SOAR Playbook to Optimize Incident Response
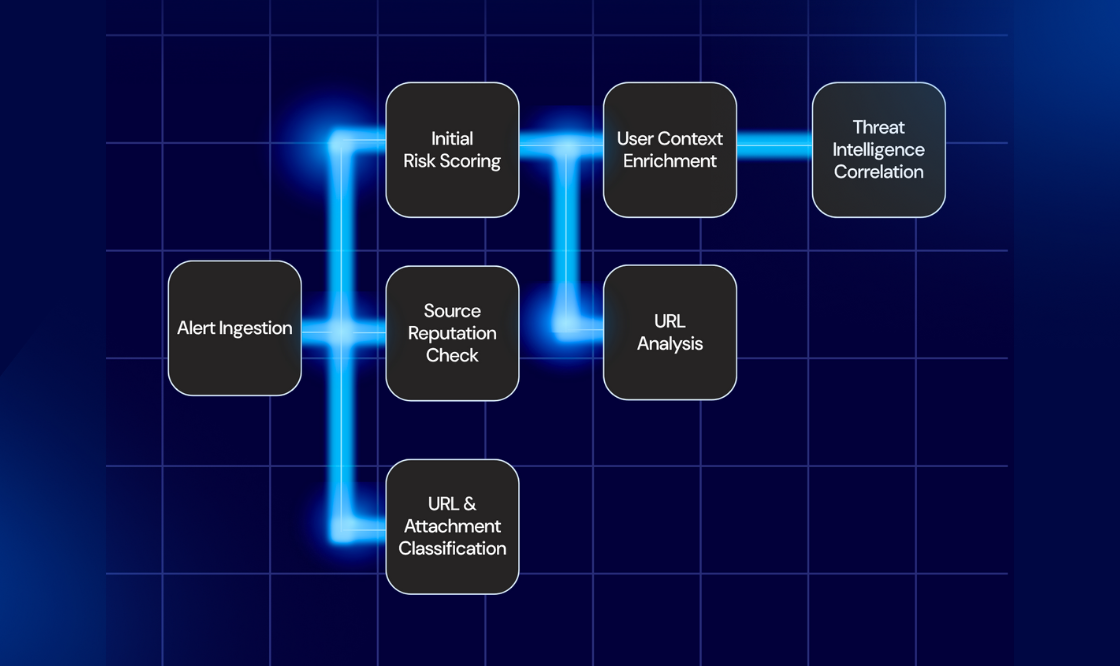
A SOAR playbook is a pre-defined, automated sequence of machine-driven actions designed to execute a specific security operation in response to an event, such as a SIEM alert or phishing report. It acts as a digital workflow that standardizes and accelerates routine incident response tasks, covering enrichment, investigation, and containment. The primary goal of a SOAR playbook is to achieve consistent, high-speed incident handling, thereby freeing up human analysts to focus on complex, high-severity threats.
Table of contents
What is a SOAR Playbook?
A SOAR playbook is a pre-defined sequence of automated actions designed to execute a specific security operation, most often in response to a security event or incident. Playbooks translate manual SOC analyst steps into a machine-driven workflow.
A playbook begins with a trigger, such as an SIEM alert or a reported phishing email, and then automatically executes a series of steps, including enrichment, investigation, containment, and, in some cases, remediation.
Agentic AI Playbooks vs. SOAR Playbooks
Today, agentic AI automation playbooks reimagine SOAR playbooks. They offer a more flexible and user-friendly building experience, allowing analysts to design, customize, and adapt workflows quickly while embedding AI agents or actions directly into the playbook itself. Agentic AI automation playbooks share a common goal with SOAR playbooks, while enabling more intelligent decision-making, dynamic responses, and continuous learning from evolving threats.
6 SOAR Playbook Examples to Boost Incident Response
Both SOAR playbooks and agentic AI automation share the same goals of reducing manual effort and speeding mean-time-to-resolution (MTTR),ultimately boosting incident response. Regardless of the technology used, the top use cases remain the same.
