Cybersecurity statistics have become a bit more ominous as we review the first half of 2017—and according to industry reports, things aren’t looking up anytime soon.
From an alarming increase in brute force ransomware attacks to more sophisticated social engineering techniques, SecOps teams are understandably looking for more reliable ways to prevent alert fatigue, make sense of the data, and implement effective solutions to avoid costly data breaches and downtime.
Today’s cybersecurity isn’t as secure as you think
To help your SecOps team better understand the latest cybersecurity statistics and cut through the noise, we’ve compiled some cybersecurity statistics and facts from the first half of 2017 along with a few potential solutions:
1. The volume of threat alerts has become staggering.
Alert fatigue is a very real problem for embattled SOC professionals.
With organizations receiving an average of 17,000 malware alerts per week—and of that, fewer than 20 percent worthy of examination—only 4 percent of all valid threats are actually investigated by those in the trenches.
To make matters worse, Intel Security reports that 93 percent of security personnel are overwhelmed by alert data and unable to triage all potential threats.
2. Incident response teams’ mean time to resolution (MTTR) is generally unacceptable.
According to the SANS Institute’s Incident Response Capabilities in 2016: The 2016 SANS Incident Response Survey, just 29 percent of survey respondents reported a response time between two and seven days—and 38 percent of SOC teams admitted they often couldn’t respond in under one week.
Ponemon’s study on Malware Prevention and Detection reports that the average company takes 170 days to detect an advanced threat, 39 days to mitigate, and 43 days to recover.
It’s clear that a more automated and orchestrated response to threats and incidents is critical.
3. Ransomware is rampant.
Ransomware is currently the hacker’s preferred method of attack—and it’s often the most elusive, making even the most sophisticated SIEM systems ineffective.
According to think-tank Cybersecurity Ventures, the number of global ransomware attacks on businesses is only expected to get worse. In just two years, attacks are up 15X—and damages are predicted to exceed $5 billion this year alone, an uptick from $325 million in 2015.
To put that into perspective, the FBI reports that more than 4,000 ransomware attacks occur per day, a 300 percent increase from 1,000 per day back in 2015.
4. Despite an organization’s best attempt at education, employees continue to be a weak link.
When it comes to your company’s security architecture, your employees’ “bring your own” mobile devices (BYOD) and networks (BYON), the popularity of wearables and IoT, and often poor password habits become one of your greatest vulnerabilities.
Cisco reports that Wi-Fi and mobile devices will make up two-thirds of internet traffic by 2020, up from 48 percent in 2015—and the number of IoT devices will increase from 16.3 billion to 26.3 billion during that time. More than 300 billion passwords will be in use by 2021, including 200 million IoT credentials alone.
SIEM systems are designed to alert SOC teams of suspected threats—but where employees’ actions and private devices are concerned, relying on SIEM alone may not be enough to trigger the immediate action necessary for an effective response.
5. Email remains the vector of choice for malware.
With today’s increasingly savvy and motivated cyberattack enterprise, employees aren’t vulnerable just because they’re connected; they’re vulnerable because they are human.
To make matters worse, a cleverly disguised email attachment that appears to come from an official source can often get past even the most powerful SIEM system. The Radicati Group reports that the number of emails transmitted per day will reach 319.6 billion by 2021—and with 88 percent of pretexting attacks using email as the top method of communication according to Verizon’s 2017 Data Breach Investigations Report, employees are an obvious vulnerability and a preferred business attack vector.
Then add a persistent hacker’s clever social engineering techniques, and even the most well-trained employee may fall victim to a phishing campaign or other malicious attack.
Optimize with security automation and orchestration (SAO)
In a cybersecurity threat landscape where no business is safe from attack, organizations must find a way to effectively triage, investigate, and escalate the threats that matter.
A comprehensive, SAO-driven interface allows you to integrate all systems into one unified, central platform to arm SOC teams with a transparent, comprehensive view of your organization’s security operations.
How Swimlane can help
While it’s impossible to completely secure to your organization, maximizing your existing investments in SIEM, IDS, and other security tools by investigating all of your security alerts is a good place to start. Swimlane, a security automation and orchestration platform, allows you to automate 80–90 percent of incoming alerts while providing additional context and analysis for alerts that require manual investigation.
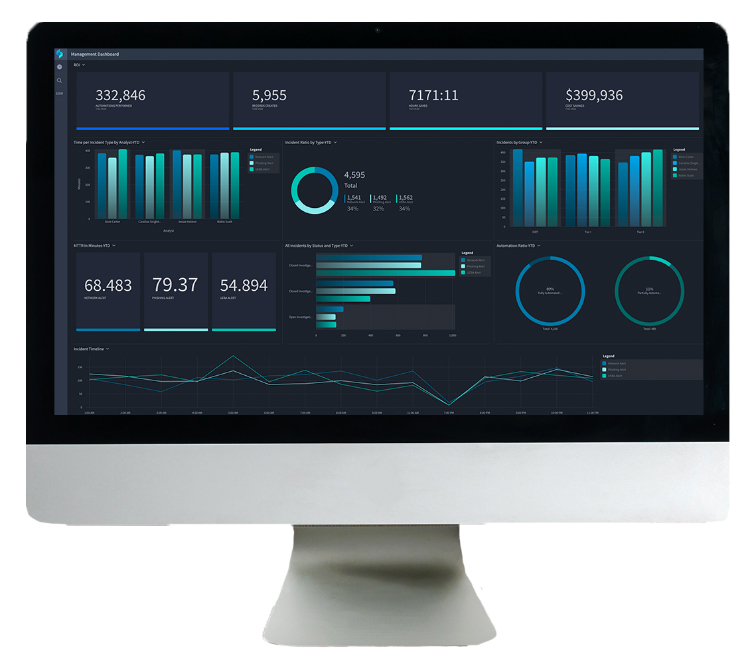
Swimlane delivers a comprehensive dashboard interface and metrics to enable SecOps teams to spend more time focusing on the critical threats that matter. Since 80 to 90 percent of all incident response tasks can be effectively automated, Swimlane helps reduce MTTR and improve operational performance with dramatically reduced downtime and, ultimately, a better bottom line.
For more information on how Swimlane can help keep your organization safe from potentially devastating cyberattacks, schedule a demo or check out our free eBook on how security automation and orchestration can help your organization.


