Incident response involves the standardization and implementation of a set of processes, policies and procedures used to triage and respond to a variety of security incidents. Simply stated, incident response is about having a plan in place to identify and handle cyberthreats before they cause more significant damage. These threats can take many forms, including everything from malware infections, compromised credentials or unauthorized access to sophisticated ransomware attacks.
Why Traditional Incident Response Falls Short
While creating one or more incident response playbooks to deal with potential threats is essential, the increasing volume and velocity of critical alerts organizations are tasked with investigating can easily overwhelm even the most skilled security professionals. With many companies now routinely handling anywhere from 10,000 to 150,000 or more alarms every day, scaling manual processes is virtually impossible – and finding the time and talent needed to develop and maintain custom scripting is impractical. That’s why as many as 70% of all alarms end up not being investigated at all, leaving organizations susceptible to serious attacks. The unfortunate truth is that traditional incident response playbooks based on manual effort are no longer effective.
The Solution: Automated Incident Response Playbooks
Faced with the challenges posed by traditional incident response, the mature security operations teams are now relying on security orchestration, automation and response (SOAR) to efficiently manage their security operations. Powerful low-code SOAR solutions like Swimlane unlock automation beyond the SOC by delivering a platform that serves as a system of record for the entire security organization. More specifically, automating incident response playbooks allows security teams to streamline alert monitoring and significantly reduce response times to address every alert and decrease risk exposure. You can learn more about the benefits of automated incident response in our previous article, “Automated Incident Response: Respond to Every Alert.”
Getting Started with Automated Incident Response
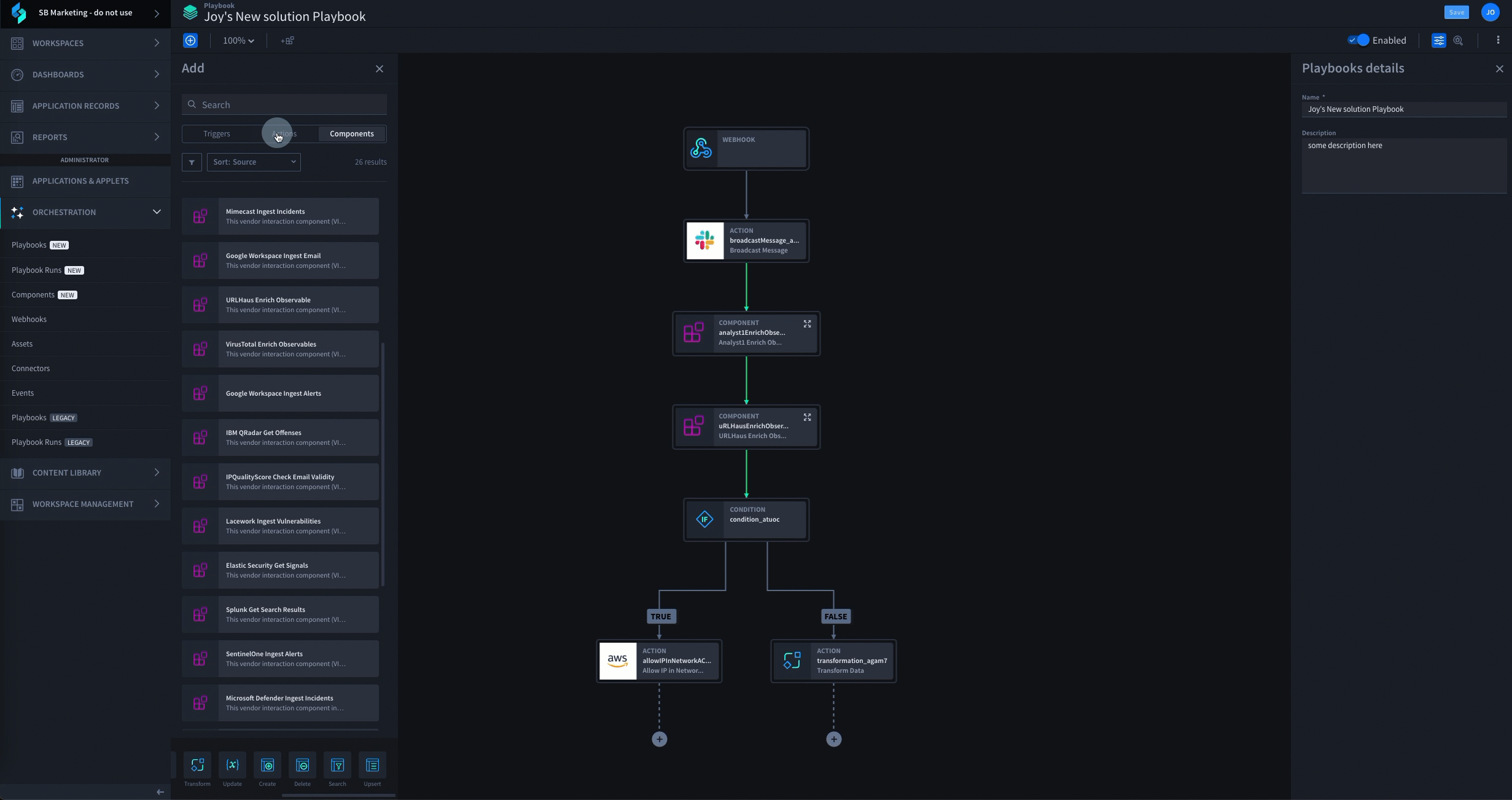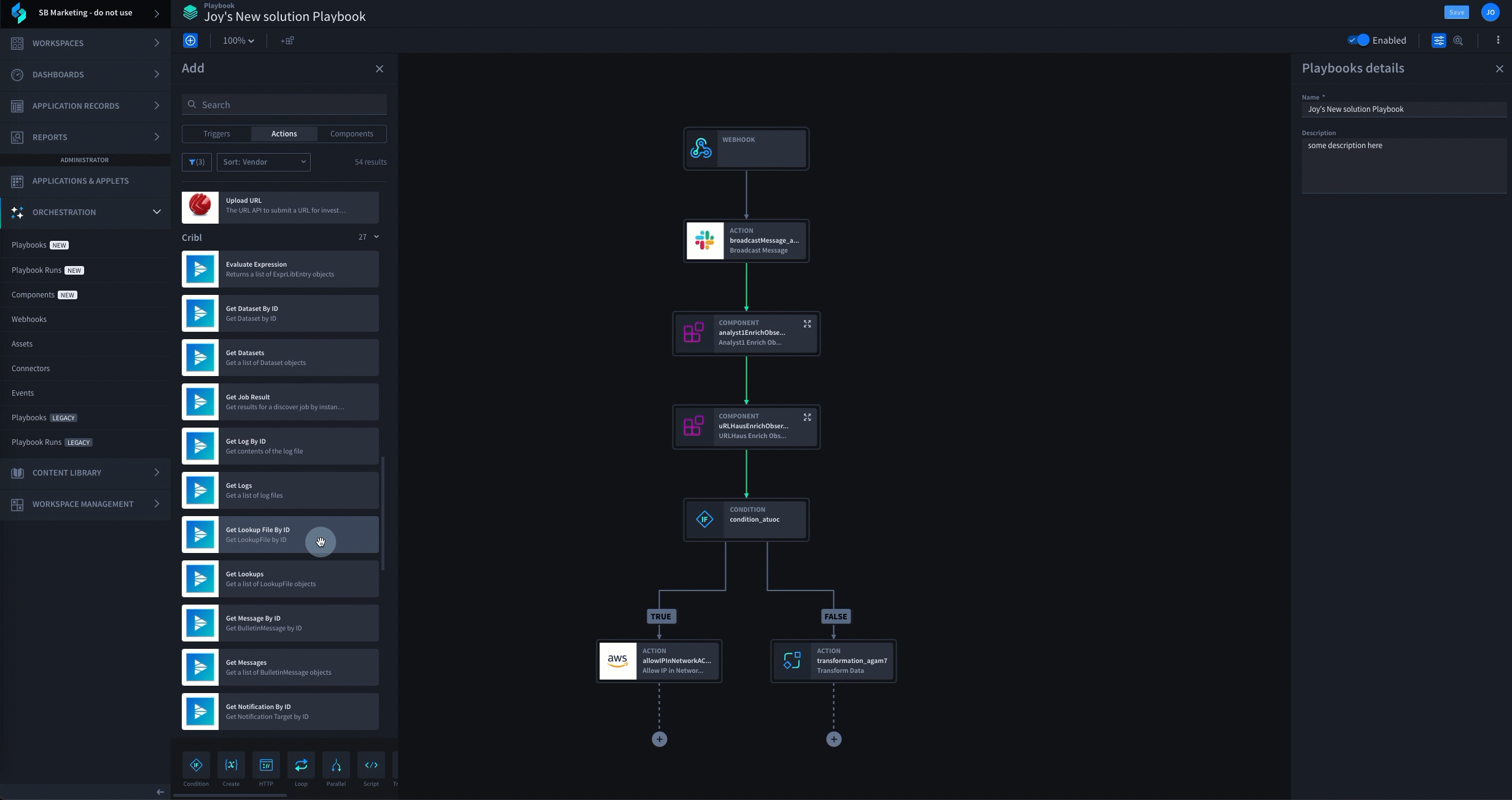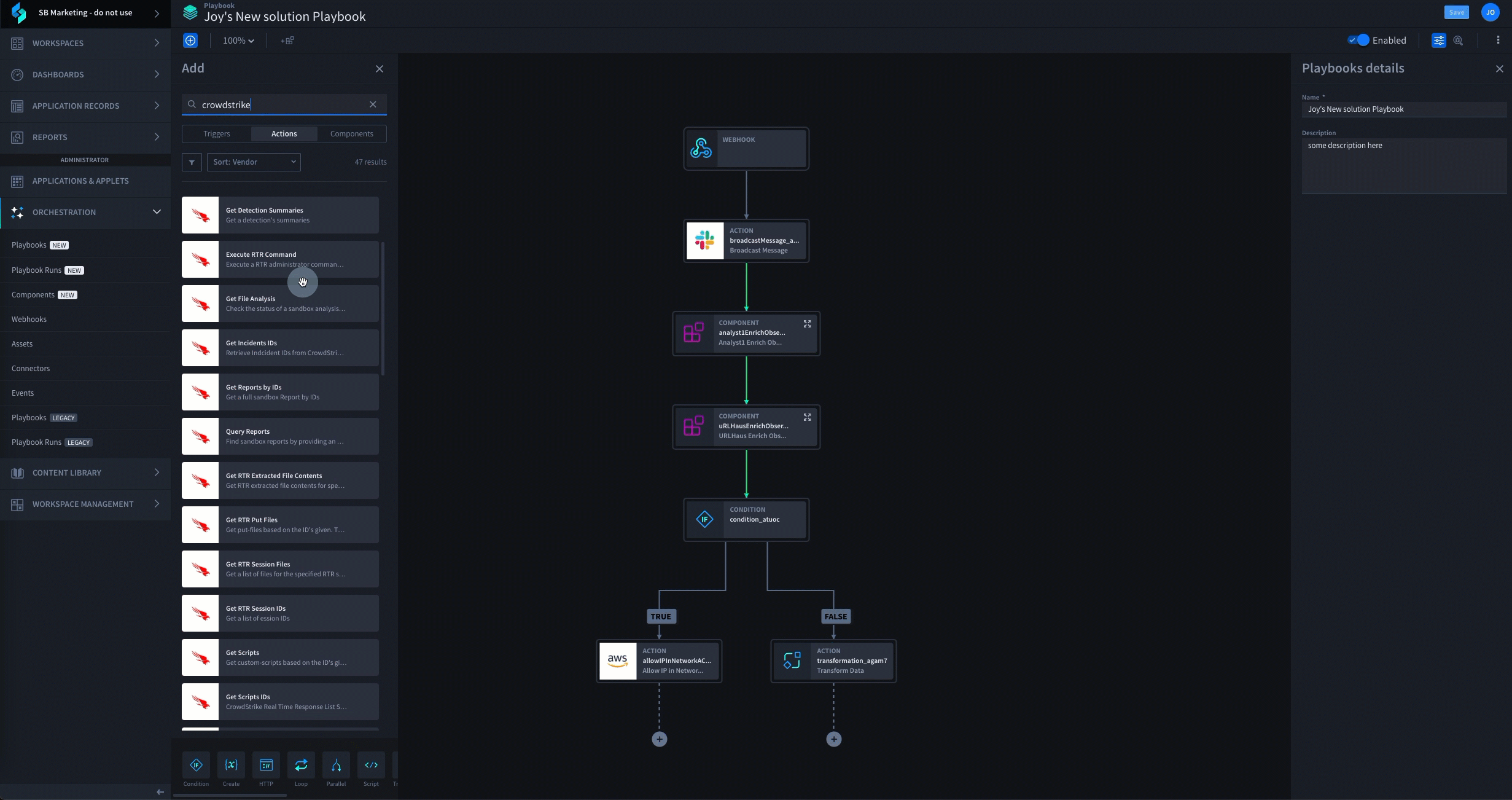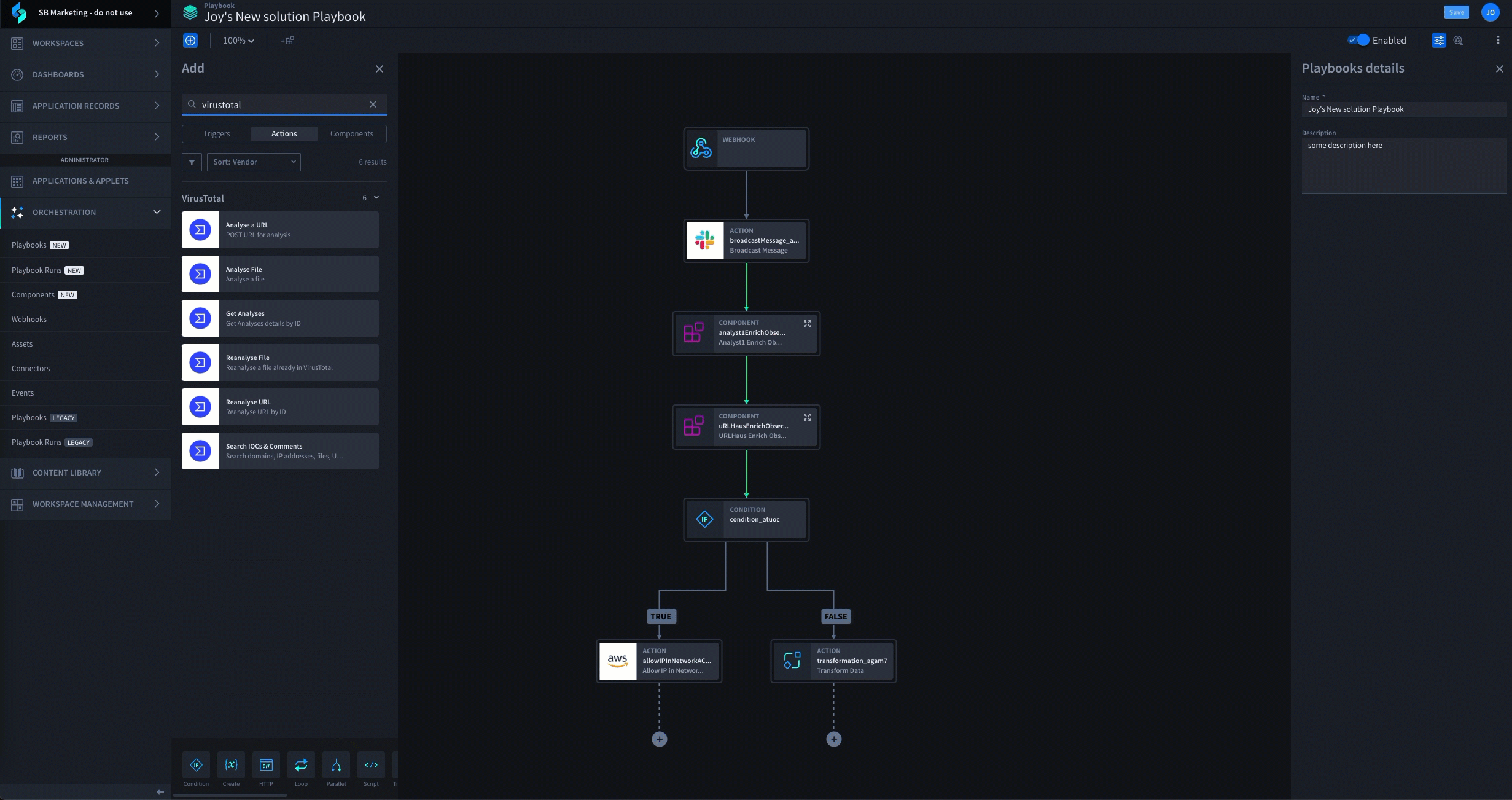