Here are six examples of how SOAR playbooks boost incident response and how agentic AI automation can take it even further:
1. Phishing Email Triage and Remediation
This playbook is triggered when a user reports a suspicious email, automatically extracting URLs and attachments, checking them against various threat intelligence feeds to determine a threat score, and then querying the email gateway to see if the message was sent to other users; if the content is confirmed as malicious, the playbook automatically quarantines the email from all inboxes across the organization, drastically reducing the window for a successful cyber attack.
Take it to the next level with agentic AI automation: Intelligently assess phishing threats beyond static indicators. It can automatically correlate reported emails with ongoing campaigns, learn patterns from historical phishing incidents, dynamically adjust risk scoring based on contextual factors, and orchestrate multi-step containment across email systems, endpoints, and network controls, all without manual intervention. Analysts receive enriched insights immediately, enabling faster decision-making and more proactive defenses.
2. Malware Containment and Eradication
Triggered by an alert from an Endpoint Detection and Response (EDR) system flagging a known malware file, this playbook immediately isolates the infected endpoint from the network to prevent lateral movement, pulls forensic data for deeper analysis, automatically updates firewall rules to block the malicious Command and Control (C2) IP address, and notifies the security team and the affected user of the containment actions taken.
Take it to the next level with agentic AI automation: Continuously monitor for anomalous behaviors associated with malware, automatically adapt containment actions based on threat severity, and coordinate cross-tool responses, such as updating firewalls, endpoint controls, and SIEM correlation rules, in real-time. Advanced playbooks can also flag patterns across incidents, helping analysts predict and preempt malware campaigns before they spread.
3. Vulnerability Management Prioritization
When a vulnerability scanner identifies a new critical vulnerability, this playbook steps in to apply business context and priority, effectively automating vulnerability management; it automatically enriches the vulnerability data with external threat intelligence to see if it’s being actively exploited in the wild, determines if the affected asset is business-critical, and then automatically creates a prioritized ticket in a ticketing system (like Jira or ServiceNow) for the patching team, ensuring the most dangerous flaws are fixed first.
Take it to the next level with agentic AI automation: Automatically evaluate vulnerabilities in context, considering threat intelligence from multiple sources, asset criticality, and business impact. AI automation can dynamically reprioritize remediation efforts as new exploits emerge, automatically generate enriched tickets with actionable insights for patching teams, and track progress across tools and teams, turning vulnerability management from a reactive task into a continuous, intelligence-driven process.
4. Security Information and Event Management (SIEM) Alert Enrichment
This essential playbook is triggered by any high-volume or novel alert generated in the SIEM; its primary function is to pull critical context from multiple sources, such as user identity from Active Directory, asset owner and recent login history from HR/IDP systems, geolocation data, and device configuration details, attaching all this information directly to the SIEM alert before it reaches an analyst, thereby reducing manual investigation time by providing a complete picture immediately.
Take it to the next level with agentic AI automation: Automatically pull and correlate data from multiple sources, learn from past alerts, and enrich SIEM events with predictive insights. With agentic AI, automation analysts receive pre-contextualized alerts with suggested next steps, reducing cognitive load and investigation time. Over time, the system adapts, automatically tuning alert thresholds and enrichment workflows to provide more accurate and actionable incident handling.
5. Brute-Force Attack Response
To mitigate account takeover attempts, this playbook is triggered by multiple failed login attempts for a single user over a short period; it immediately suspends the compromised user’s account via the Identity Provider (IdP), forces a password reset for the user on their next attempted login, and alerts the security team for manual confirmation and analysis of the attack source, effectively stopping the attack before it succeeds.
Take it to the next level with agentic AI automation: Dynamically detect patterns indicative of credential attacks across multiple systems, automatically adjust response thresholds, and execute multi-layered remediation, like account suspension, risk-based MFA enforcement, and endpoint monitoring, without waiting for manual approval. Additionally, agentic AI automation can track trends across incidents to identify emerging threats and recommend proactive security hardening.
