In today’s ever-evolving cybersecurity landscape, choosing the right threat detection and incident response (TDIR) strategy is paramount. It’s like selecting the perfect toolset for a critical job – you need it to be precise, reliable, and efficient.
When it comes to coverage and capabilities, many believe that extended detection and response (XDR) is ahead of its field. However, does it really supersede the traditional incident response platforms like SIEM and SOAR? Are any of these solutions truly effective for understaffed security operations center (SOC) teams, or are they just “good enough” because they are the status quo or bundled “freebee” capabilities? The rest of this blog will provide information about SOC tools that some perceive to be “good enough” for types of cybersecurity attacks and incidents.
What sets XDR, SIEM, and SOAR apart? Are these even the right questions to be asked or categories to be evaluated to select a solution that will maximize automation ROI and SOC outcomes? At the end of the day, outcomes are all that matters. Let’s unpack the reality of XDR, SIEM, and SOAR technologies so that you can make an informed decision for your security solutions.
XDR: The Next Level of Cybersecurity?
First things first, there is no one-size-fits-all tool for the future of cybersecurity. In response to the increasing wave of cyber threats, the security industry must continually innovate and develop solutions that surpass the sophistication of these attacks. And one of the latest advancements is XDR. This category of technology got the XDR name because it extends detection and response beyond endpoint detection and response (EDR). It strives to revolutionize how we combat cyber adversaries. But efficient security is not just about increasing detection sources, it’s about responding swiftly and smartly.
What does XDR mean in Cybersecurity?
XDR is a trending approach to cybersecurity that aims to consolidate threat detection and response into a single management console. There are two types of XDR – Open and Native. The former counts on third-party integrations to gather telemetry forms, while the latter relies on one vendor to execute responses. Open XDR can be achieved through strategic security automation implementation. In contrast, Native XDR is offered by a single vendor who often standardizes telemetry sources around their product ecosystem. Watch this 2-minute video where Swimlane Co-founder Cody Cornell, and TAG Cyber CEO, Ed Amoroso discuss the reality of XDR to learn more.
XDR vs EDR (Endpoint Detection and Response)
These can easily get confused with each other, so here’s a brief distinction. As the name implies, EDR platforms are exclusively focused on endpoint detection sources. XDR solutions are considered an extension of EDR, hence the “x”. They consolidate sources like email, cloud, identity, and endpoint detection sources into a single platform. These examples are a few of the front-end features of XDR
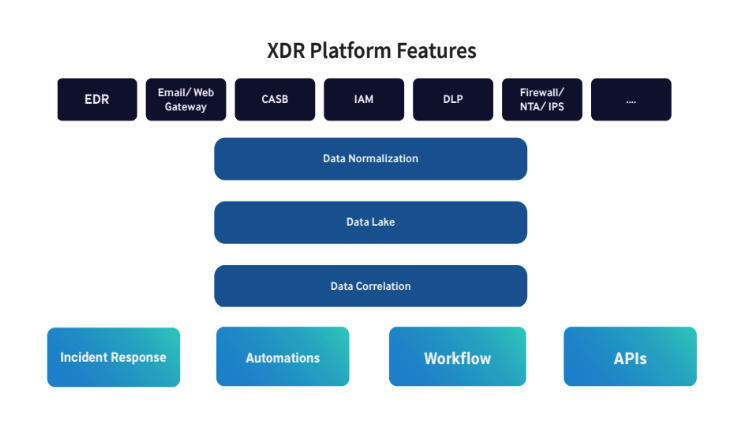
XDR was designed to be the “next-generation” of EDR. The problem with EDR tools is the amount of technical expertise and manual monitoring required to adopt them. XDR aspires to solve this problem and advertises higher alert efficacy with fewer false positives. However, it’s important to know that many XDR vendors differentiate based on the breadth of their front-end features (EDR, email or web gateway, cloud access security brokers (CASB), identity access management (IAM), data loss prevention (DLP), firewalls, etc.), not the quality of their back-end capabilities (incident response, automation, workflows, and APIs). As you evaluate XDR solutions, it’s important to consider if this checkbox or “soar-lite” approach is capable of the outcomes you need to achieve.
