Security Operations Center (SOC) Case Management: How to Streamline Incident Response
Streamlining SOC case management starts with centralizing incident data, automating routine tasks, and ensuring real-time context is available for faster, more consistent decision-making. By adopting tools that integrate threat intelligence, AI-driven triage, and automation, organizations can significantly reduce MTTR and analyst fatigue while improving overall incident response efficiency.
What Is SOC Case Management?
Security Operations Center (SOC) case management is the process of tracking and resolving cybersecurity incidents from detection through closure. It serves as the foundation of a SOC’s ability to organize, investigate, and respond to threats in a structured, repeatable way.
A modern case management approach centralizes all incident data, assigns tasks, automates response playbooks, and ensures that analysts follow consistent processes. It brings together threat intelligence, investigation details, and audit trails in one place. This is essential for operational efficiency and compliance.
Why Effective Case Management Matters in the SOC
Effective case management directly impacts the SOC’s ability to reduce mean-time-to-detect (MTTD) and mean-time-to-respond (MTTR), which are two of the most critical metrics in a cybersecurity strategy.
Without centralized workflows, teams face a host of challenges:
- Alert overload: Analysts waste time sorting through low-fidelity alerts.
- Siloed tools: Context and evidence are scattered across disconnected systems.
- Manual processes: Analysts spend hours copying data, enriching alerts, and routing tasks.
- Lack of visibility: Security leaders struggle to track outcomes or measure efficiency.
Improving case management enables faster threat resolution, clearer accountability, and more consistent incident handling, all of which are essential in today’s high-volume threat landscape.
Limitations of Traditional Case Management Tools