6. Cloud Security Policy Enforcement
Triggered when a misconfiguration is detected in a cloud environment, this playbook’s crucial action is to automatically revert the configuration to the organization’s secure baseline, restoring the correct security posture (e.g., making the S3 bucket private), recording the violation for auditing purposes, and notifying the responsible DevOps team about the policy drift.
Take it to the next level with agentic AI automation: Continuously monitor cloud environments for misconfigurations, automatically remediate policy violations across multiple cloud platforms, and maintain an up-to-date compliance record. By correlating changes with deployment pipelines and risk data, an agentic AI automation system can prioritize alerts, guide DevOps teams with recommended actions, and ensure that the cloud security posture remains aligned with organizational standards, eliminating the need for manual intervention.
What’s the Difference Between a SOAR Playbook vs. SOAR Runbook?
While the terms are often confused, their distinction is crucial in a security operations center (SOC):
| Feature | SOAR Playbook | SOAR Runbook |
| Nature | Automated code and logic. | Manual documentation. |
| Execution | Executed by the SOAR platform. | Executed by a human analyst. |
| Format | Flowcharts, YAML/JSON definitions, integrations. | Step-by-step text, checklists, diagrams. |
| Goal | Automation and machine speed. | Guidance and human standardization. |
| Typical Use | Repetitive tasks, data enrichment, containment. | Complex, novel, or high-judgment incidents. |
In short: A playbook does the work; a runbook tells a human how to do the work. A runbook may contain instructions for when a playbook fails or when a human decision is required. As AI agents continue to gain prevalence in production SOC environments, the definition of a playbook is bound to change again. This shift is already a reality in agentic AI automation platforms, where actions are executed by AI agents rather than traditional SOAR platform mechanisms.
SOAR’s Role in Incident Response
SOAR’s (Security Orchestration, Automation, and Response) role in incident response has long been to act as the control center for security operations, bridging the gap between alert generation and final resolution. By deploying playbooks, SOAR ensures a consistent, fast, and measurable IR process.
- Speed: SOAR executes actions in seconds that would take an analyst minutes or hours, which is crucial for time-sensitive events such as data exfiltration or active malware campaigns.
- Scale: It enables a small SOC team to handle a massive volume of daily alerts without being overwhelmed by noise, addressing alert fatigue.
- Consistency: Every incident of the same type is handled using the exact codified steps, reducing human error and ensuring compliance.
- Focus: By automating tier-1 and tier-2 tasks (such as data enrichment, system checks, and initial containment), SOAR enables analysts to focus on complex threat hunting and strategic cybersecurity initiatives.
The Shift Towards Agentic AI Incident Response is Here Now
Agentic AI automation takes incident response even further. Platforms like Swimlane Turbine combine deterministic playbooks with agentic AI, changing the way that playbooks analyze context and take action across security operations. The intersection between traditional automation and AI agents provides a best-of-both-worlds scenario where deterministic if-then logic acts as guardrails for AI agents to reason and operate independently on approved tasks.
Ready to transform your SOAR-driven incident response playbooks to an agentic AI automation approach?
TL;DR SOAR Playbook
A SOAR playbook is an automated, machine-driven workflow that streamlines incident response by removing repetitive, time-consuming tasks like enrichment, containment, and remediation from human involvement. Its goal is to standardize security operations, achieve machine-speed response times, and free analysts to focus on complex threats. The blog provided six examples (phishing triage, malware containment, vulnerability prioritization, SIEM alert enrichment, brute-force response, and cloud policy enforcement) and highlights the shift towards agentic AI automation, which offers more flexible, intelligent, and dynamic playbooks, building upon the core benefits of SOAR.

Extend Beyond SOAR
Traditional SOAR platforms promise relief but often fall short, struggling with high maintenance demands, limited integrations, and inflexible processes. Learn what makes AI automation different.