Today is the day. Microsoft Windows 7 is officially end-of-life (EOL). The Windows 7 operating system was released on October 22, 2009. For 10 years now, IT and system administrators around the globe have relied on their trusty old Windows 7 OS. I mean, it was a step beyond Windows XP for sure. With EOL here, have you migrated all of your systems to Windows 10?
If you have not migrated, you definitely should. Here are several reasons why you should from a security perspective:
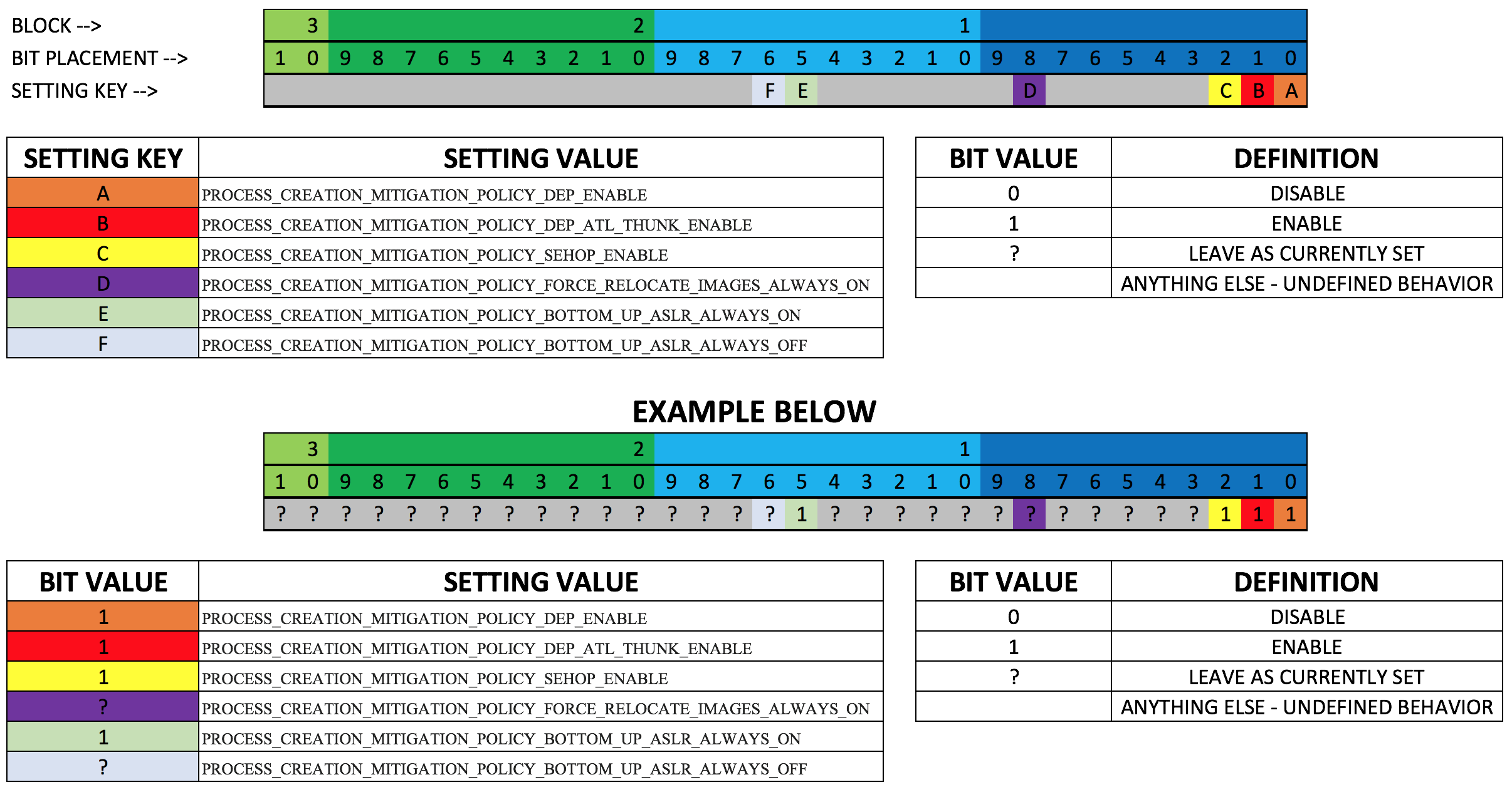
Process Creation Mitigation Cheatsheet
- Process Creation Mitigation
- In Windows 10 you can specify process creation mitigation features for a specific process. This means you can set DEP (Data Execution Prevention), SEHOP (Structured Exception Handler Overwrite Protection), and ASLR (Address Space Layout Randomization) on a per process basis. This is a huge win for security
- Credential Guard
- Credential Guard is used to isolate secrets such as NTLM hashes & Kerberos Ticket Granting Tickets using virtualization so that only privileged software can access them.
- SMB Hardening
- When connecting to Active Directory, Windows 10 offers SMB hardening for SYSVOL and NETLOGON shares which helps mitigate man-in-the-middle attacks
- Control Flow Guard
- When building software that will run on Windows systems, developers can enable CFG when compiling. CFG is used to detect an attacker’s attempt to change the flow of code. If detected, the application is terminated.
- Heap Protections
- Windows 10 introduced more secure protections against Heap memory. Heap is the location of memory that is allocated and utilized by the operating system. In Windows 10, randomization of Heap memory was introduced. Additionally, Windows 10 introduced Heap guard pages which protect against buffer overflow attacks
As a previous IT and System Administrator, management of these systems – especially deployment of GOLD images was difficult at first – that is until Microsoft Deployment Toolkit 2012.
When it was released, Microsoft provided a 700+ page document outlining how each component worked but didn’t really provide a “how-to” guide so I dove in and figured it out. This resulted in me writing a series of blog posts on deploying Windows using MDT 2012. Now, it’s much easier as Microsoft provides robust documentation on deploying Windows operating systems using MDT. In addition, Microsoft has made it quite a bit easier to deploy GOLD images using SCCM.
Windows 10 also provides more configuration and hardening options in regards to Group Policy Object settings which helps both security and IT administrators protect and manage their systems easier than any previous operating system. There are also several different Windows Update streams, which can either ease updates across your systems or make it more complex – all dependent on your environment setup.
If you have not upgraded your systems to Windows 10 then, well, you’re a little late. As of today your Windows 7 systems will no longer receive security updates from Microsoft. This means, any exploits found in the wild will not be patched unless Microsoft deems them critical.
If you are unable to remove all Windows 7 systems then I highly recommend that you segment them into their own networks and reduce system-to-system communication from these hosts. Additionally, I would add additional logging (you are logging right?) especially around PowerShell and process creation/execution/etc.

