What is Security Orchestration, Automation and Response (SOAR)? Guide to SOAR Platforms in Cyber Security
| Security Orchestration, Automation, and Response (SOAR) is a powerful security solution that combines disparate security tools, automates repetitive tasks, and orchestrates workflows. It empowers security teams to manage and respond to security incidents more efficiently, consolidate and analyze threat intelligence, and streamline overall security operations. By integrating automation and orchestration, SOAR platforms dramatically reduce manual effort and accelerate incident resolution. |
Security teams are constantly battling an overwhelming volume of alerts, complex attack surfaces, and a shortage of skilled professionals. This relentless pressure can lead to burnout, missed threats, and inefficient security operations. Fortunately, a powerful solution has emerged to help organizations reclaim control: Security Orchestration, Automation, and Response (SOAR). This guide will demystify SOAR, exploring its core components, benefits, and how these vital cybersecurity tools empower your team to operate with unprecedented speed, precision, and efficacy.
What is a SOAR Platform?
A Security orchestration, automation and response (SOAR) platform is designed to help security operations (SecOps) teams automatically execute repetitive tasks, such as responding to phishing alerts, SIEM or EDR alert triage and is typically used within the context of the Security Operations Center (SOC).
Gartner defines SOAR technology as “solutions that combine incident response, orchestration and automation, and threat intelligence platform management capabilities in a single solution”. At the most basic level, there are three primary ways that SOAR works to improve SecOps outcomes:
- Automates incident response: SOAR security software – specifically security automation – executes a sequence of workflow tasks without human intervention. Security teams who automate incident response with SOAR speed their mean time to resolution (MTTR). Automation also frees up analyst time for more strategic work, increasing the team’s job satisfaction and retention rates.
- Adds context to incident data: Security orchestration integrates disparate systems or platforms. This leads to consolidated and contextualized intelligence so that analysts can quickly view all incident data in a single case management view, complete with customizable dashboards and reports. This enrichment process provides security teams with actionable intelligence so they can improve operational efficiencies and mature the security posture.
- Unifies people, process and technology: Integrations are the magic behind how SOAR unites people, processes, and technology. SOAR technologies that deliver well-orchestrated security ecosystems ensure that security teams accelerate time-to-value and speed incident response times.
What are Security Orchestration and Automation?
Security orchestration integrates and coordinates the various security tools and processes involved in a security operation. The goal of security orchestration is to streamline and improve the efficiency of security operations by automating manual tasks and integrating different tools and processes.
Security automation refers specifically to the use of automated tools and processes to perform security tasks. This can include things like automating the deployment of security patches, automating the investigation of security incidents, and automating the implementation of security controls.
The Difference Between Automation and Orchestration
The main difference between security orchestration and security automation is that security orchestration involves coordinating a wide range of security tasks simultaneously across tech stacks, while security automation focuses specifically on the use of automated tools and processes to perform these tasks.
Both approaches can help improve the efficiency and effectiveness of security operations, but security orchestration takes a more holistic view of the security landscape, while security automation is more focused on the use of specific tools and processes.
Discover our blog Security Orchestration vs. Automation for more information.
What is Threat Intelligence Management?
Threat intelligence management ingests, analyzes and enriches data about potential security threats. This can include information about cyber threats such as malware, phishing attacks, and hacking attempts, as well as physical security threats such as terrorism or other forms of violence.
Threat intelligence management is an important part of a comprehensive security strategy, as it helps organizations stay informed about potential threats and take proactive measures to protect themselves.
The goal of threat intelligence management is to provide organizations with the information they need to protect themselves against potential threats. This can involve gathering information from a variety of sources, such as open-source intelligence, proprietary data sources and even social media. Once this information is collected, it is analyzed to determine its relevance and potential impact on the organization.
Finally, the information is disseminated to the appropriate parties within the organization, such as the security team or top executives, so that they can take appropriate action to mitigate any potential threats.
What is Incident Response?