SOAR or automation tools built around generic IT ticketing systems fall short when applied to SOC environments. These tools were not designed with cybersecurity use cases in mind and often lack the functionality needed to support complex investigations
Key limitations include:
- Static ticketing workflows that can’t adapt to evolving threats or automation needs.
- No real-time enrichment, meaning analysts must manually gather context from multiple tools.
- Lack of automation in assigning, escalating, or resolving cases based on live data.
- Poor integration with SIEM, EDR, threat intel platforms, and other SOC tools.
As threat actors move faster and attacks grow more sophisticated, SOC teams need tools that keep pace with that speed through automation, intelligence, and integrated case management.
How Swimlane Transforms SOC Case Management
Swimlane overcomes the inefficiencies of traditional SOC tools by delivering case management capabilities that scale and speed up modern security operations. Rather than relying on disconnected systems or static ticketing tools, Swimlane offers an integrated environment where alert triage, investigation, collaboration, and resolution all happen within a unified AI-driven system.
Unified Case Management Application
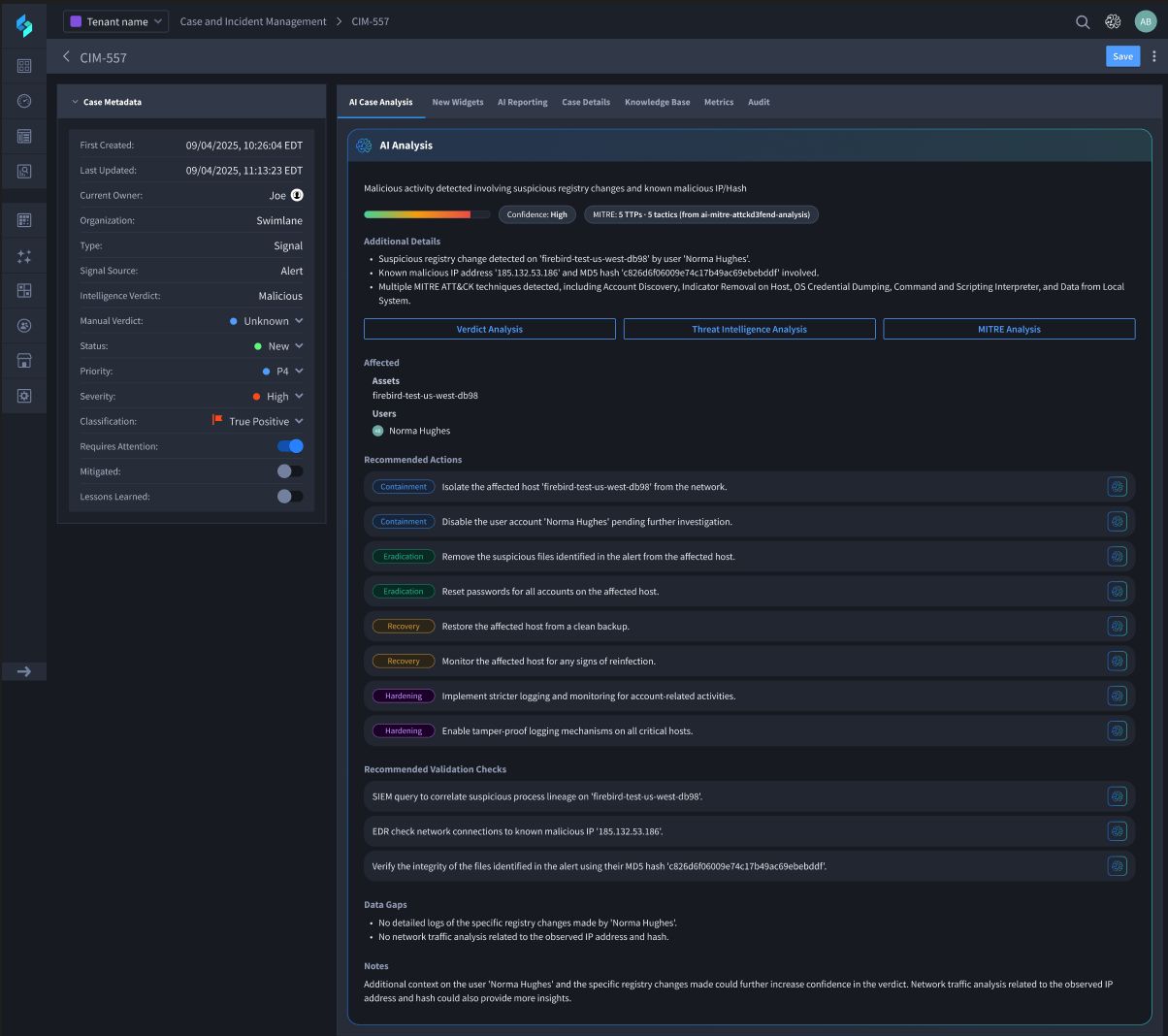
At the heart of the Swimlane Turbine platform is a dynamic, centralized case management application that leverages AI agents and automation to consolidate all incident-related data, including alerts, observables, threat intelligence, analyst notes, and linked cases, into a single interactive view. This enables SOC teams to investigate more quickly, act with greater context, and maintain a complete audit trail of every decision.
Real-Time Automation and Enrichment
Turbine automates routine tasks and instantly contextualizes cases. By pulling in real-time data from SIEMs, threat intelligence feeds, detection sources, and internal systems, Turbine eliminates the need for manual data gathering. Analysts are presented with enriched, fully contextualized cases the moment they open them, speeding up triage and decision-making.