To protect your data from security threats, you need to have an established plan that can be executed by a robust incident response platform driven by low-code security automation. The first step in this process is the development of an extensible incident response plan that can be leveraged to create a playbook. This plan should include aspects such as: a strategy for the coordination of people, processes and technology; a framework for incident detection and analysis; protocols for breach containment, eradication and recovery; and a blueprint for post-incident action. These elements can then be combined to construct one or more incident response playbooks for dealing with specific threat vectors. Automating phishing analysis and response is often the first playbook Swimlane customers deploy. They complete this use case within the first 8 hours of their onboarding. See how it works:
With one or more incident response playbooks established, it’s now time to select a platform that enables you to execute your plan at scale. Such a solution should enable the automation of at least 80 – 90% of your established incident response process, allowing your security team to triage alarms more effectively, respond to critical events faster, and seamlessly integrate and leverage your existing security solutions. This enables your organization to extend the capabilities of its existing resources to handle vastly more threats in the same amount of time.
A few examples of some of the tasks a solution like Swimlane can enable you to automate include:
- Reviewing and analyzing threat intelligence sources
- Investigating incidents involving log gathering and analysis
- Updating security and support tickets
- Gathering key metrics and creating reports
- Sending email alerts to impacted parties
- Resolving and closing alerts
To delve further into the process of automating incident response you should review our blogs on “How to Build an Incident Response Playbook,” and “Managing Security Alerts with an Incident Response Platform.”
Swimlane’s Low-Code SOAR & Automated Incident Response Platform
Swimlane is at the forefront of the growing demand for powerful SOAR solutions. Its cloud-scale, low-code security automation solution replaces time-consuming manual tasks involved in incident investigation and response with machine-speed decision making and remediation to better protect your business. Integrating your people, processes and technology for a consistent and effective approach to automated incident response has never been easier. As a result, the world’s leading brands are increasingly turning to Swimlane to address a wide variety of security operations needs, including the automation of alert prioritization, threat remediation, tool orchestration and more – improving performance across the entire organization.
Interested in learning more about automating incident response? Download our comprehensive 19-page guide to Automating Incident Response.
Want to see Swimlane’s automated incident response capabilities for yourself? Request a live demonstration with a platform expert – or watch a customized on-demand demo now.
UP NEXT Check out the Webinar:
Swimlane Turbine
Schedule a Swimlane Turbine live demonstration with our experts! Learn how our AI-enabled security automation platform can help you solve the most challenging problems across your entire security organization.

