The idea of cutting SOC playbook-building time in half is pretty enticing. There is no magic step-by-step process that provides this result. Instead, the solution is rooted in having the right technology capabilities at your disposal. Low-code security automation platforms include many no-code features while still offering the ability to execute Python scripts for advanced automation.
A Platform for Inventors
Swimlane Turbine is a low-code security automation platform – a platform for inventors. It enables orchestrators to develop complex security use cases without the need to develop complicated coding. Turbine empowers security developers to tackle complex security challenges through an efficient no-code playbook-building experience. With Turbine, analysts can automate without extensive programming knowledge, while orchestrators can develop and debug faster. Keep reading this blog to learn about the no-code capabilities and features that make it possible to build complete end-to-end use cases in as little as 25 minutes.
Why Customization is Critical
Security operations center (SOC) teams have the potential to address their most intricate challenges through automation. To fully harness the power of automation, and the ability to adapt, it is imperative to possess the inherent adaptability to tailor and personalize the code as required.
For those organizations constrained by time and resources, low-code platforms like Turbine emerge as a favorable option, striking a harmonious balance. These platforms cater to organizations that acknowledge the complexity of certain use cases within their operations, recognizing that pre-built workflows may not encompass the full spectrum of their needs.
No-Code Capabilities
Turbine provides a range of powerful no-code playbook features, including action testing, if/else, loops, variables, artificial intelligence (AI) ChatBots, Python inputs, and conditions. These features expedite the development of complex use cases and empower orchestrators to:
- Automate intricate processes: Turbine’s no-code playbook-building experience helps reduce the risk of human errors enhancing overall accuracy and reliability.
- Pre-Action Testing: Turbine allows users to test actions before implementation, ensuring that workflows operate as intended and errors are caught early in the process.
- Advanced Schema Mappings: Turbine supports sophisticated schema mappings, facilitating the transformation and manipulation of data within workflows.
Advanced Transformations: With its extensive capabilities, Turbine enables complex data transformations to be carried out effortlessly, streamlining data processing tasks.
In summary, Turbine’s advanced features enable a no-code approach to building intricate workflows, resulting in error reduction, efficient testing, and sophisticated data handling. To illustrate how these features come together in a real-life scenario, here is an example of how to build playbooks for phishing automation.
How to Efficiently Prevent Phishing Attacks
In the days of security orchestration automation and response (SOAR) a phishing triage use case would have required thousands of lines of code. Today, low-code security automation platforms make it possible to build this use case through a complete no-code experience.
Now, let’s walk through an example of a phishing scenario with fraudulent emails that exploit Gmail attachments. This use case might describe how an attacker sends fraudulent email attachments or posing as a popular online retailer to trick recipients into clicking on a malicious link and entering their login information, ultimately compromising their accounts. Here’s a step-by-step outline of the triggers and actions in this playbook.
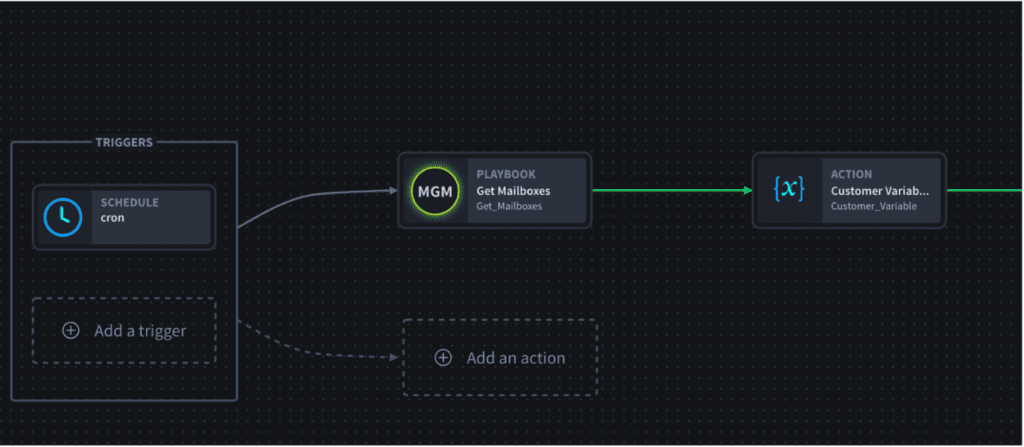
- Retrieve Customer Email Boxes: Obtain a list of customer email boxes that are to be processed.
- Customer Iteration: Iterate through the list of customers, setting a customer variable for each customer mailbox.
- Retrieve Email IDs: For each customer, collect the email IDs from their respective mailbox.
- Email Details Retrieval: Iterate through the email IDs, retrieving the complete details of each email.
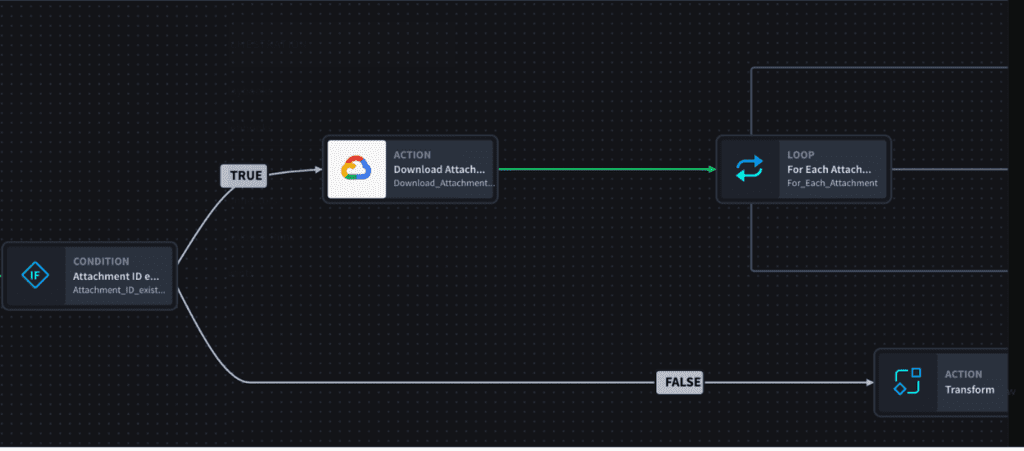
- Attachment Handling: Check if an email contains attachments; if yes, download the attachments. If there are no attachments, create a record.
- Attachment Iteration: Go through the list of downloaded attachments, and for each attachment, check whether it is in a zipped format. If it’s zipped, unzip it; if not, create a record for it.
Check out this diagram for a visual illustration of how to use no-code automation capabilities to prevent phishing attacks.
Outcomes
Phishing triage is a foundational SOC use case for all Swimlane customers. Pre-built phishing solutions are available for all Swimlane customers as a foundation, but no-code capabilities make it easy to customize. The ease of no-code and power of Python make low-code security automation the perfect solution for organizations who plan to extend automation to advanced use cases like fraud and SOAR case management, physical security, or insider threat.
This phishing triage use case has been tested by many customers. On average, our customers who leverage Turbine’s no-code capabilities have reported 50% time savings. They are now able to build complete end-to-end use cases in 25 minutes vs. 56 minutes.
Swimlane customers are having a great time creating playbooks with the Swimlane Turbine. If you haven’t had the chance to explore Swimlane Turbine yet, we’d encourage you to request a demo here.
Swimlane Turbine Demo
See how Swimlane Turbine can help you and your SecOps team hyperautomate by requesting a demo below


