Planning and executing a cybersecurity incident response workflow means trying to achieve certainty about facts that cannot be known in advance. Given that challenge, security managers find that automating some or all of their incident response workflow using a security automation and orchestration (SAO) solution can provide numerous benefits. Automation reduces uncertainty and promotes efficiency in the response process. This article explores what’s involved in making it happen.
Don’t include the walrus in your incident response planning
The incident response plan for the 2010 Deepwater Horizon oil rig tragedy contained a curious detail that reveals a great deal about why these plans don’t always work. The 600-page plan called for protection of “sea lions, seals, sea otters (and) walruses” in the Gulf of Mexico. None of these animals call the Gulf of Mexico home, and they’re in the plan because the text was pasted from a document written for oil rigs in the Arctic.
The only thought more laughable than sending people out to rescue walruses in a tropical climate is the notion that a static 600-page response plan would be useful in a real emergency. Even the best plan can be rendered useless over time by staff turnover and changes in relevant technology. As you prepare your incident response plans and incident response workflows, keep those walruses in mind to stay focused on what matters.
Common Incident Response Plans
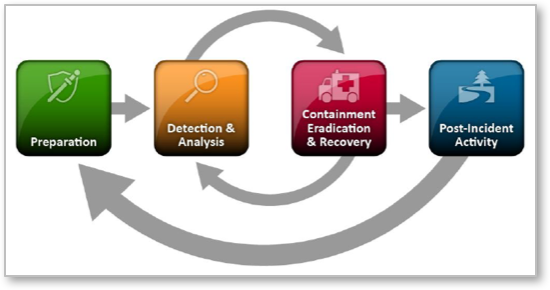
Figure 1 – Basic incident response workflow. (Source: NIST – Computer Security Incident Handling Guide – Special Publication 800-61)
Every organization has its own unique set of incident response steps. However, most incident response plans follow a pattern set out in the National Institute of Standards and Technology (NIST) Computer Security Handling Guide.
As shown in the figure, there are four essential elements in the NIST incident response workflow:
- Preparation
- Detection and analysis
- Containment, eradication and recovery
- Post-incident activity.
Within these four simple boxes, however, may be hundreds of steps connecting dozens of people and entities — and varying widely by organization.
Incident response highlights
The NIST recommendations, which are mandatory for certain types of government agencies and businesses, typically include the following elements:
- Preparation – As experienced security managers know, the best incident response plan is the one you never have to use. NIST recommends focusing on incident prevention. It’s important to anticipate threats and mitigate them with effective countermeasures. However, since today’s threat environment basically guarantees there will be incidents, an incident response workflow benefits from solid preparation. There is enough stress when a serious incident occurs, and it pays not to be caught flat-footed by something truly unexpected.
As experienced security managers know, the best incident response plan is the one you never have to use.
- Detection and Analysis – This incident response step validates that an incident has occurred, determines what has happened and the seriousness of the incident, and puts notification procedures in place. Cybersecurity teams are inundated with false positives. A good incident response plan immediately recognizes the signs of an incident, which helps security managers determine whether the events being observed actually constitute an incident. The workflow should include steps to identify the attack vectors, prioritize the seriousness of the incident, put remediation into effect, and communicate with key stakeholders on a timely basis. The process also needs to include incident documentation.
- Containment, Eradication and Recovery – The incident response workflow invariably documents the containment of the threat. This step also rids the environment of the threat, recovers any affected systems, gathers and handles evidence and identifies the attacker.
- Post-Incident Activity – After the incident, most teams discuss lessons learned, as it may help to improve future defenses and incident responses. In many cases, it is important to retain all evidence collected during the incident for auditors, attorneys, technology vendors, government agencies, insurance carriers, and other stakeholders.
- Coordination – Incident response is not a solo activity. Depending on the size and scope of the organization and the incident itself, the incident response plan may involve communicating with internal stakeholders, like senior executives, general counsel and others, or external third parties, such as law enforcement agencies and media. How these communications are handled can either heighten or diminish the incident’s business impact. For example, a clumsy disclosure of a data breach could result in costly brand damage or increased customer service costs. Or worse, poorly delivered information sharing could cause legal liability.
The NIST document makes it clear that incident response is not a solo activity.
Security automation and orchestration (SAO) and incident response plans
A cybersecurity incident combines risk with complexity. These two factors together are seldom a good thing. The team has to execute quickly and effectively even though the nature of the incident may not be fully understood at the outset. Plan or no plan, it may not be known which stakeholders need to be notified, which resources are required and so forth when the threat is first detected.
One solution is to automate as many steps of the process as possible. This way, team members can focus on important matters while routine steps, like sending email notifications and assessing threats, can be done automatically. This is the idea surrounding security automation and orchestration (SAO). SAO solutions, like Swimlane, replace slow, manual analyst tasks with machine-speed decision making.
SOA solutions, like Swimlane, remove slow, manual analyst tasks from threat and event responses.
Coupled with comprehensive data gathering, standardization and analysis, SAO enables security teams to implement sophisticated incident response plans. Its effect on an incident response workflow looks like this:
- Preparation – SAO makes it possible to transfer plans developed in preparation into actionable, automated workflows. An SAO solution captures the knowledge generated in the preparation stage, making it resistant to the effects of staff turnover and forgetfulness. For instance, if part of the plan includes notifying certain stakeholders during an incident, then that task will be performed automatically. The team will not have to crack open a never-before-read PDF to determine who to alert.
- Detection and analysis – SAO streamline the critical steps of detection and analysis. For example, an SAO solution can gather contextual alert data from multiple sources, analyze it and recommend a course of action to the analyst. Or, it can automatically execute the appropriate preventative actions, like setting up a ticket in JIRA, emailing key stakeholders, quarantining the threat, updating the threat database and so forth.
- Containment, eradication and recovery – Team productivity counts in incident response, and the incident response steps may not align with staffing conditions at the moment of an actual incident. However, SAO solutions help the cybersecurity team perform efficiently and save hours in incident response and threat detection work. Part of the productivity gain stems from the team member’s ability to monitor an incident through a single instance and take action where needed.
- Embedding of team reaction processes – SAO solutions can mimic the detailed practices of the best members of the security team. As their reaction processes (e.g. what’s important, what’s not, who to call, who to email, what to do, etc.) are included in automated workflows, the tool captures knowledge and best practices. By “remembering” how things get done, SAO can mitigate knowledge loss during inevitable staff turnover.
- Post-incident activity – By their nature, SAO solutions create logs of the incident response tasks it performs. This enables a more holistic view of an incident and provides time savings when reviewing the incident post-resolution.
- Coordination – SAO solutions orchestrate the coordination between people, entities and systems that arise in incident response workflows. They make it easier for team members to concentrate on critical decisions rather than notifications – the system does it for them.
How Swimlane can help
Swimlane delivers security automation and orchestration that is easy to implement, use, manage and scale. Swimlane allows a security operations team to leverage the capabilities of their existing security solutions and enrich the information presented to the analyst.
Want to learn more about the Swimlane SAO solution? Download our e-book: Automating Incident Response.