XDR Functionality and Features
To better understand what XDR represents in security, let’s take a look at its capabilities below. Many of these capabilities can also be achieved through AI-enabled security automation platforms.
- Gathers and evaluates data from various sources such as cloud, networks, and endpoints
- Streamlines the entire detection and response process
- Make use of a single console to deliver relevant insights
- Leverages different AI and micro-automation features for security
- Integrates siloed security solutions
- Offers potential access to key threat specialists in managed solutions
Impact of XDR Security
Now, after understanding the XDR definition and capabilities, it’s time to unravel the key benefits and weaknesses. From enhanced threat visibility to accelerated security operations, an XDR endpoint offers an incident management process. The strength of an XDR approach lies in its comprehensive data collection and analysis capabilities across multiple domains:
- XDR for Advanced Threat Detection
- XDR for Multi-Vector Threat Response
- XDR for Rapid Incident Response
From a business point of view, XDR by itself, means a more secure system against cyber threats. To maximize the impact of XDR, it’s important to be aware of common pitfalls.
- Offers a similar signal-to-noise ratio as EDR
- The cost of initial deployment and configuration services averages an additional 37%
- Telemetry consolidation requires robust APIs and automation. Many XDR platforms are light on these capabilities.
To enhance XDR, combining it with low-code automation as a force multiplier will streamline visibility and actionability at the point of inception.
XDR and Other Security Technologies
MDR vs XDR
Managed Detection and Response (MDR) is associated with both XDR and EDR. Considered “as a service”, MDR offers the same features as EDR, only with more capabilities. These include managed remediation, cyber threat hunting services, and guided response.
XDR vs MXDR
Managed Extended Detection and Response (MXDR) is a term that service providers use to differentiate their managed XDR services from their managed EDR, or other managed security services. Simply put, MDR or MXDR are the service components that typically accompany an XDR platform deployment. The high level of technical expertise and time required to manually monitor XDR alerts often require the support of a managed service.
XDR vs Traditional Security Solutions
Long before XDR platforms gained traction within the industry, security information and event management (SIEM) and security orchestration automation and response (SOAR) were invented to help SOC teams consolidate alerts and streamline remediation actions. With so many technology acronyms and options available, it’s important to know the difference between XDR, SIEM and SOAR.
Security Information and Event Management (SIEM)
SIEM platforms first entered the crowded security landscape in 2005. At this time, SIEM presented itself as a consolidated version of security event management (SEM) and security information management (SIM). The purpose of SIEM is to identify unusual system behavior that may indicate a cyberattack within a system’s log data. Most importantly, SIEMs generate alerts based on this information.
SIEM Core Functions
- Utilizes log data and security events
- Analyzes key information to assess the security incident
- Unifies all event data into a centralized platform to provide the visibility of malicious activities
- Provides security alerts and reports
Comparison Between XDR and SIEM
As the name implies, SIEM was created to help security professionals manage security events. At its core, it should make incident response faster and easier. The truth is, SIEM vendors never truly got around to the “EM” part of their namesake. That’s why many have acquired SOAR companies to supplement this feature set.
Unfortunately, early adopters have found that this bundled SIEM and SOAR platform approach is not working. That’s why many customers are looking for alternative solutions like XDR, or independent AI-Enabled Security Automation platforms, to replace this legacy SOC technology.
So where does this leave the SIEM? The truth is, like it or not, log management is still a very necessary function of any SOC. SIEM technology is a popular solution for achieving this. The SIEM provides many critical capabilities related to big data analytics, compliance, and audit requirements. If you have already invested in SIEM, no need to throw the baby out with the bathwater in favor of XDR. Instead, rethink the relationship between SIEM and SOAR so that you can achieve XDR outcomes using your current investments and a modern security automation approach.