Incident response responds to and manages the aftermath of a security incident. A security incident is any event that poses a potential threat to an organization’s information, systems, or networks. This can include cyber attacks, data breaches, network intrusions, and other types of security incidents.
The goal of incident response automation is to minimize the impact of a security incident and restore normal operations as quickly as possible. To achieve this, organizations typically have an incident response plan in place that outlines the steps to be taken in the event of a security incident.
Effective incident response requires a coordinated effort between different teams and departments within an organization. This can include the security team, IT staff, legal departments and other stakeholders. Some SOAR platforms offer case management and reporting to make this communication across teams easier.
Why is SOAR Important?
SOAR platforms help organizations streamline and improve the efficiency of their security operations by automating tasks and integrating different security tools and processes. There are several reasons why a SOAR platform can be important for an organization:
- You can increase SOC efficiencies: SOAR technologies can automate many routine tasks, freeing up security analysts to focus on more complex and high-priority tasks. This can help improve the efficiency of security operations centers (SOC) and reduce the workload of security staff.
- You can enhance incident response: A robust SOAR platform can provide a centralized platform for managing incident response, including automating the investigation and response to security incidents. This can help organizations respond to incidents more quickly and effectively.
- You can integrate with diverse tech stacks: Certain SOAR solutions can integrate with a variety of different security tools and processes, allowing organizations to better manage their security infrastructure and gain a more comprehensive view of their security posture.
- You can improve security risk posture: By automating tasks and integrating different security tools and processes, a SOAR platform can help organizations identify and mitigate potential security risks more effectively. This can help reduce the overall risk profile of the organization.
4 Benefits of SOAR
SOAR technologies have many benefits for SOC teams. Breach prevention, improved SecOps KPIs, reduced analyst burnout and improved overall ROI are the leading benefits that customers realize.
- Reduce the likelihood of a breach: With SOAR, enterprise security teams are able to proactively respond to ~80% more security telemetry data. They were able to stop attacks earlier in the attack lifecycle and prevent them from becoming breaches. Actionable intelligence that is gathered through modern SOAR platforms helps measurably improve their risk posture over time.
- Improve SecOps metrics: German MSSP, fernao magellan, talks about how Swimlane helped their team consolidate case management, improve alert triage, and ultimately save 70% of the time previously spent on incident response.
- Reduce staff burnout: By using low-code SOAR, analysts save the time required to filter, sort, and visualize data. This frees analysts from manual and error-prone tasks so they can spend more time on strategic initiatives. Because of this, customers are able to retain talent and institutional knowledge, which leads to greater overall security.
- Improve ROI for all security investments: A Fortune 100 security team saves $160,000 per month in labor costs. This financial benefit is a result of low-code SOAR, saving them 3,700 hours of work each week. The ROI was calculated by measuring the percentage of detection alerts that require manual processes versus automated processes. Automation dashboards and reporting make it easy to measure these statistics so that security leaders can evaluate the efficacy of their investments.
The benefits of SOAR for SOC teams are expansive. Below, watch how SOAR improves the life of a security analyst.
Common SOAR Use Cases
The most common SOAR use cases tend to be SOC-oriented use cases, such as:
- Phishing investigation and triage
- SIEM and EDR alert/event management
- Threat intelligence enrichment & processes
- Digital forensics
- Incident response
- Vulnerability management
- Threat hunting
- Insider Threats
Read more about Common SOAR Use Cases.
SOAR Use Cases Outside the SOC
Security teams are also looking for ways to utilize automation outside of traditional SOC use cases. SecOps teams can turn to modern SOAR platforms to help automation:
- security fraud and brand impersonation
- Fraud case management
- Securing employee onboarding and offboarding
- Mobile phishing triage
Read more about Outside the SOC Use Cases.
5 SOAR Best Practices: What to Look for in a SOAR Platform?
When considering a SOAR platform, there are several key factors that you should consider:
- Integration capabilities: Look for a SOAR platform that can easily integrate with a variety of different security tools and processes. This will allow you to manage your security infrastructure and gain a more comprehensive view of your security posture.
