Today, Swimlane is excited to announce that we are releasing a new SSP (Swimlane Solutions Package) for use within the Swimlane platform. This SSP will enable organizations to automate the testing of their defenses using Atomic Red Team using our new open-source project called atomic-operator.
When using this SSP organizations can gain an understanding of their defensive posture against tests mapped to MITRE ATT&CK techniques. By using this use case you can correlate detections of these tests against their existing automation and log sources thus giving them fast feedback on their defensive posture based on tests available within Atomic Red Team.
How It Works
Utilizing our new open-source project atomic-operator and the open-source project by Red Canary called Atomic Red Team (ART), enables organizations to run tests against desired systems to help determine their defensive capabilities. Using this project in combination with the power of SOAR and the Swimlane platform, we can run these tests remotely and correlate a given set of alerts to a test being run.
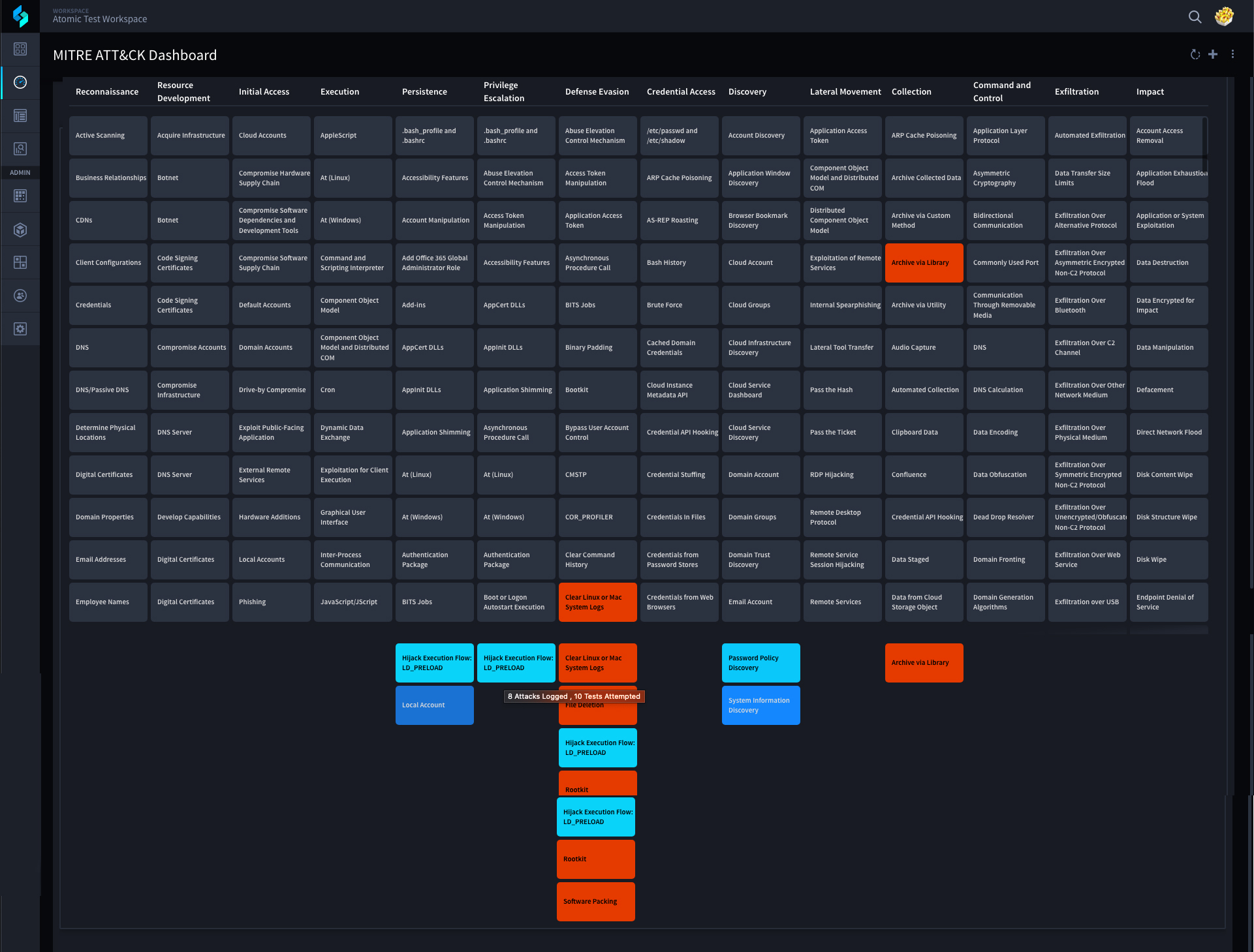
By correlating incoming alerts to a given test we can visually see how we are fairing when it comes to detection capabilities, or lack thereof, as well as visibility and coverage. We can see this by using a Swimlane widget to overlay this information across the MITRE ATT&CK Framework.
Operationalize the MITRE ATT&CK Framework
For each MITRE ATT&CK Technique run on our test systems, we display shades of color representing an organization’s ability to detect that test (technique). Each time a test is run, this use case attempts to find alerts coming into Swimlane within a specified period (configurable) and associate them to our test attempt via correlation. Depending on the results of this correlation our MITRE ATT&CK Dashboard displays our defensive “coverage” of that technique.
Red represents that you have run a test for the identified technique but NO detections have been identified as similar to the test being run.
If a technique is NOT red then we provide a gradient of color which represents the ability to detect this technique. The darker color means you have detected tests associated with this technique but very few times. The lightest color means you have detected tests associated with this technique every time you have run it’s tests.
Using this use case requires that you have credentials to remotely access test systems whether they are Windows, macOS, or *nix. Once you have configured your credentials for these systems, an organization then associates any tests that they would like to run on the desired system.
Next select our “Run Atomic Test on Host” widget button and we will immediately begin running those tests on the selected system.
Each time a test is run on a host we create a Test History record to keep track of our progress as well as associate any identified incoming alerts (detections) with a single run of an Atomic test. It is configurable but by default we have set this use case to look for incoming alerts similar to our test from the time the test was run to an hour in the future. If any are found we know we have successfully detected this technique within our environment.
All of this is reflected on our MITRE ATT&CK Dashboard widget. If we have not detected any incoming alerts to a test then we know we need to improve our defenses, thus the red color on our dashboard. The lighter the colors on a technique means the stronger defensive controls an organization has in place.
As we mentioned before, this use case utilizes a new open-source project called atomic-operator. atomic-operator is a Python execution framework for Atomic Red Team tests than enable you to run these tests locally or remotely from Windows, macOS, or *nix based systems. A true cross-platform execution framework. You can find more information about atomic-operator here: https://www.atomic-operator.com/ or on GitHub.
See Swimlane Turbine in Action
Schedule a Swimlane Turbine live demonstration with our experts! Learn how our AI-enabled security automation platform can help you solve the most challenging problems across your entire security organization.