Security Orchestration, Automation, and Response (SOAR)
Both EDR and SIEM solutions are often associated with alert fatigue and poor signal-to-noise ratios. SOC teams cannot effectively detect threats without these detection and analytics signals, but they can’t keep pace without automation. This is where SOAR comes in. This traditional security automation solution simplifies the incident response process, emphasizing the orchestration and automation of routine responses. There are many key benefits of SOAR, but these benefits can be enhanced by using an AI-enabled security automation platform to extend the impact of automation beyond SOAR use cases.
SOAR vs XDR: Simplifying Automation
s XDR the same as SOAR? The answer is no. If we compare XDR with SOAR, there’s still a substantial disparity in terms of function. The backend capabilities of XDR do include “SOAR-lite” features, but XDR maxes out at micro-automation outcomes. SOAR on the other hand provides extensible automation capabilities. Its main goal is to efficiently collect data against cyber threats by automating key responses. Traditional SOAR platforms are built to primarily respond to the data gathered from the SIEM. This is one of the main reasons why some vendors employ SIEM optimization by pairing the two traditional security platforms together to increase response time and efficiency.
The future of SOAR security removes the dependency on SIEM as the alert source for remediation action. As you evaluate technology for your TDIR program, it’s important to evaluate the difference between SOAR, no-code, and AI-enabled automation approaches.
Key Differences Between XDR, SIEM, and SOAR
What is the biggest difference between XDR, SIEM, and SOAR tools? Are these tools effective for maximizing the value of automation for modern SOC teams? To wrap this up, let’s have a quick run-through of the distinct features that make each security solution unique:
- SIEM primarily acts as a log collection tool for key event data. In doing so, it needs manual effort to support data storage, compliance reporting, and real-time analysis.
- SOAR benefits by simplifying manual efforts through the streamlining of key processes: incident response, orchestration, and automation. Additionally, it integrates the core capabilities of SIEM solutions with key security tools.
- XDR consolidates many threat detection sources that previously would have been sent to a SIEM, while offering “SOAR-lite” capabilities.
Choosing the Right Solution: XDR, SIEM, or SOAR?
So, what is the best solution for your organization? Only YOU can answer that question. Just remember that the promise of XDR may not require an XDR platform to achieve. Regardless of which technology approach you choose, the right security automation strategy can help you strengthen your TDIR ARMOR. After all, it’s not only about enhancing security posture but also automating manual processes, freeing up time for your SecOps team, and providing broader organizational coverage.
Aligning your Cybersecurity Needs with the Right Solution
It’s no secret the cybersecurity market is saturated with challenges in critical infrastructure and countless solution options, including various extended response examples. But choosing the right cybersecurity solution for your organization is crucial to your success. A quick tip: select a solution that will be easy for your team to deploy, manage, and customize for your organization’s unique environment, requirements, and goals.
If you’re confident in your security tech stack that you’ve already invested in and would like to improve efficiency without adding a hard-to-hire headcount, consider an AI-enabled security automation platform like Swimlane Turbine. It offers greater value than legacy SOAR, no-code automation, or a SIEM-XDR combo. Turbine integrates with your existing technology stack, eliminates missed alerts, and provides low-code security automation for comprehensive threat protection from internal and external threats – safeguarding your organization.
And after reading this blog, you’re still uncertain about your organizational needs. Swimlane has built the Automation Readiness and Maturity of Orchestrated Resources (ARMOR) framework for this exact reason. The ARMOR assessment offers security teams a clearer understanding of their security posture and helps evaluate their readiness for automation. This 20-question assessment utilizes a five-tiered model, serving as a roadmap to enhance security outcomes through automation.

The Swimlane ARMOR Framework
SecOps teams who want to map their goals, tactics, and security automation use cases to industry standard frameworks like NIST, CMMC, CMMI or C2M2