- Automation capabilities: Consider the types of tasks that the SOAR platform can automate and whether these align with your organization’s needs. Look for a platform that can automate a wide range of tasks, including incident response, vulnerability management, and threat intelligence gathering.
- Customization and flexibility: Look for a SOAR platform that can be customized and configured to meet the specific needs of your organization. This will allow you to tailor the platform to your unique security requirements and workflows.
- Ease of use: Consider the usability of the SOAR platform, including its user interface and the overall learning curve for your team. A platform that is easy to use will make it easier for your team to get up and running quickly and will reduce the time and effort required to manage and maintain the platform.
- Support and training: Look for a SOAR platform that offers comprehensive support and training resources. This will ensure that you have the resources you need to effectively use and maintain the platform.
By considering these factors, you can choose the best security automation tools that meet the specific needs of your organization and help improve the efficiency and effectiveness of your security operations.
What SOC metrics should I be looking at?
SOAR success and metrics are going to be unique to each company and the organization’s goals, but a few basic key performance indicators (KPIs) and incident response metrics that all security teams need to measure include:
- Mean time to detect (MTTD)
- Mean time to investigate (MTTI)
- Mean time to respond (MTTR)
- Granular ROI reporting
- Analyst workload
What SOAR Metrics Should I Be Looking At?
Traditionally, the value of SOAR has been limited to the SOC, but as we look to the future of security automation, we can expect to see the notion of SOC metrics expand to include more comprehensive security metrics.
Gartner has started referring to this as their “CARE standard for cybersecurity.” This framework provides a suggestion for what the industry standard of security metrics or KPIs should be. This framework is outlined by the CARE acronym: consistent, adequate, reasonable, and effective. Some KPIs that align with these groups include metrics like:
- Consistent: security awareness training completed by employees in the past month
- Adequate: percentage of endpoints that have been updated for anti-malware protections
- Reasonable: average length of delays caused by security protocols
- Effective: number of incidents in the past year related to configuration issues
While these metrics are not commonly associated with SOAR use cases, some platforms are capable of offering these detailed insights. That’s why it’s important to evaluate SOAR vendors in detail before investing in these security automation solutions.
TL;DR: What is SOAR?
SOAR is a powerful cybersecurity solution designed to streamline security operations by integrating your existing tools, automating repetitive tasks, and orchestrating complex workflows. Essentially, it helps security teams respond to threats faster and more effectively by reducing manual effort and human error. In short, SOAR enhances your team’s efficiency, significantly cuts down MTTR, combats analyst burnout, and ultimately maximizes the return on your security investments, all while bolstering your defense against breaches.
SOAR FAQs
What are the characteristics of a SOAR security platform?
SOAR platforms are characterized by their ability to orchestrate workflows, automate repetitive tasks, manage security incidents, and integrate threat intelligence. Key features include customizable playbooks, case management, and robust reporting.
Which SOAR platform offers the best integration with existing security tools?
Swimlane is designed for extensive integration with existing security tools. It offers an API-first architecture and a vast library of pre-built connectors and a marketplace to integrate with virtually any security product, overcoming vendor lock-in and allowing organizations to leverage their current investments.
How does SOAR improve the efficiency of security teams?
SOAR significantly improves efficiency by automating repetitive, manual tasks, which drastically reduces MTTR to incidents. By streamlining workflows and providing enriched context, it frees up security analysts to focus on more complex, strategic initiatives, thereby mitigating burnout and enhancing overall SecOps effectiveness.
How does SOAR integrate with other security tools?
Swimlane integrates with other security tools via its API-first architecture and a wide range of pre-built connectors available in its marketplace. This enables bi-directional communication, allowing Swimlane to ingest alerts, enrich data, and trigger actions across various security solutions (like SIEMs, EDRs, firewalls, and threat intelligence platforms) to automate the entire incident response lifecycle.
