual and time-consuming response processes.
Tasks that can be automated include:
- Reviewing and analyzing threat intelligence sources
- Investigating incidences involving log gathering and analysis
- Updating tickets
- Gathering metrics and creating reports
- Sending email alerts
- Resolving alerts
Every automated step saves a few minutes for each alert, saving time and improving your organization’s incident response.
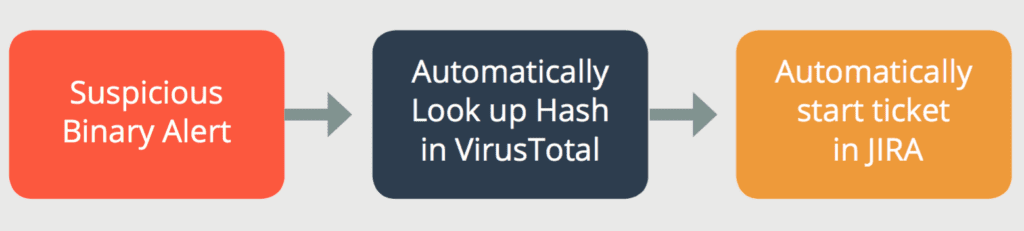
Incident response automation allows your organization to handle more threats in the same amount of time. Plus, by automating responses, your cybersecurity team can focus their training and skills on serious threats instead of operational drudgery. This force multiplier has the additional positive effect of increasing morale and lowering staff turnover as the tedium and stress of the workday is reduced.
A comprehensive dashboard logs and interprets past incidents while providing context for new threats. This information provides a basis for deep analysis and understanding of your organization’s current security condition. With this information, you can address risk management planning and future security needs… as well as provide additional reporting for security audits and compliance.
The Swimlane solution
Swimlane replaces your organization’s manual and time-consuming incident response methods with a centralized automated system. With Swimlane you can:
- Track enterprise security tasks
- Centralize data into accessible reports, dashboards, and metrics
- Standardize the threat response and notification processes
- Leverage APIs and Software Defined Security (SDSec) to rapidly respond and prevent attacks sooner
Want to learn more about the benefits, impacts, and ROI of incident response automation? Download our Automating Incident Response 20-page eBook for a more comprehensive look.