AI Agents Purpose-Built for Case Management
Swimlane introduces a groundbreaking set of AI agents designed to take case management efficiency to the next level. These include:
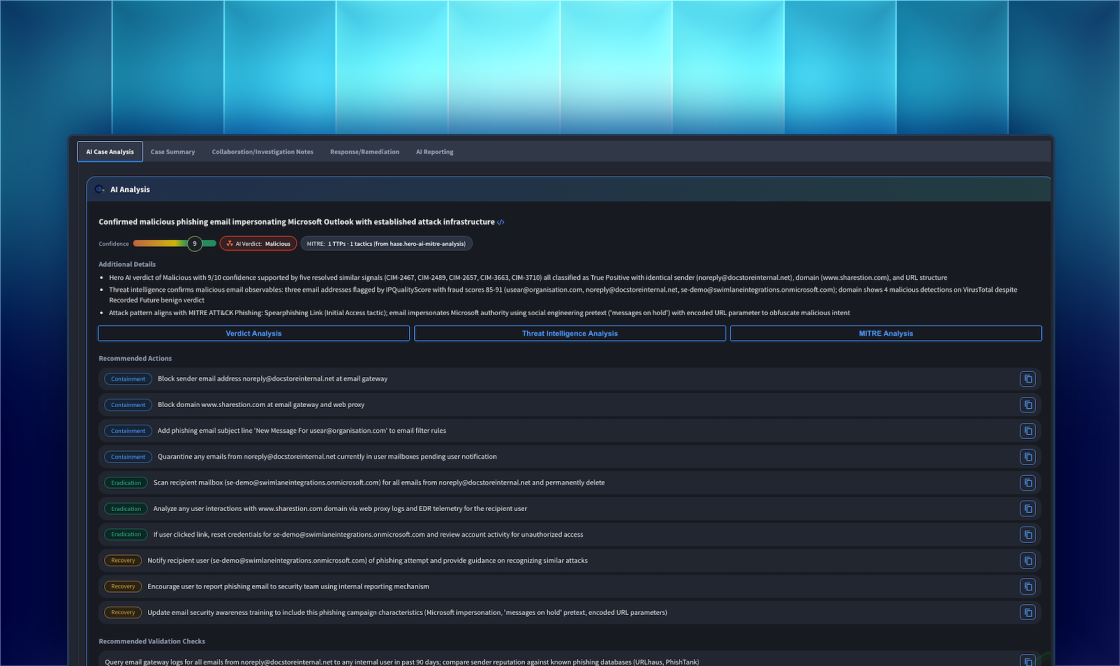
Verdict Agent: Evaluates case data in real-time and determines whether an alert is a true or false positive based on historical patterns and contextual evidence.
Investigation Agent: Automatically runs a comprehensive investigation, building timelines, narratives, and recommendations without analyst intervention.
Threat Intelligence Agent: Aggregates and correlates data from multiple threat intel sources such as VirusTotal, Cisco Umbrella, and RecordedFuture to provide a clear, consolidated threat view.
MITRE ATT&CK & D3FEND Mapping Agent: Translates alerts into standardized frameworks, helping teams understand attacker tactics and align response actions with industry-recognized models.
Outcome-Driven Incident Response
Turbine supports a wide range of response actions directly within the case, including isolating endpoints, revoking access, and launching playbooks for containment and recovery. With built-in workflows that align to frameworks like NIST, Turbine ensures incident response is both fast and compliant.
Benefits of AI Agents for Case Management with Swimlane
Swimlane’s agentic AI for case management brings measurable advantages:
- Faster response times: AI agents accelerate triage and action, reducing MTTR and dwell time.
- Reduced analyst workload: Repetitive tasks are handled autonomously, preventing burnout and freeing up time for complex investigations.
- Improved visibility and accountability: All case actions and AI-generated insights are logged and auditable, enhancing compliance and post-incident reviews.
Real-world deployments have shown significant time and cost savings, including an 8-hour reduction in daily analyst workload and 90% faster case handling for common use cases.
SOC Case Management FAQs
What is Security Case Management?
Security case management is the centralized handling of incidents, combining alerts, evidence, and actions into a trackable workflow for faster, more accountable responses.
How Does Incident Case Management Work in Modern SOCs?
Modern SOCs use platforms like Swimlane Turbine to automatically enrich cases, apply AI analysis, and trigger workflows, enabling faster detection, more contextual decision-making, and streamlined resolution.
What Should I Look for in Security Case Management Software?
Look for solutions that offer automation, AI assistance, visibility into case context, flexible integration, and customization.
What Does Case Security Mean in a SOC Context?
It’s about safeguarding investigation data, access logs, and case metadata throughout the lifecycle, critical for compliance, audit, and maintaining incident integrity.
TL;DR: SOC Case Management
Traditional SOC case management struggles to keep pace with today’s threats, hampered by manual processes, siloed tools, and alert fatigue. Effective case management is key to improving MTTD and MTTR, but legacy systems lack automation and real-time context. Swimlane changes the game by offering a unified platform with built-in AI agents that automate triage, threat analysis, and response. This allows SOC teams to enrich cases instantly, reduce analyst workload, and streamline resolution, transforming incident response into a faster, more scalable, and more consistent process.
Swimlane Case Management Demo
See what makes Swimlane Turbine case management unbeatable with a personalized demo.