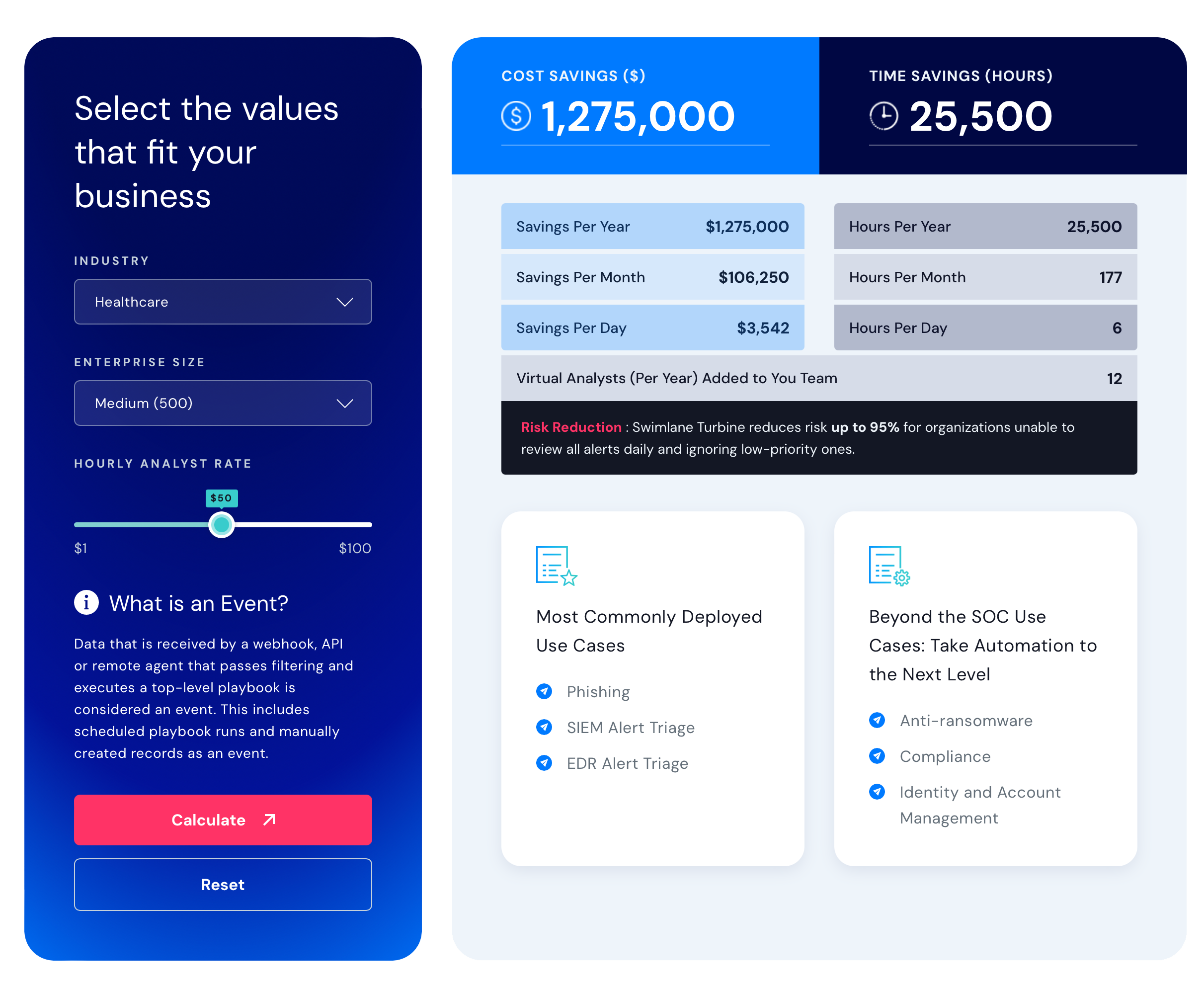
Swimlane ROI calculator
Estimate the savings you can achieve with Swimlane Turbine.


